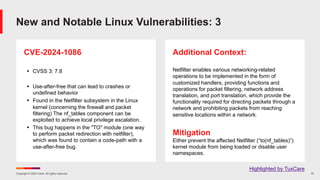
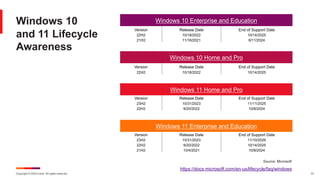
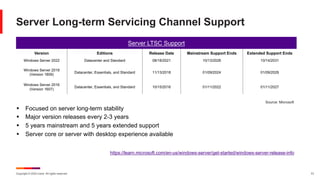
The February 2024 Patch Tuesday webinar presented a comprehensive overview of Microsoft's resolution of 73 CVEs, including two critical zero-day vulnerabilities and updates across various platforms. Key vulnerabilities include security-bypass flaws in Windows, a critical flaw in the glibc affecting numerous Linux distributions, and multiple patches in the Microsoft Office suite. The session also highlighted lifecycle support information for Windows versions and notable vulnerabilities in recent software updates.














![Copyright © 2024 Ivanti. All rights reserved. 19
February Known Issues for Windows 10
§ KB 5034763 – Windows 10 Enterprise and Education, version 21H2 Windows 10 IoT Enterprise,
version 21H2 Windows 10 Enterprise Multi-Session, version 21H2 Windows 10, version 22H2,
all editions
§ [Copilot Not Supported] Copilot in Windows (in preview) is not currently supported when
your taskbar is located vertically on the right or left of your screen. Workaround: To
access Copilot in Windows, make sure your taskbar is positioned horizontally on the top or
bottom of your screen.
§ [Icon Display] Windows devices using more than one (1) monitor might experience issues
with desktop icons moving unexpectedly between monitors or other icon alignment issues
when attempting to use Copilot in Windows (in preview).
§ Microsoft is working on a resolution for both issues.](https://image.slidesharecdn.com/frfebruary2024patchtuesday-240215162103-28febabd/85/2024-Francais-Patch-Tuesday-Fevrier-19-320.jpg)
![Copyright © 2024 Ivanti. All rights reserved. 20
February Known Issues for Windows 10 (cont)
§ KB 5034770 – Windows Server 2022
§ [Image File Execution] After you install KB5034129 (Jan), chromium-based internet
browsers, such as Microsoft Edge, might not open correctly. Browsers affected by this issue
might display a white screen and become unresponsive when you open them.
Devices that have browser specific Image File Execution Options (IFEO) might be affected
by this issue. When an entry for Microsoft Edge (msedge.exe) or other chromium-based
browsers is found in the Windows registry, the issue might occur. A registry entry can be
created by developer tools or when certain debugging and diagnostic settings are in place
for browsers.Microsoft is working on a resolution for both issues.
§ Workaround: See KB for registry editing options. Microsoft is working on a resolution and
will provide an update shortly.](https://image.slidesharecdn.com/frfebruary2024patchtuesday-240215162103-28febabd/85/2024-Francais-Patch-Tuesday-Fevrier-20-320.jpg)