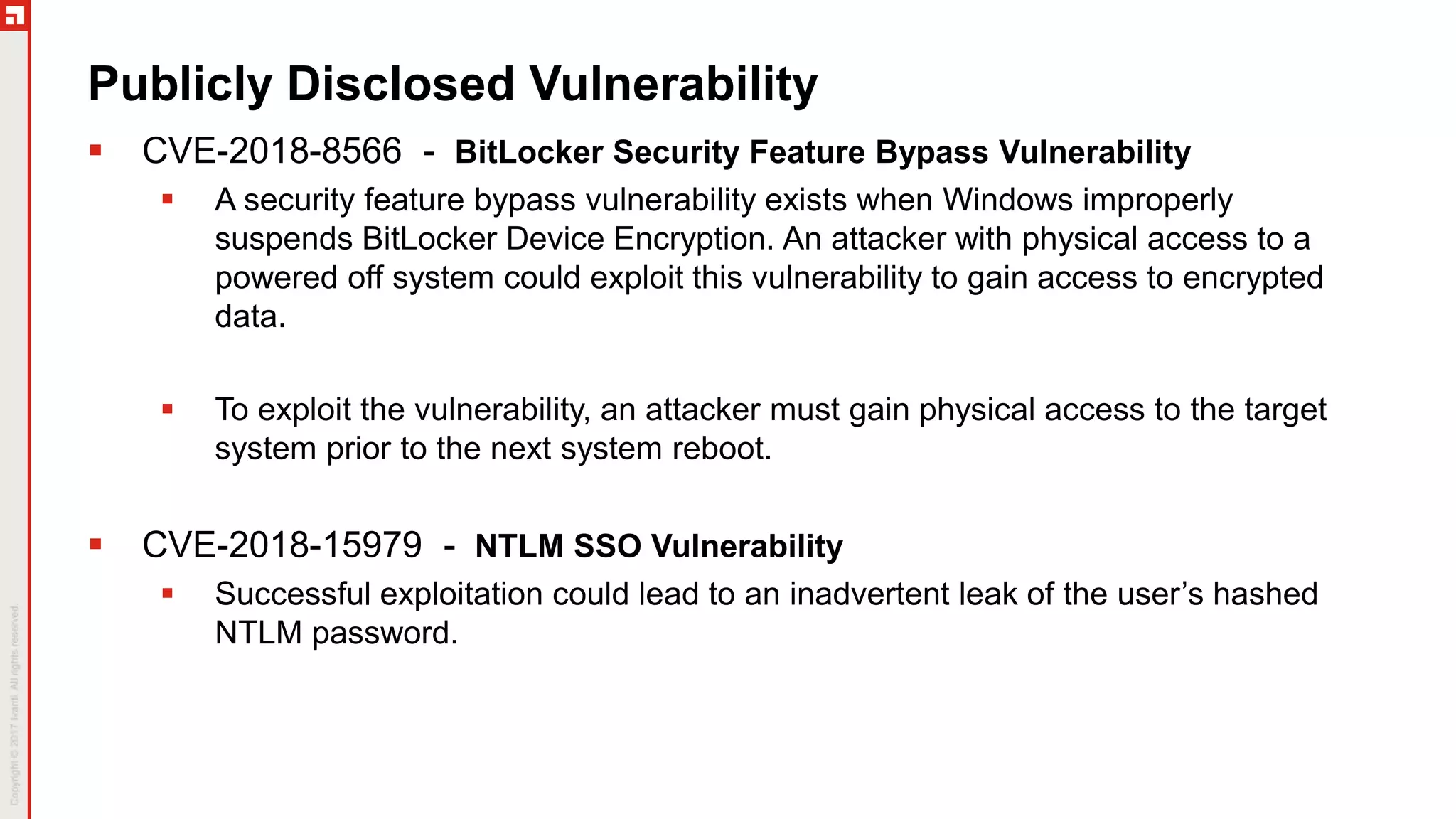
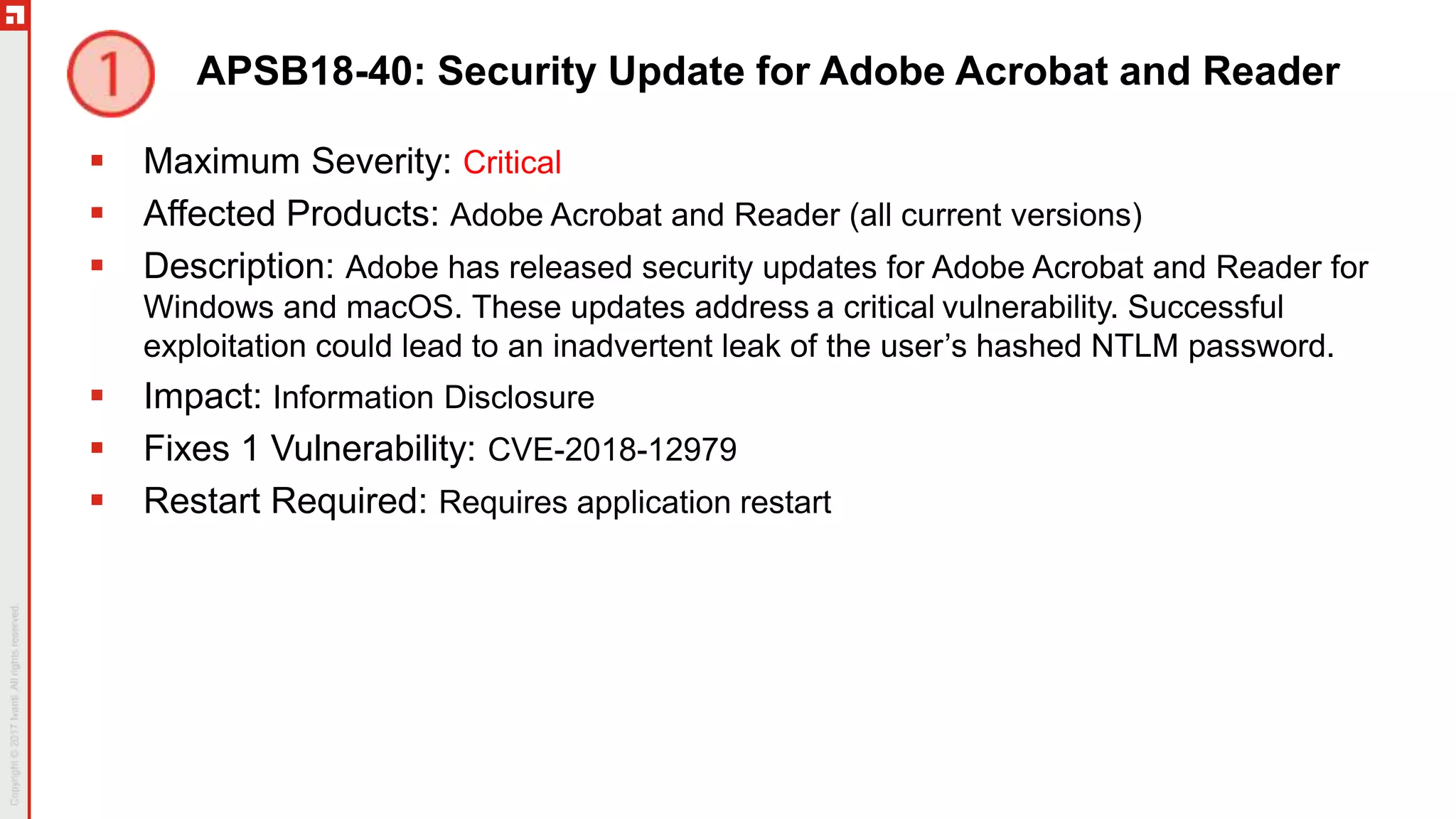
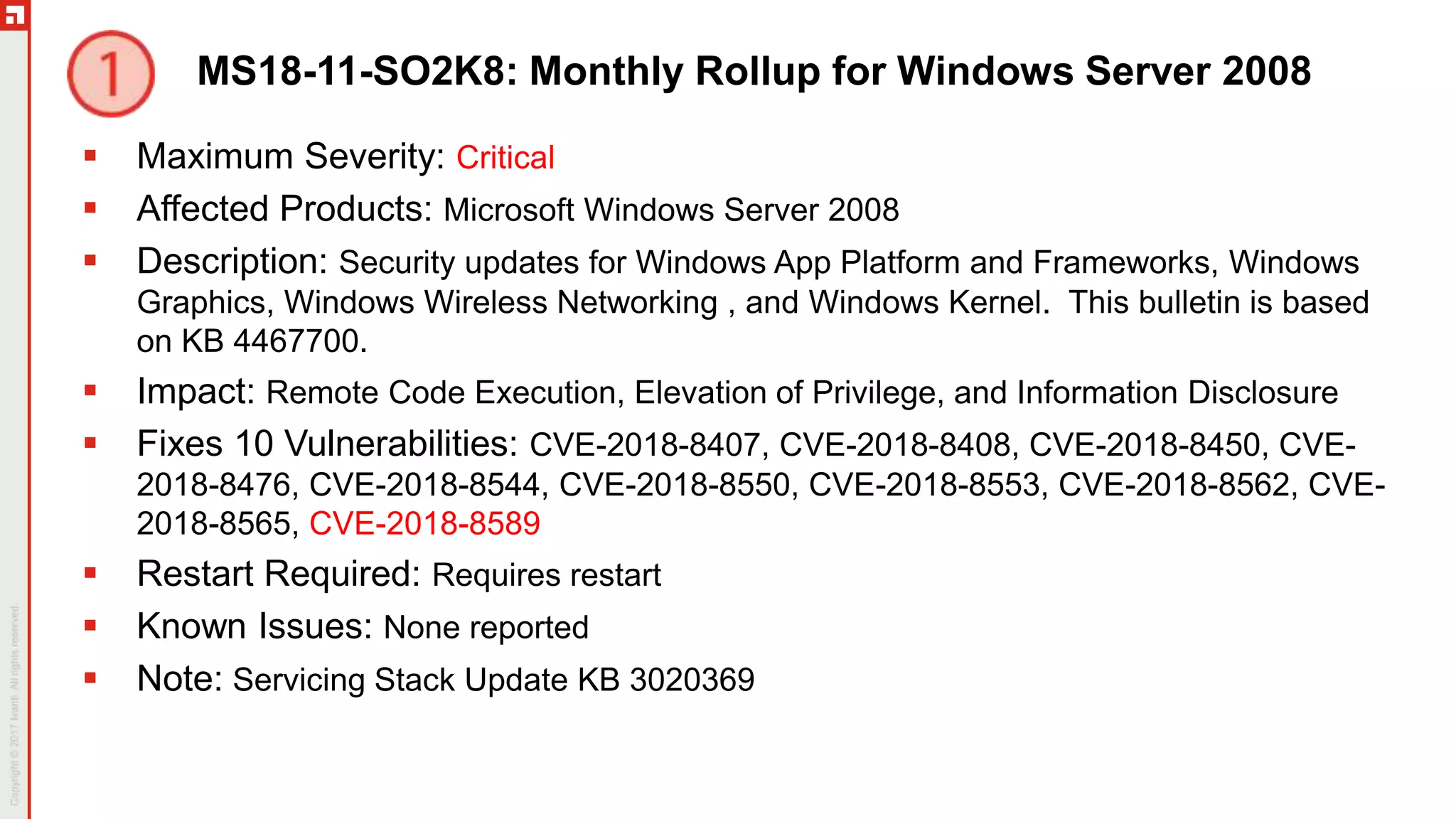
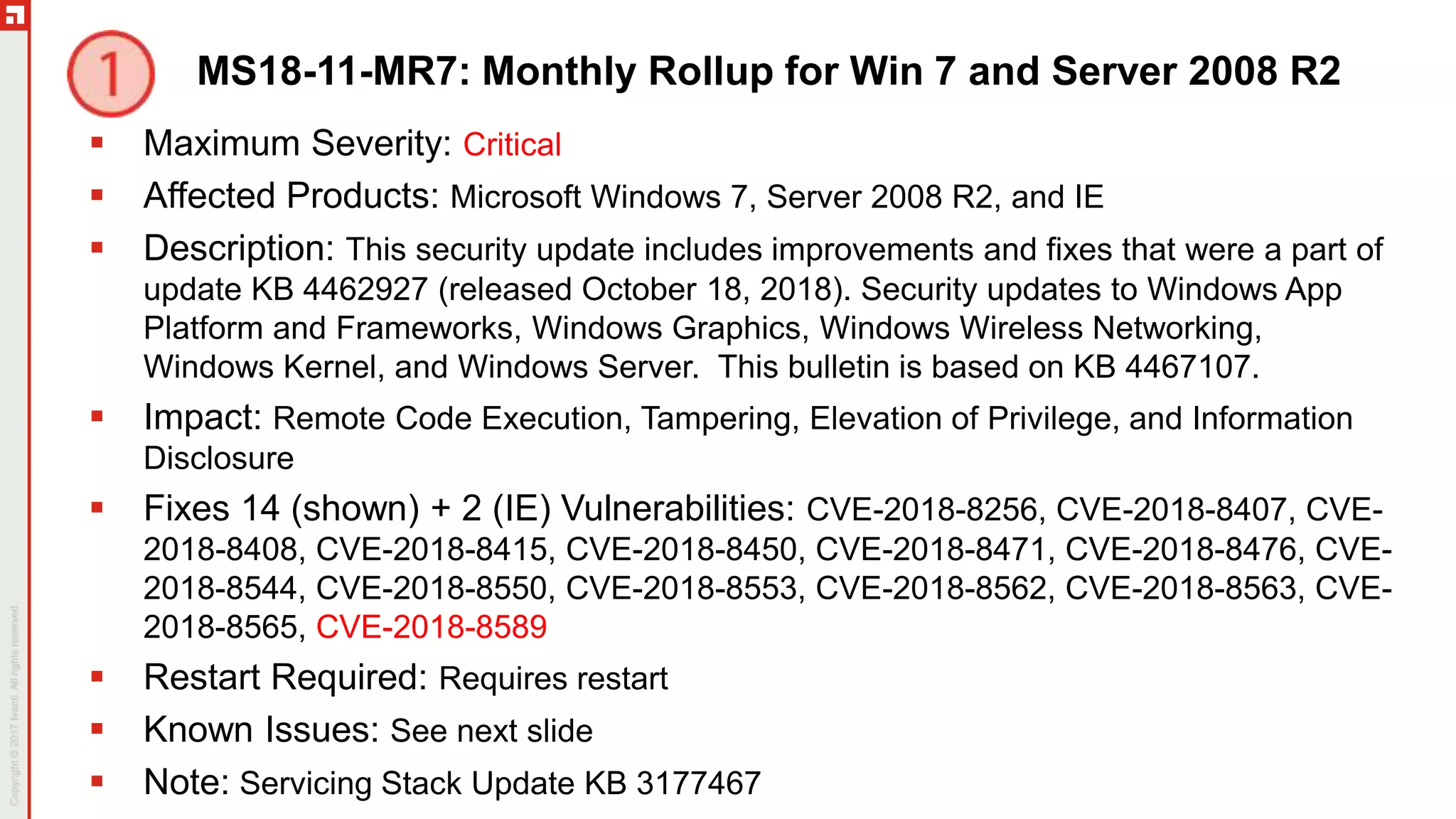
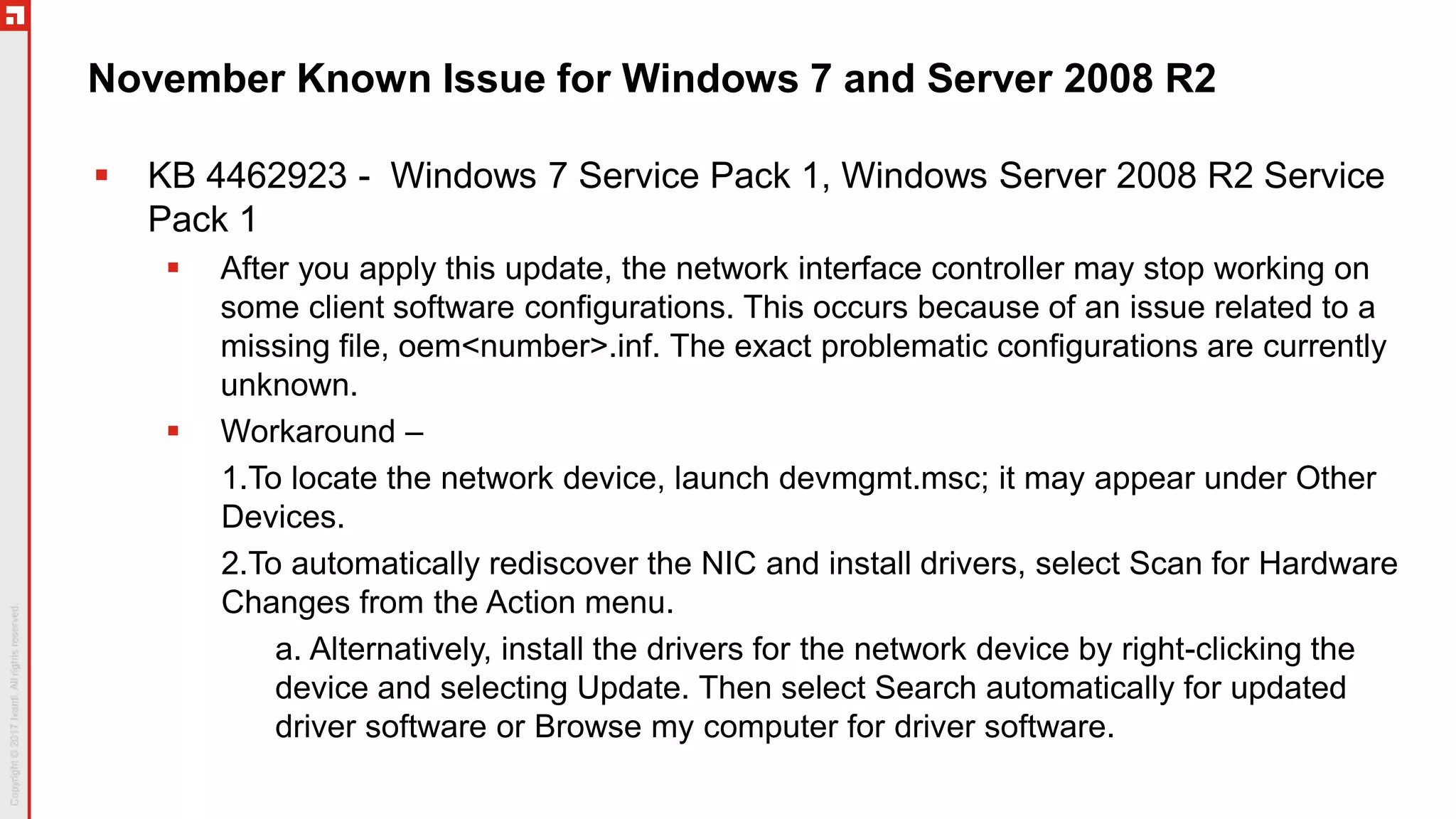
The document provides a comprehensive overview of the November 2018 Patch Tuesday, hosted by Chris Goettl and Todd Schell, discussing key updates, vulnerabilities, and issues in Microsoft products. It highlights specific vulnerabilities such as CVE-2018-8566 impacting BitLocker security and mitigations applied for various speculative execution vulnerabilities. The document also details the cessation of Microsoft's hotfix service, updated Windows versions, and various known issues affecting different Microsoft operating systems.







![New Microsoft Announcements
Windows 10, Version 1809 Released Again!
https://cloudblogs.microsoft.com/windowsserver/2018/11/13/update-on-windows-
server-2019-availability/
Fixes Known Major Issues
Deletion of files in C:/Users/[username]/Documents/
Compatibility issue with Intel Display Audio device drivers
Incorrect CPU usage reported in Task Manager
Issues opening compressed files
New Latest Cumulative Update (LCU) update file
Still some issues
Mapped network drives don’t connect
https://support.microsoft.com/en-us/help/4471218/mapped-network-drives-don-t-
work-in-windows-10-version-1809
Workaround – Scripts in article](https://image.slidesharecdn.com/nov2018patchtuesdayivanti-181114225835/75/November-Patch-Tuesday-Analysis-8-2048.jpg)