The June 2020 Patch Tuesday webinar discussed important Microsoft security updates, including advisories for critical vulnerabilities in Windows and Adobe Flash Player, and emphasized the necessity of continuous vulnerability management. The session highlighted various updates across multiple Microsoft products, potential impacts including remote code execution, and known issues associated with updates. Participants were encouraged to stay informed through community forums and subscribe to product announcements for timely notifications.













![Copyright©2019Ivanti.Allrightsreserved
June Known Issues for Windows 10
KB 4561616 – Windows 10, Version 1607 and Server 2016
[Min Password] After installing KB4467684, the cluster service may fail to start with the error
“2245 (NERR_PasswordTooShort)” if the group policy “Minimum Password Length” is
configured with greater than 14 characters. Workaround: Set the domain default "Minimum
Password Length" policy to less than or equal to 14 characters. Microsoft is working on a
resolution.
KB 4561608 – Windows 10, Version 1809, Server 2019 All Versions
[Asian Packs] After installing KB 4493509, devices with some Asian language packs installed
may receive the error, "0x800f0982 - PSFX_E_MATCHING_COMPONENT_NOT_FOUND.“
Workaround: Uninstall and reinstall any recently added language packs or select Check for
Updates and install the April 2019 Cumulative Update. See KB for more recovery details.
Microsoft is working on a resolution.](https://image.slidesharecdn.com/june2020patchtuesdayivanti-200610172456/85/Ivanti-Patch-Tuesday-for-June-2020-18-320.jpg)
![Copyright©2019Ivanti.Allrightsreserved
June Known Issues for Windows 10 (cont)
KB 4560960 – Windows 10 version 1903, Windows Server version 1903,
Windows 10 version 1909, Windows Server version 1909
[Modem] After installing this update on a Windows 10 device with a wireless wide area network
(WWAN) LTE modem, reaching the internet might not be possible. However, the Network
Connectivity Status Indicator (NCSI) in the notification area might still indicate that you are
connected to the internet. Workaround: None. Microsoft is working on a resolution.](https://image.slidesharecdn.com/june2020patchtuesdayivanti-200610172456/85/Ivanti-Patch-Tuesday-for-June-2020-19-320.jpg)
![Copyright©2019Ivanti.Allrightsreserved
MS20-06-MR2K8-ESU: Monthly Rollup for Windows Server 2008
Maximum Severity: Critical
Affected Products: Microsoft Windows Server 2008 and IE 9
Description: This security update includes improvements and fixes that were a part of
update KB 4556860 (released May 12, 2020). Bulletin is based on KB 4561670.
Security updates to Windows App Platform and Frameworks, Windows Kernel,
Microsoft Graphics Component, Windows Input and Composition, Windows Media,
Windows Cloud Infrastructure, Windows Peripherals, Windows File Server and
Clustering, Windows Hybrid Storage Services, the Microsoft Scripting Engine, and the
Microsoft JET Database Engine.
Impact: Remote Code Execution, Denial of Service, Elevation of Privilege, and
Information Disclosure
Fixes 26 + 7 (IE 9) Vulnerabilities: No CVEs are publicly disclosed or known
exploited. See the Security Update Guide for the complete list of CVEs.
Restart Required: Requires restart
Known Issues: [ESU Fail] See next slide.](https://image.slidesharecdn.com/june2020patchtuesdayivanti-200610172456/85/Ivanti-Patch-Tuesday-for-June-2020-21-320.jpg)
![Copyright©2019Ivanti.Allrightsreserved
June Known Issues for Server 2008
KB 4561670 – Windows Server 2008 (Monthly Rollup)
[ESU Fail] After installing this update and restarting your device, you might receive the error,
“Failure to configure Windows updates. Reverting Changes. Do not turn off your computer”, and
the update might show as Failed in Update History.
Workaround: This is expected in the following circumstances:
• If you are installing this update on a device that is running an edition that is not supported
for ESU. For a complete list of which editions are supported, see KB 4497181.
• If you do not have an ESU MAK add-on key installed and activated.
If you have purchased an ESU key and have encountered this issue, please verify you have
applied all prerequisites and that your key is activated.
https://support.microsoft.com/en-us/help/4522133/procedure-to-continue-receiving-security-
updates
KB 4561645 – Windows Server 2008 (Security-only Update)](https://image.slidesharecdn.com/june2020patchtuesdayivanti-200610172456/85/Ivanti-Patch-Tuesday-for-June-2020-22-320.jpg)
![Copyright©2019Ivanti.Allrightsreserved
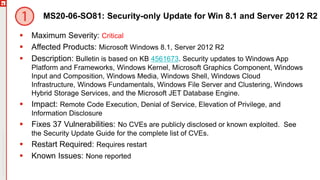
MS20-06-SO2K8-ESU: Security-only Update for Windows Server 2008
Maximum Severity: Critical
Affected Products: Microsoft Windows Server 2008
Description: This bulletin is based on KB 4561645. Security updates to Windows App
Platform and Frameworks, Windows Kernel, Microsoft Graphics Component, Windows
Input and Composition, Windows Media, Windows Cloud Infrastructure, Windows
Peripherals, Windows File Server and Clustering, Windows Hybrid Storage Services,
and the Microsoft JET Database Engine.
Impact: Remote Code Execution, Denial of Service, Elevation of Privilege, and
Information Disclosure
Fixes 26 Vulnerabilities: No CVEs are publicly disclosed or known exploited. See
the Security Update Guide for the complete list of CVEs.
Restart Required: Requires restart
Known Issues: [ESU Fail]](https://image.slidesharecdn.com/june2020patchtuesdayivanti-200610172456/85/Ivanti-Patch-Tuesday-for-June-2020-23-320.jpg)
![Copyright©2019Ivanti.Allrightsreserved
MS20-06-MR7-ESU: Monthly Rollup for Win 7
MS20-06-MR2K8R2-ESU Monthly Rollup for Server 2008 R2
Maximum Severity: Critical
Affected Products: Microsoft Windows 7, Server 2008 R2, and IE
Description: This security update includes improvements and fixes that were a part of
update KB 4556836 (released May 12, 2020). Bulletin is based on KB 4561643.
Security updates to Windows App Platform and Frameworks, Windows Kernel,
Microsoft Graphics Component, Windows Input and Composition, Windows Media,
Windows Shell, Windows Cloud Infrastructure, Windows Fundamentals, Windows
Storage and Filesystems, Windows File Server and Clustering, Windows Hybrid Storage
Services, the Microsoft Scripting Engine, and the Microsoft JET Database Engine.
Impact: Remote Code Execution, Denial of Service, Elevation of Privilege, and
Information Disclosure
Fixes 30 + 8 IE Vulnerabilities: No CVEs are publicly disclosed or known exploited.
See the Security Update Guide for the complete list of CVEs.
Restart Required: Requires restart
Known Issues: [ESU Fail]](https://image.slidesharecdn.com/june2020patchtuesdayivanti-200610172456/85/Ivanti-Patch-Tuesday-for-June-2020-24-320.jpg)
![Copyright©2019Ivanti.Allrightsreserved
MS20-06-SO7-ESU: Security-only Update for Win 7
MS20-06-SO2K8R2-ESU: Security-only Update for Server 2008 R2
Maximum Severity: Critical
Affected Products: Microsoft Windows 7 SP1, Server 2008 R2 SP1
Description: Bulletin is based on KB 4561669. Security updates to Windows App
Platform and Frameworks, Windows Kernel, Microsoft Graphics Component, Windows
Input and Composition, Windows Media, Windows Shell, Windows Cloud
Infrastructure, Windows Fundamentals, Windows Storage and Filesystems, Windows
File Server and Clustering, Windows Hybrid Storage Services, and the Microsoft JET
Database Engine.
Impact: Remote Code Execution, Denial of Service, Elevation of Privilege, and
Information Disclosure
Fixes 30 Vulnerabilities: No CVEs are publicly disclosed or known exploited. See
the Security Update Guide for the complete list of CVEs.
Restart Required: Requires restart
Known Issues: [ESU Fail]](https://image.slidesharecdn.com/june2020patchtuesdayivanti-200610172456/85/Ivanti-Patch-Tuesday-for-June-2020-25-320.jpg)