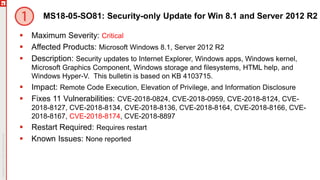
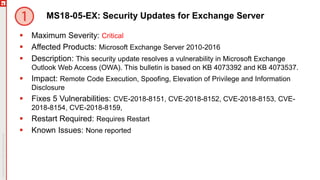
The document is a summary of the May 2018 Patch Tuesday webinar, detailing an overview of vulnerabilities, updates, and known issues for various Microsoft products. Key vulnerabilities include remote code execution risks in Windows components and Internet Explorer, with several critical updates released to address these security concerns. The document emphasizes the importance of updating to the latest versions of Windows 10 and notes service end dates for unsupported versions.