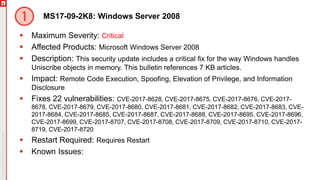
The document provides an overview of a Patch Tuesday webinar that took place on September 13, 2017, discussing significant security vulnerabilities and updates for various Microsoft products. It highlights notable breaches, including the Equifax breach, and outlines the severity and impact of several disclosed vulnerabilities. Specific Microsoft updates addressing these vulnerabilities are detailed, including required actions and known issues related to installation.