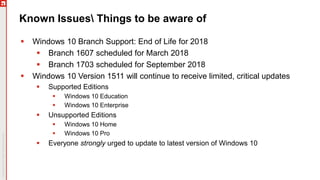
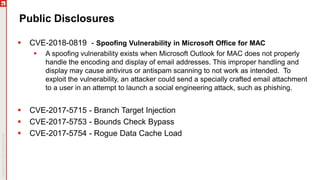
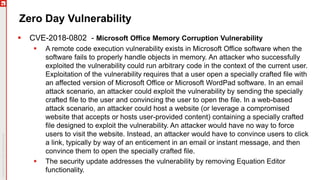
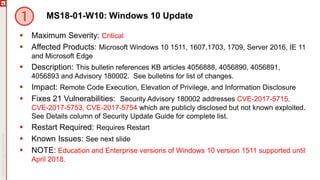
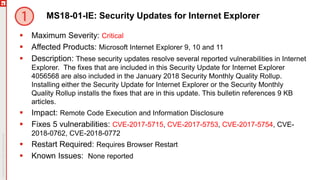
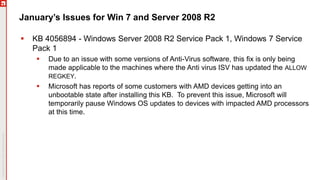
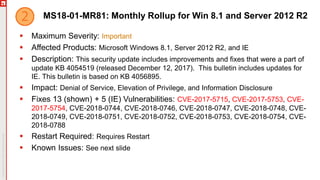
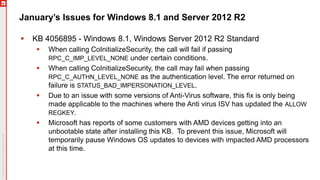
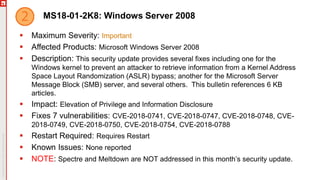
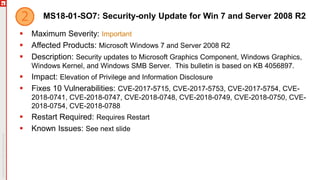
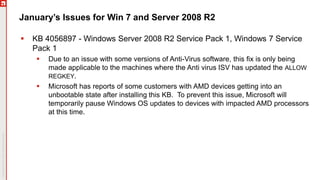
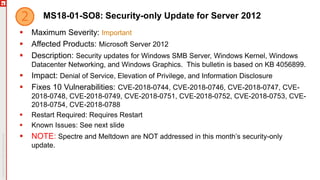
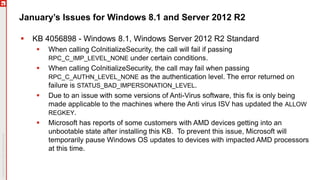
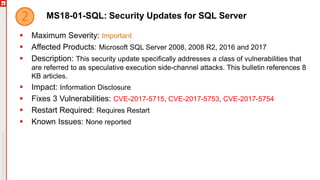
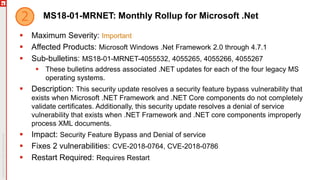
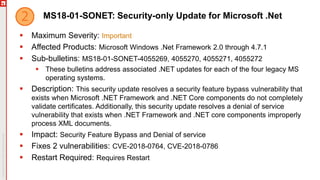
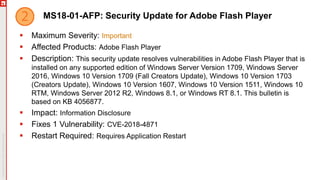
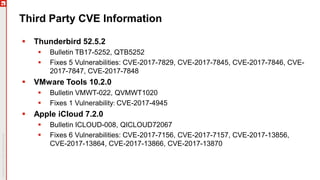
The January 2018 Patch Tuesday webinar outlined critical updates for various Microsoft products, including Windows 10, Microsoft Office, and Internet Explorer, addressing numerous vulnerabilities such as remote code execution and spoofing issues. Key noted vulnerabilities include CVE-2018-0802 in Office and ongoing concerns with AMD devices experiencing boot failures post-update. Attendees were encouraged to ensure systems are upgraded to the latest versions and to monitor for related issues with antivirus software compatibility.