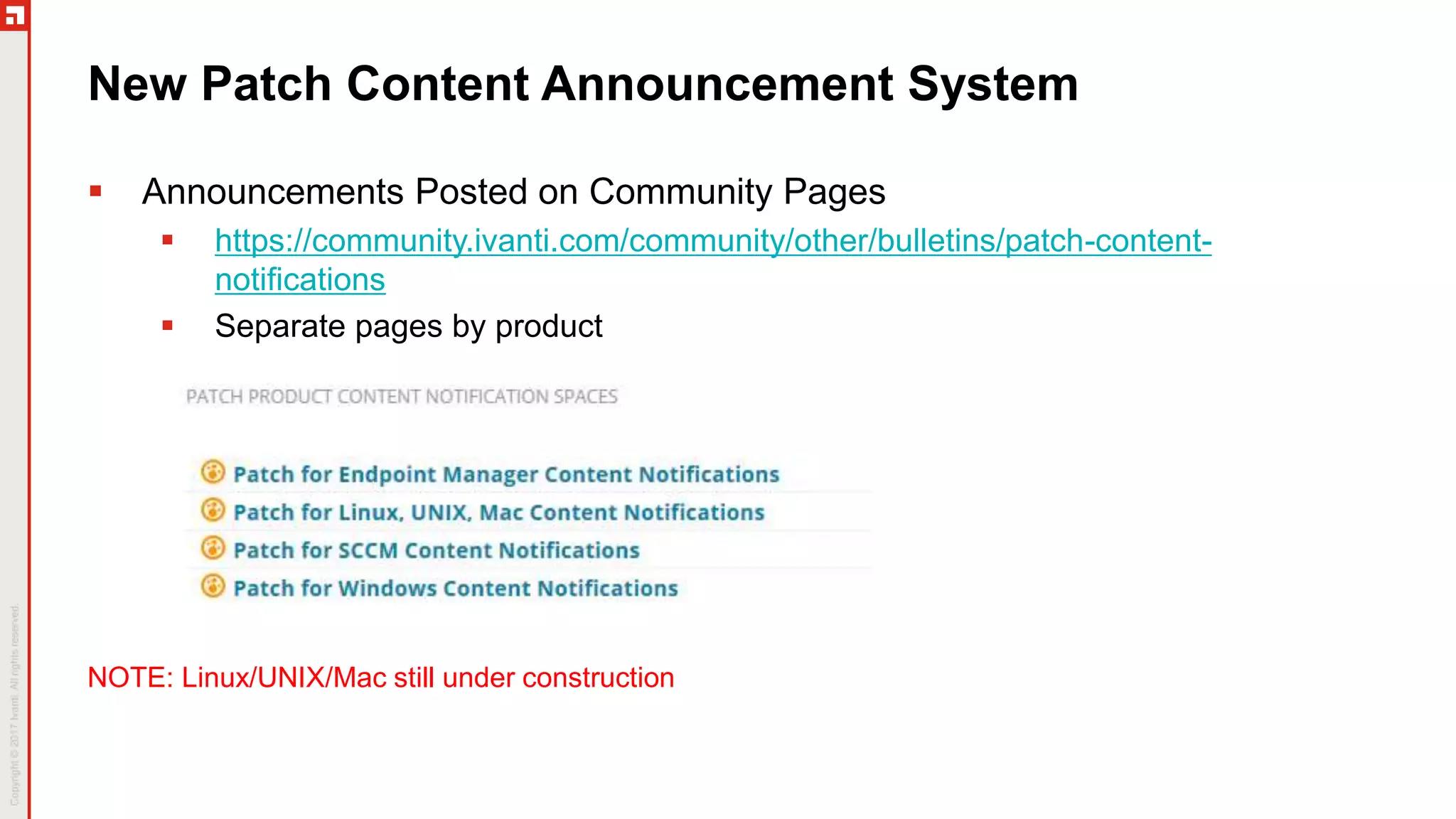
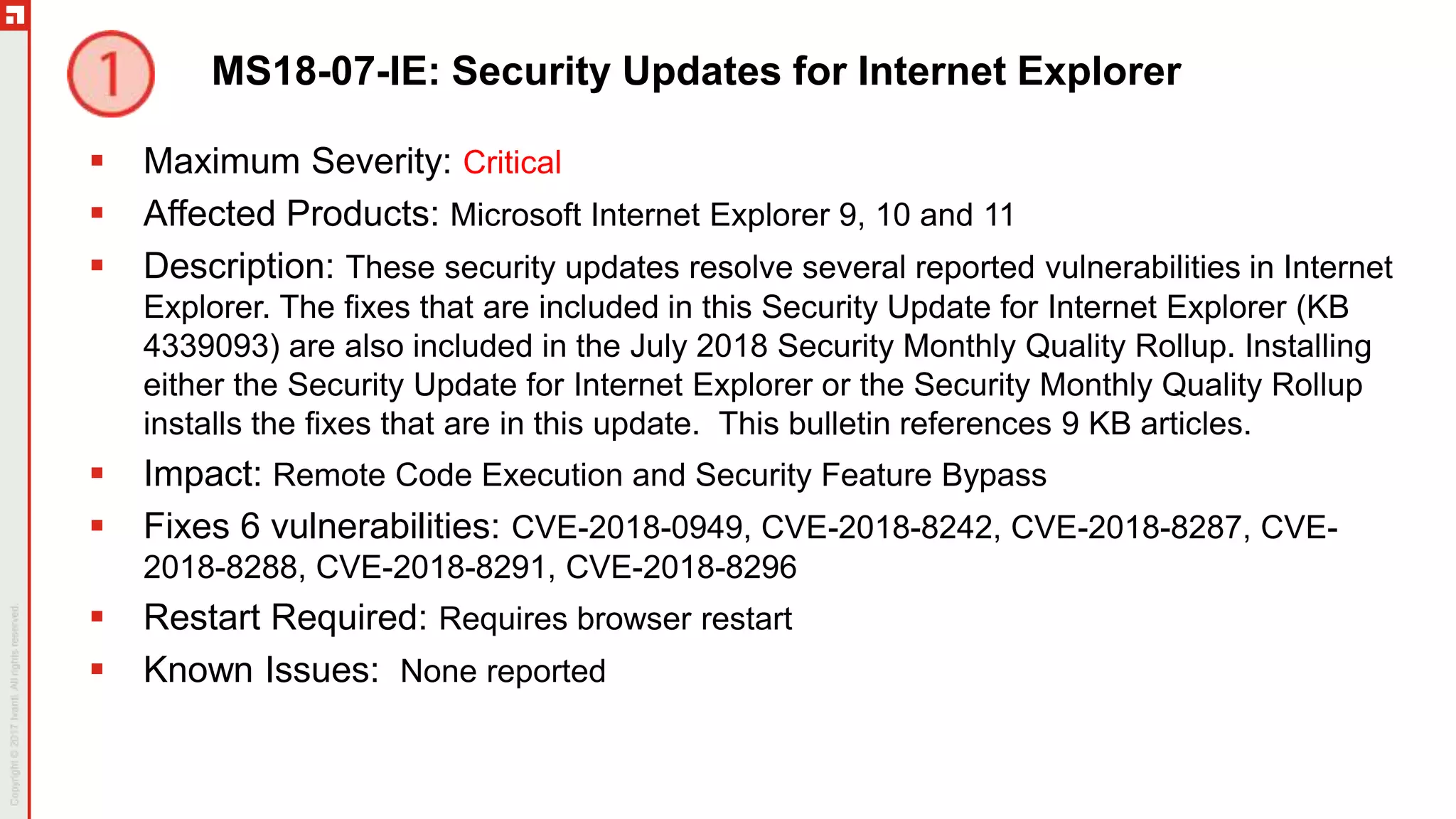
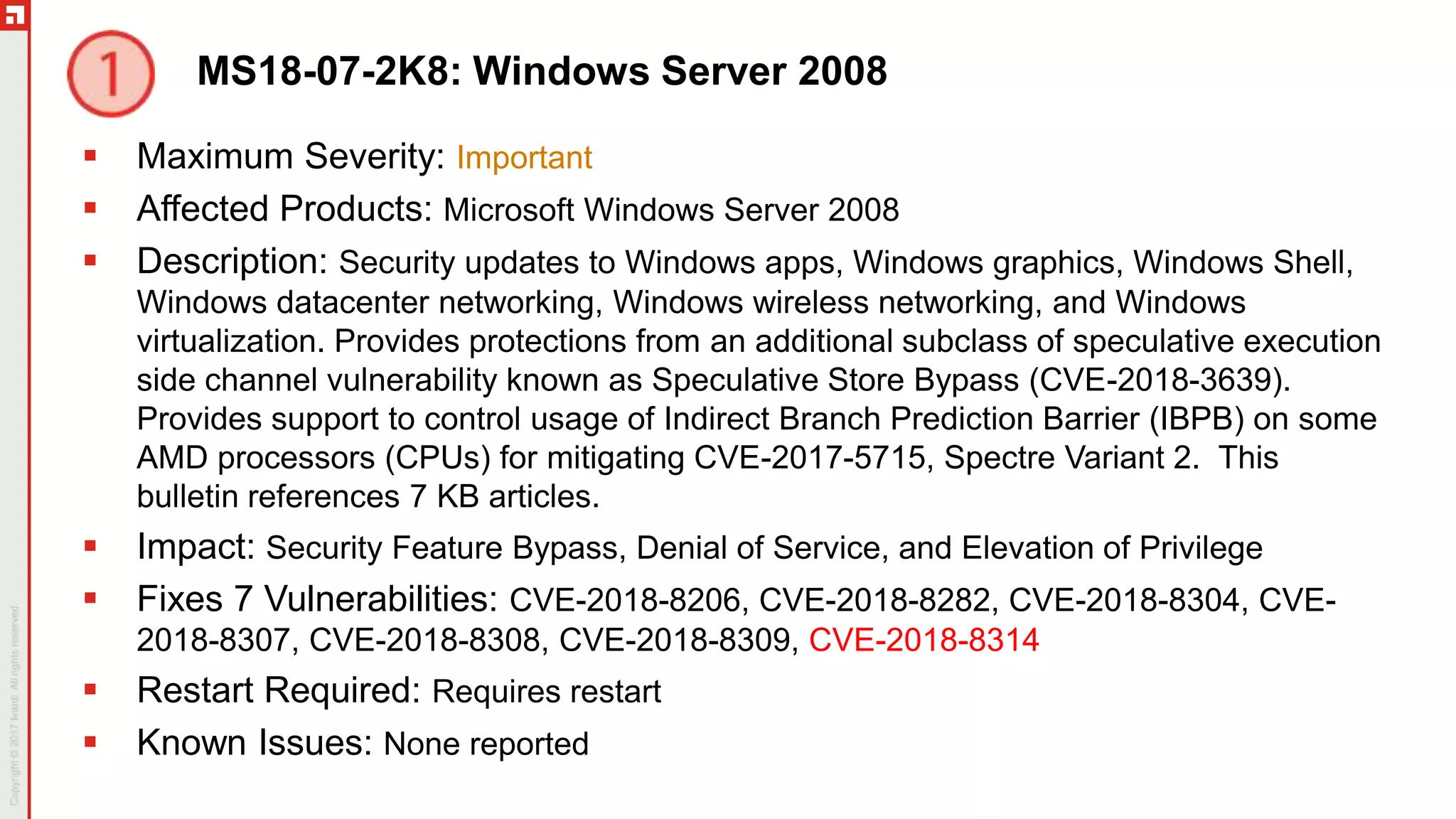
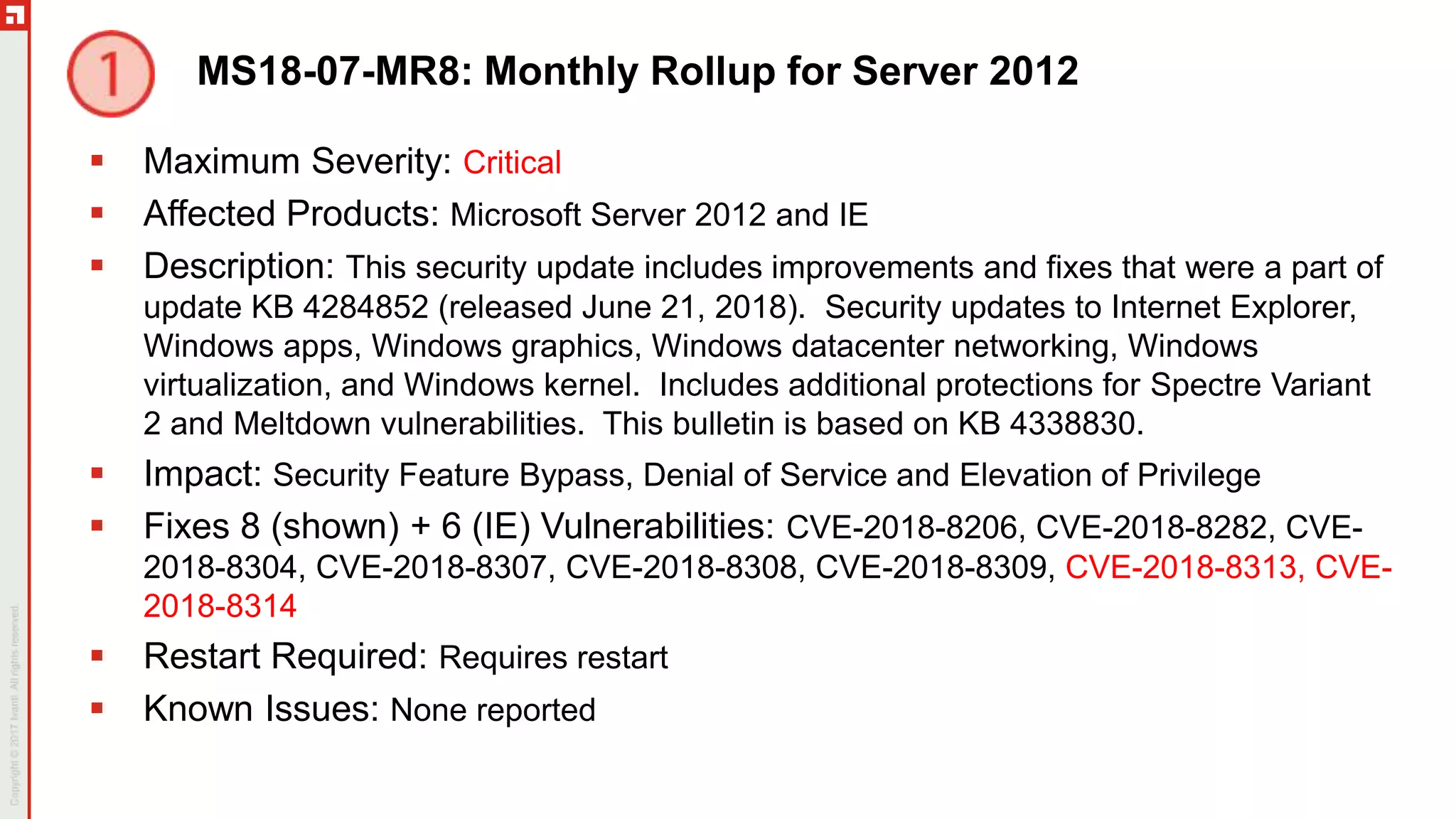
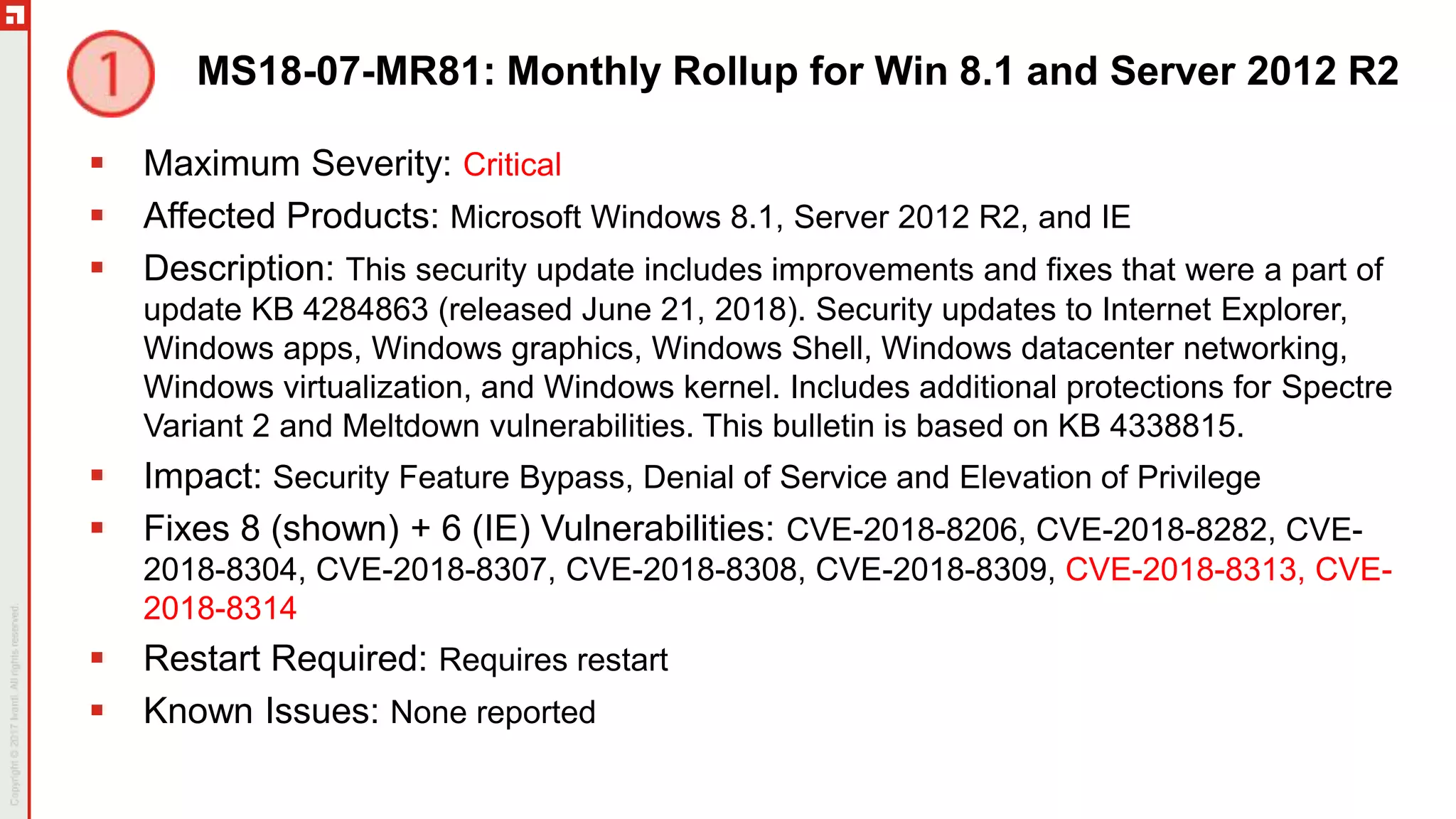
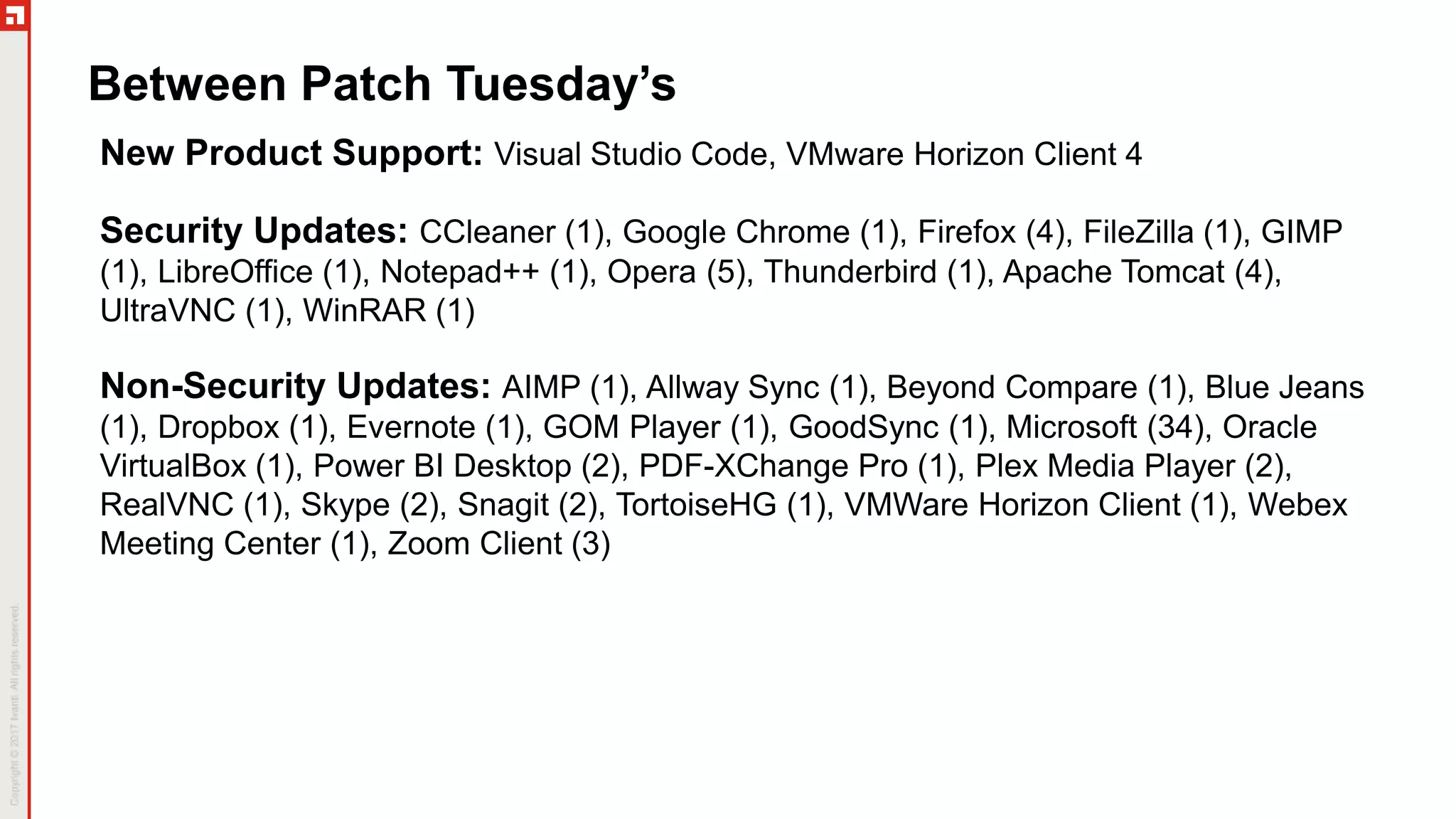
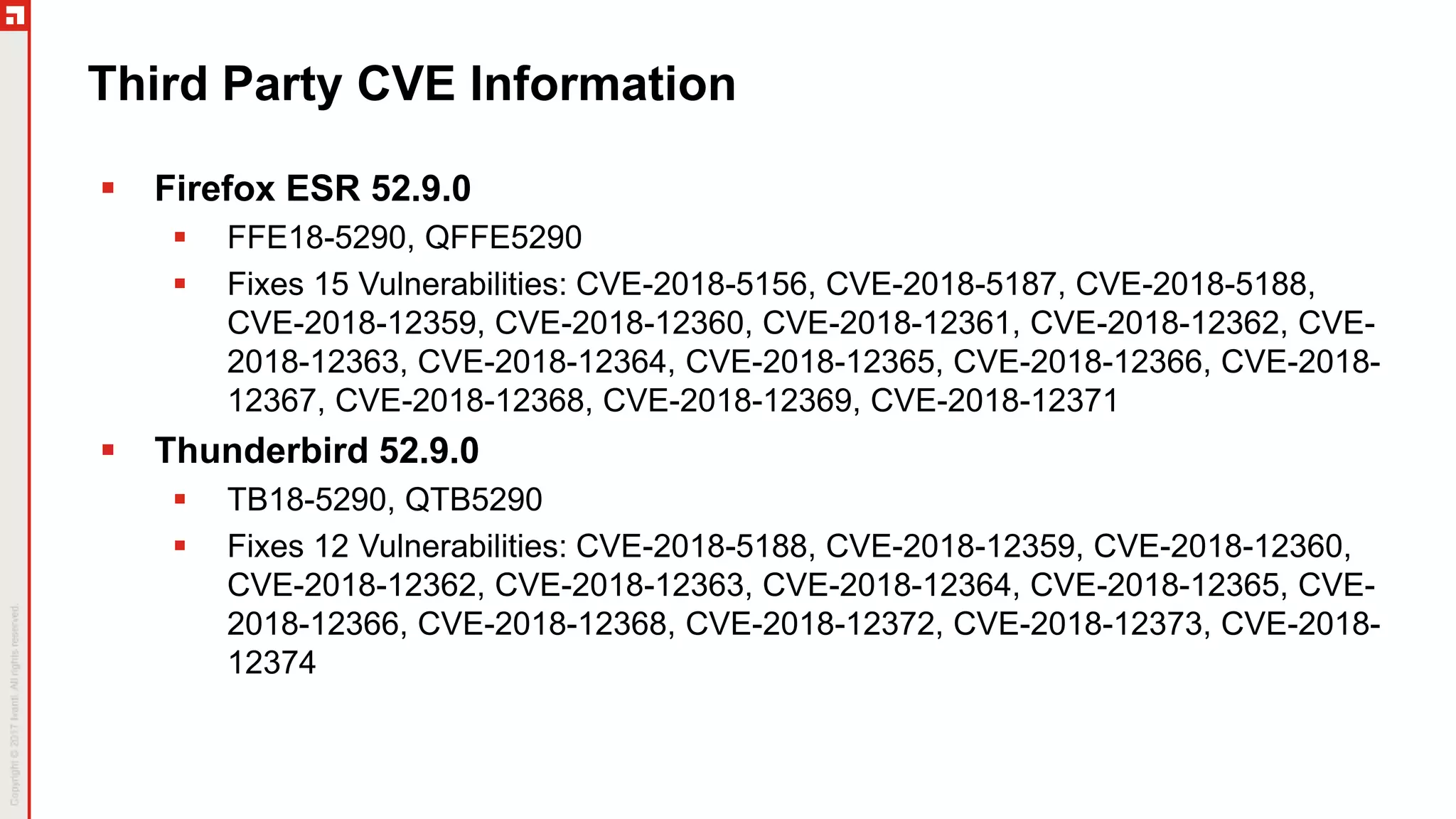
The document is a summary of the Patch Tuesday webinar held on July 11, 2018, detailing updates on vulnerabilities, guidance for mitigating risks related to Spectre and Meltdown, and notable updates across various Microsoft products. It details specific security vulnerabilities categorized by their CVE numbers along with the potential impacts and mitigation strategies. Additional updates on Adobe security fixes and issues related to Windows and third-party software are also highlighted.