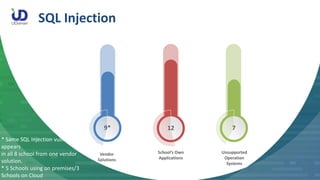
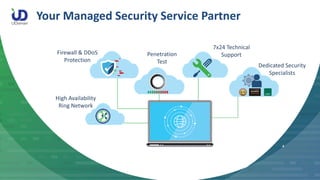
The document summarizes a school penetration testing project conducted by UDomain. They identified over 1,700 vulnerabilities across 10 school websites, including 20,000+ records of personal data. Critical vulnerabilities included SQL injection, XSS, and passwords in plaintext. Recommendations included more regular scanning, patching of outdated systems, and reliance on secure vendor solutions. UDomain demonstrated SQL injection techniques and explained their security services and qualifications.