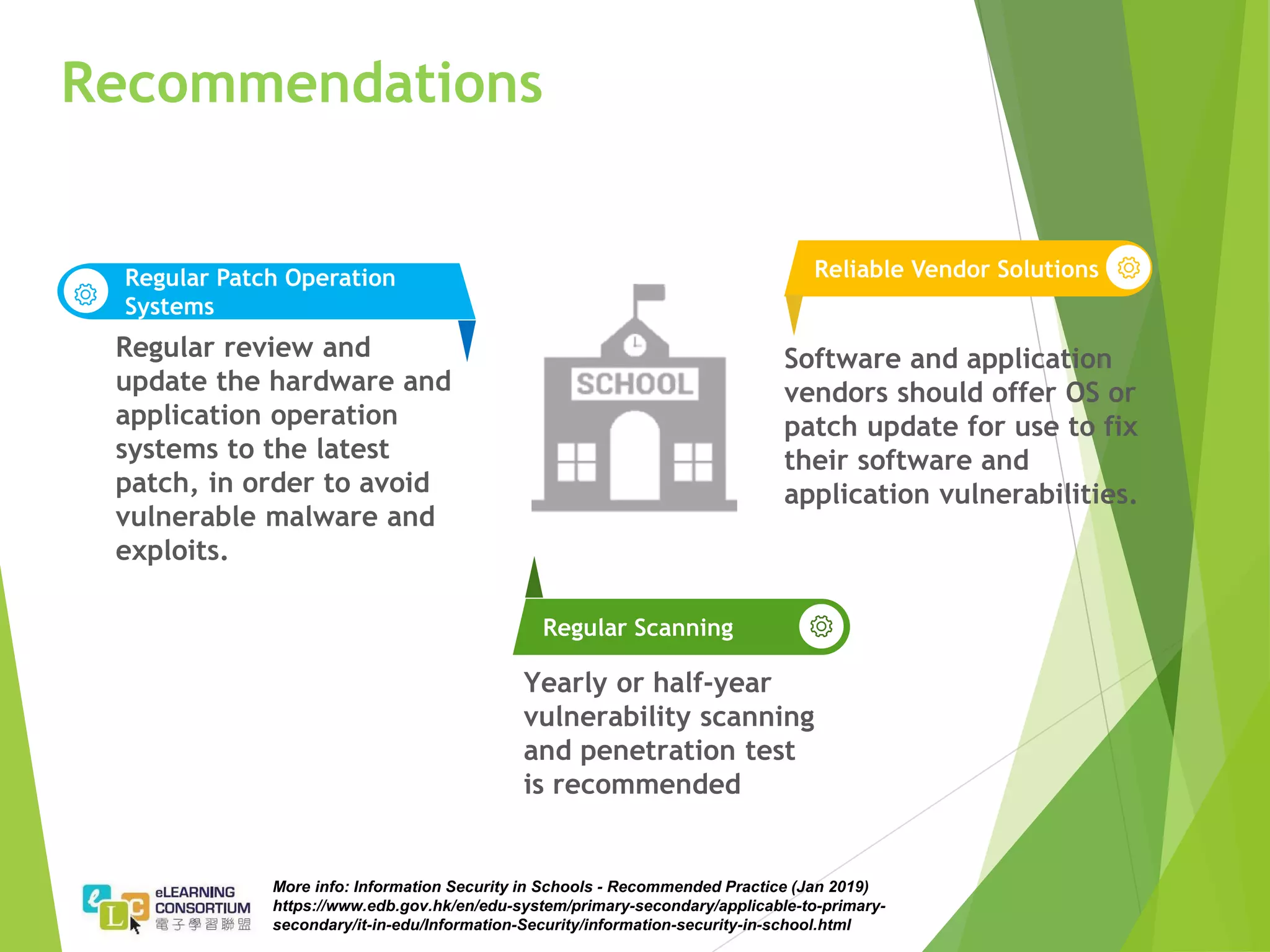
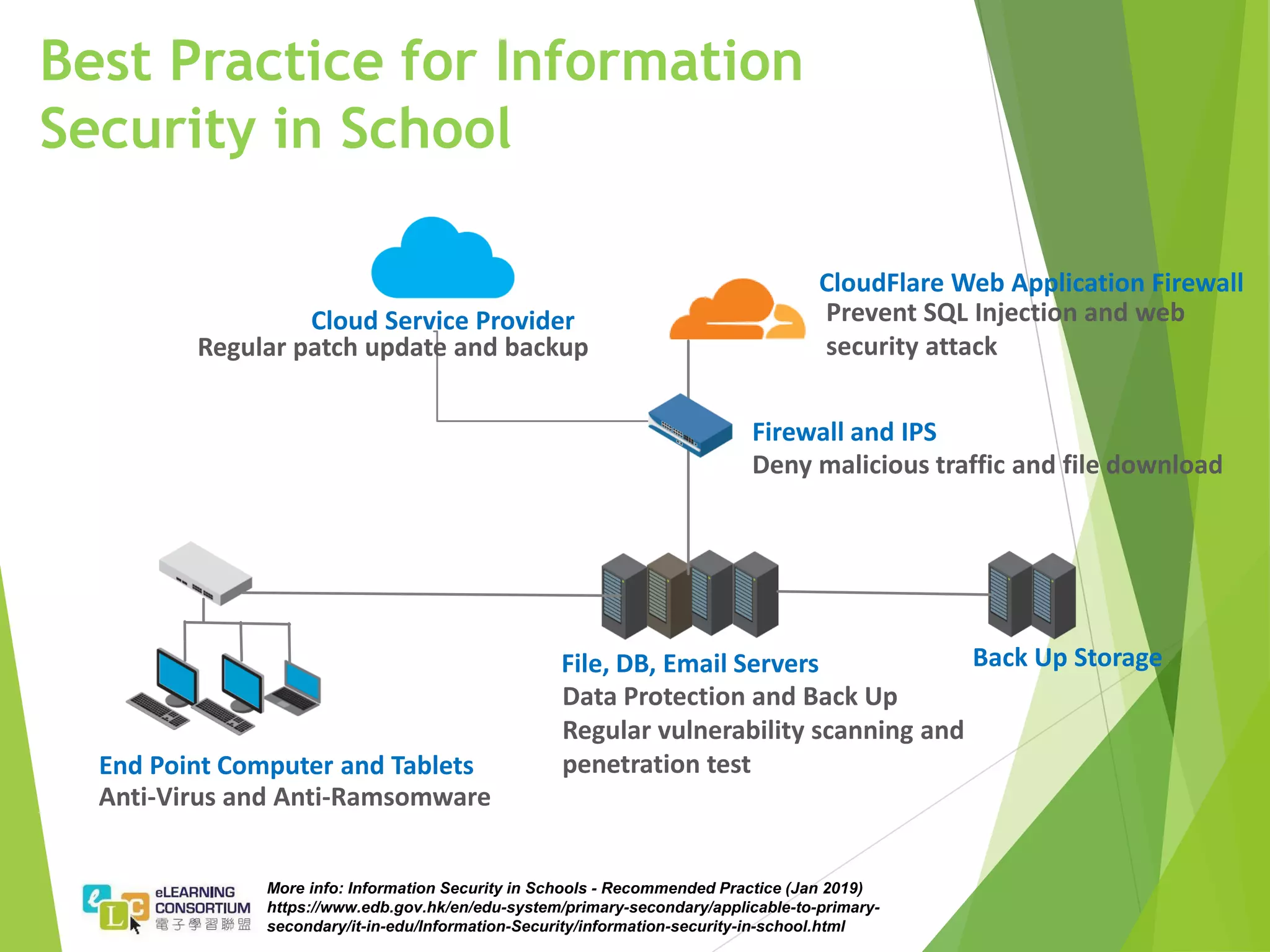
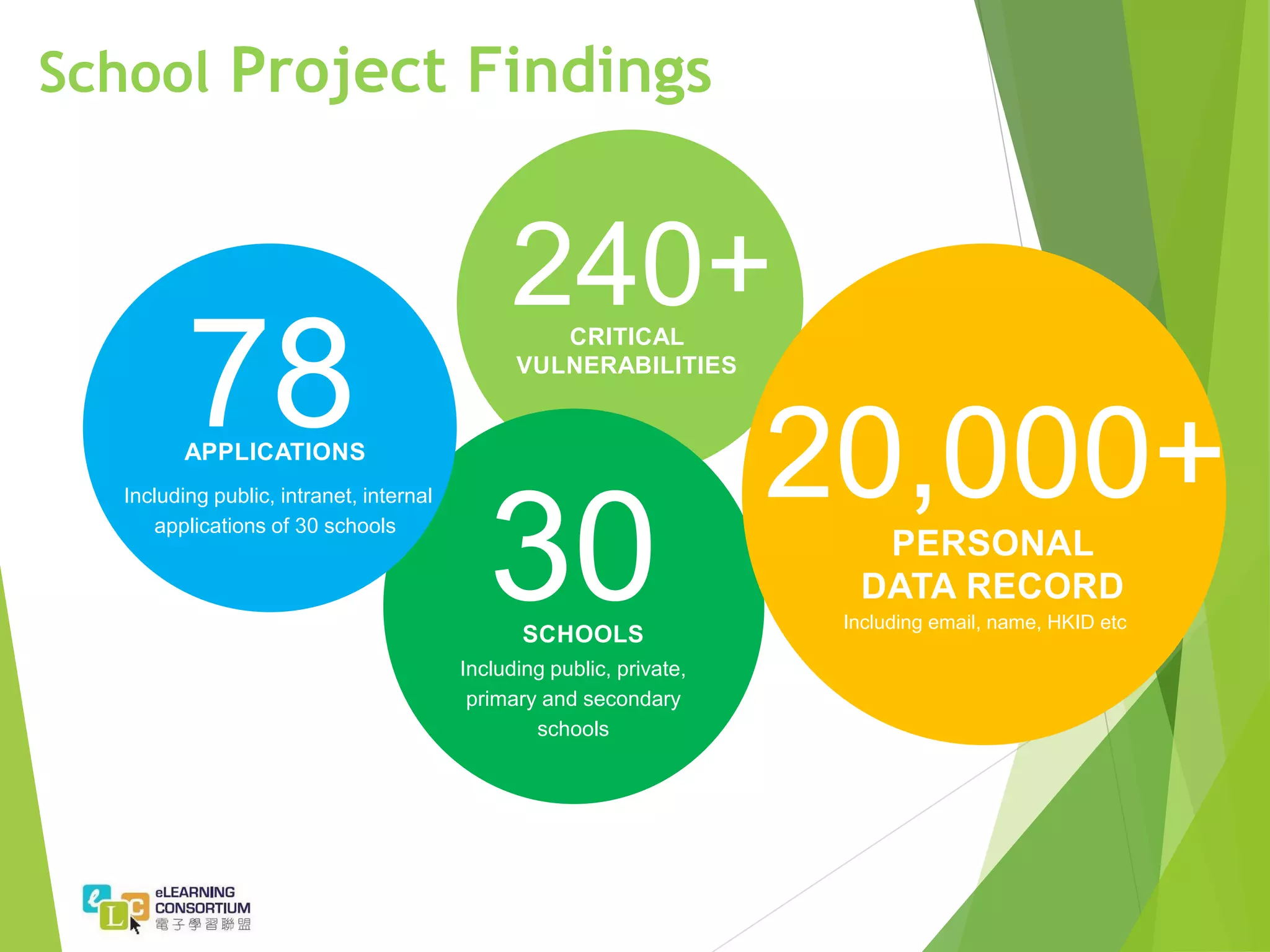
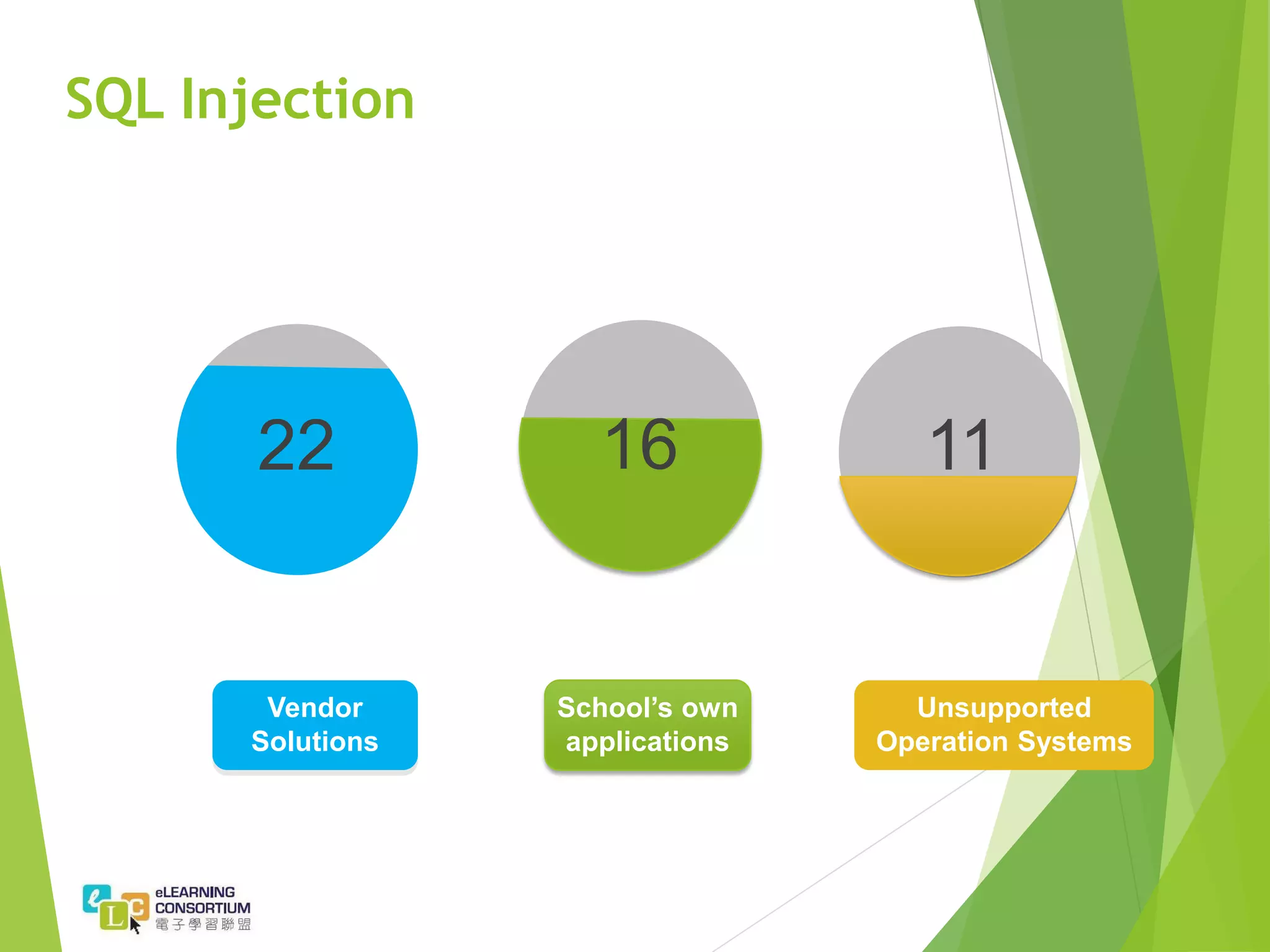
The document summarizes the findings of a penetration test project conducted on the websites and applications of over 30 schools. It identifies over 240 critical vulnerabilities across the schools, including exposed personal data, outdated software with known vulnerabilities, and SQL injection issues. Recommendations include encouraging software vendors to provide ongoing patches, implementing regular vulnerability scanning, and ensuring systems and software are regularly updated to the latest versions. Best practices for schools outlined in the document include implementing firewalls, regular backups, web application firewalls, and security awareness training for practitioners.







![SSL Cert
[CATEGORY
NAME]
[PERC
ENTAG
E]
[CATEGORY
NAME]
[PERC
ENTAG
E]](https://image.slidesharecdn.com/0301-2020-elcseminar-ericfan-final-200116041734/75/03-11-2048.jpg)