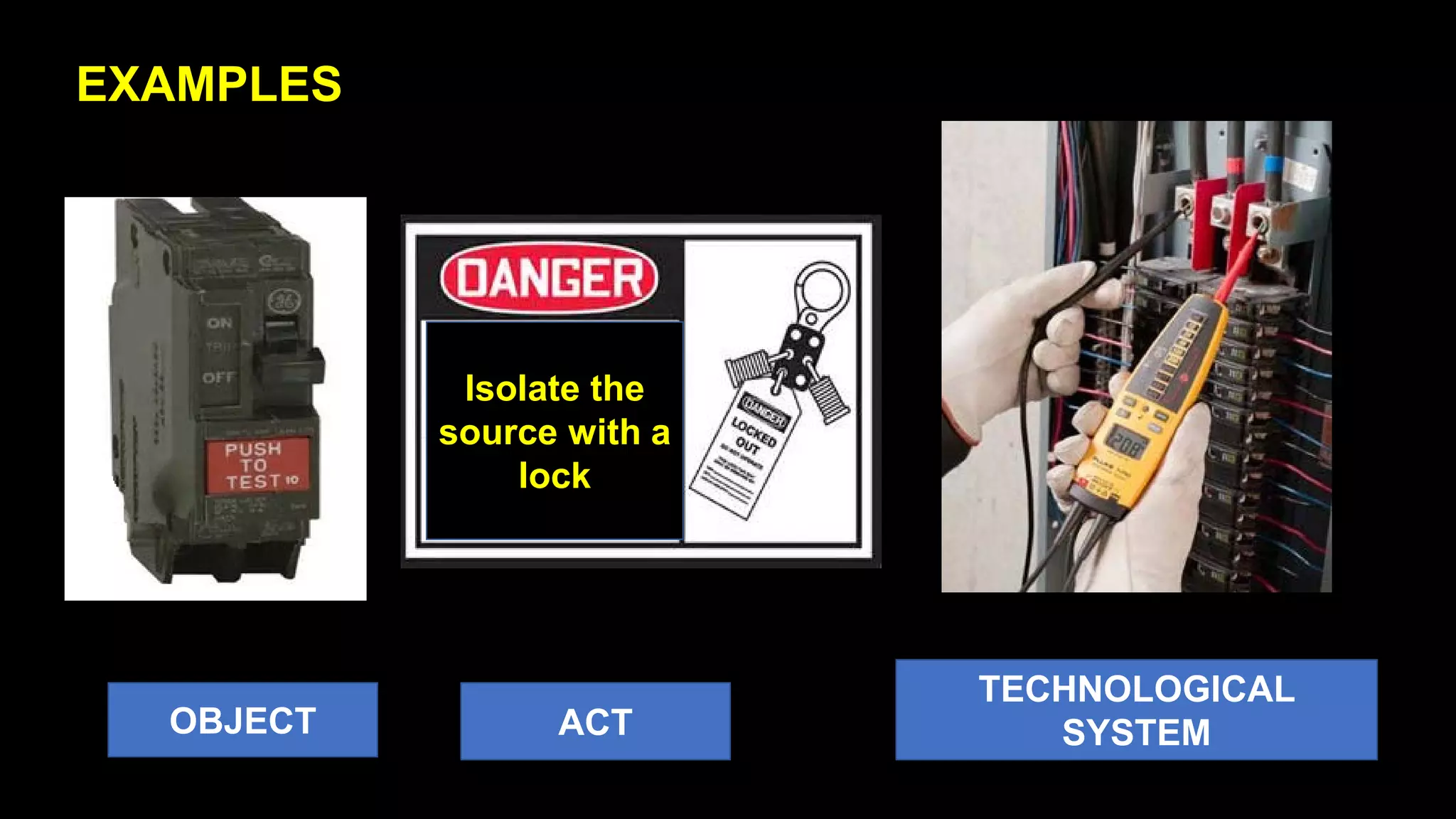
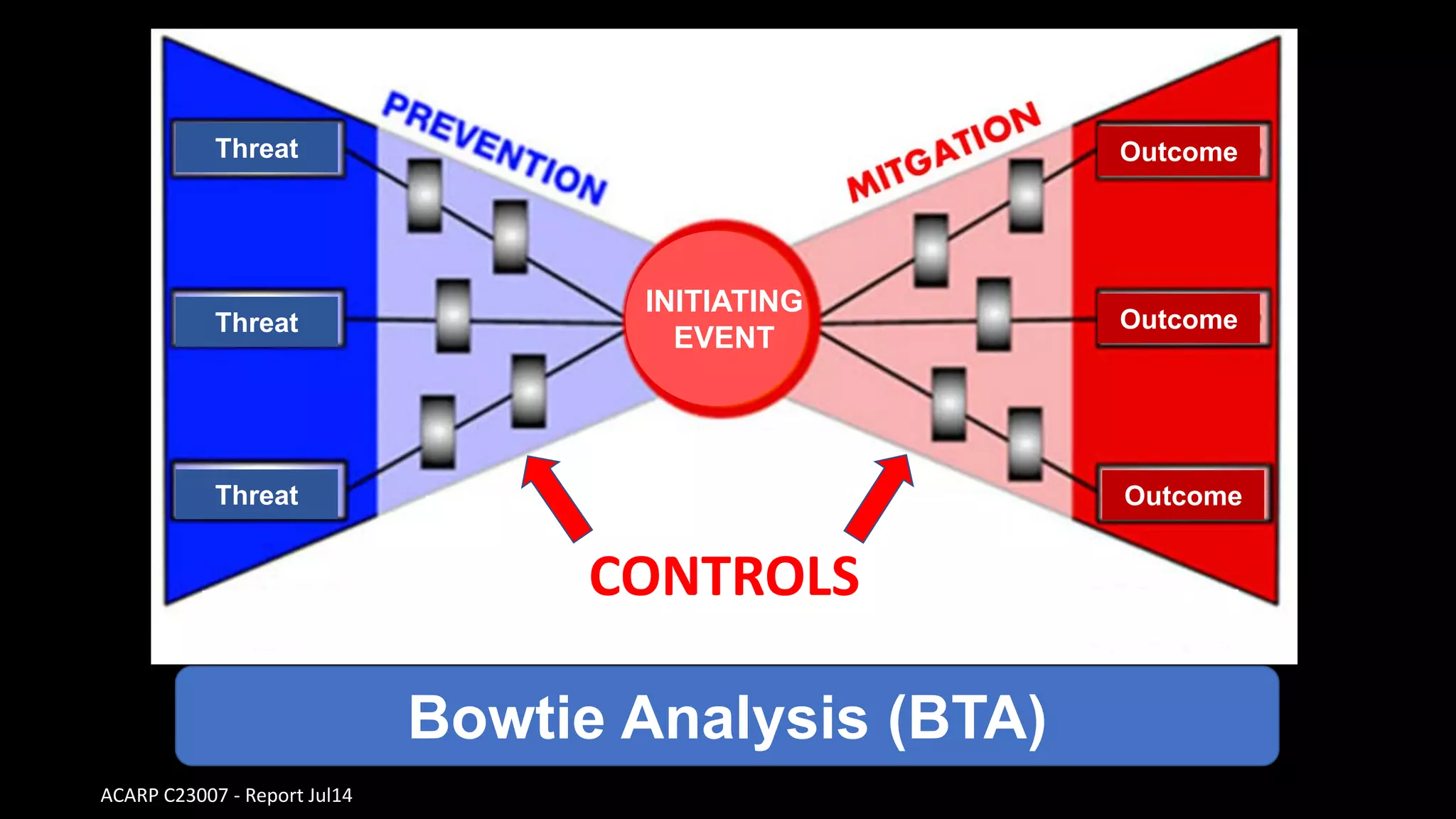
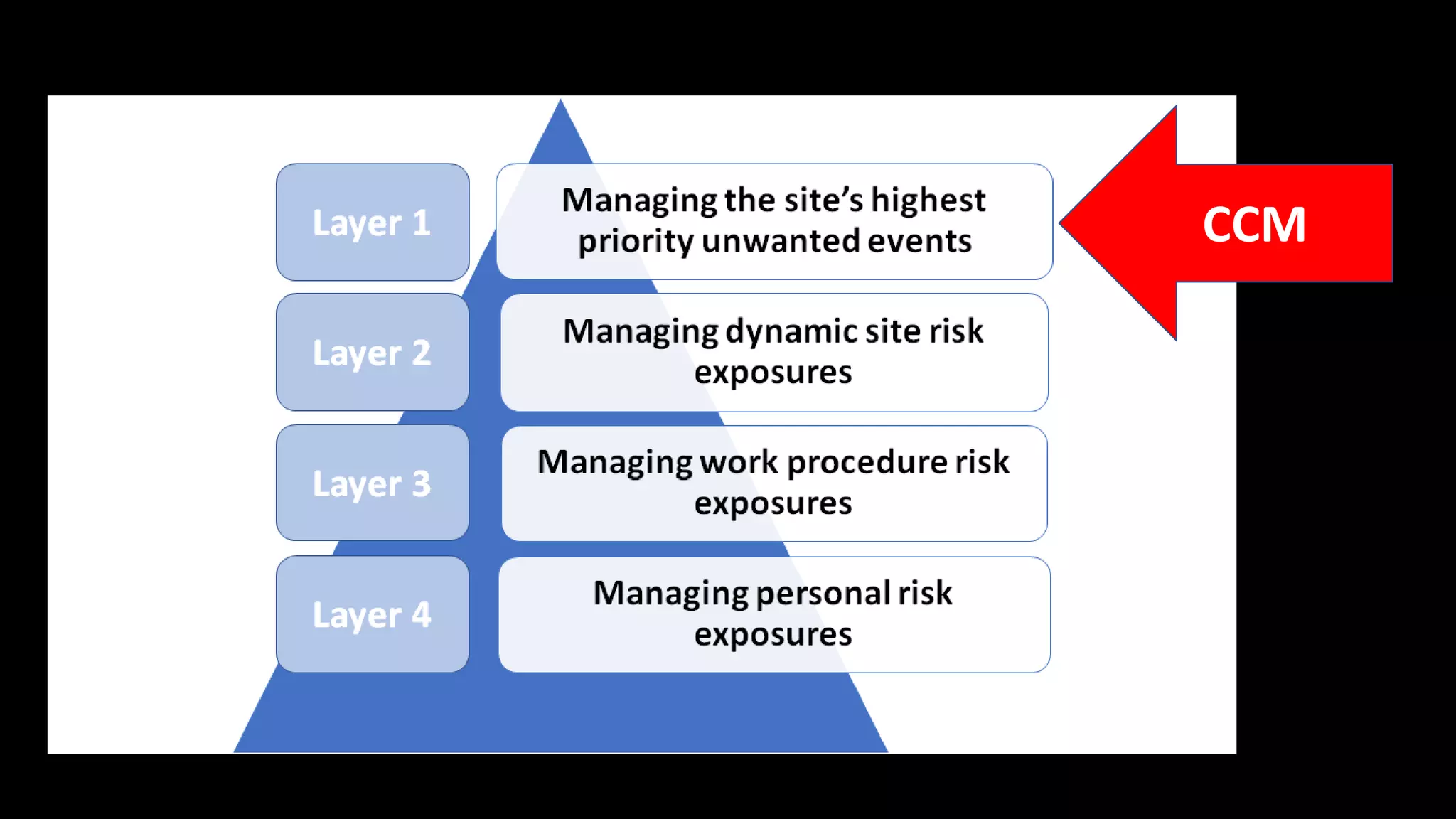
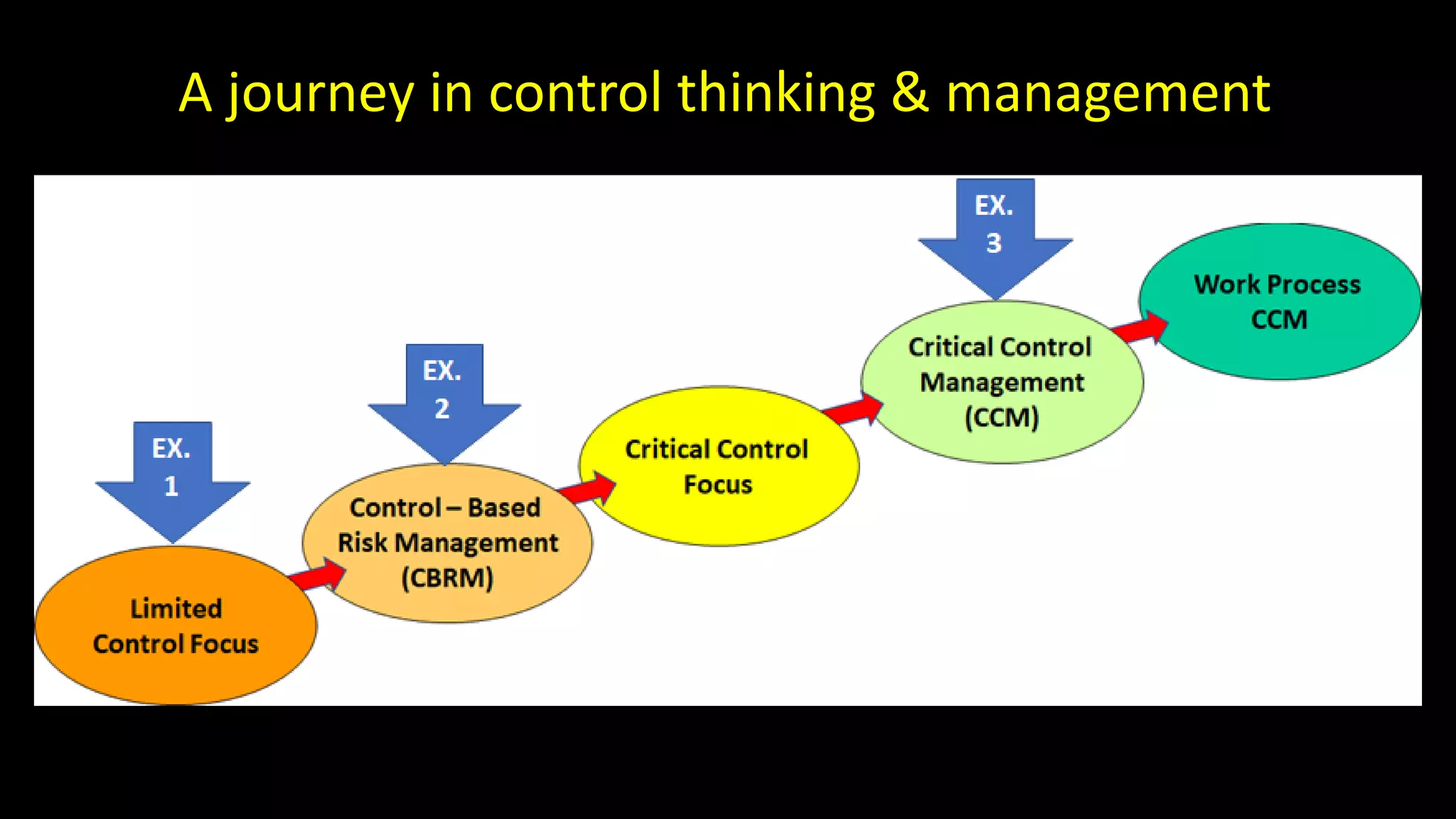
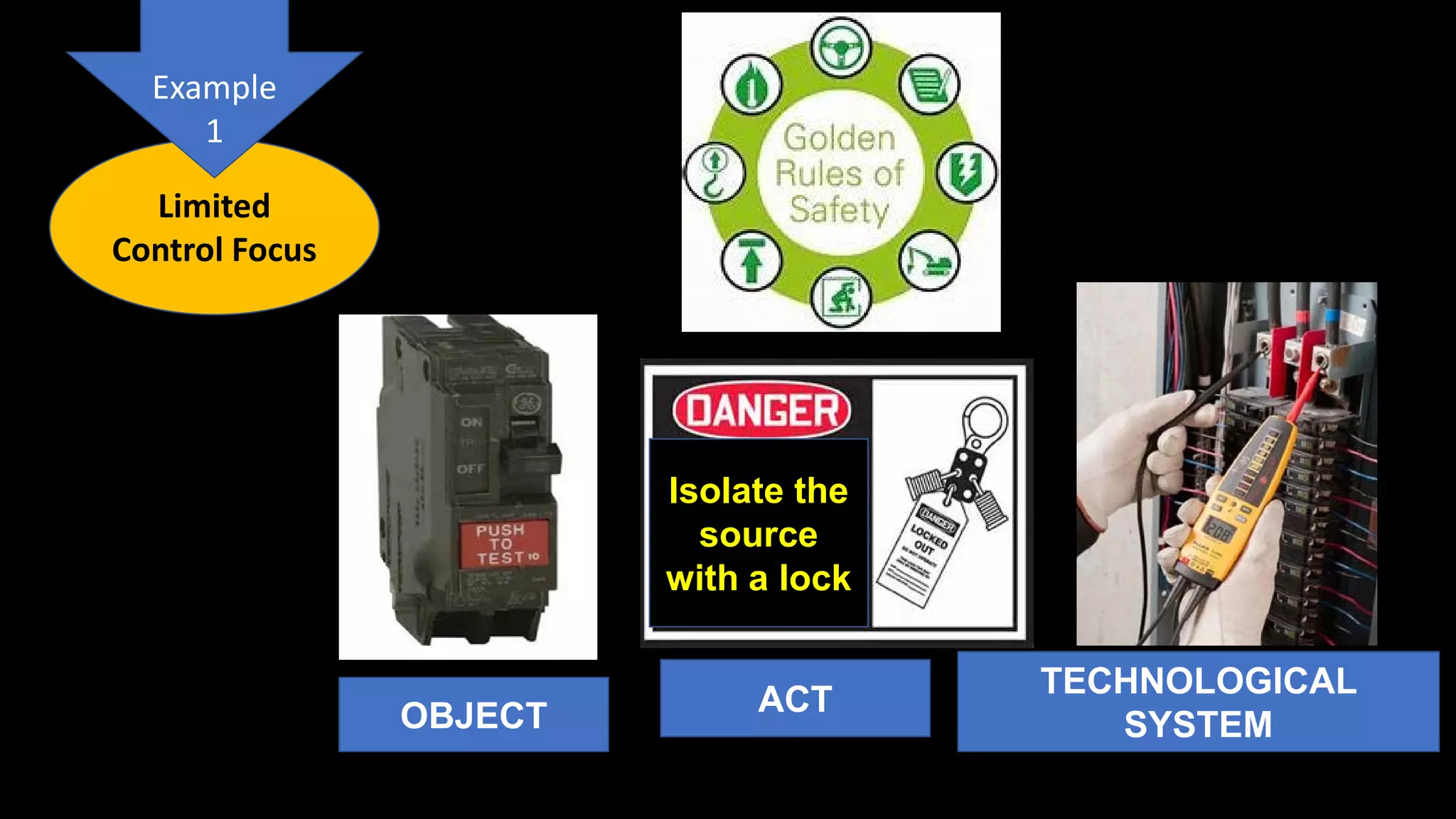
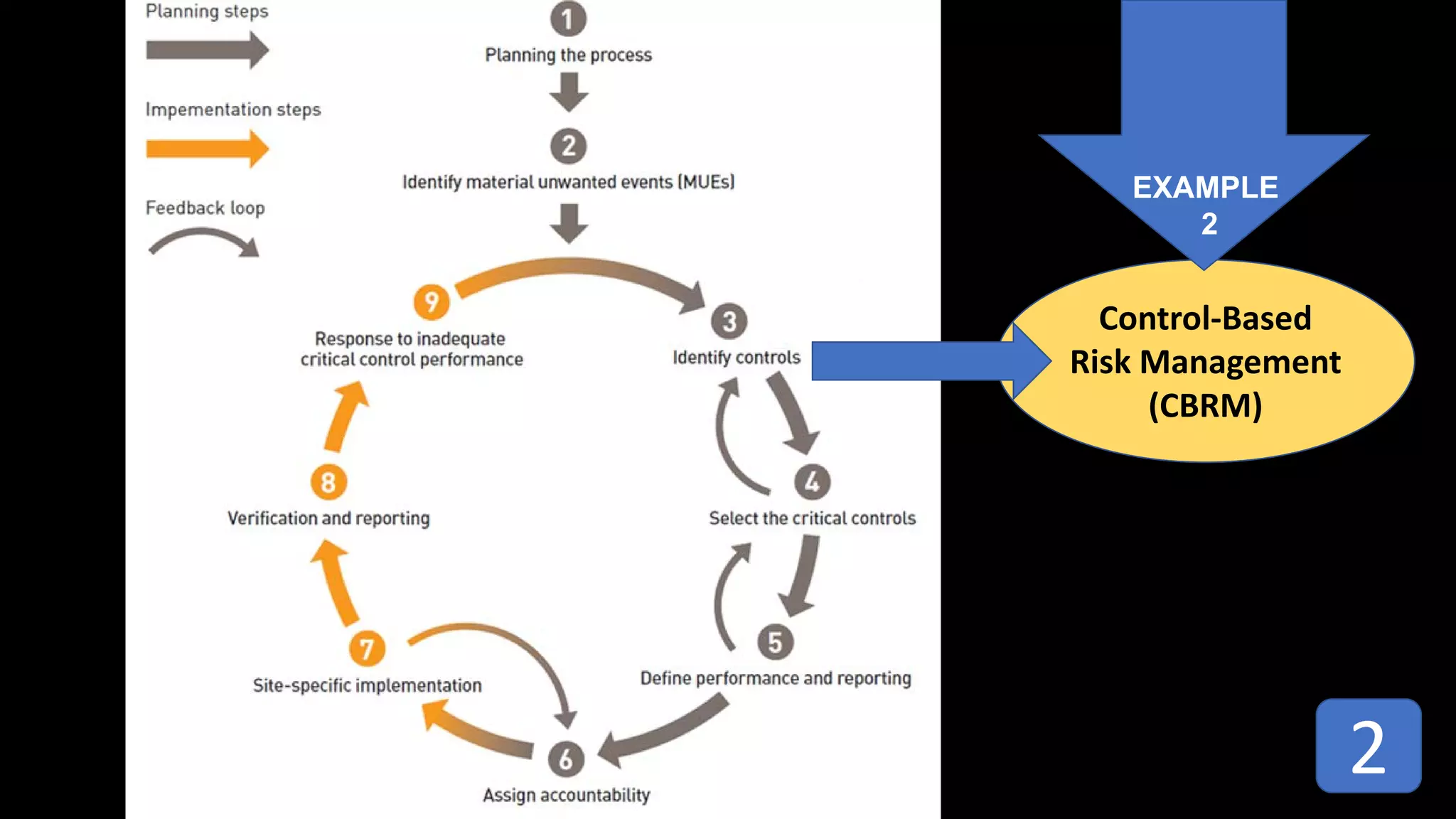
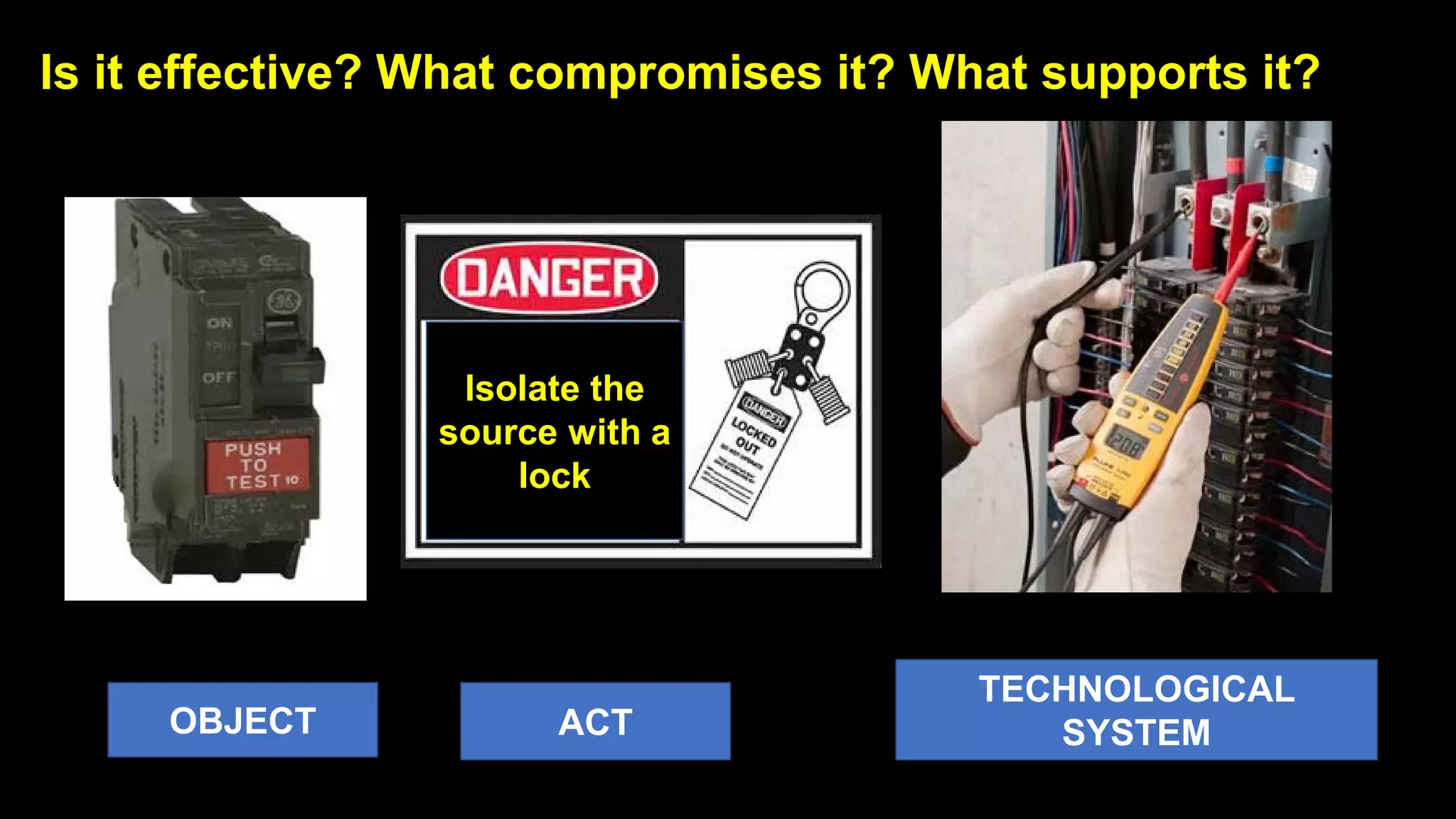
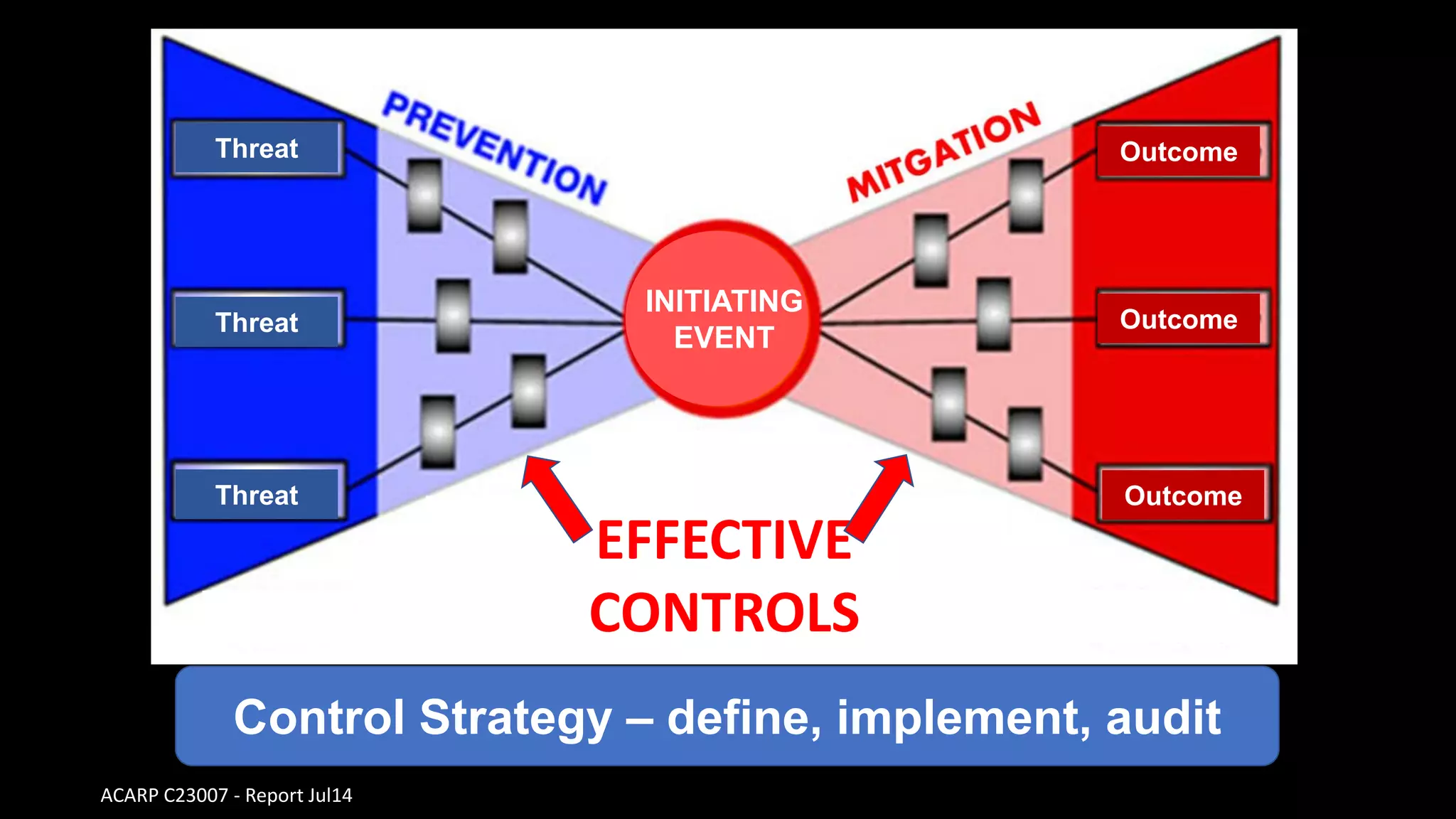
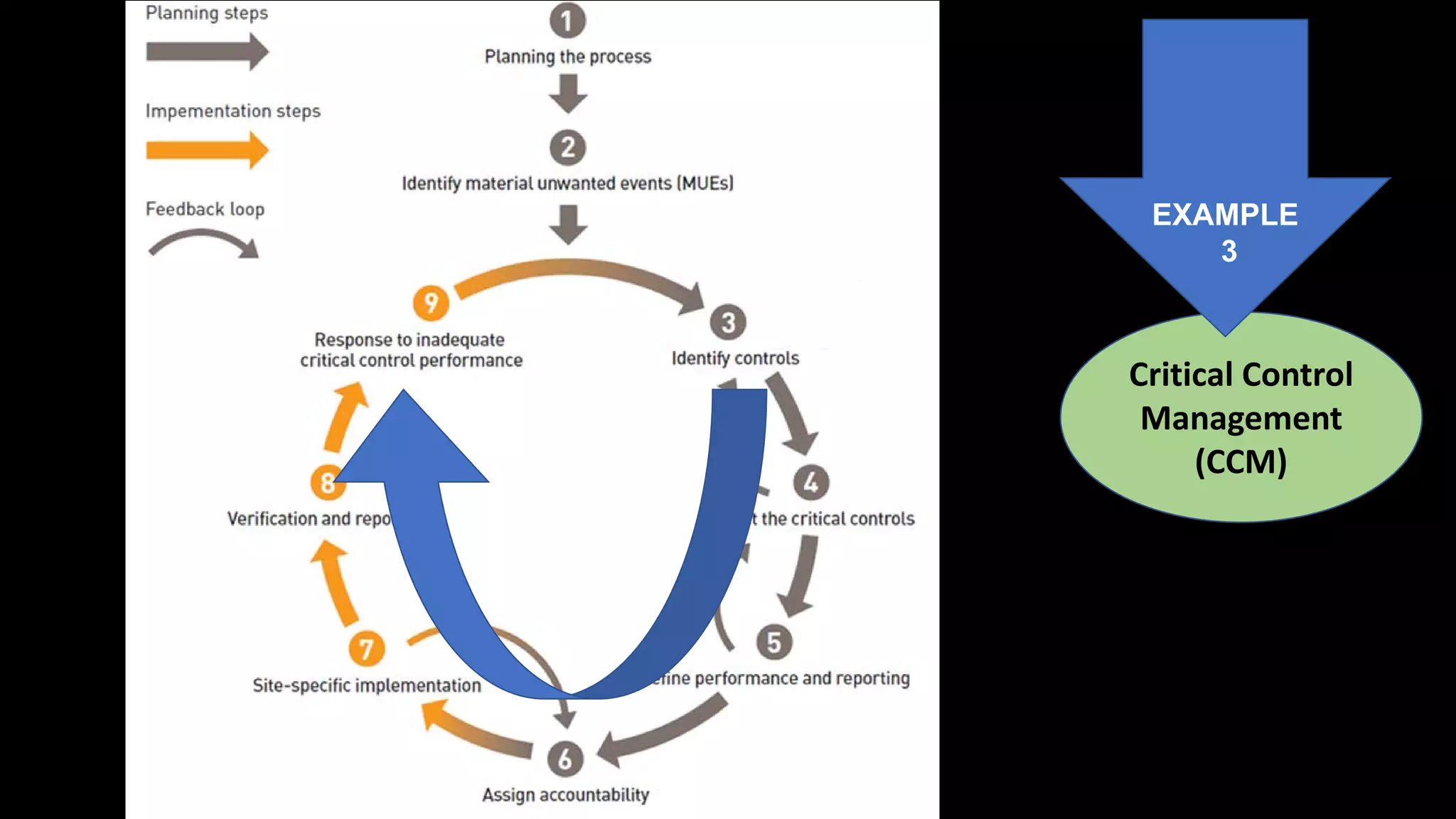
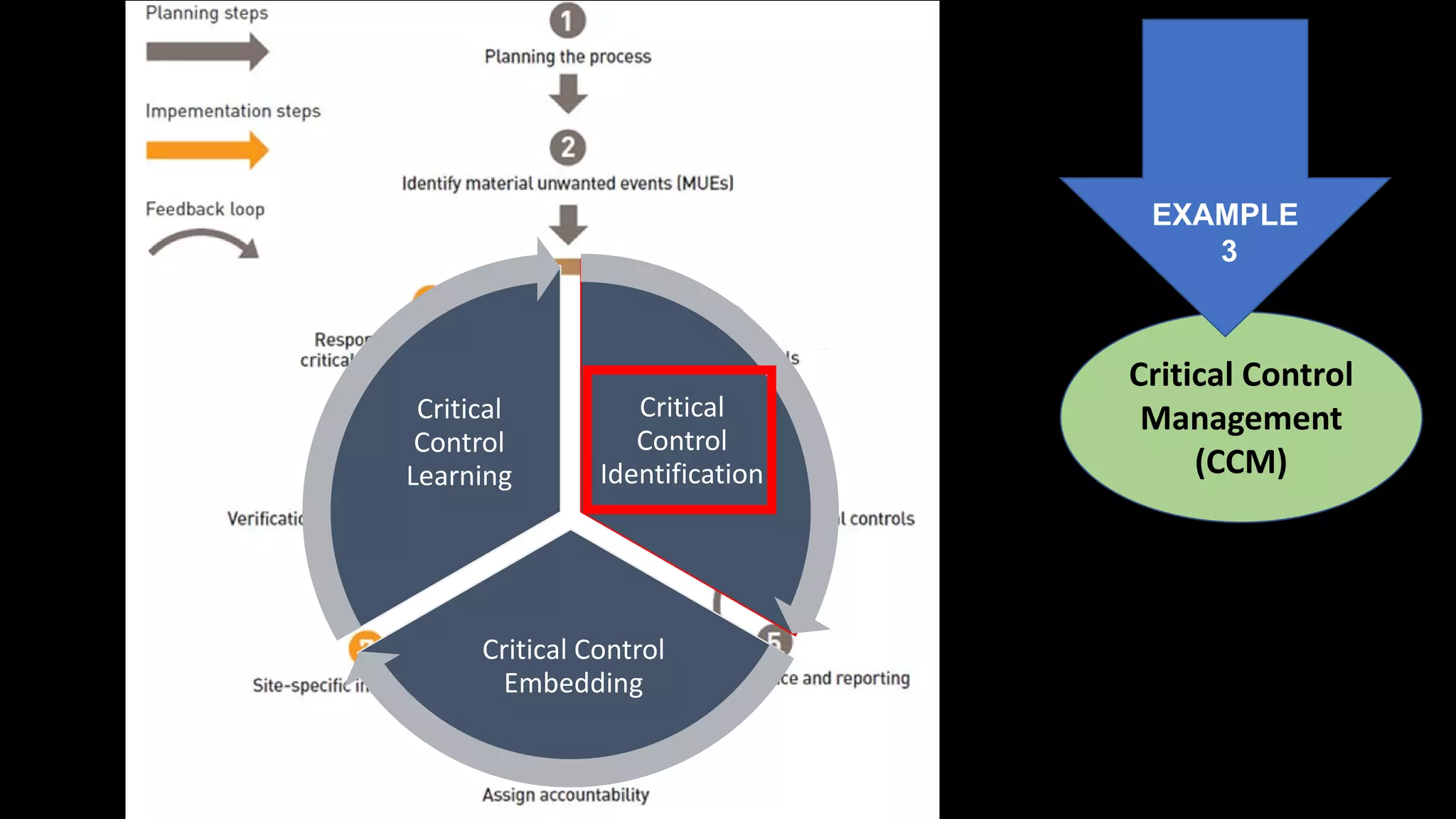
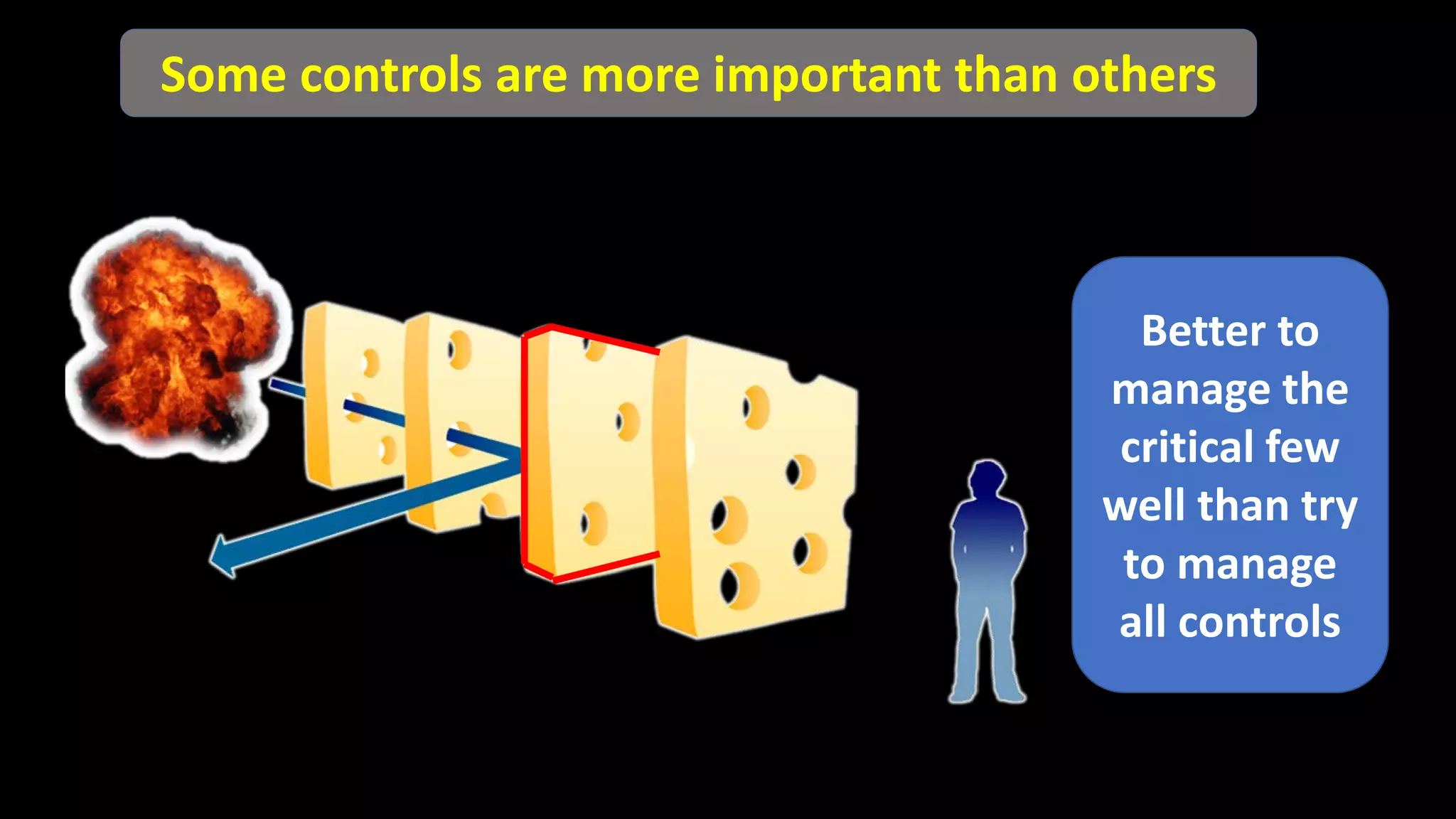
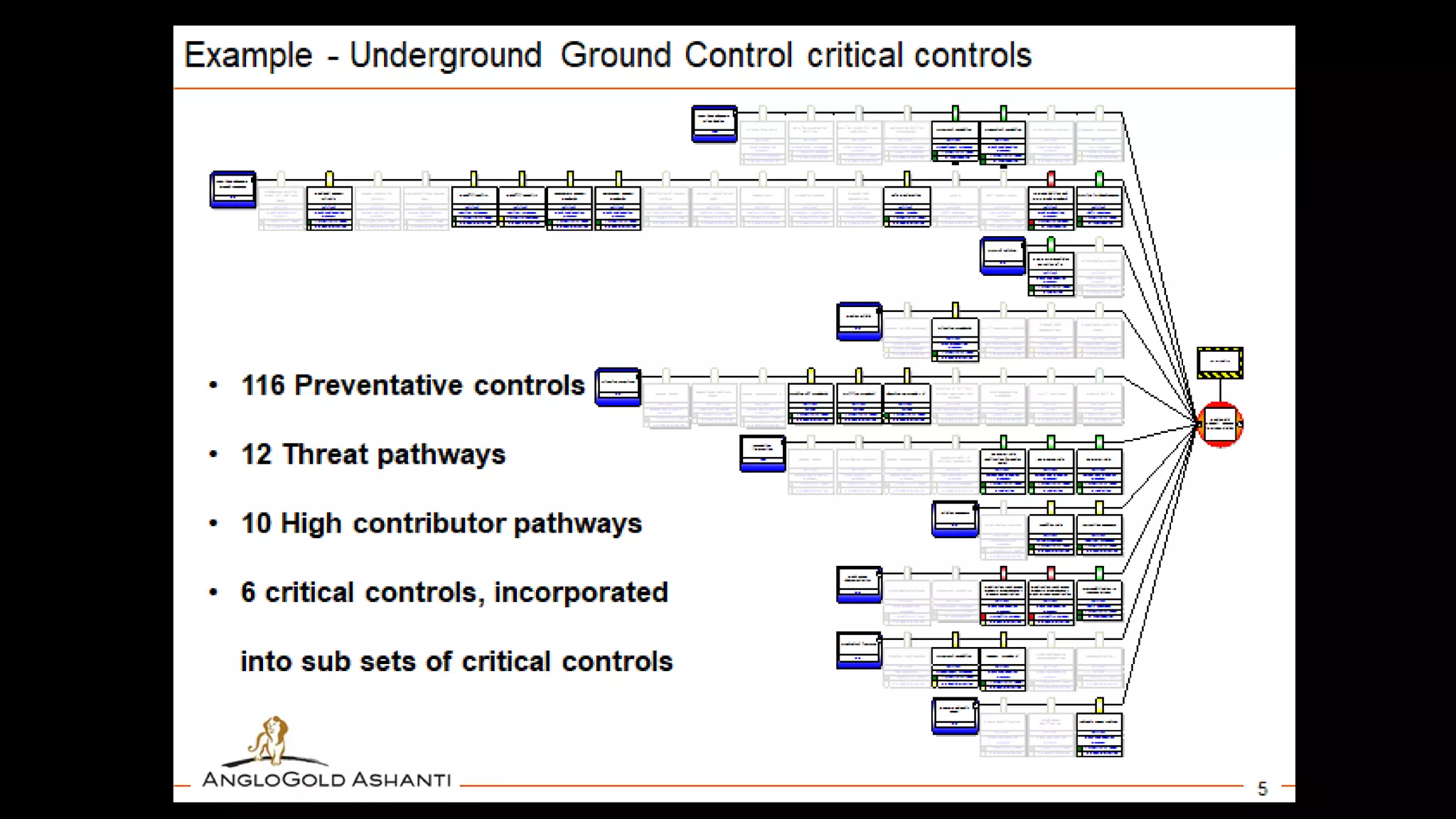
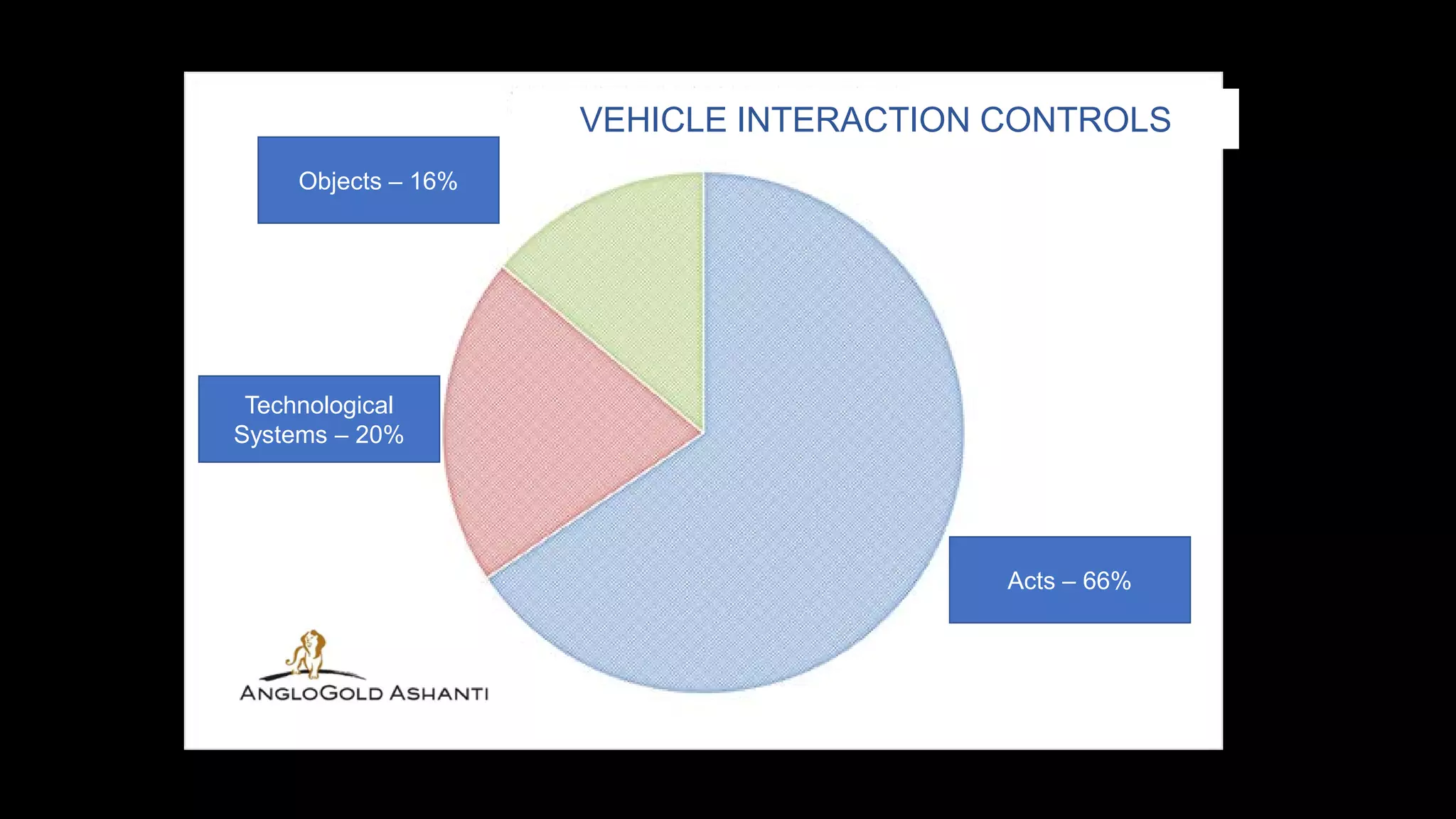
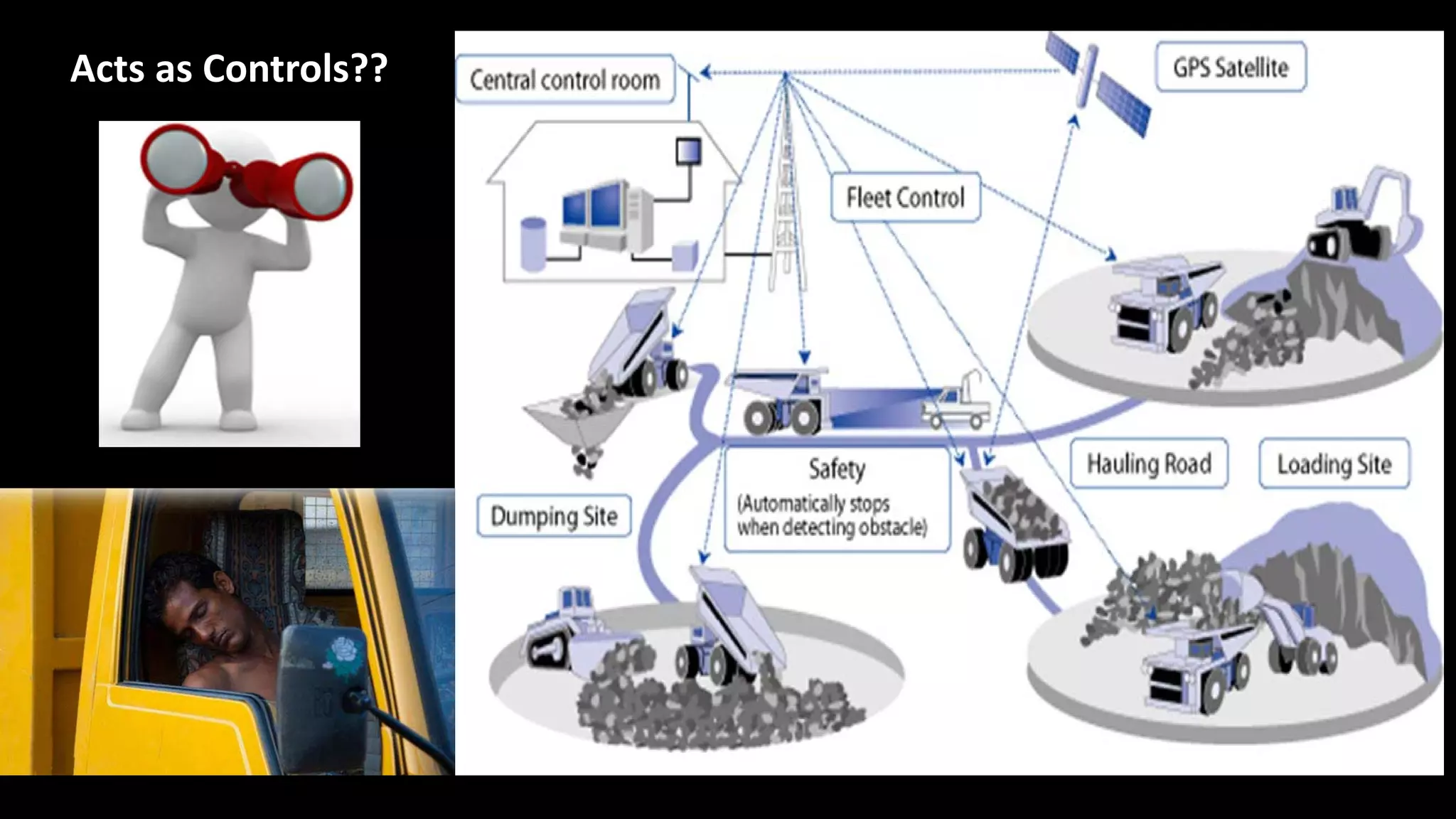
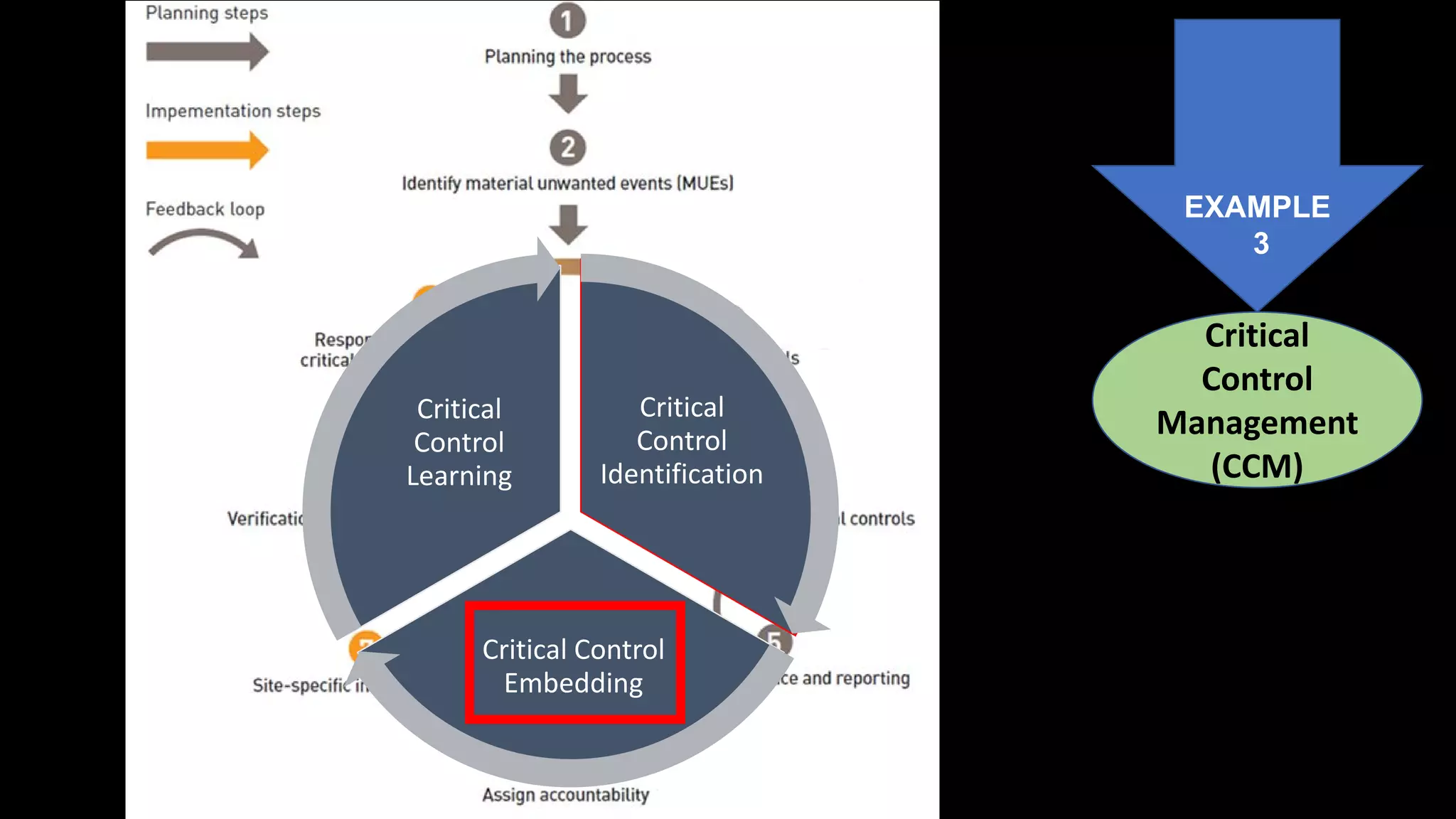
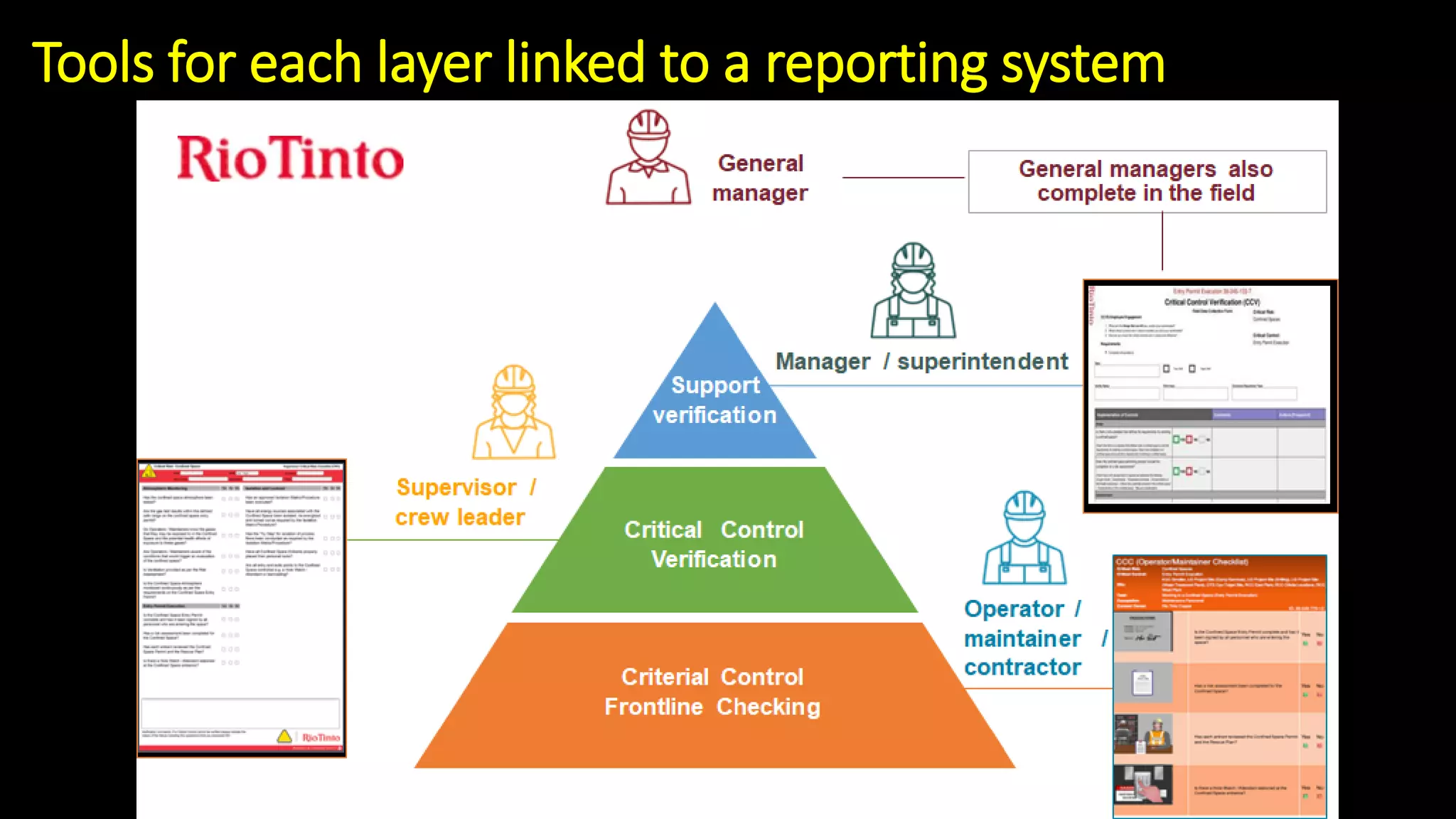
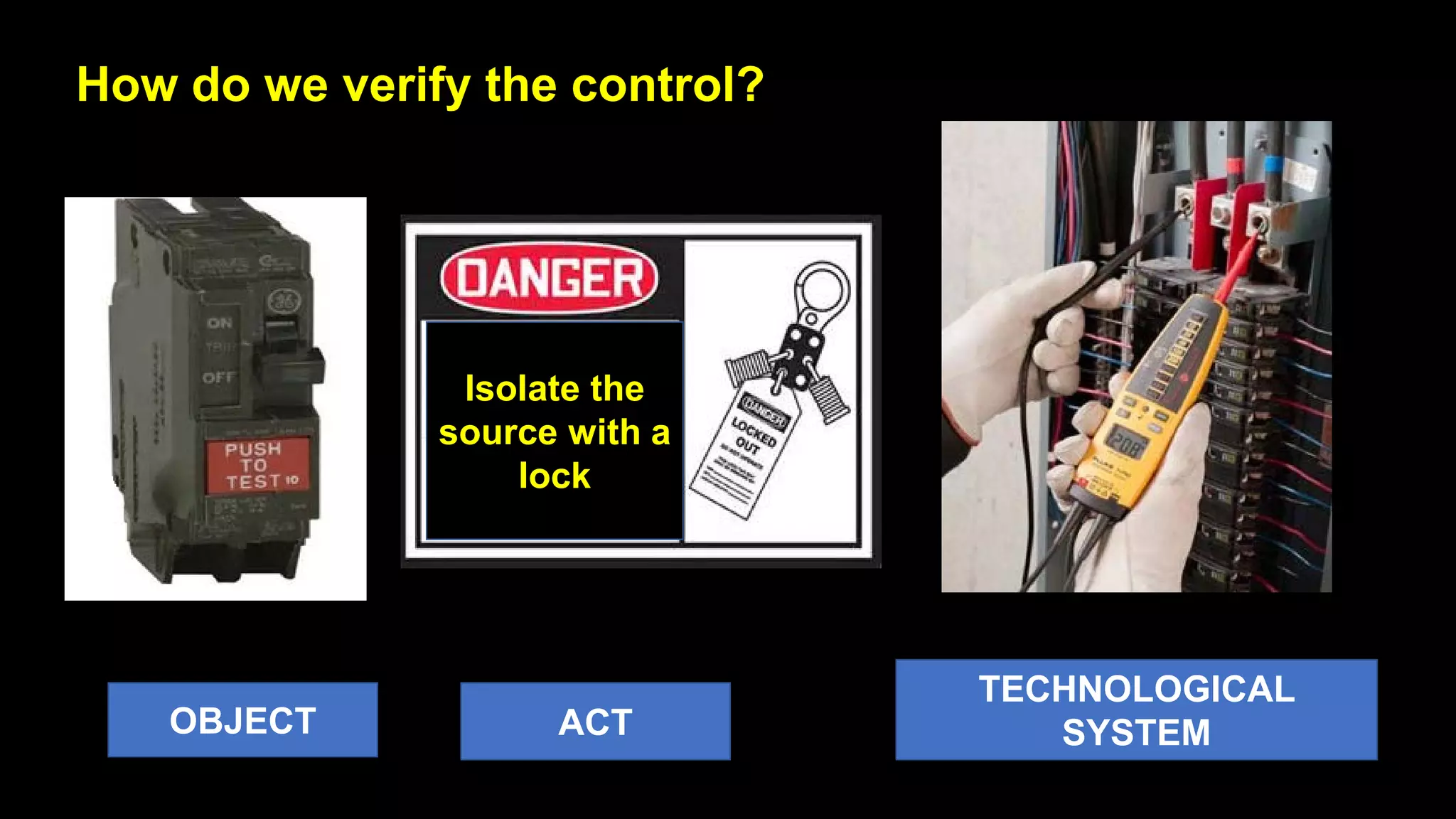
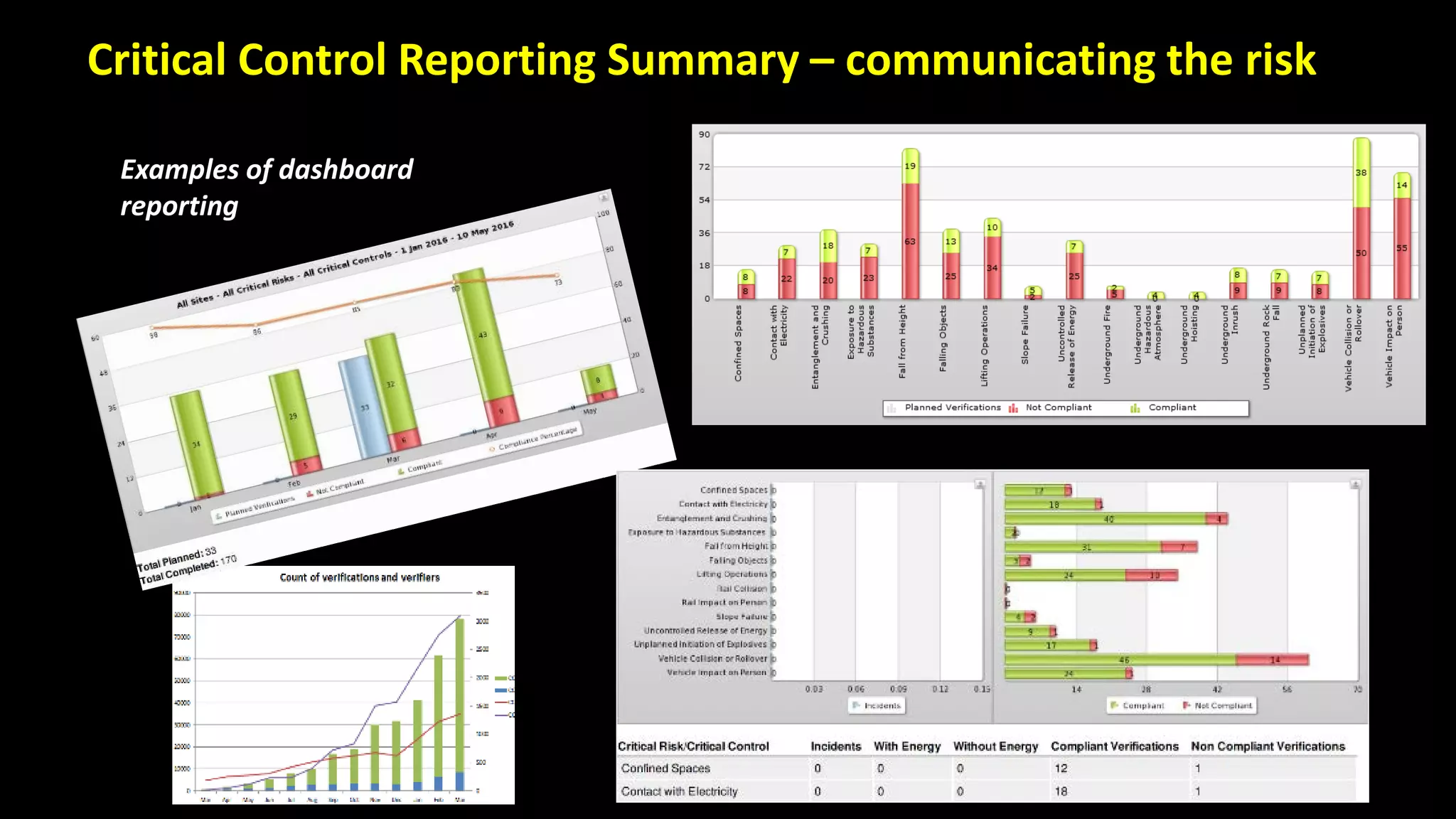
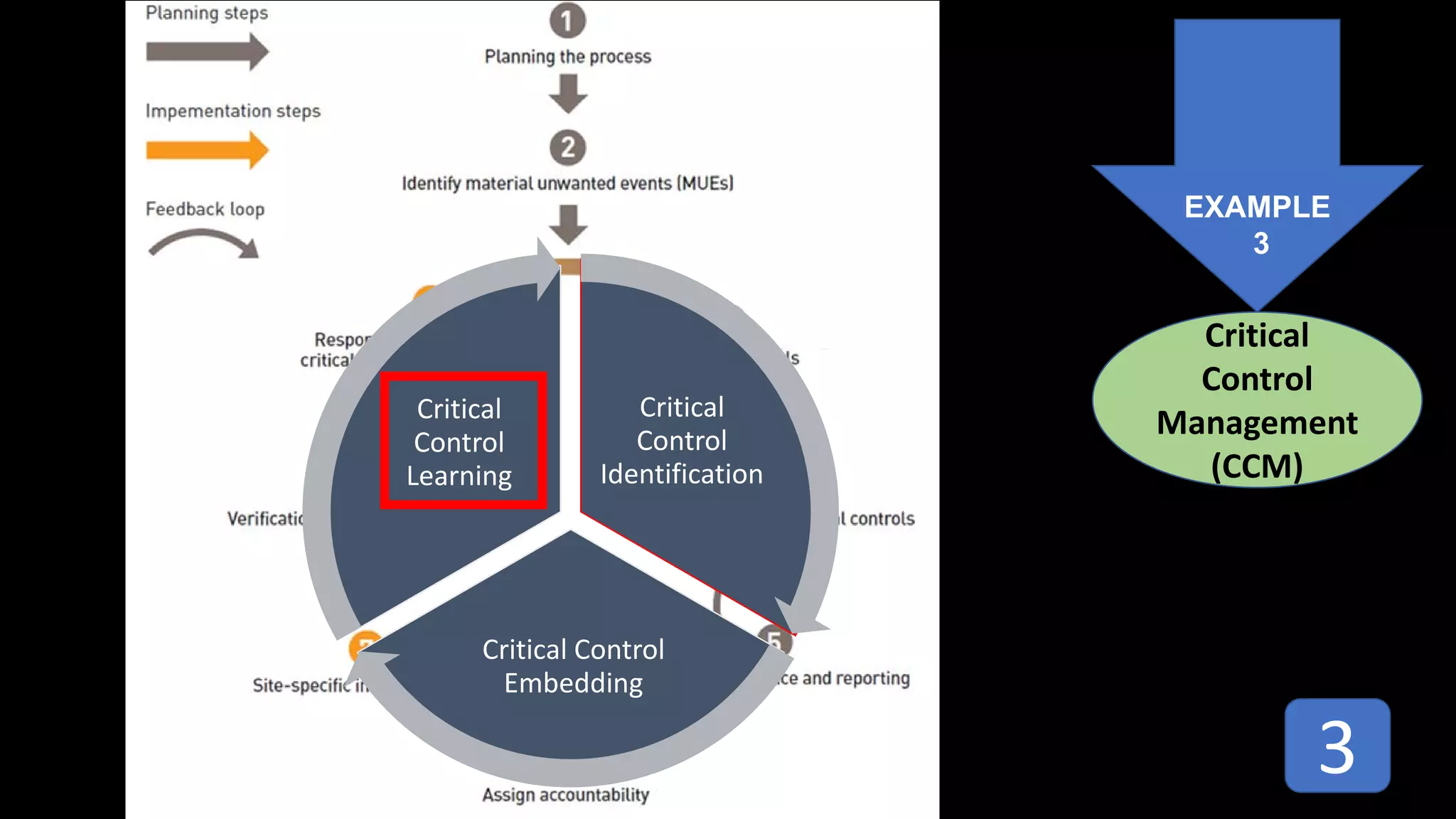
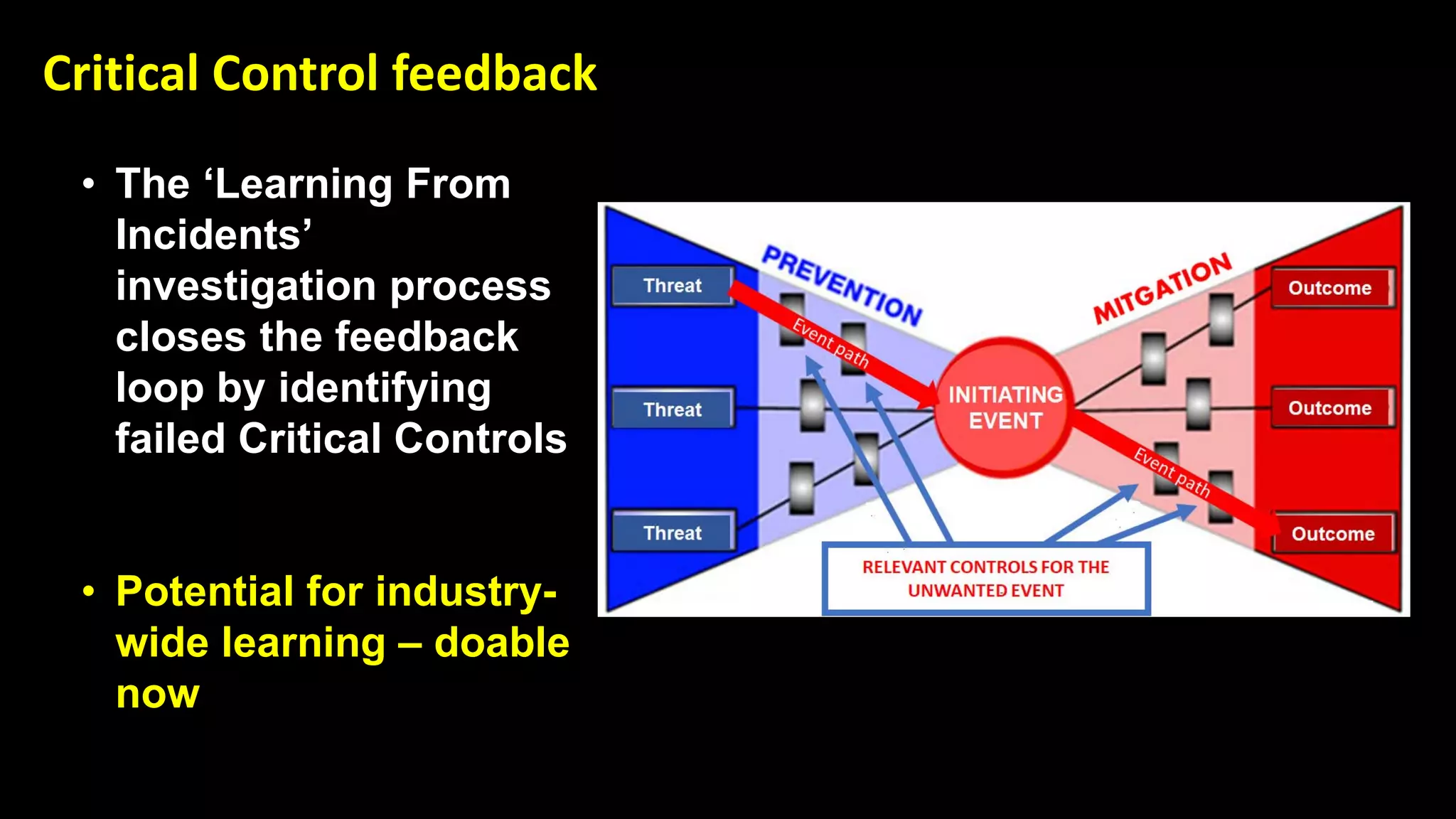
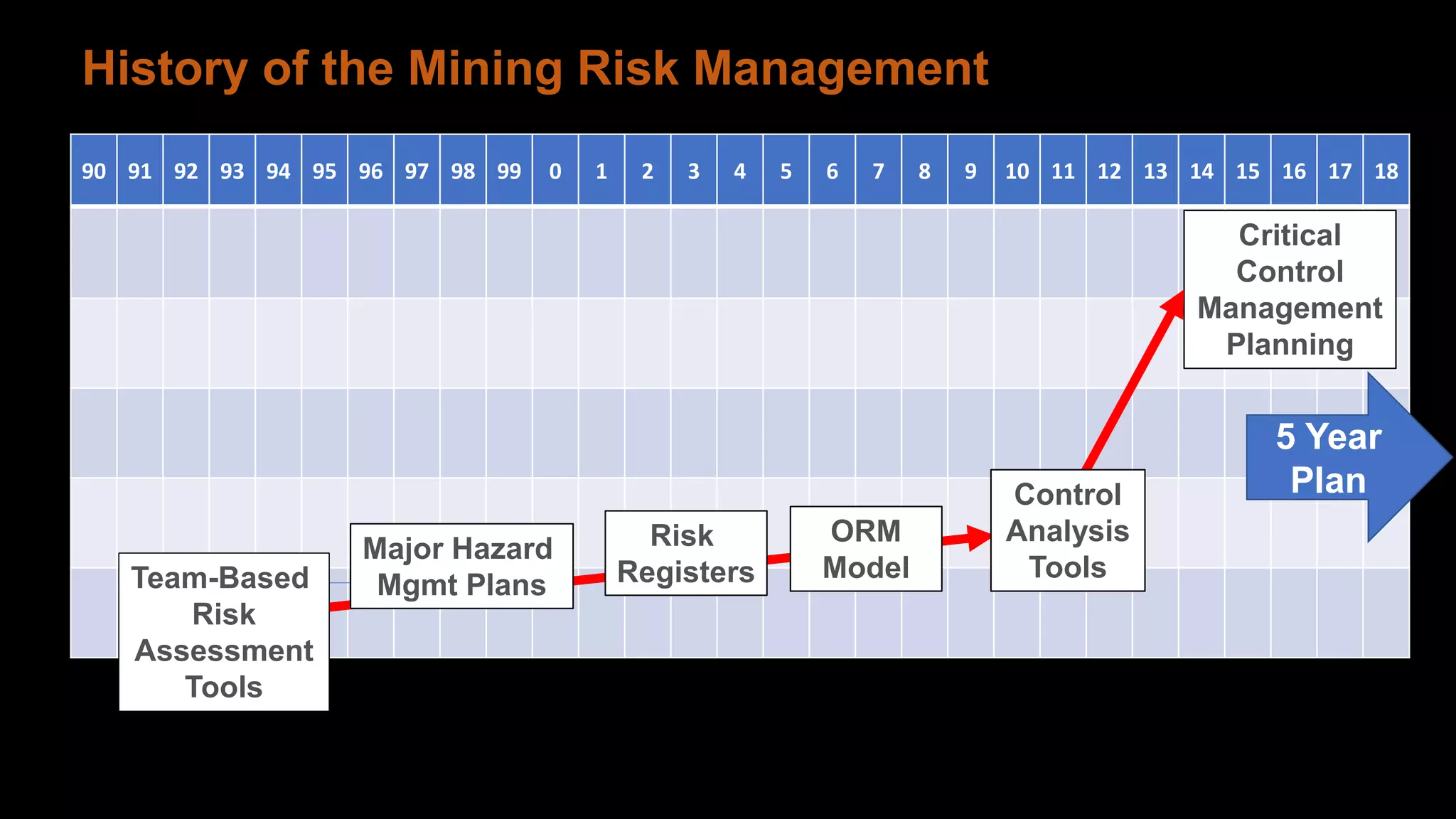
Jim Joy outlines the evolution of operational risk management (ORM) in the mining industry from control-based risk management to critical control management (CCM). CCM prioritizes identifying and managing the critical few controls that are most important for preventing high-risk events. It involves identifying critical controls, embedding their effective use, verifying control performance, and establishing feedback loops to support continuous learning. CCM provides a framework for mining companies to focus on controls known to be crucial for eliminating fatalities and achieving risk management objectives.