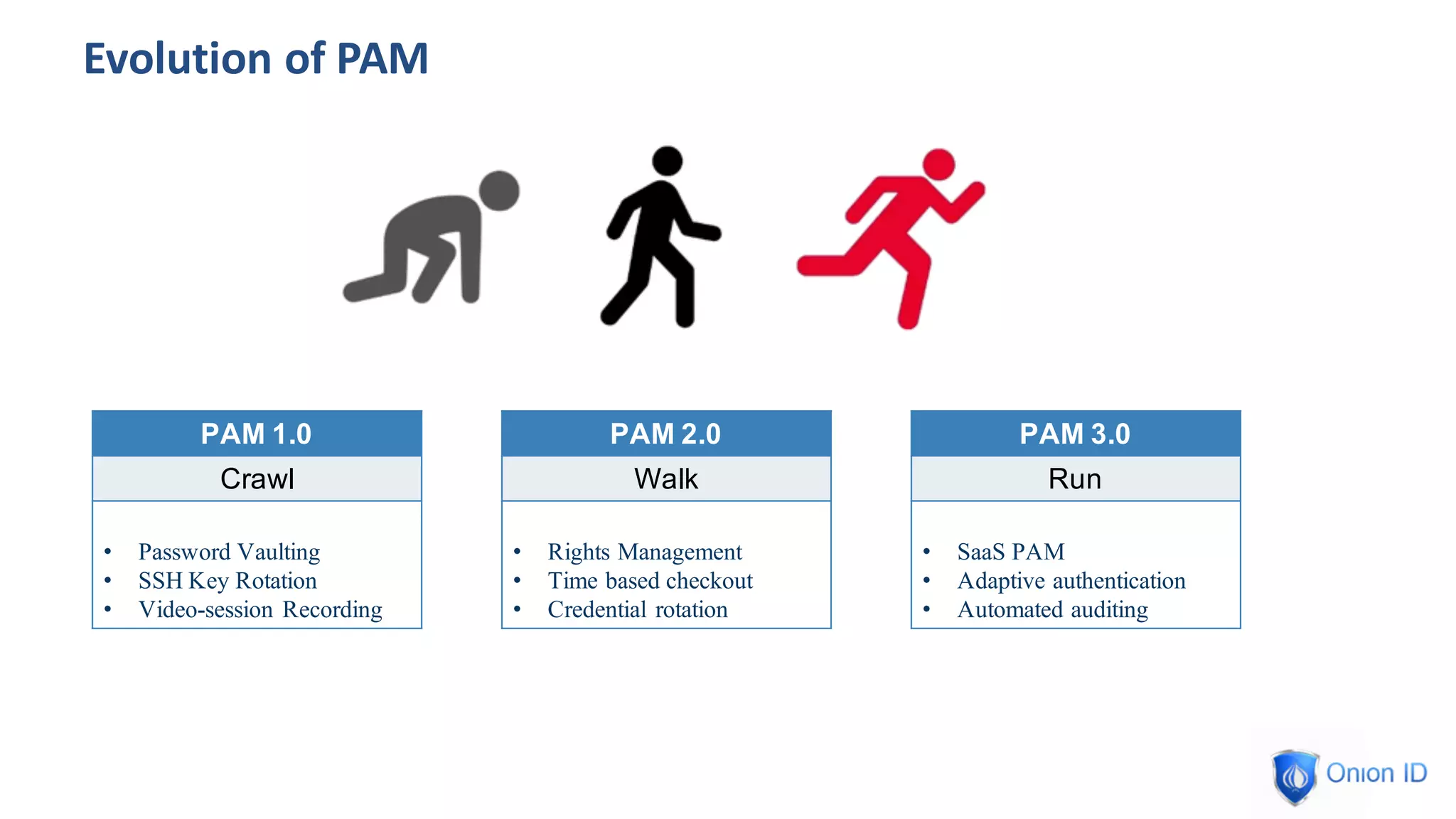
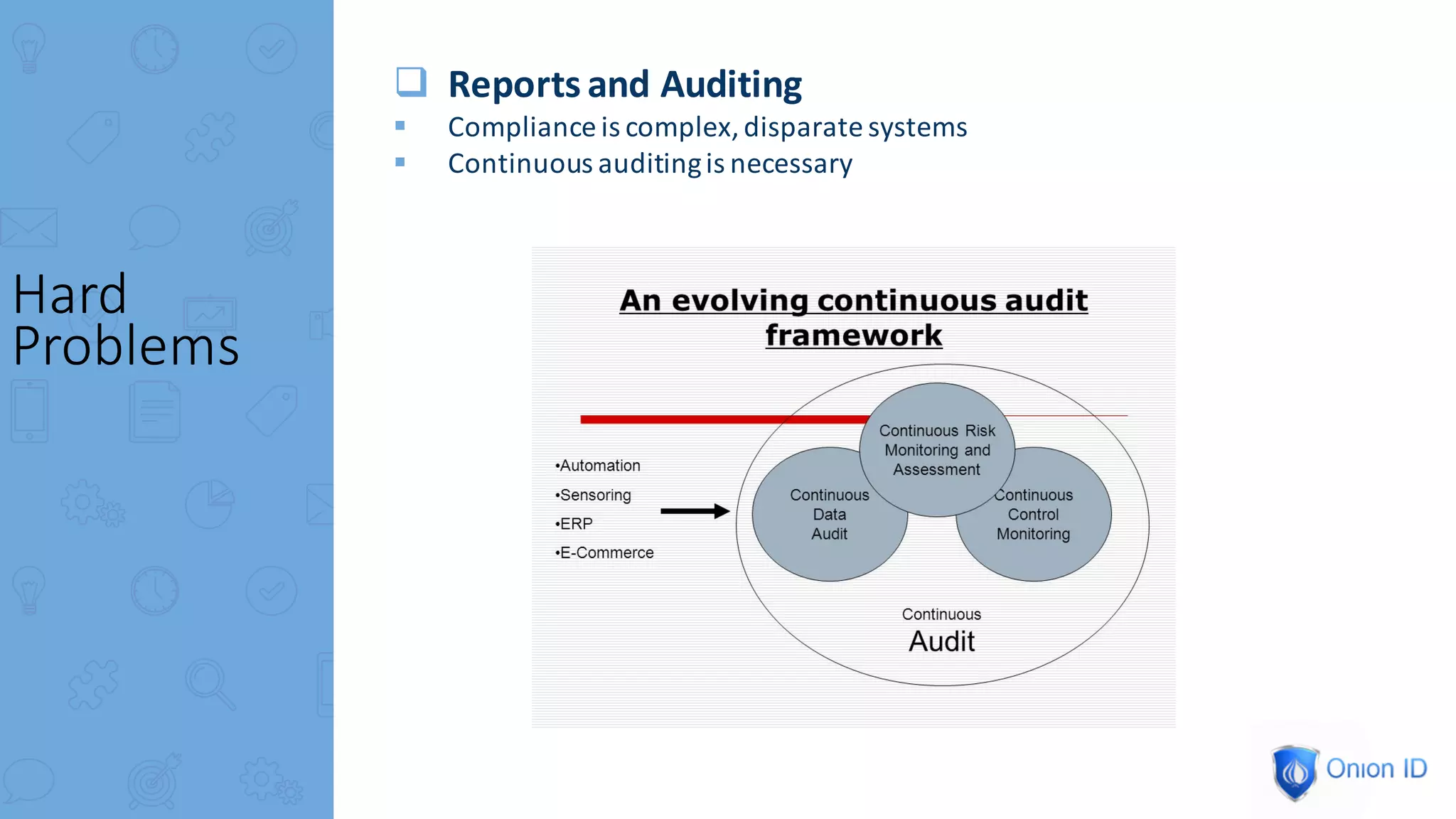
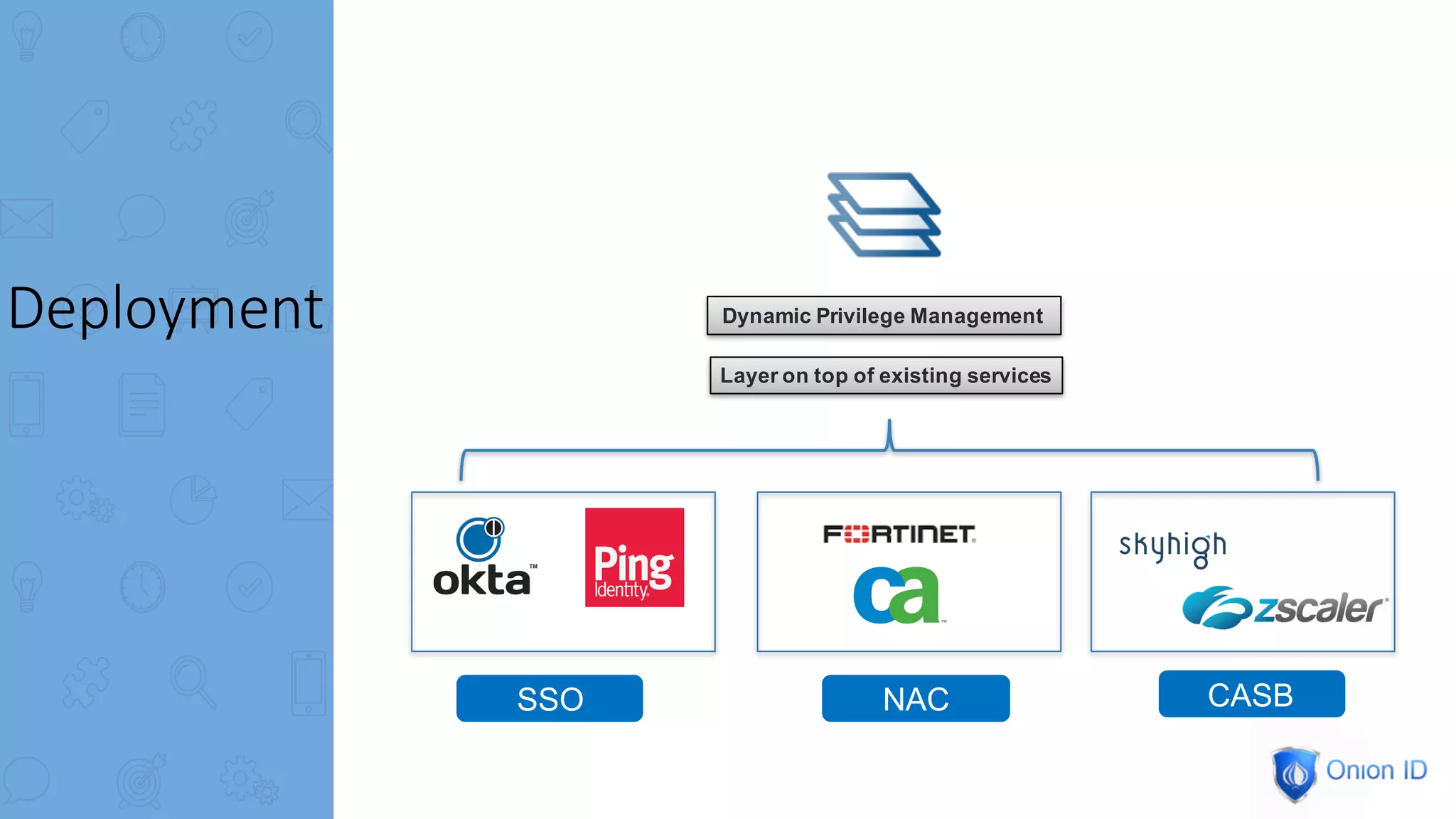
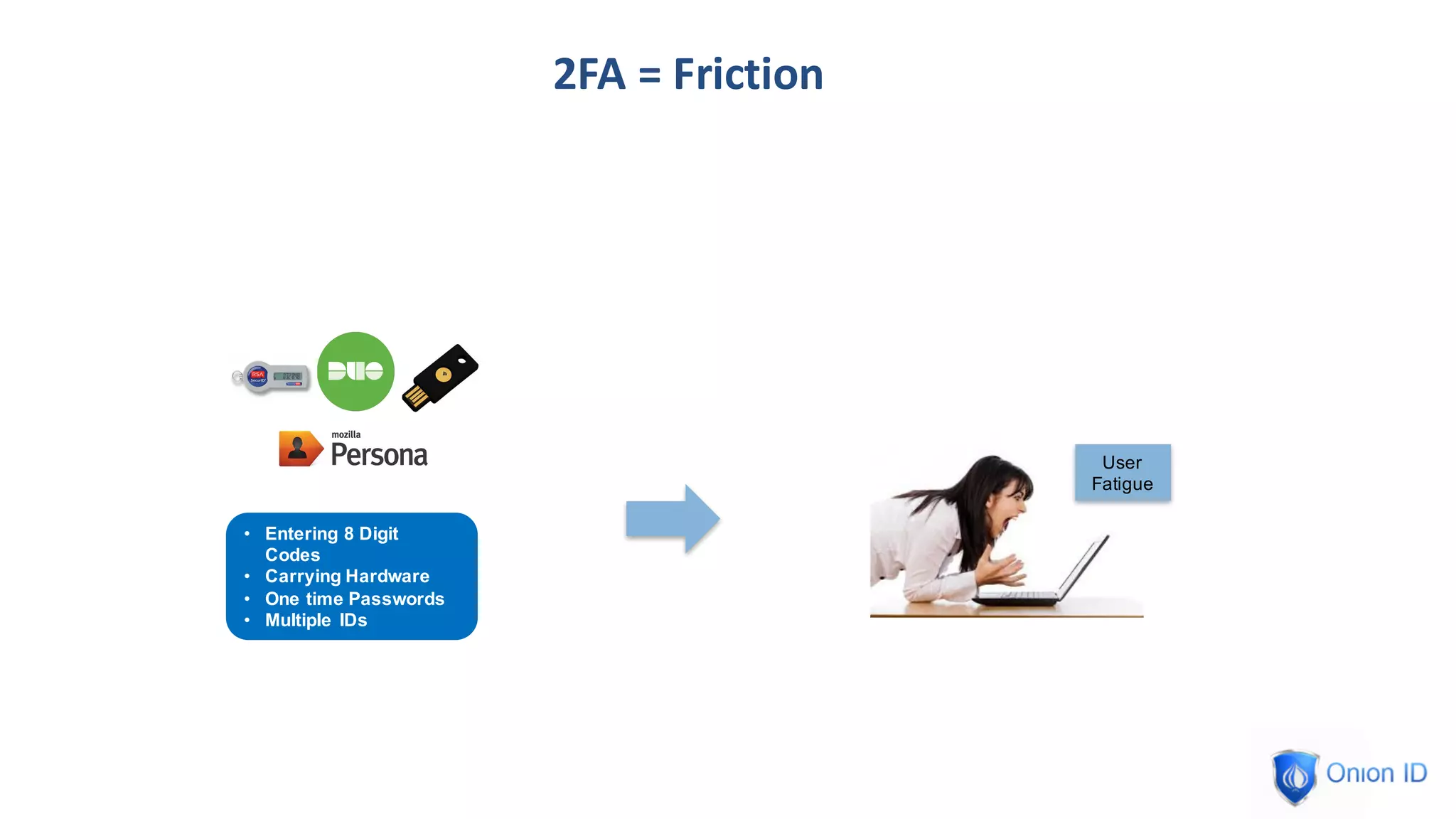
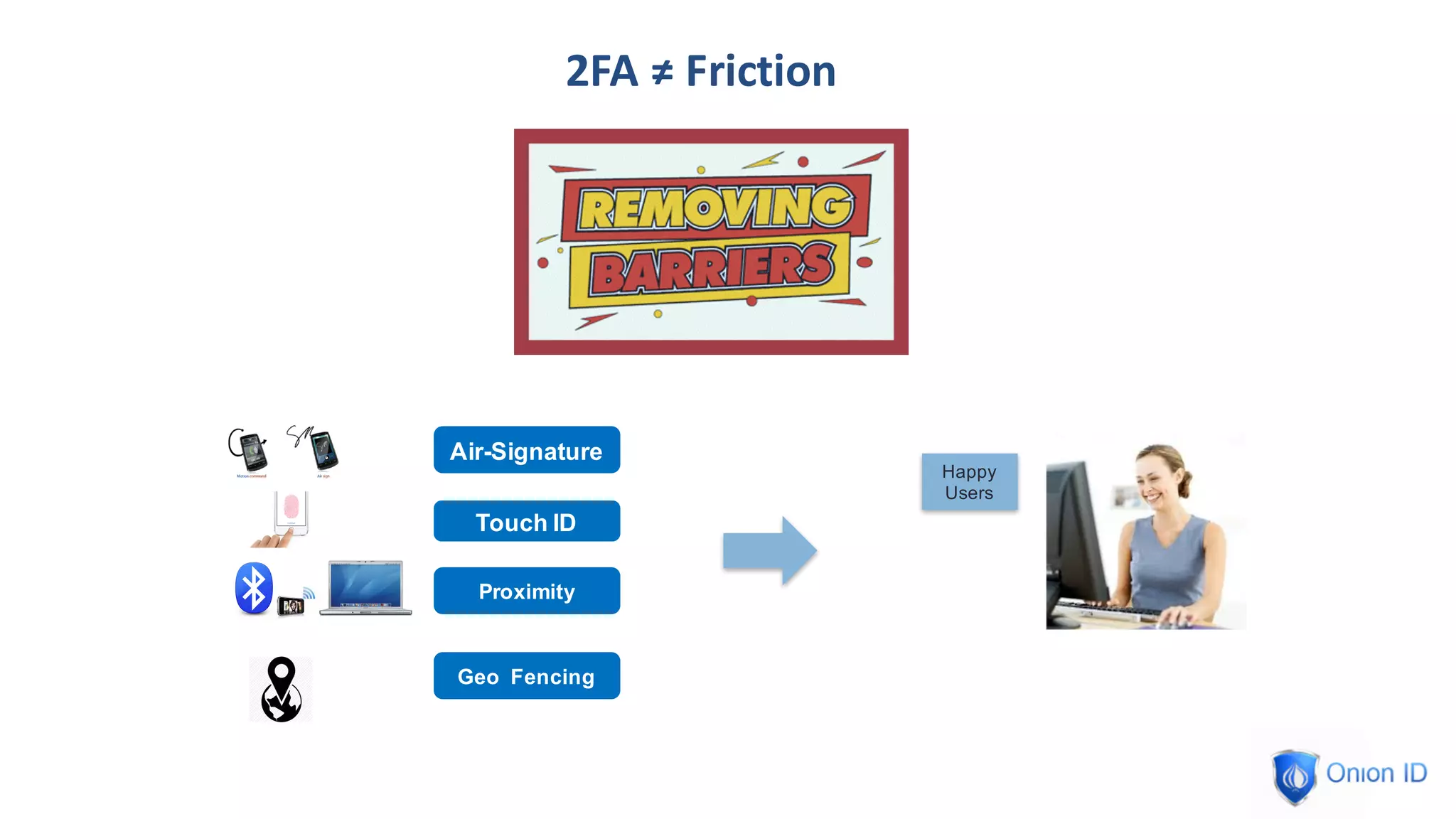
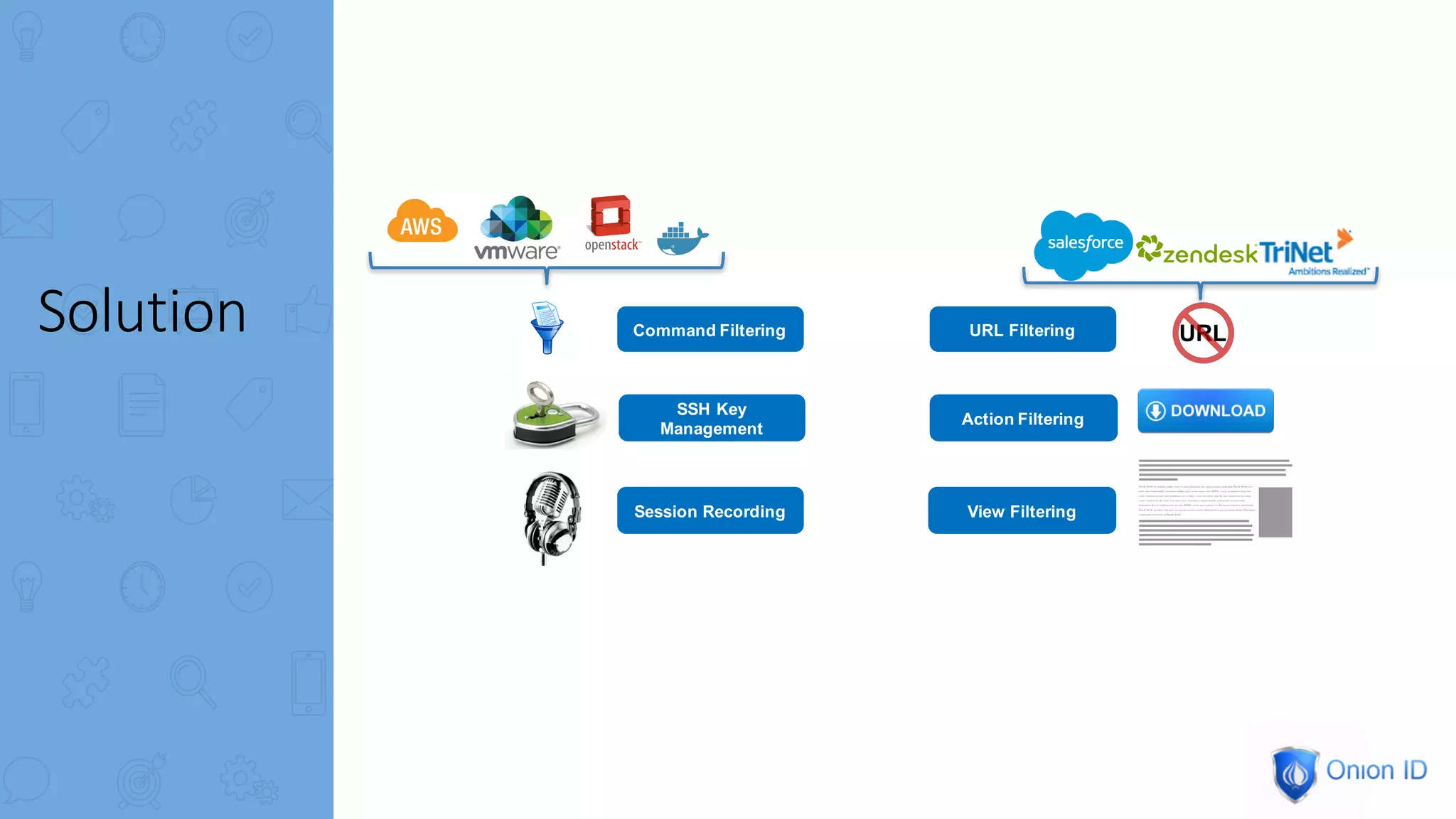
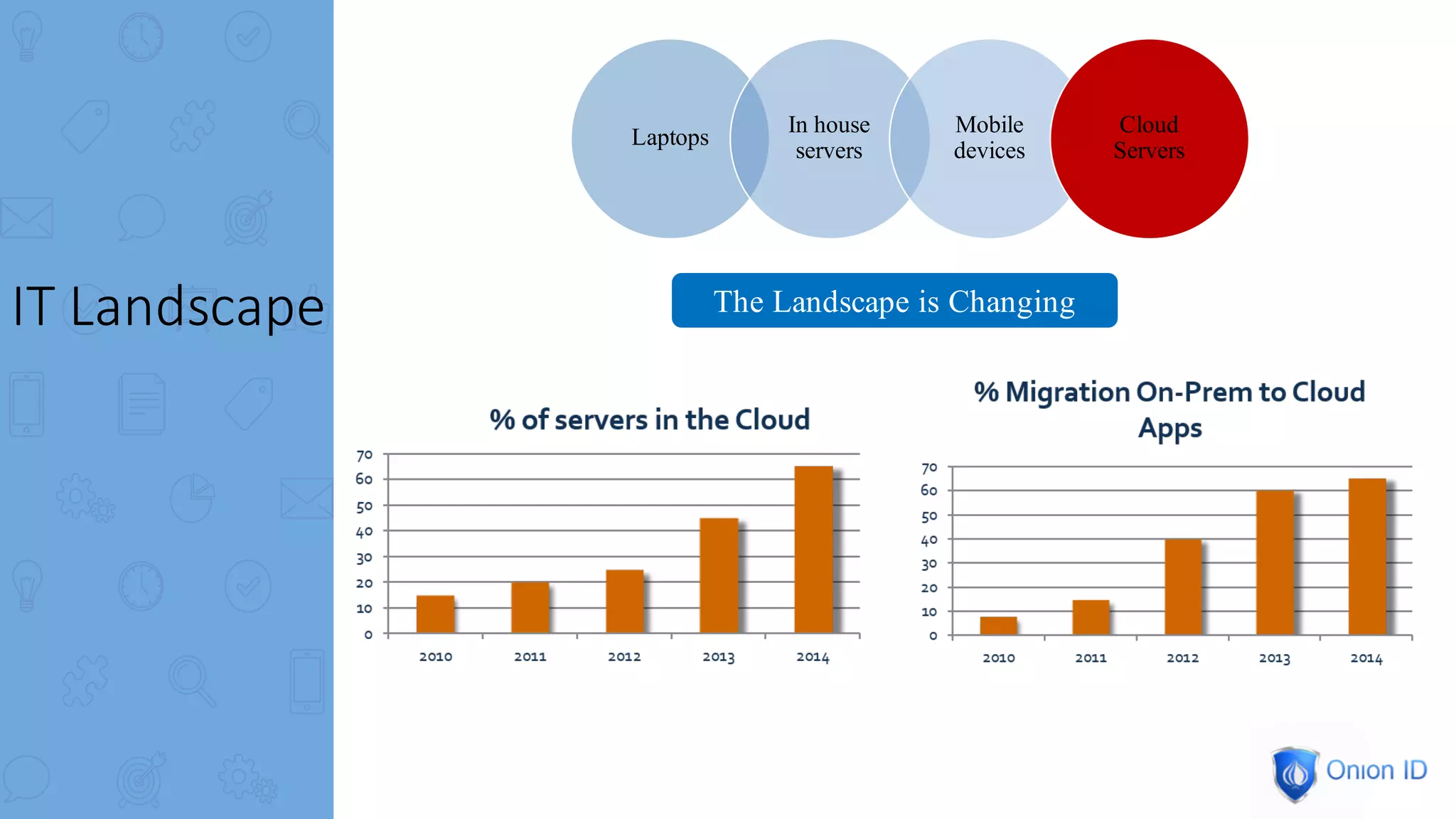
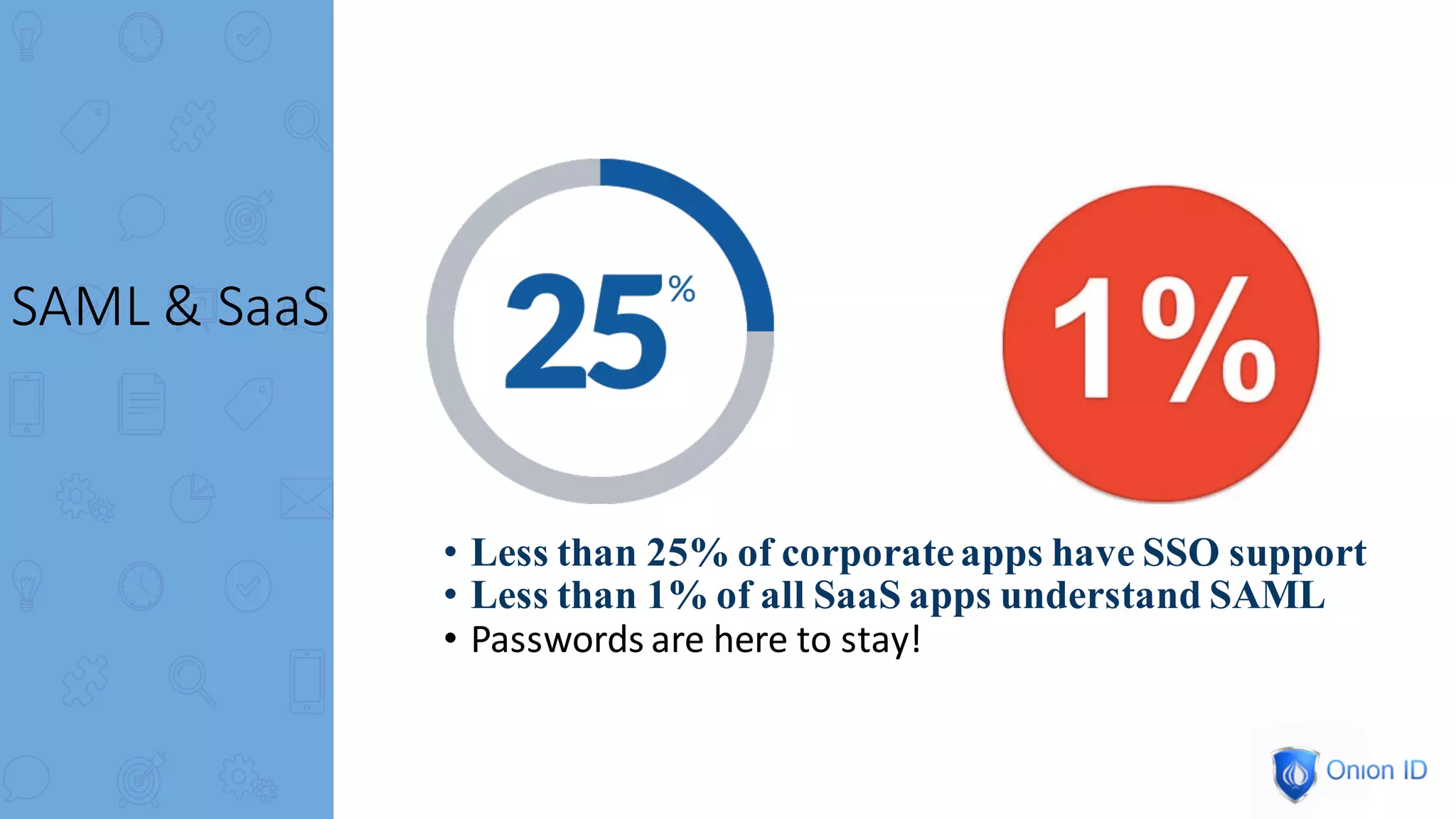
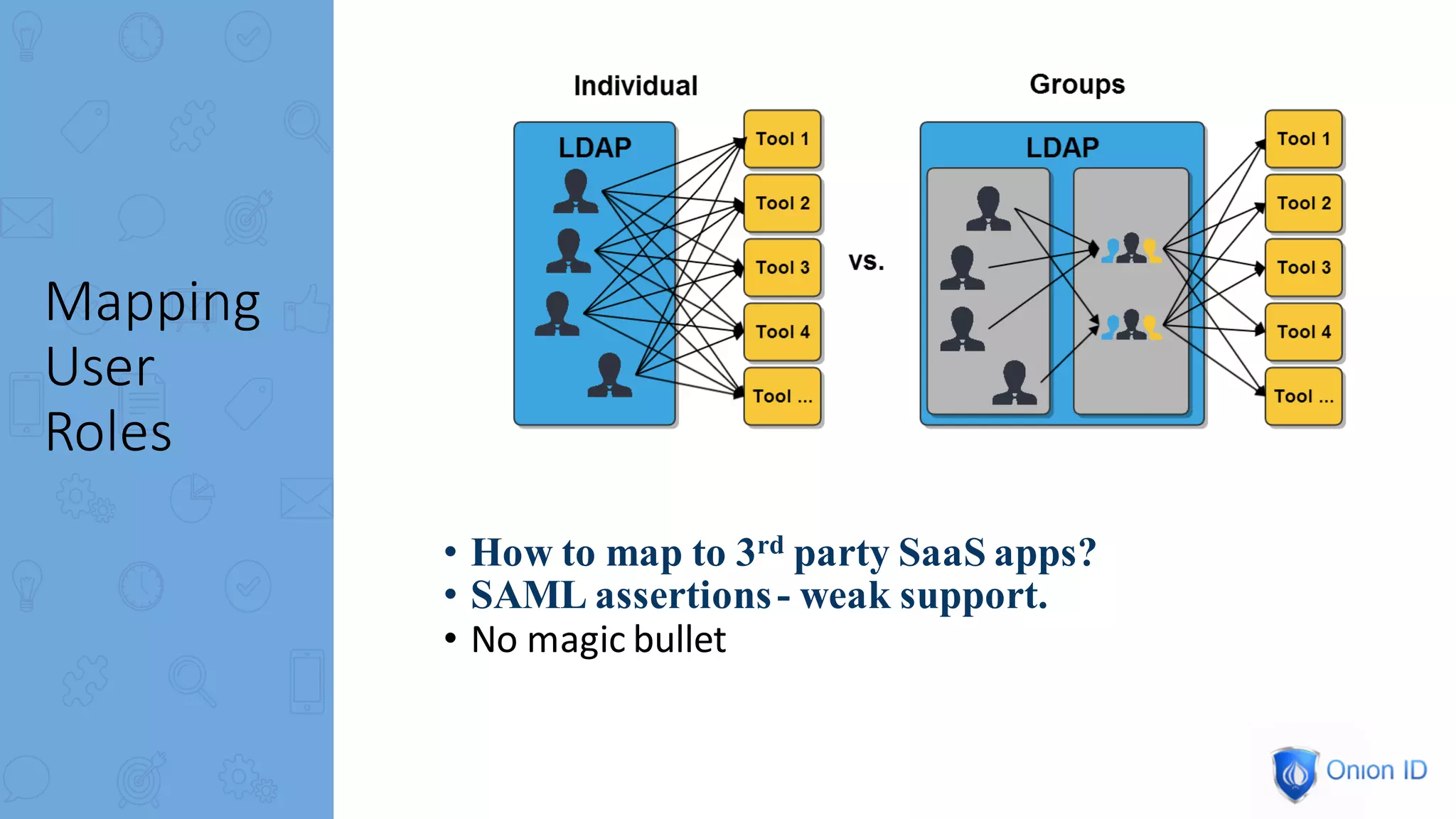
The document discusses the complexities of privilege management, highlighting its evolution and the importance of secure access in cloud environments. It outlines the seven layers of Privilege Access Management (PAM), emphasizing challenges such as user activity tracking and secrets management. The conclusion stresses the need for continuous auditing, fine-grained controls, and reducing friction in two-factor authentication experiences.







![PAM - Layers
Shrek: Ogres are like onions
Donkey: They Stink?
Shrek: Yes. No.
Donkey: Oh.....they make you cry
Shrek: No!
Donkey: Oh, you leave 'em out in
the sun,they get all brown,start
sproutin' little white hairs
Shrek: NO. Layers.Onions have
layers.Ogres have layers.Onions
have layers.You get it? We both
have layers.[sigh]
Donkey: Oh, you both have layers.
Oh.
PAM has layers. Onions have layers. We both have layers.Get it?](https://image.slidesharecdn.com/5ccee80f-5f27-4552-838b-513ec4e422c1-160701135255/75/The-7-Layers-of-Privileged-Access-Management-12-2048.jpg)