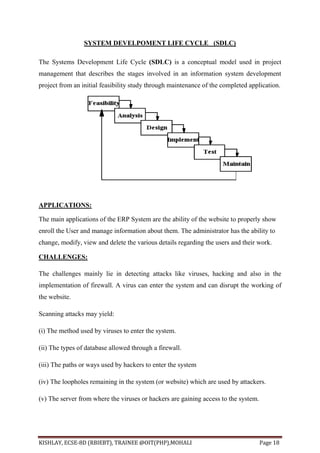
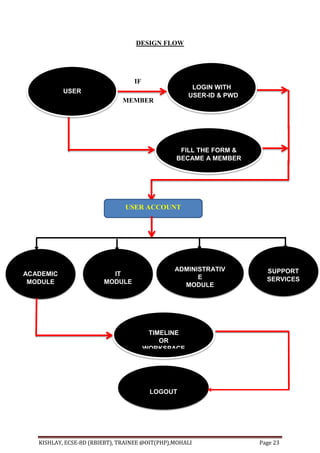
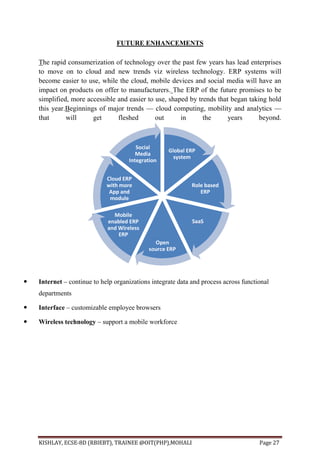
This document provides an overview of an Enterprise Resource Planning (ERP) project. It discusses the various modules of the ERP system, including academic, IT, administrative, and support service modules. It also covers the tools used to build the front-end and back-end of the ERP system, including HTML, PHP, JavaScript, and MySQL. The document aims to provide requirements, analysis, and descriptions of the various components that make up the ERP project.