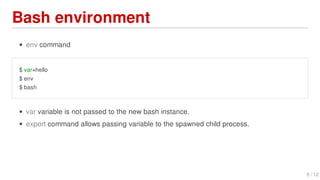
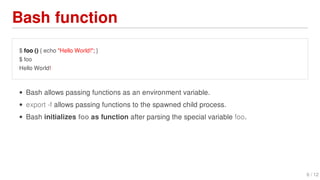
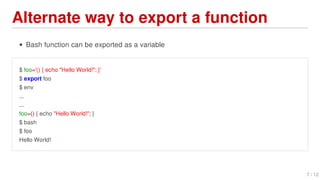
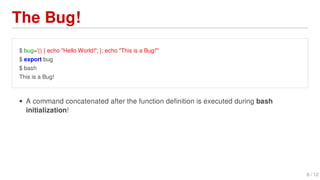
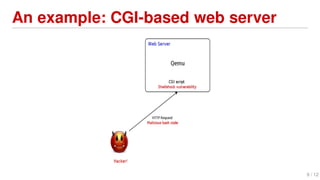
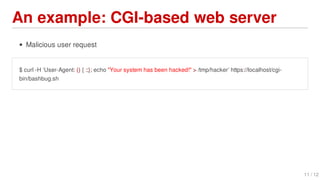
Shellshock is a vulnerability in Bash that allows attackers to execute arbitrary commands on vulnerable systems. It was discovered in September 2014 and affected many Linux and Unix-based systems. The bug allows environment variables passed to Bash to execute code, potentially allowing remote code execution. This could enable large-scale DDoS attacks and access to sensitive systems.