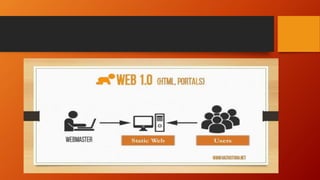
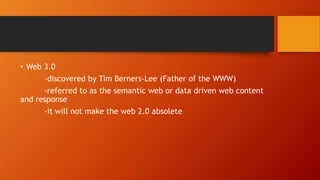
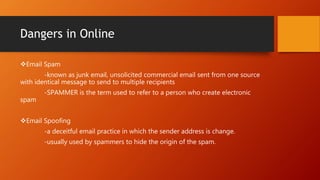
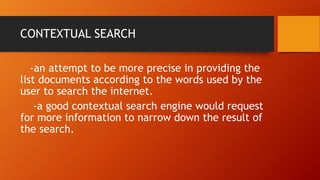
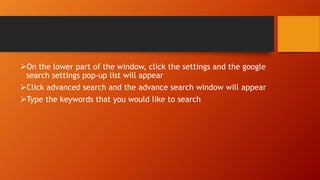
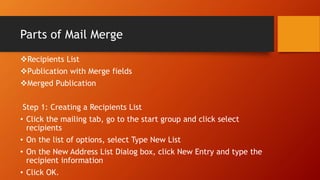
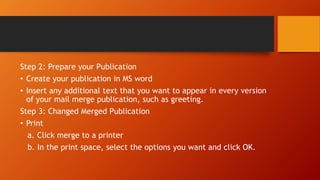
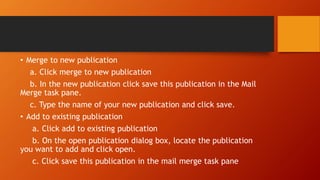
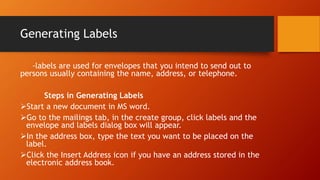
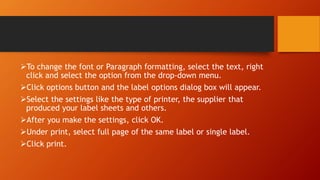
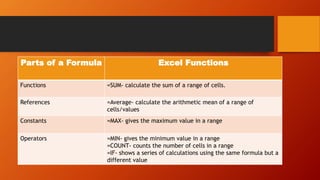
This document discusses information and communication technology (ICT) and how it can be used across different fields like education, commerce, health services, and more. It explains the evolution of the World Wide Web from static Web 1.0 to more interactive Web 2.0 and the emerging data-driven Web 3.0. The document also discusses technology convergence using smartphones as an example. It covers social media platforms and online dangers like spam, spoofing, and hacking. Finally, it provides guidance on contextualized online research and detecting satirical news sources.