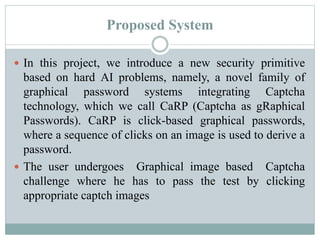
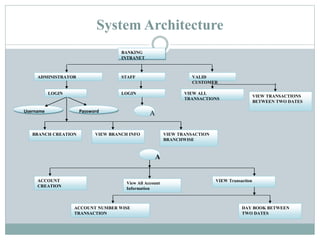
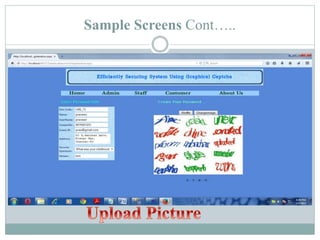
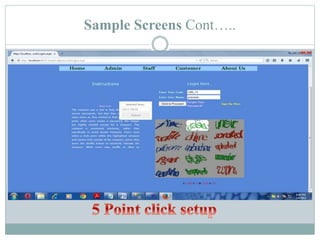
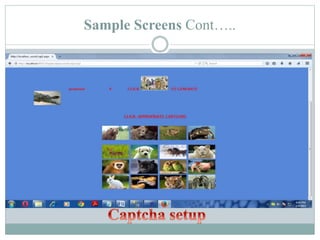
The document proposes a new security system called CaRP (Captcha as graphical passwords) that integrates captcha technology into a graphical password scheme. CaRP allows users to set passwords by clicking on images in a captcha challenge. This addresses weaknesses in existing systems like vulnerability to brute force and dictionary attacks. The proposed system offers stronger security against online attacks while being easy for users. It is recommended for domains like banking that require enhanced security.