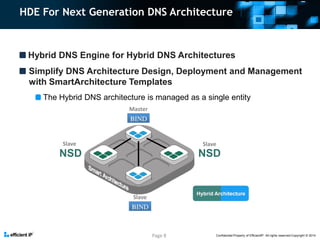
The document discusses the evolution and benefits of efficientip's hybrid DNS engine, which integrates multiple DNS technologies to enhance security and performance against rising DNS attacks. It highlights the increasing threat of DNS vulnerabilities and provides a comprehensive overview of its features, including automated management and a unified architecture for simpler deployment. The company has established a strong presence with significant clientele across various sectors, leveraging innovative software solutions since 2004.