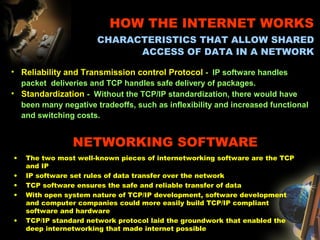
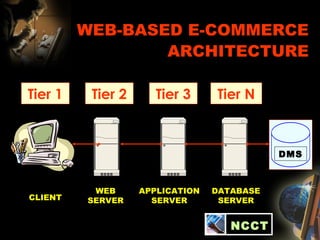
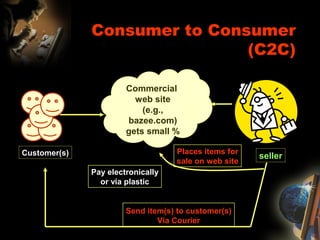
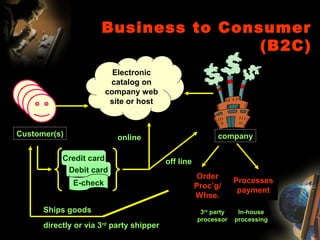
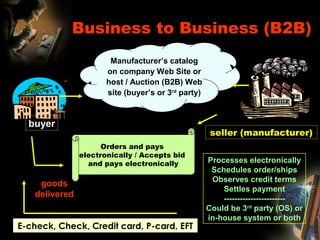
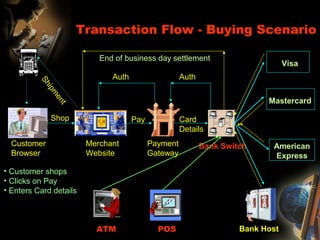
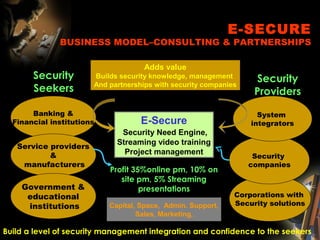
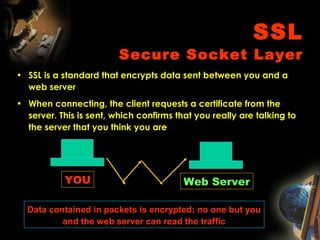
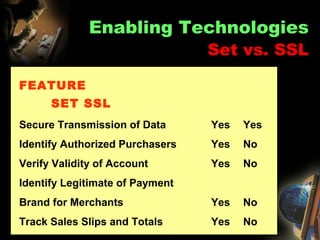
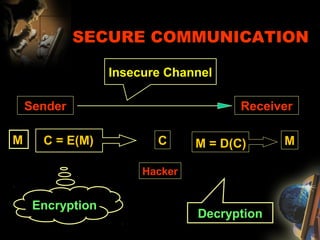
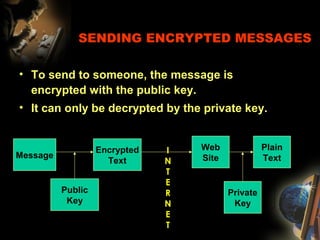
The document provides an extensive overview of NCCT, highlighting its focus on software development, particularly in e-commerce and web technologies. It covers the evolution of commerce through technological advancements, the structure and functioning of the internet, and the implications of electronic commerce on business operations. Additionally, it discusses various e-commerce models, applications, and technologies that enhance online commercial activities.