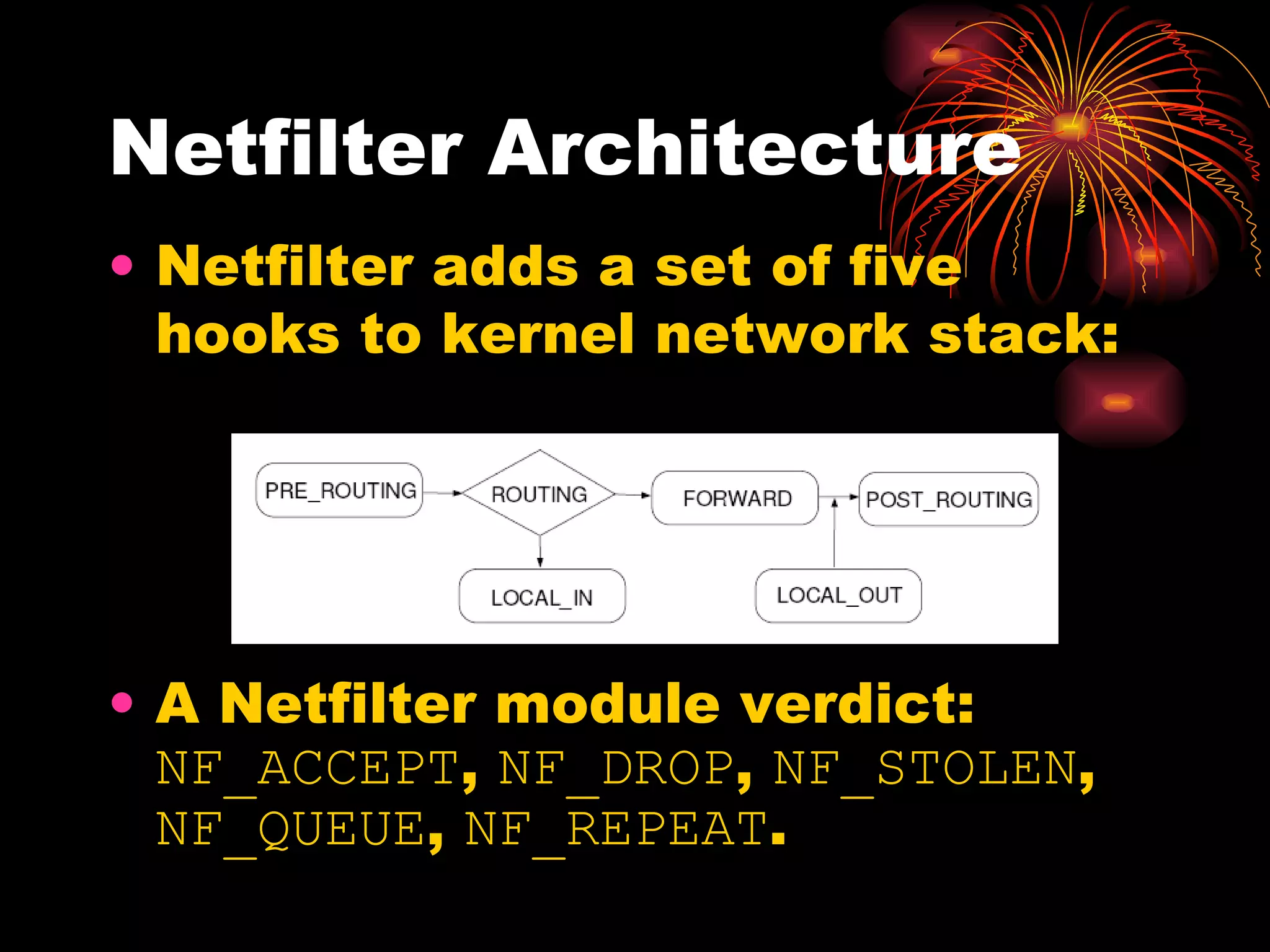
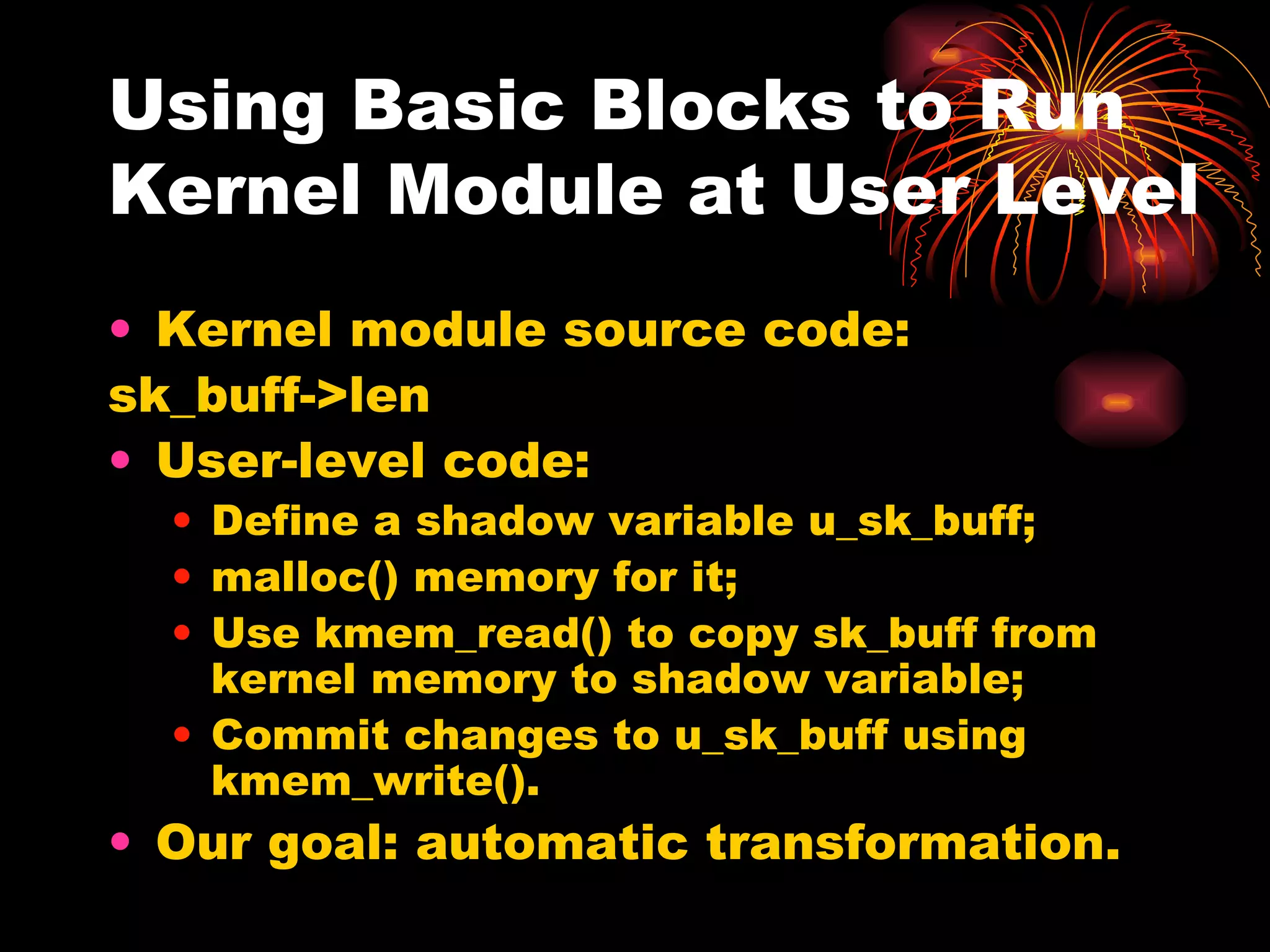
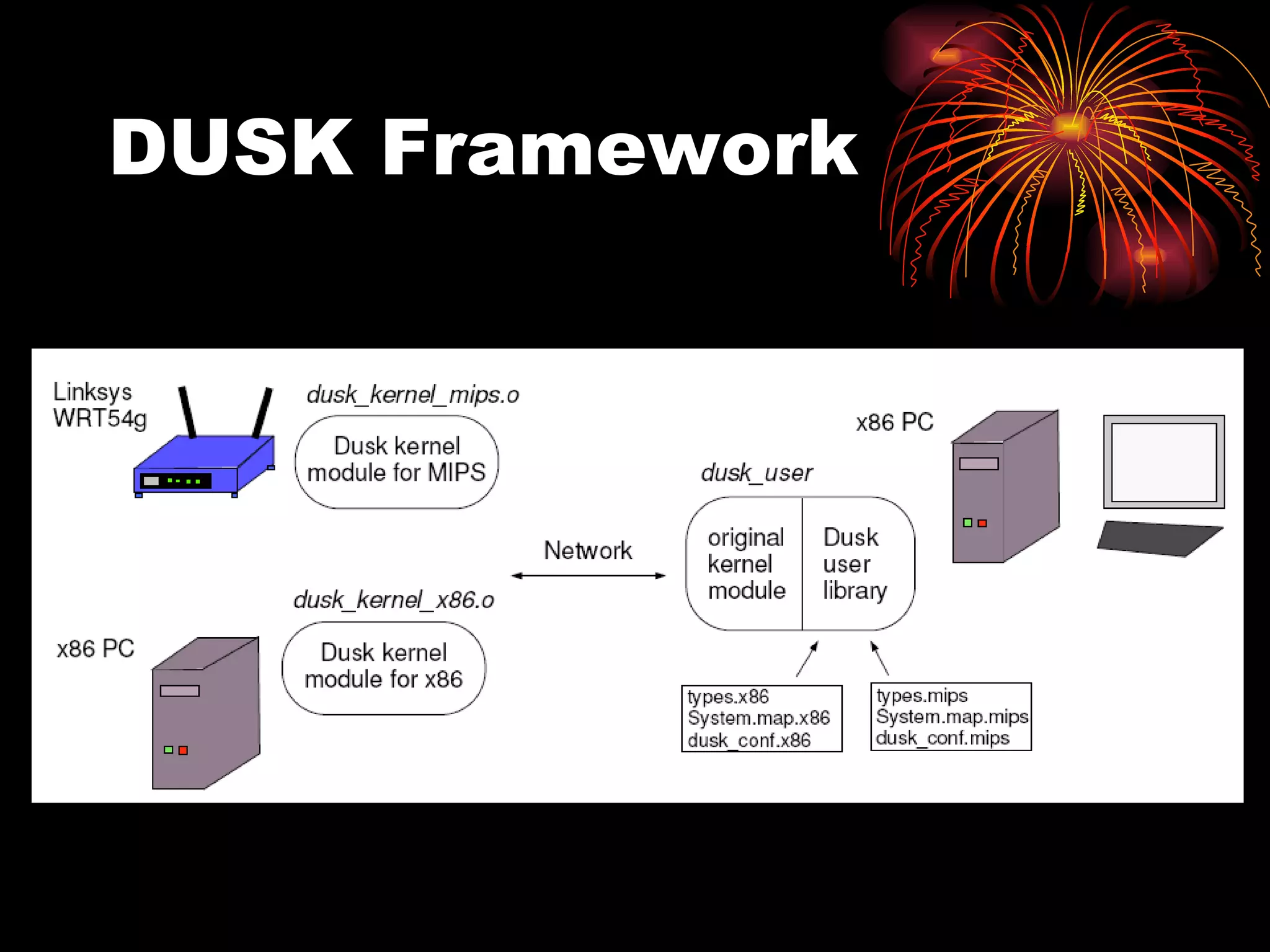
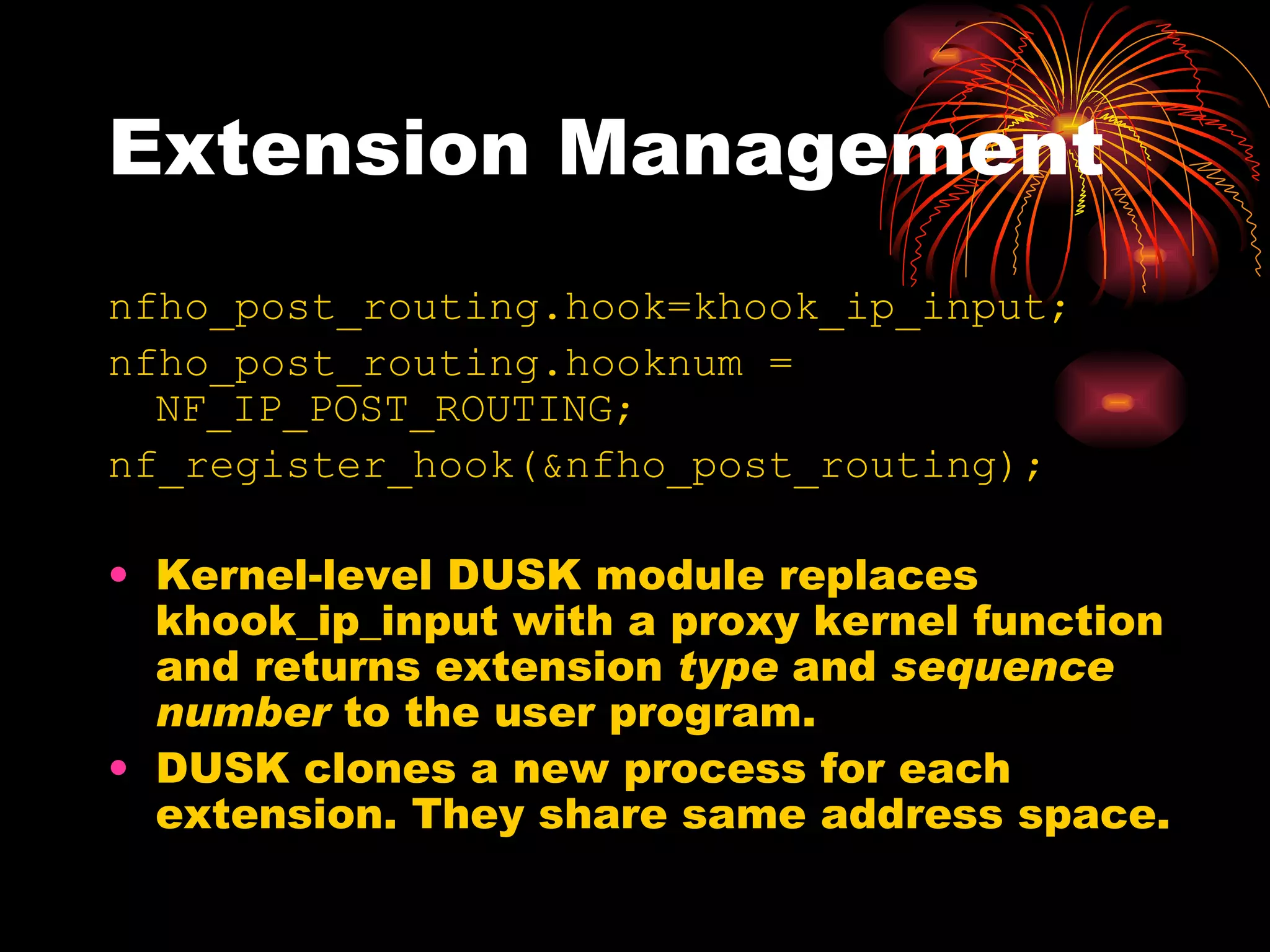
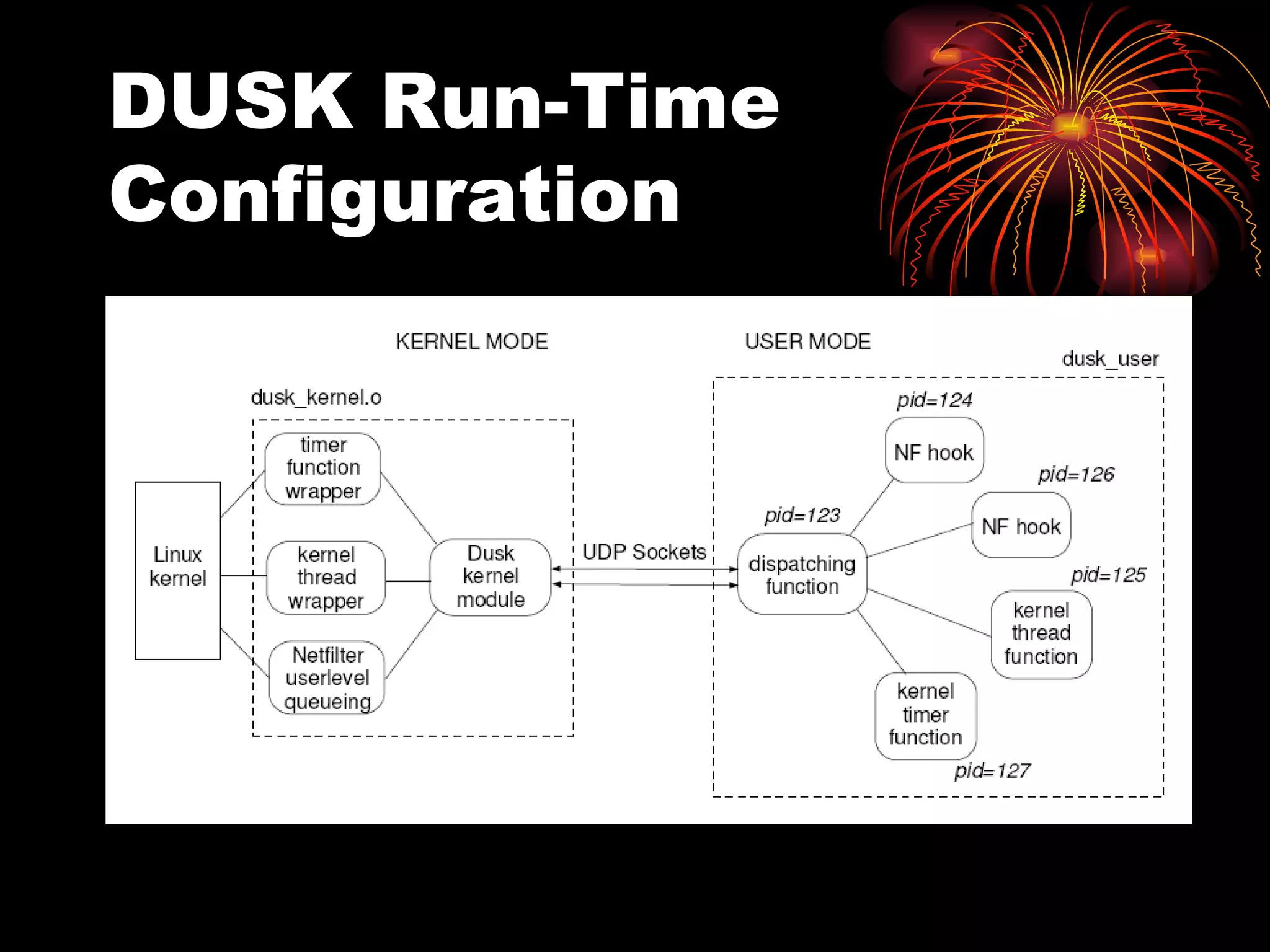
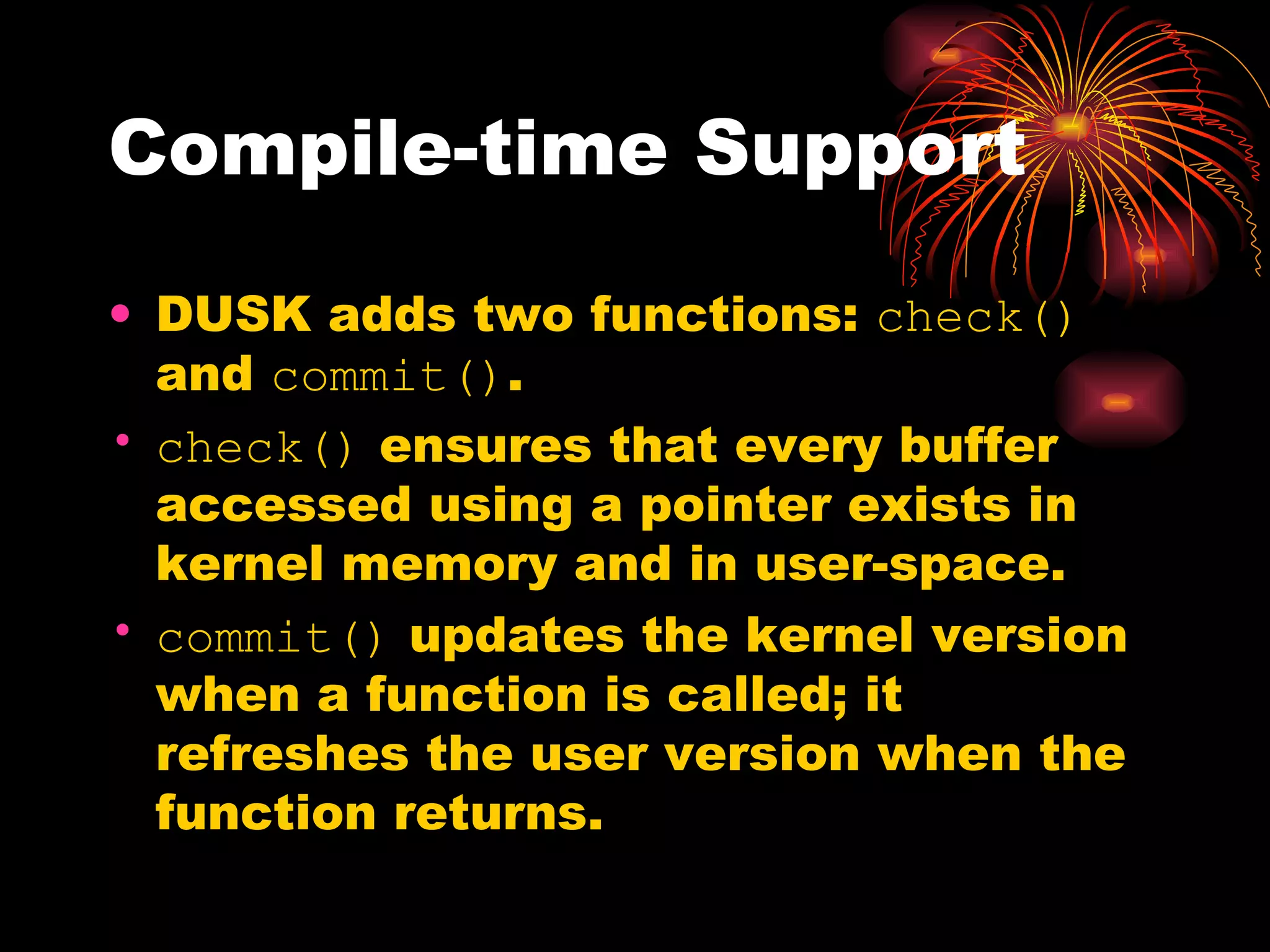
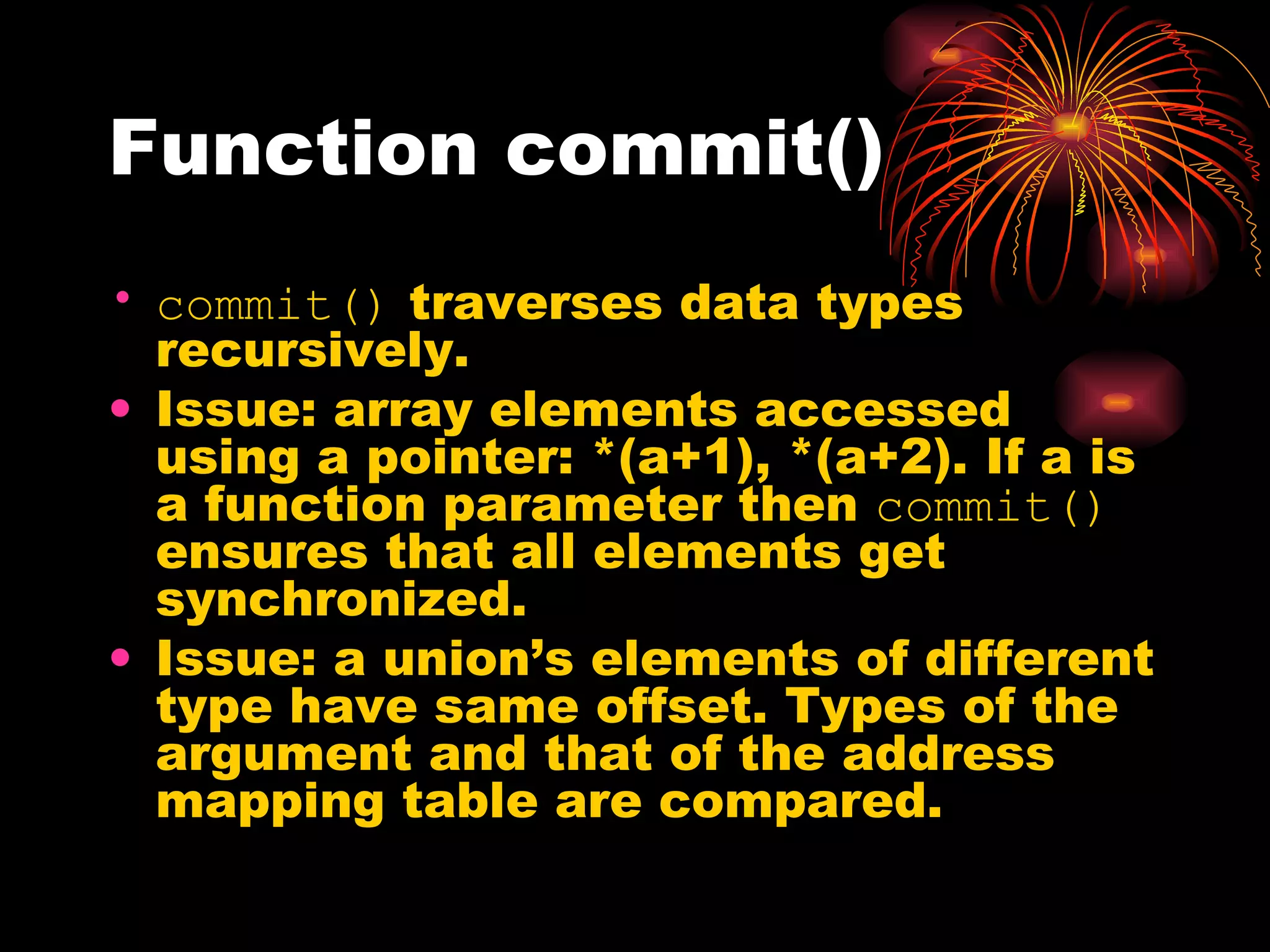
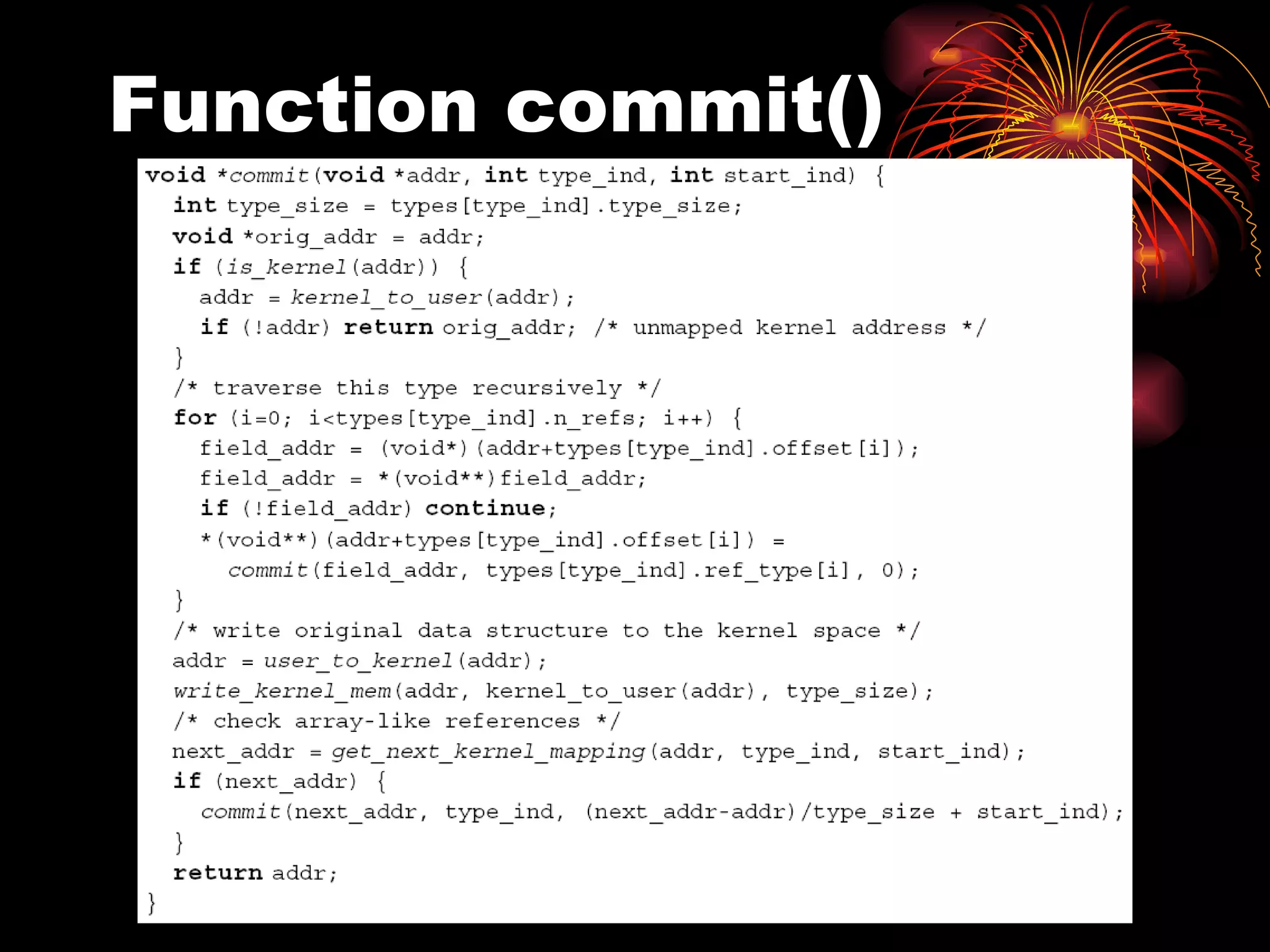
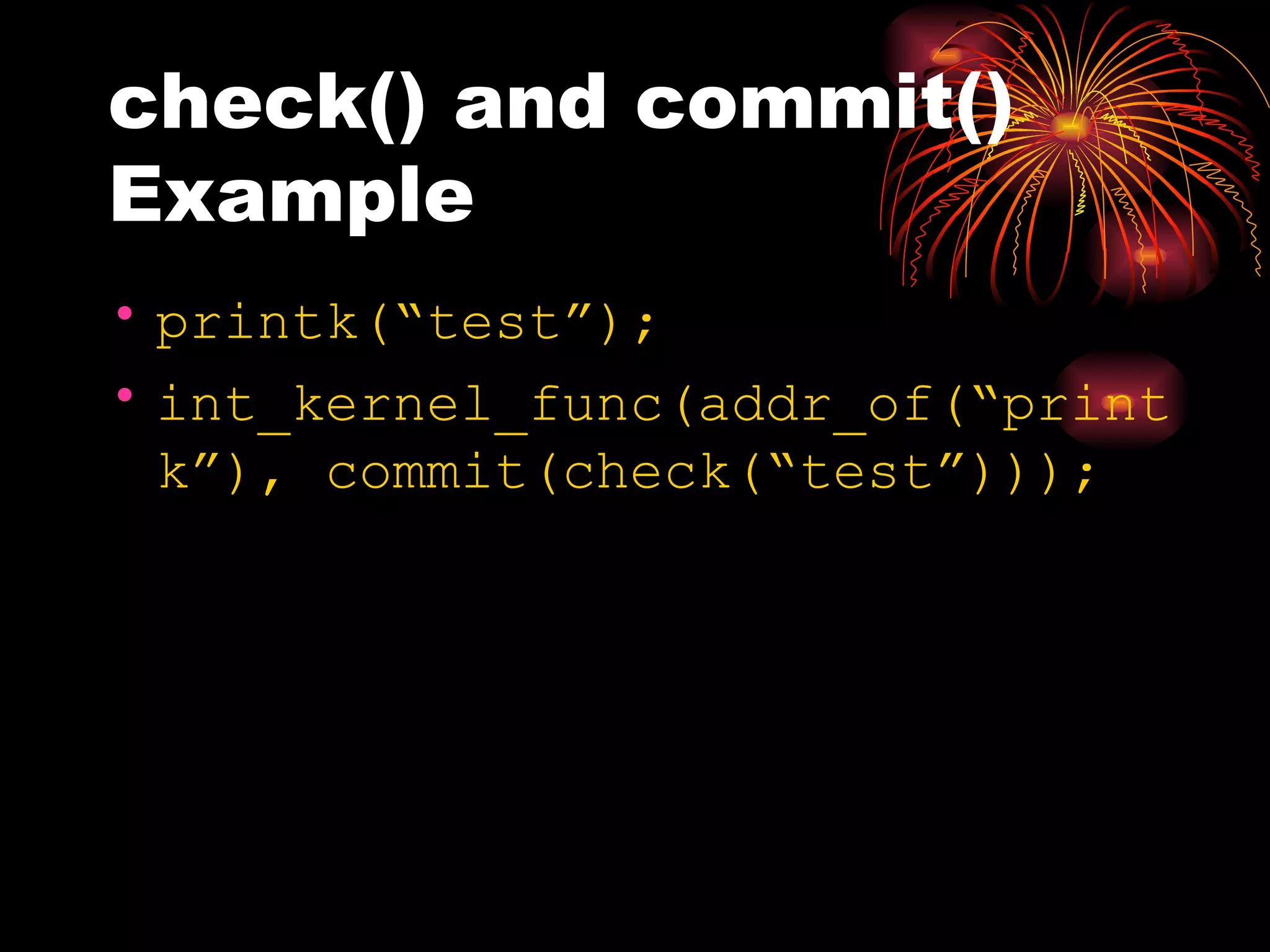
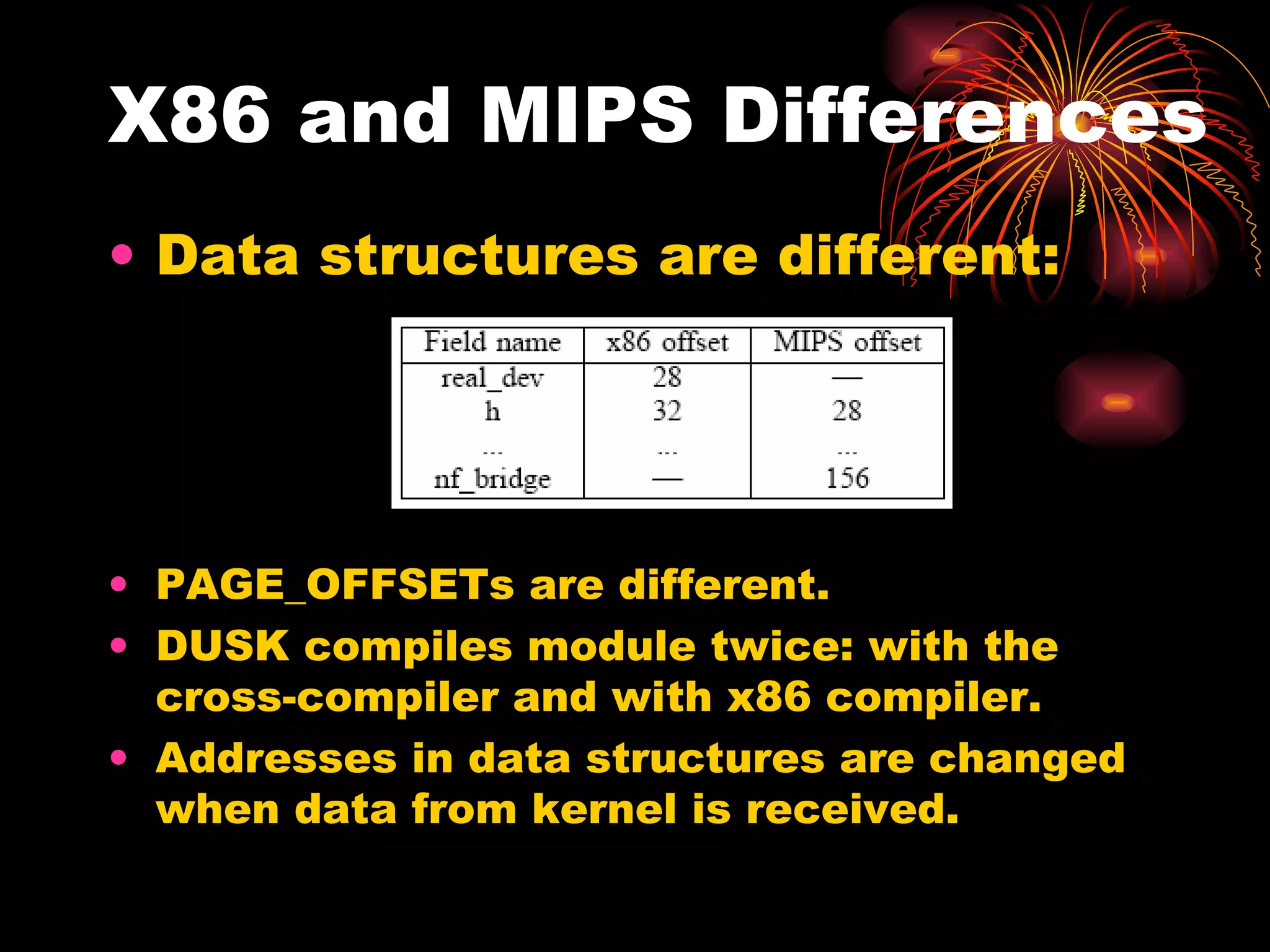
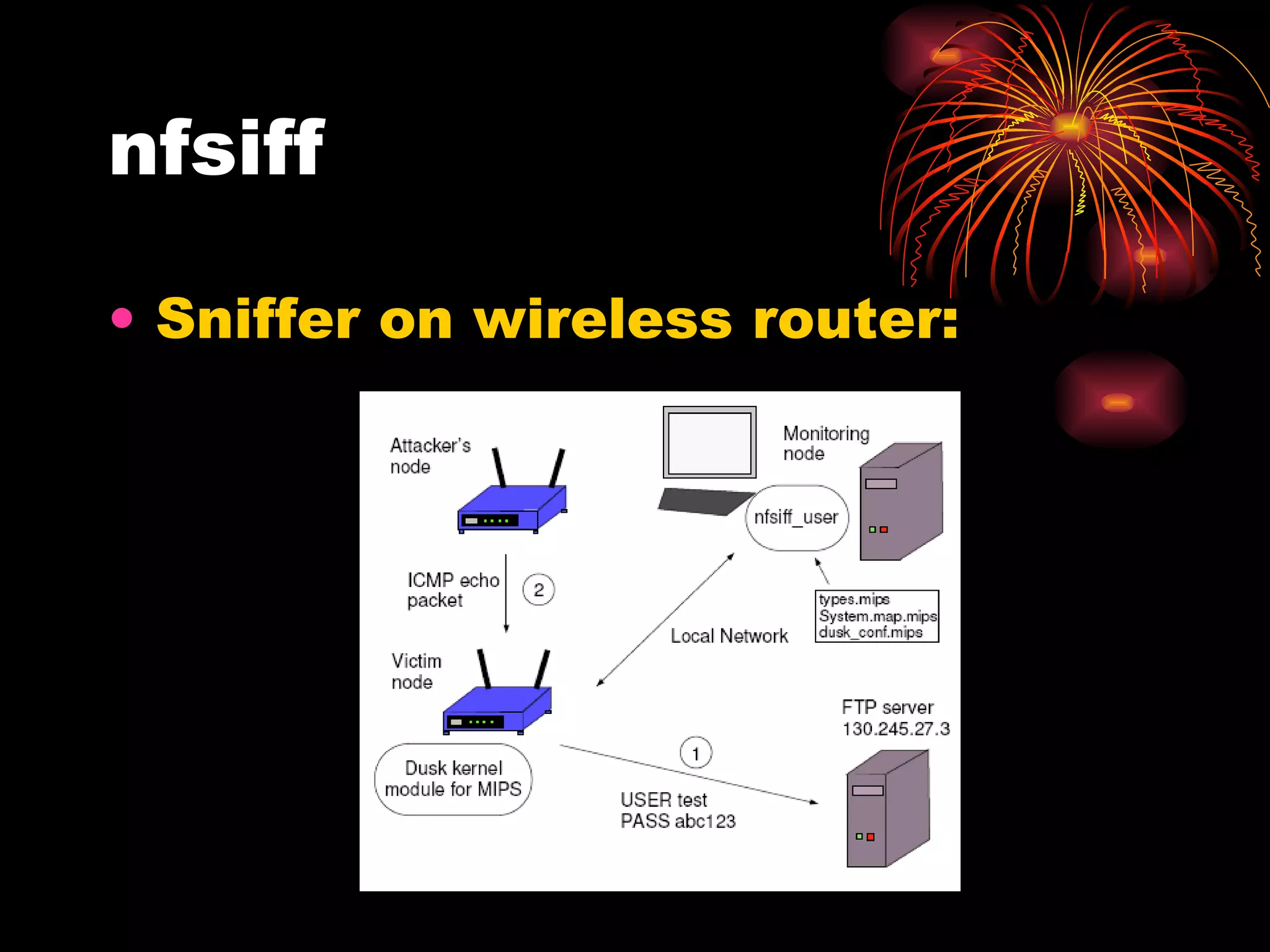
DUSK is a framework that allows kernel modules to be developed at the user level by compiling them into a user-level program while still maintaining the performance of running in the kernel. It uses helper functions to connect the user-level component to the kernel-level component, allowing things like debugging and testing to be done at the user level. DUSK supports Netfilter modules initially and aims to provide an easier development process for kernel modules.