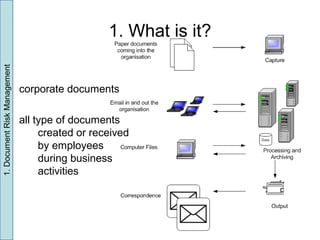
1) The document discusses document risk management and introduces the EBIOS method for managing document risks.
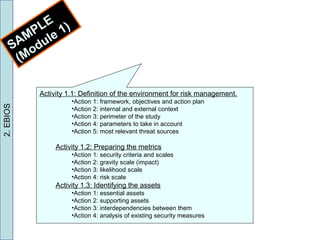
2) EBIOS is a comprehensive method developed by ANSSI that follows the ISO 31000 risk management process in 5 modules.
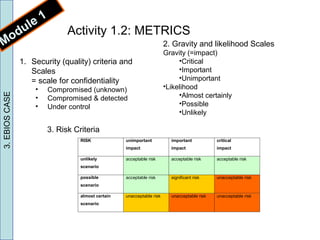
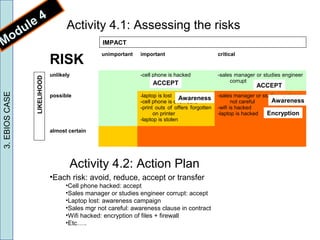
3) The document provides a case study example of applying EBIOS to assess risks to confidential price documents for a small telecom company. Risks were identified, assessed, and an action plan was developed to manage the risks.