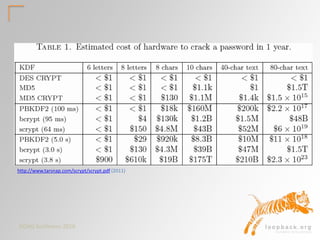
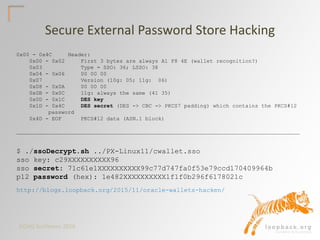
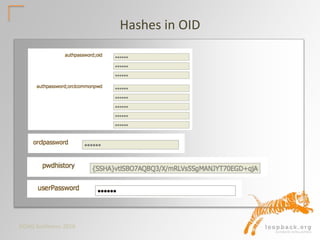
This document summarizes a presentation on database authentication methods and security. It discusses different hashing algorithms used by Oracle over time, password cracking calculations, and various authentication methods including native Oracle authentication, secure wallet stores, LDAP/OID, Kerberos integration with Active Directory, and Kerberos configuration in Oracle 12c. Key topics covered include hashing algorithms, password strength, external user security, and single sign-on authentication protocols.


![DOAG Konferenz 2016
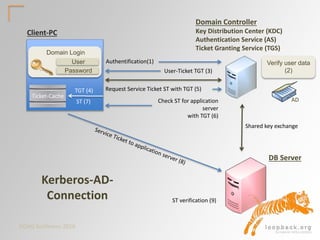
Oracle Native Authentication Protocol
Client
Oracle
Database Server
Connect [SID]
Resend
Connect [SID]
Accept
....
[Username]
[AUTH_VFR_DATA] (11g Salt)
[AUTH_SESSKEY]
[AUTH_SESSKEY]
[AUTH_PASSWORD ]
Password verification
takes place. Server
authenticates user or
responds with error.](https://image.slidesharecdn.com/doag2016logonsecurity-161120165859/85/DOAG-2016-Oracle-Logon-Security-9-320.jpg)



![DOAG Konferenz 2016
Kerberos User Login
SQL> create user USER01 identified externally as
'USER01@TESTED.LCL';
User created.
SQL> grant connect to user01;
[oracle@ioaotow01 ~]$ okinit user01
Kerberos Utilities for Linux: Version 12.1.0.2.0 - Production
Copyright (c) 1996, 2014 Oracle. All rights reserved.
Password for user01@TESTED.LCL:
_______________________________________________________________________________________________
[oracle@ioaotow01 ~]$ oklist
Kerberos Utilities for Linux: Version 12.1.0.2.0 - Production on 08-FEB-2016 16:24:43
Copyright (c) 1996, 2014 Oracle. All rights reserved.
Ticket cache: /oracle/diag/krb/cc/krb5cc_99
Default principal: user01@TESTED.LCL
Valid Starting Expires Principal
08-Feb-2016 14:11:20 08-Feb-2016 22:11:11 krbtgt/TESTED.LCL@TESTED.LCL
08-Feb-2016 14:11:33 08-Feb-2016 22:11:11 oracle/ioaotow01@TESTED.LCL
08-Feb-2016 14:16:40 08-Feb-2016 22:11:11 oracle/ioaotow01.tested.lcl@TESTED.LCL
_______________________________________________________________________________________________
[oracle@ioaotow01 ~]$ sqlplus /@TESTDB
SQL*Plus: Release 12.1.0.2.0 Production on Mon Feb 8 16:24:51 2016
Copyright (c) 1982, 2014, Oracle. All rights reserved.
Last Successful login time: Mon Feb 08 2016 14:17:35 +01:00
Connected to: Oracle Database 12c Enterprise Edition Release 12.1.0.2.0 - 64bit Production With
the Partitioning, OLAP, Advanced Analytics and Real Application Testing options
SQL> show user;
USER is "USER01@TESTED.LCL](https://image.slidesharecdn.com/doag2016logonsecurity-161120165859/85/DOAG-2016-Oracle-Logon-Security-17-320.jpg)
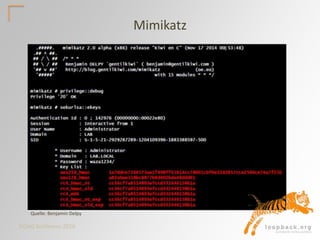
![DOAG Konferenz 2016
AD-Integration with Oracle
Unified Directory (OUD) & Kerberos
DB FARM
OUD
Database
Client
SqlPlus,
Java, etc
(EUS)
Map Users,
Schema,Roles
Groups
OracleContext
OUD Proxy Setup:
• AD-User w/ read privilege
• Read privilege on DB-user
data in AD
• Oracle Context on LDAP
server
• Software: OUD,
WebLogic, ADF
• Works with EUS also[linux7 Oracle_OUD1]$ ./oud-proxy-setup
[linux6]$ okinit testuser
[linux7]$ oklist
Kerberos Ticket
https://wiki.loopback.org/confluence/x/FQCl](https://image.slidesharecdn.com/doag2016logonsecurity-161120165859/85/DOAG-2016-Oracle-Logon-Security-18-320.jpg)



![DOAG Konferenz 2016
Display Wallet
[oracle@linux11 ~]$ orapki wallet display -wallet
/u01/app/oracle/product/11.2.0/dbhome_1/network/pki
Oracle PKI Tool : Version 11.2.0.3.0 - Production
Copyright (c) 2004, 2011, Oracle and/or its affiliates. All rights reserved.
_________________________________________________________________________________________
Requested Certificates:
User Certificates:
Subject: CN=LOOPDS
Trusted Certificates:
Subject: OU=Class 1 Public Primary Certification Authority,O=VeriSign, Inc.,C=US
Subject: CN=LBO Root Certificate II,OU=LoopCA,O=Loopback.ORG
GmbH,O=Loopback.ORG,L=Hamburg,ST=No-State,C=DE
Subject: OU=Secure Server Certification Authority,O=RSA Data Security, Inc.,C=US
Subject: CN=GTE CyberTrust Global Root,OU=GTE CyberTrust Solutions, Inc.,O=GTE
Corporation,C=US
Subject: OU=Class 3 Public Primary Certification Authority,O=VeriSign, Inc.,C=US
Subject: OU=Class 2 Public Primary Certification Authority,O=VeriSign, Inc.,C=US](https://image.slidesharecdn.com/doag2016logonsecurity-161120165859/85/DOAG-2016-Oracle-Logon-Security-24-320.jpg)