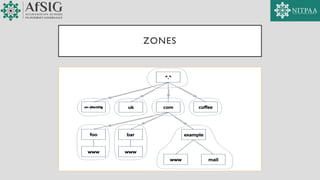
The document discusses the fundamentals of internet naming, addressing, and routing, highlighting the role of the Domain Name System (DNS) in translating human-readable names to IP addresses for easier navigation. It also covers the architecture of DNS, including the resolution process and various types of DNS abuse, such as phishing and DDoS attacks. The content presents an overview of principles discussed during ICANN 58, emphasizing the importance of DNS in maintaining internet usability and security.