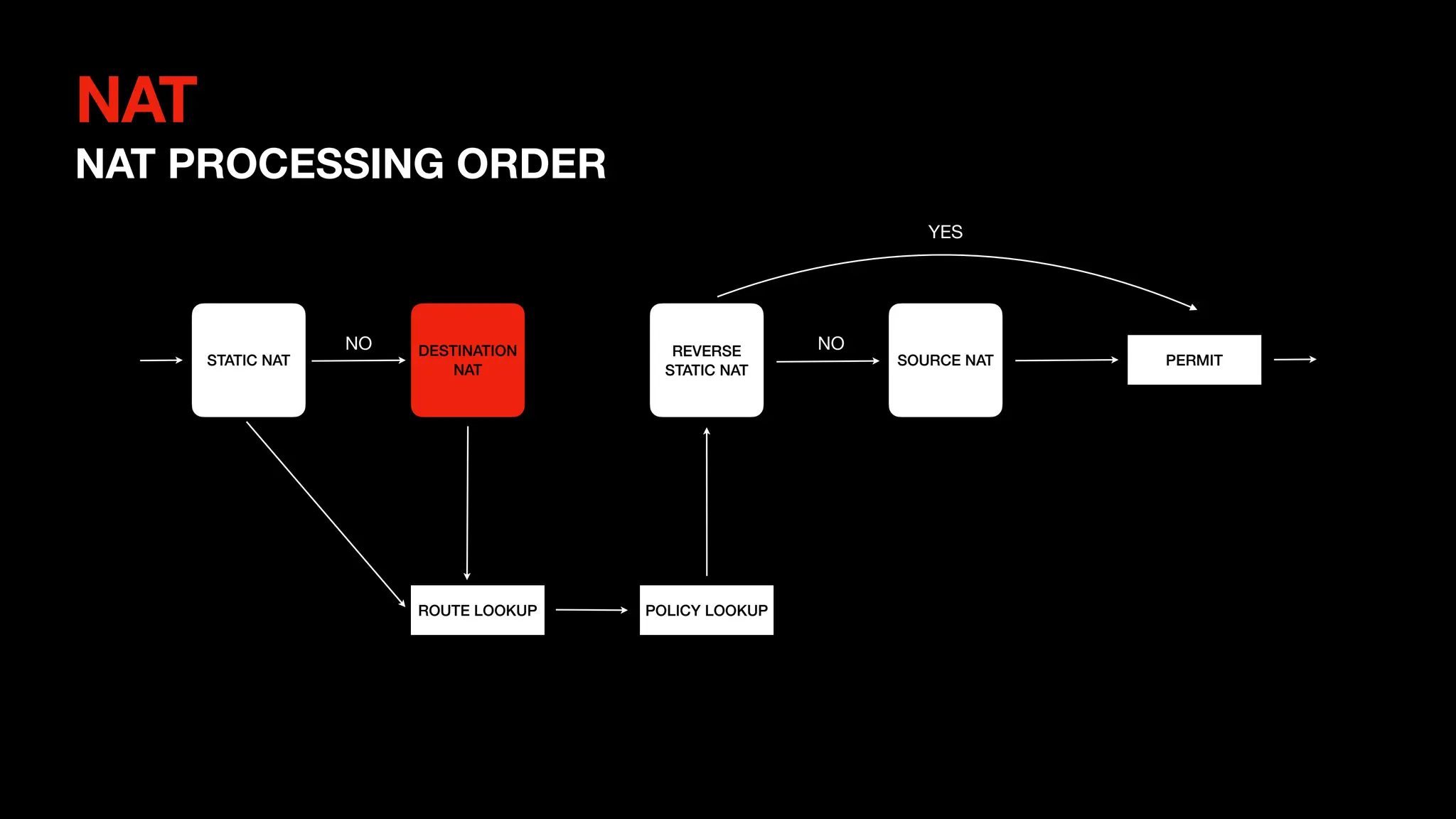
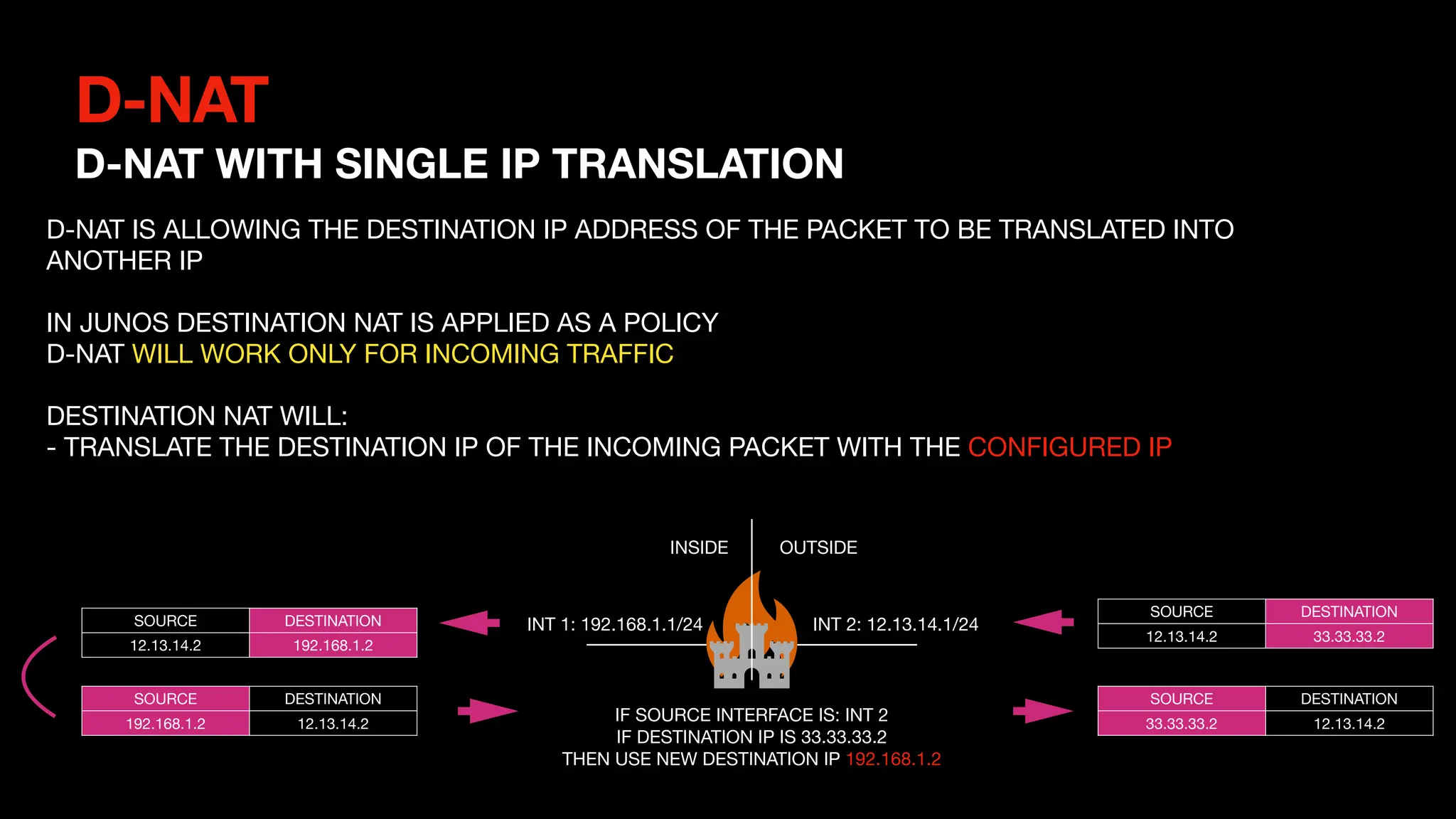
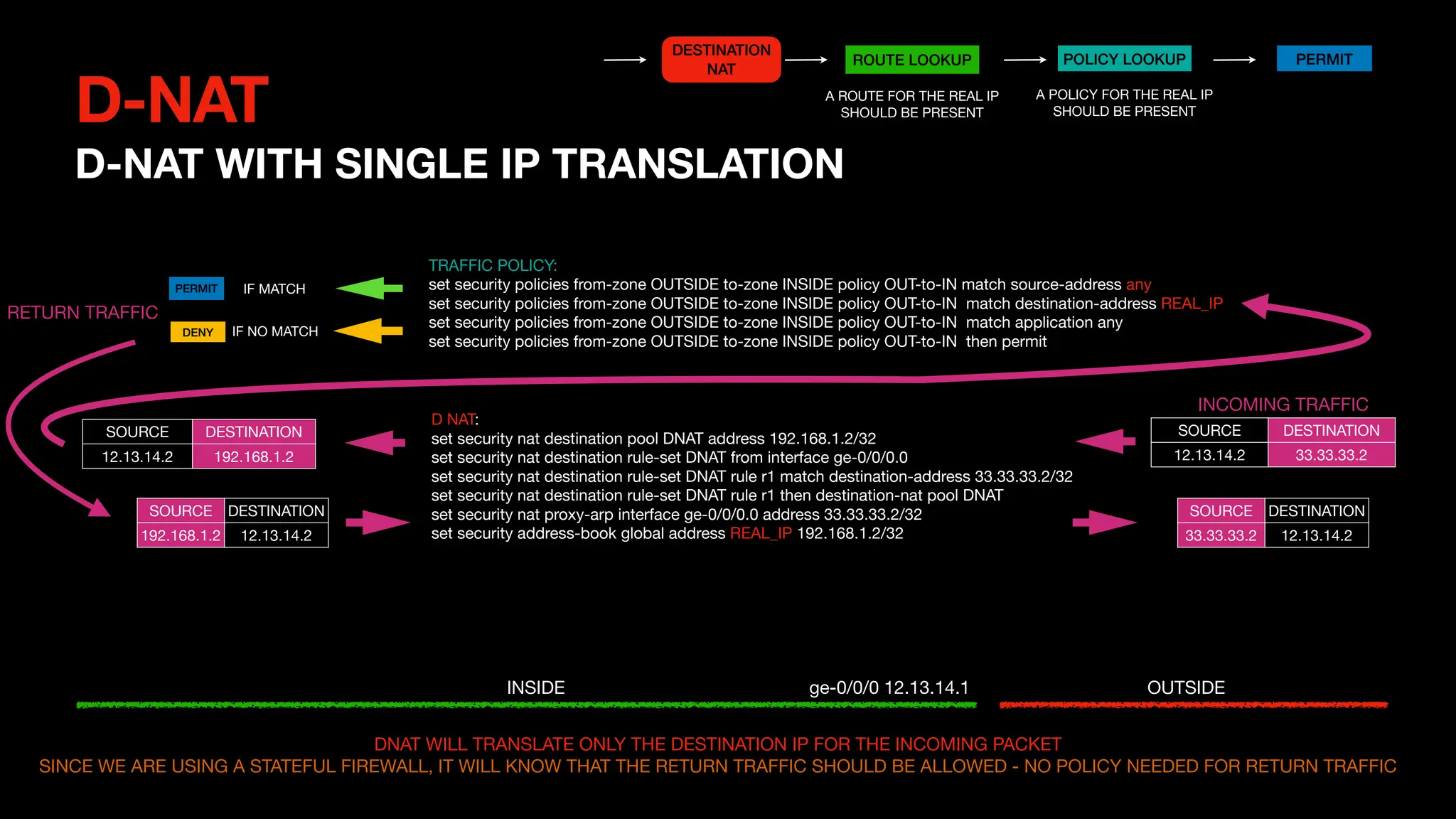
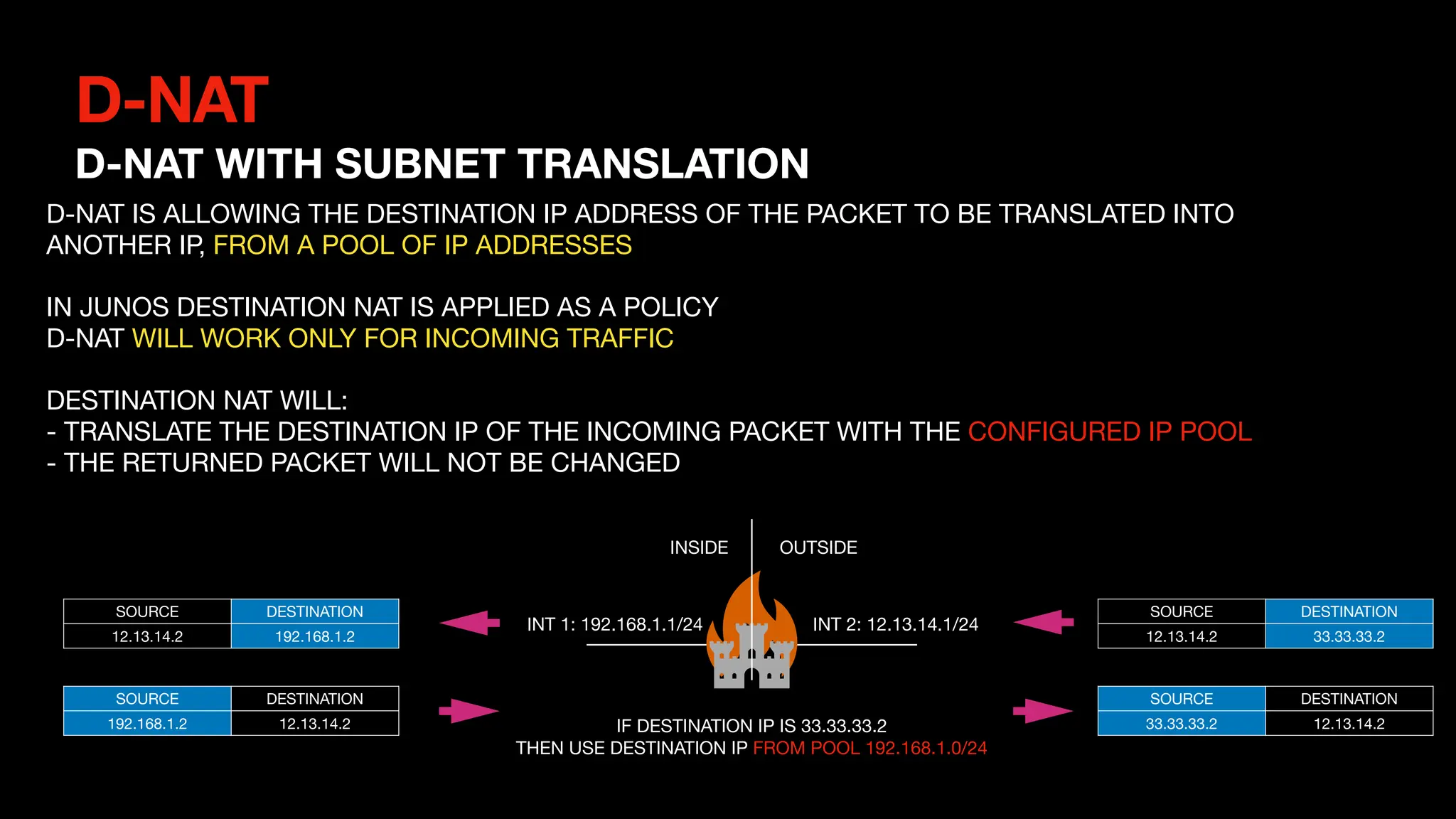
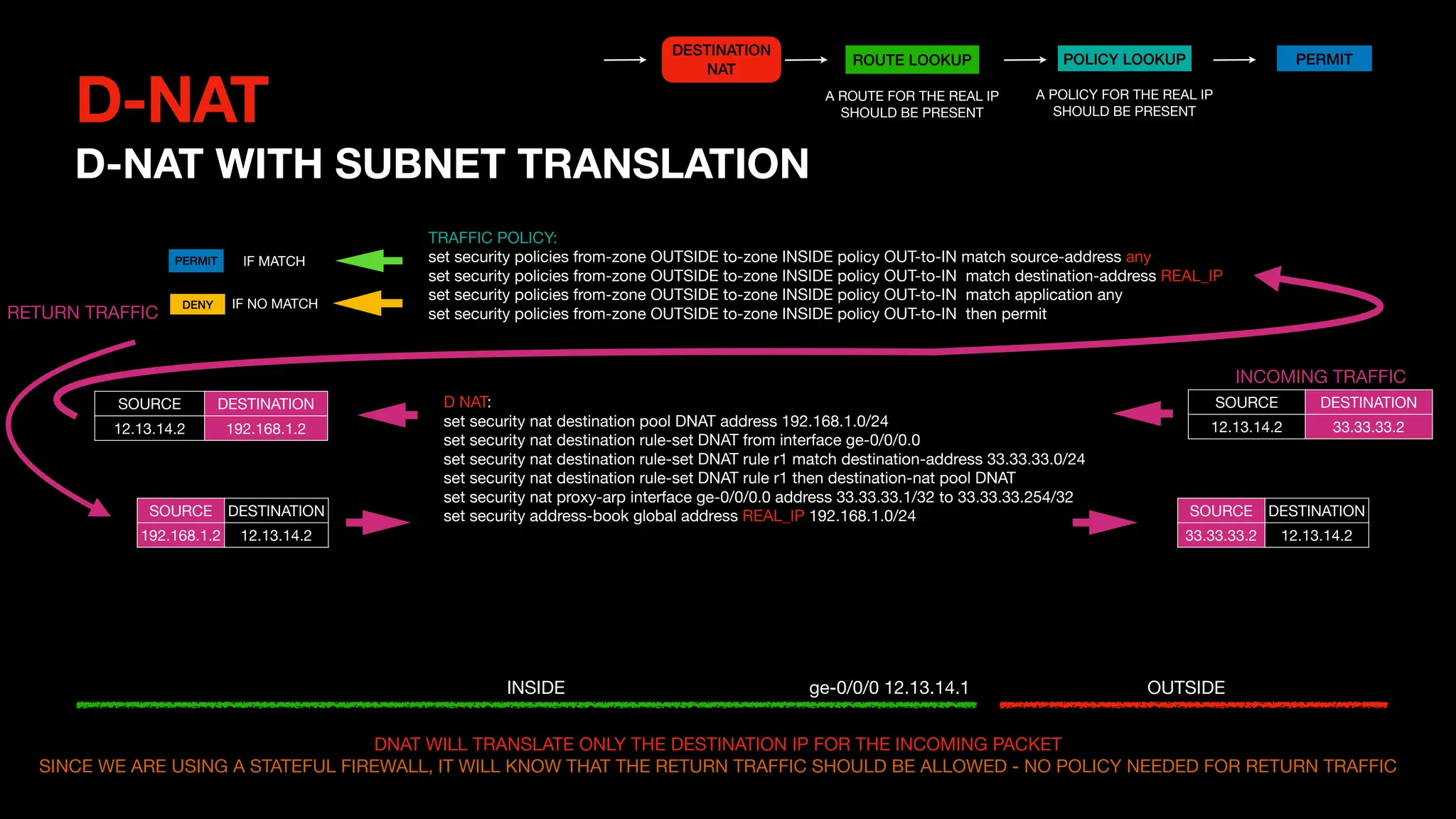
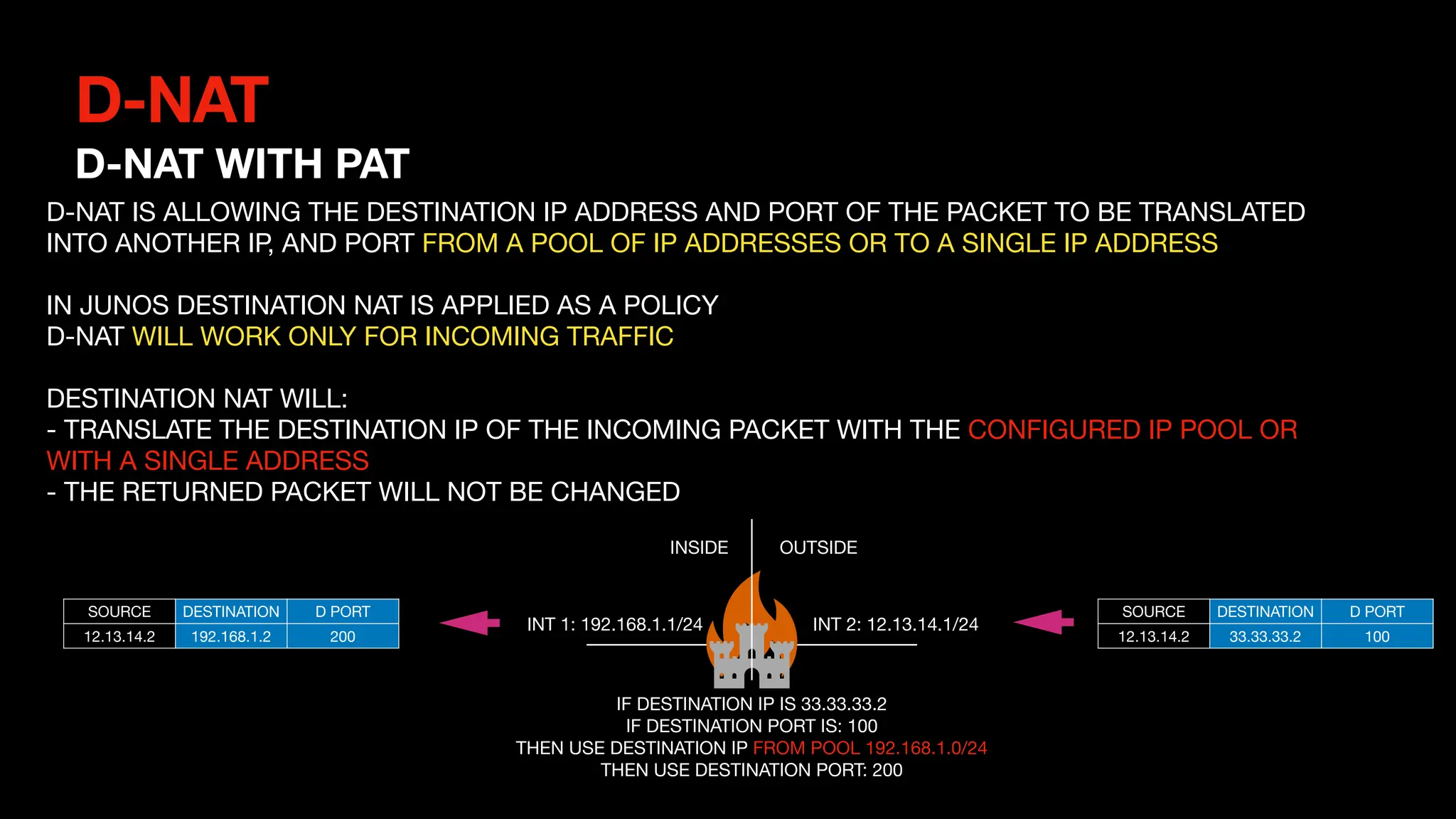
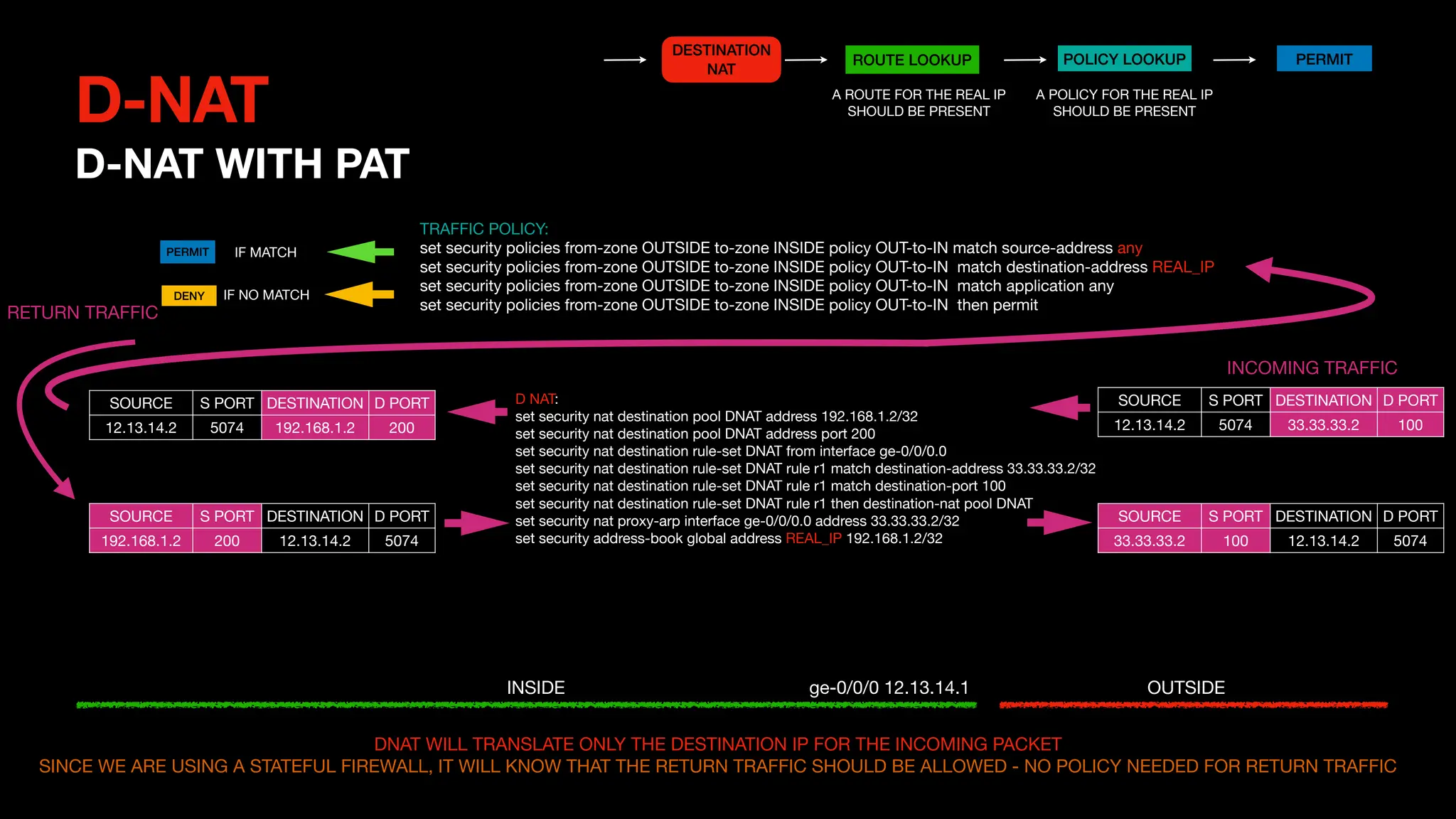
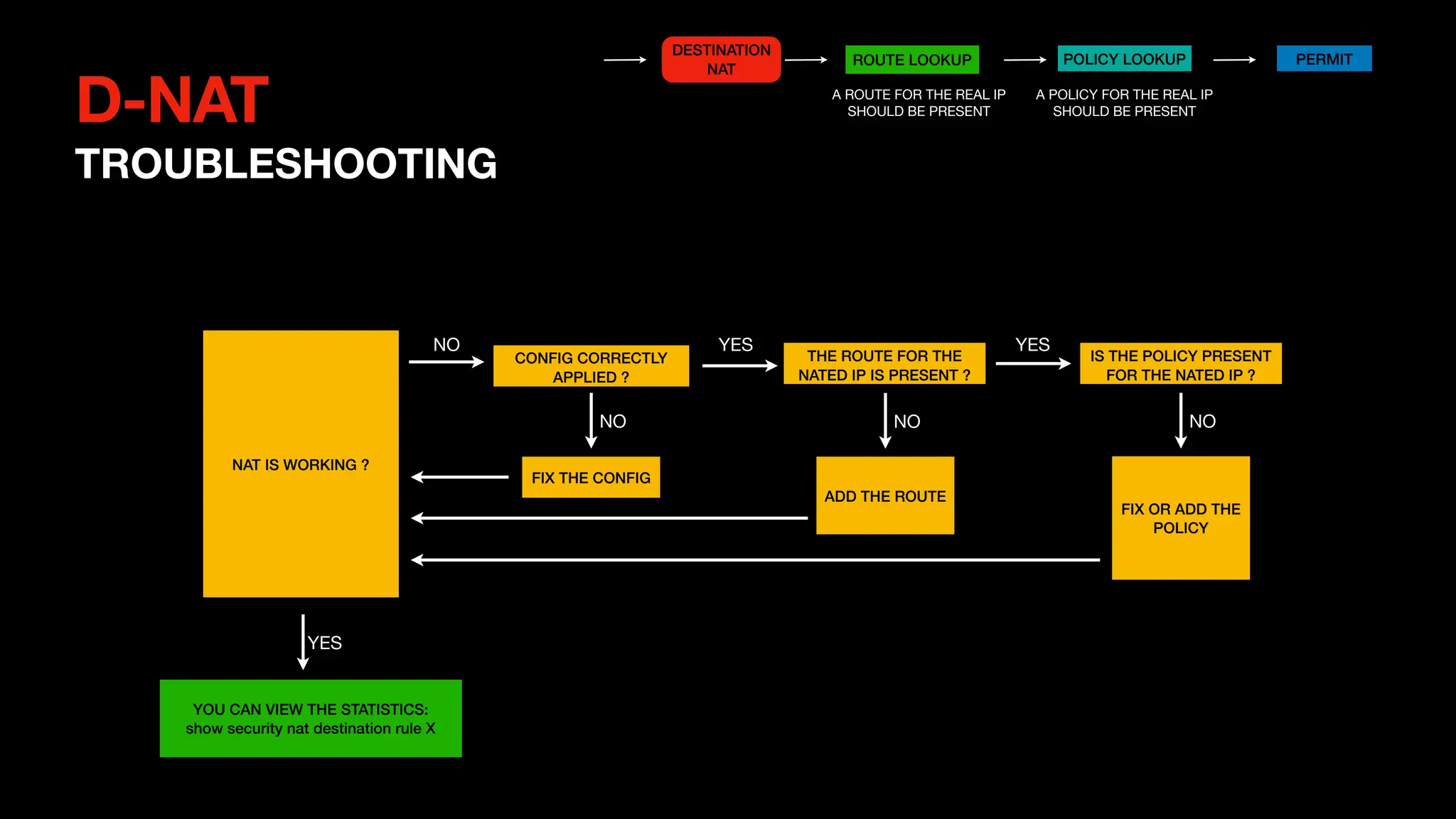
This document outlines the concepts and configurations related to destination Network Address Translation (D-NAT), including key topics like public vs private IP addresses, types of NAT, and processing order. It covers various configurations for D-NAT scenarios, including single IP translation, subnet translation, and Port Address Translation (PAT), and emphasizes the application of D-NAT policies in Junos. Troubleshooting guidelines for D-NAT are also provided to ensure correct configurations and functionality.