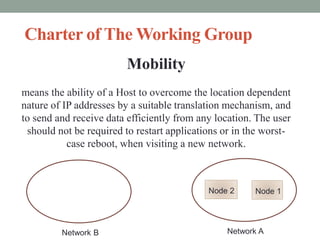
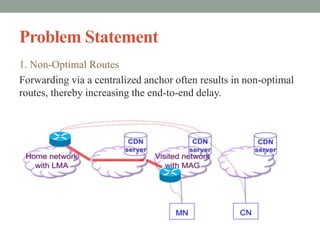
The document discusses Distributed Mobility Management (DMM), which aims to optimize traffic distribution without relying on centralized mobility anchors, thereby improving efficiency and scalability in mobile networking. It covers the requirements and solutions for addressing common issues in mobility management, including optimizing routes, handling mobile node identifiers securely, and ensuring compatibility with existing protocols. The document outlines the need for a transparent solution above the IP layer and emphasizes security considerations for DMM implementations.