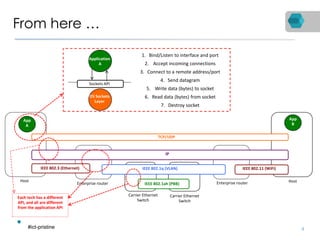
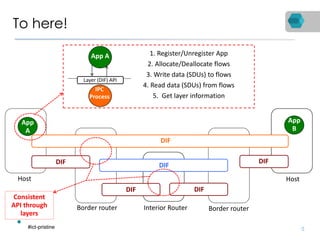
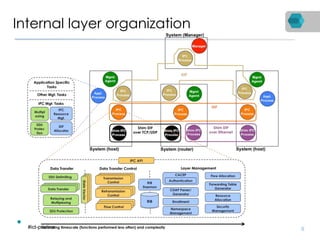
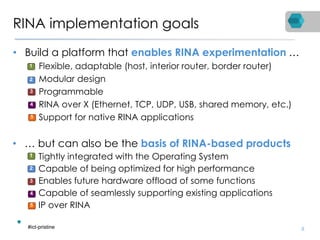
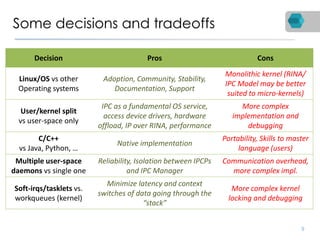
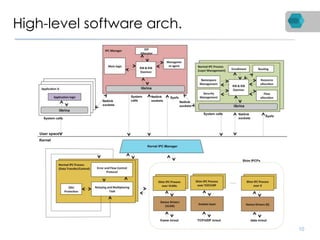
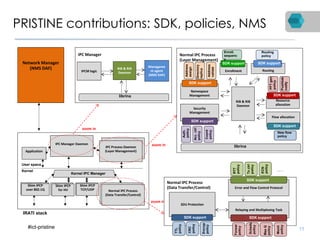
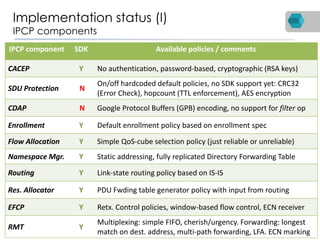
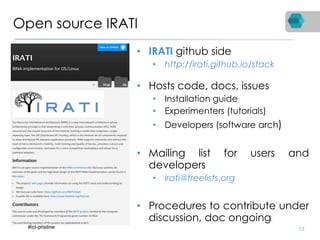
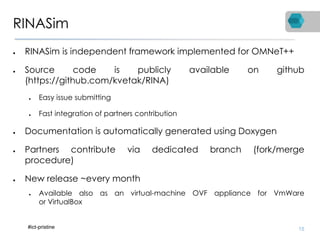
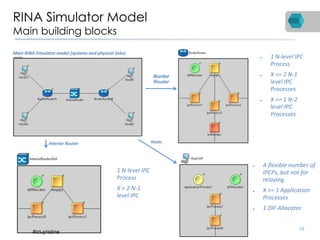
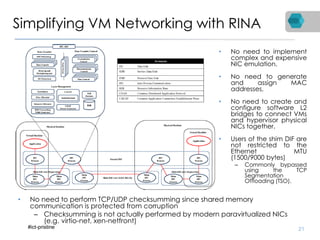
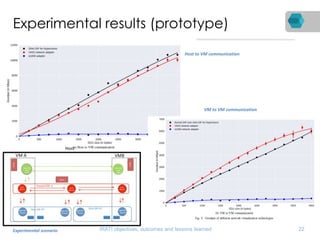
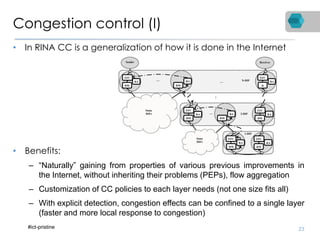
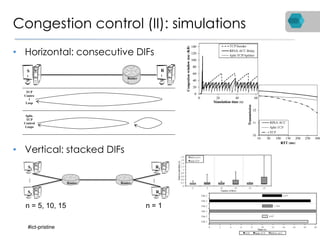
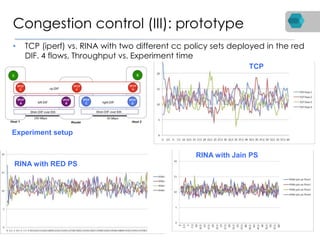
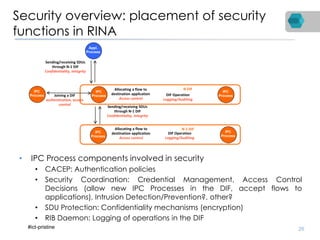
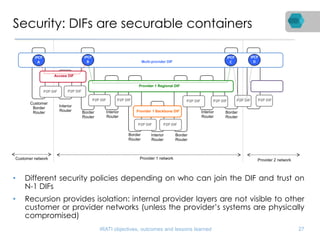
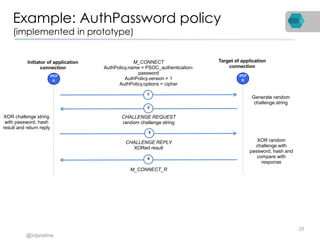
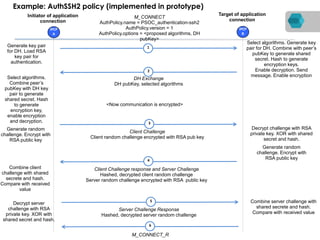
RINA is a new network architecture that provides a consistent API across layers through a recursive model. The PRISTINE project has made advances in RINA including developing an open source implementation called IRATI and a simulator called RINASim. IRATI focuses on being flexible, modular, and programmable. Key components like IPC processes and policies are under development. Experiments show potential benefits of RINA for areas like congestion control, security, and simplifying VM networking. Further work includes improving core protocols, developing policy specifications, quantifying benefits, and engaging with standards bodies.