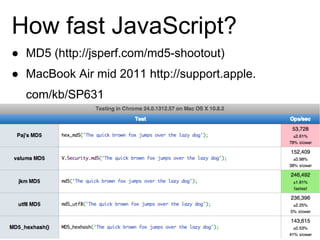
This document discusses using distributed computing via browsers as a potential client-side attack. It outlines resources like CPU, GPU, RAM, and storage that are available to websites through browsers. While distributed computing in browsers is not new, it could be used maliciously for attacks like XSS, CSRF, or malware distribution. The document then examines ways this could be done using techniques like web workers, local storage, and Flash to bypass restrictions on CPU and storage usage. It provides examples of how fast hashing algorithms can run in JavaScript and Flash compared to dedicated hardware. In the end, it questions whether optimizations could further increase speeds for distributed attacks using browser resources.




![Distributed computing in
browsers not so new theme
● Browser-based distributed evolutionary computation:
performance and scaling behavior [2007]
○ http://dl.acm.org/citation.cfm?id=1274083
● Unwitting distributed genetic programming via
asynchronous JavaScript and XML [2007]
○ http://dl.acm.org/citation.cfm?id=1277282](https://image.slidesharecdn.com/distributedcomputinginbrowsersasclient-sideattack-130223165946-phpapp02/85/Distributed-computing-in-browsers-as-client-side-attack-5-320.jpg)








![How fast Flash?
http://www.blooddy.by/ru/crypto/benchmark/
● SHA-256
○ mx.utils.SHA256
○ as3corelib
○ blooddy [x8 faster]
● MD5
○ as3corelib
○ blooddy [x10 faster]](https://image.slidesharecdn.com/distributedcomputinginbrowsersasclient-sideattack-130223165946-phpapp02/85/Distributed-computing-in-browsers-as-client-side-attack-16-320.jpg)


![???
@ONsec_Lab [http://lab.ONsec.ru]
@d0znpp
d0znpp@onsec.ru](https://image.slidesharecdn.com/distributedcomputinginbrowsersasclient-sideattack-130223165946-phpapp02/85/Distributed-computing-in-browsers-as-client-side-attack-19-320.jpg)