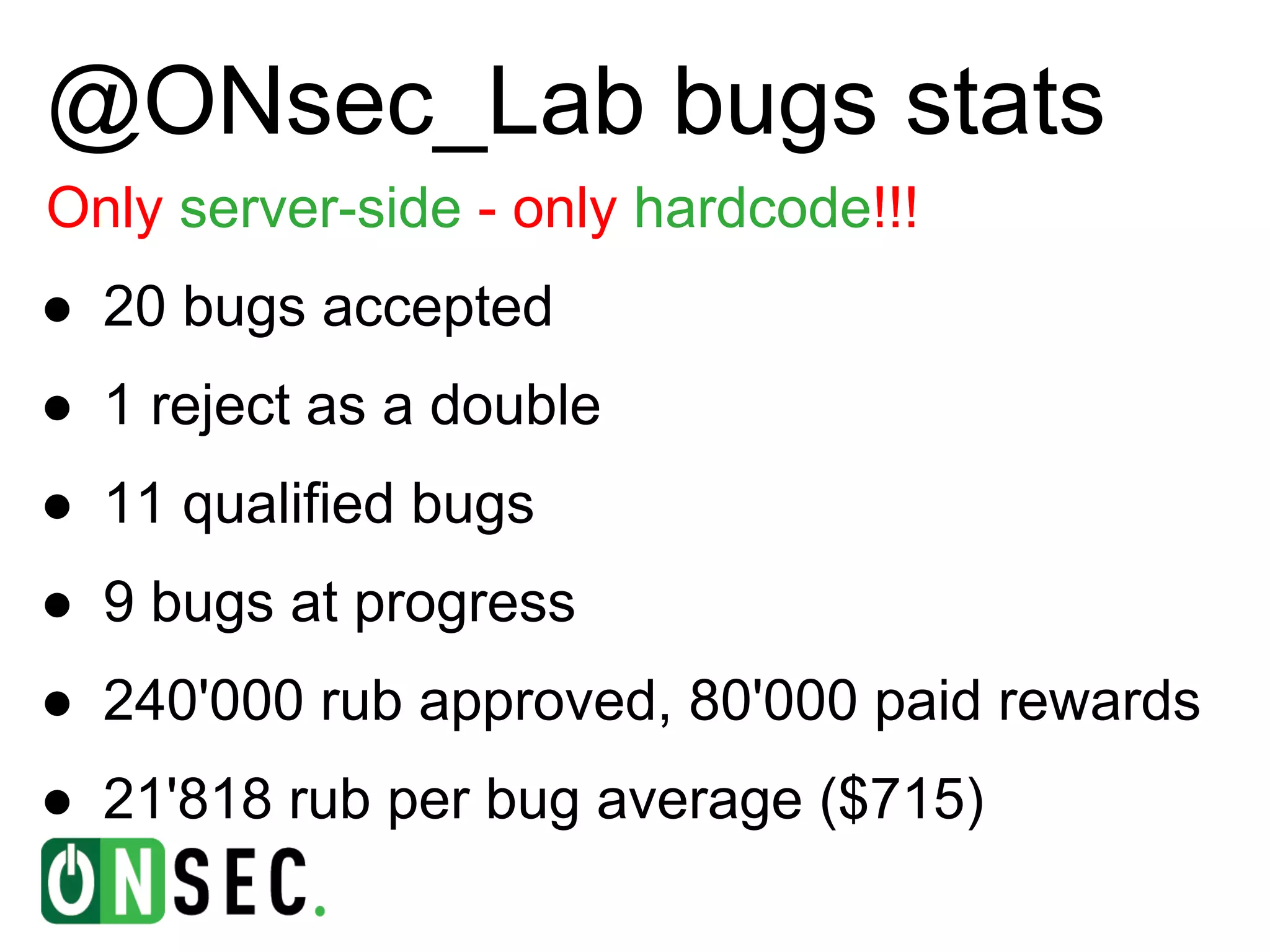
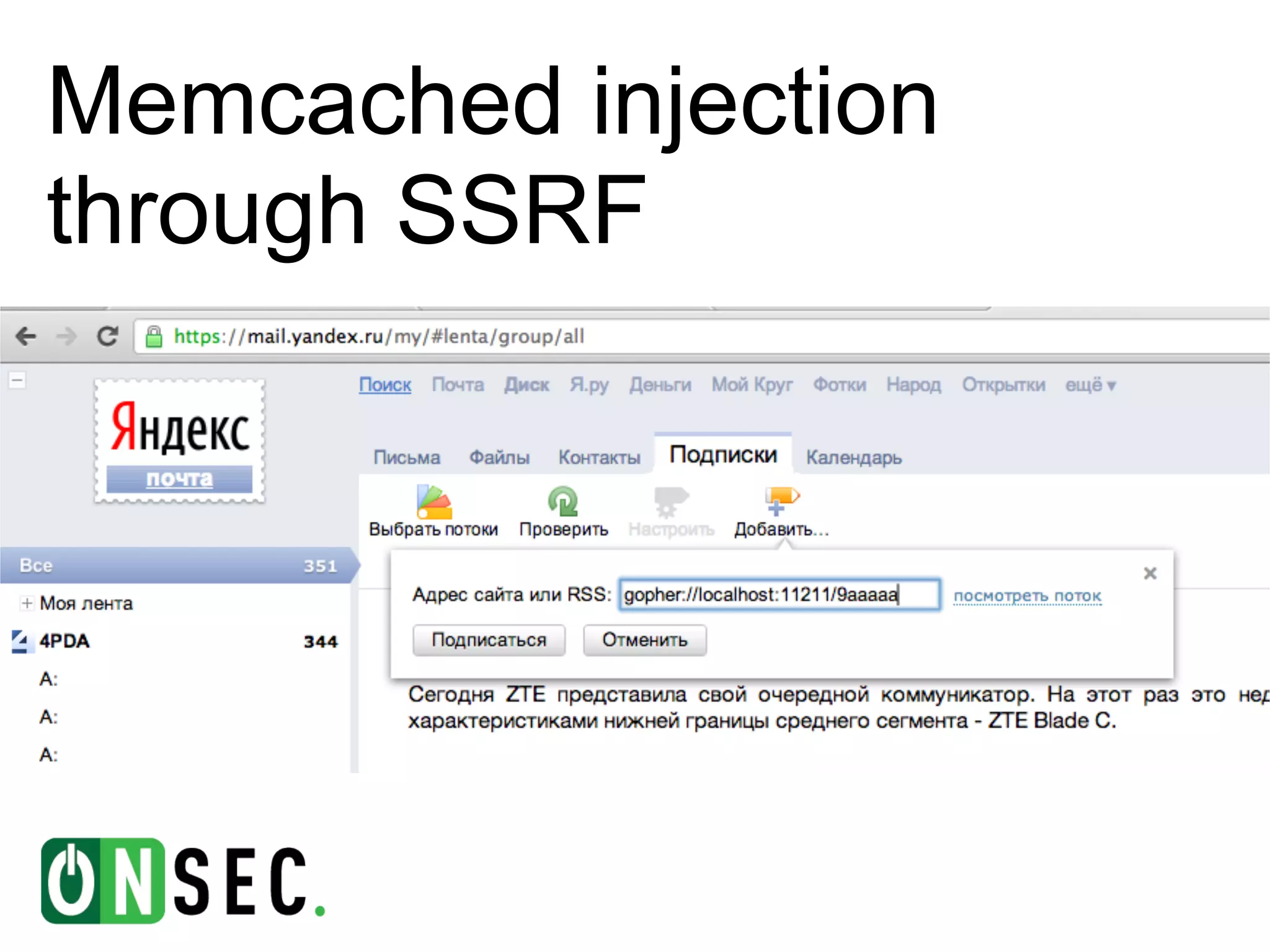
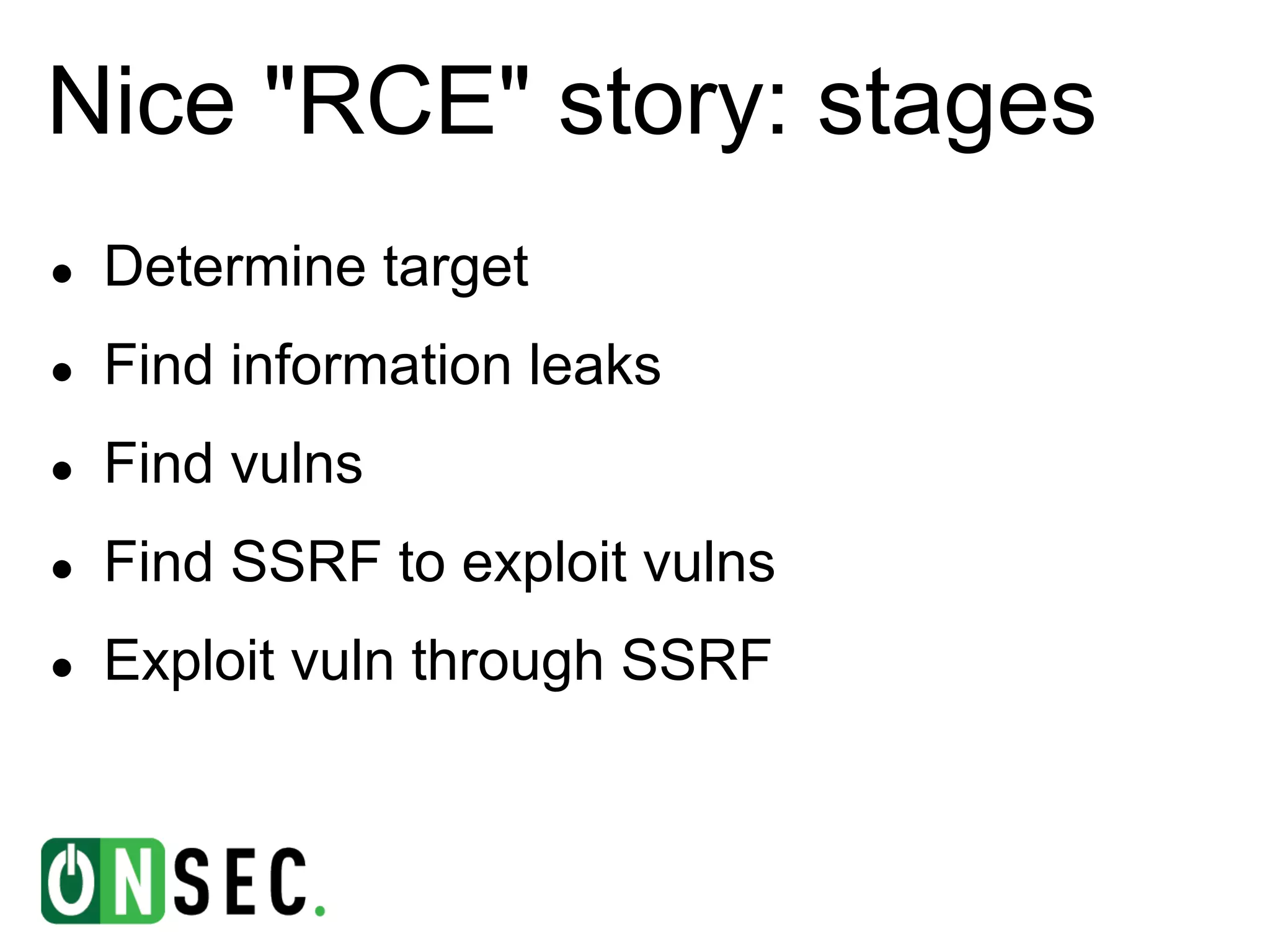
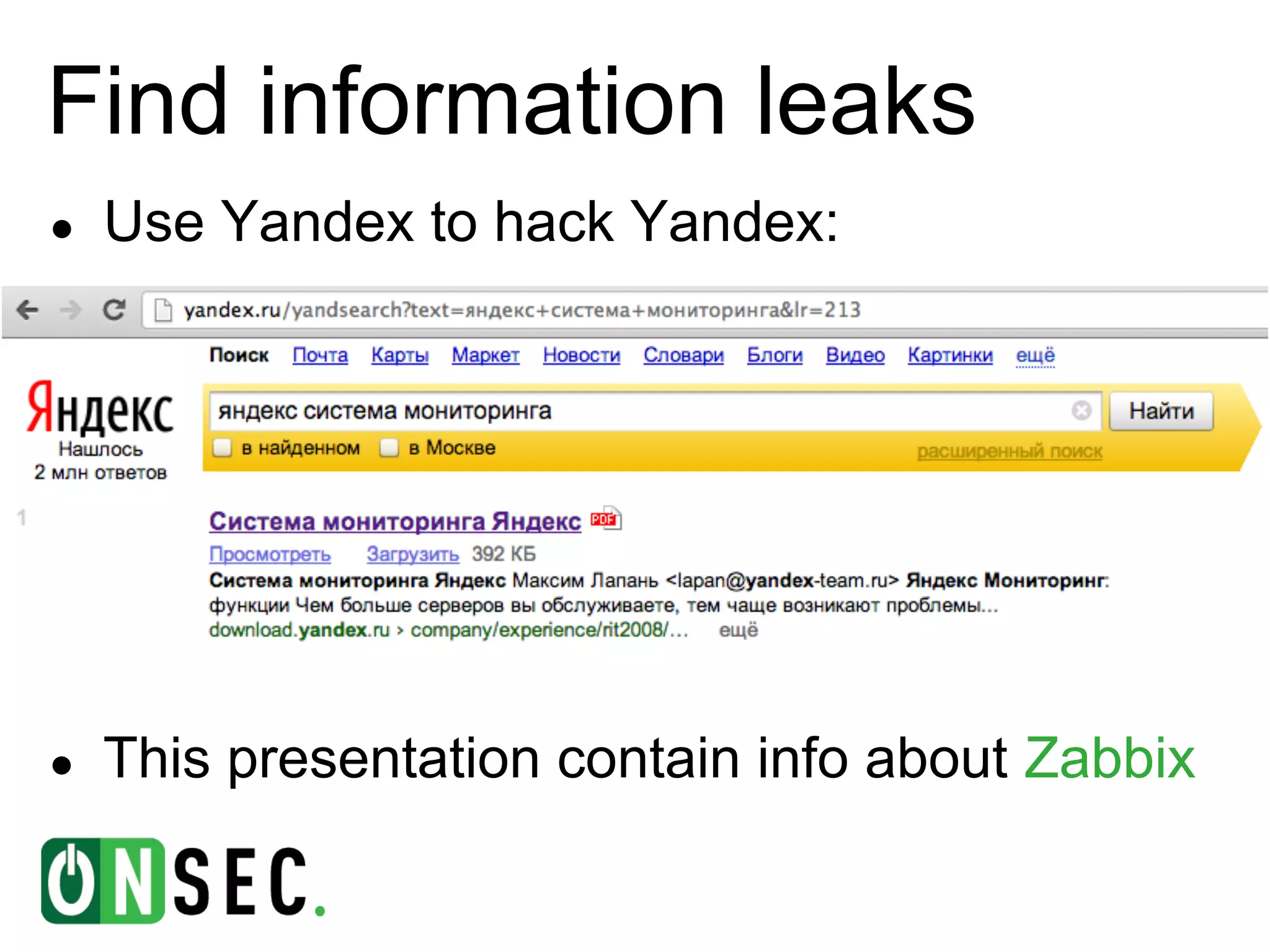
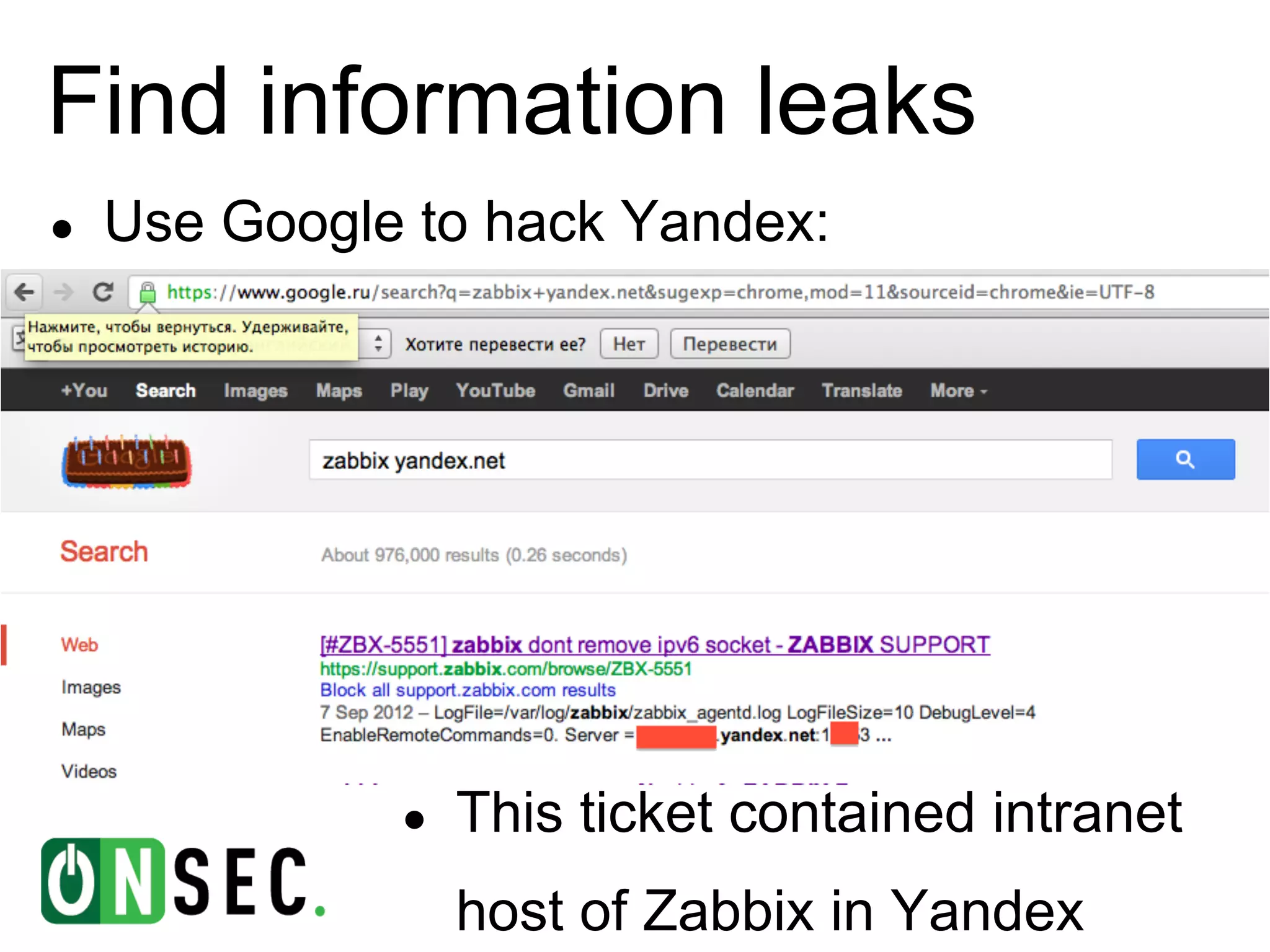
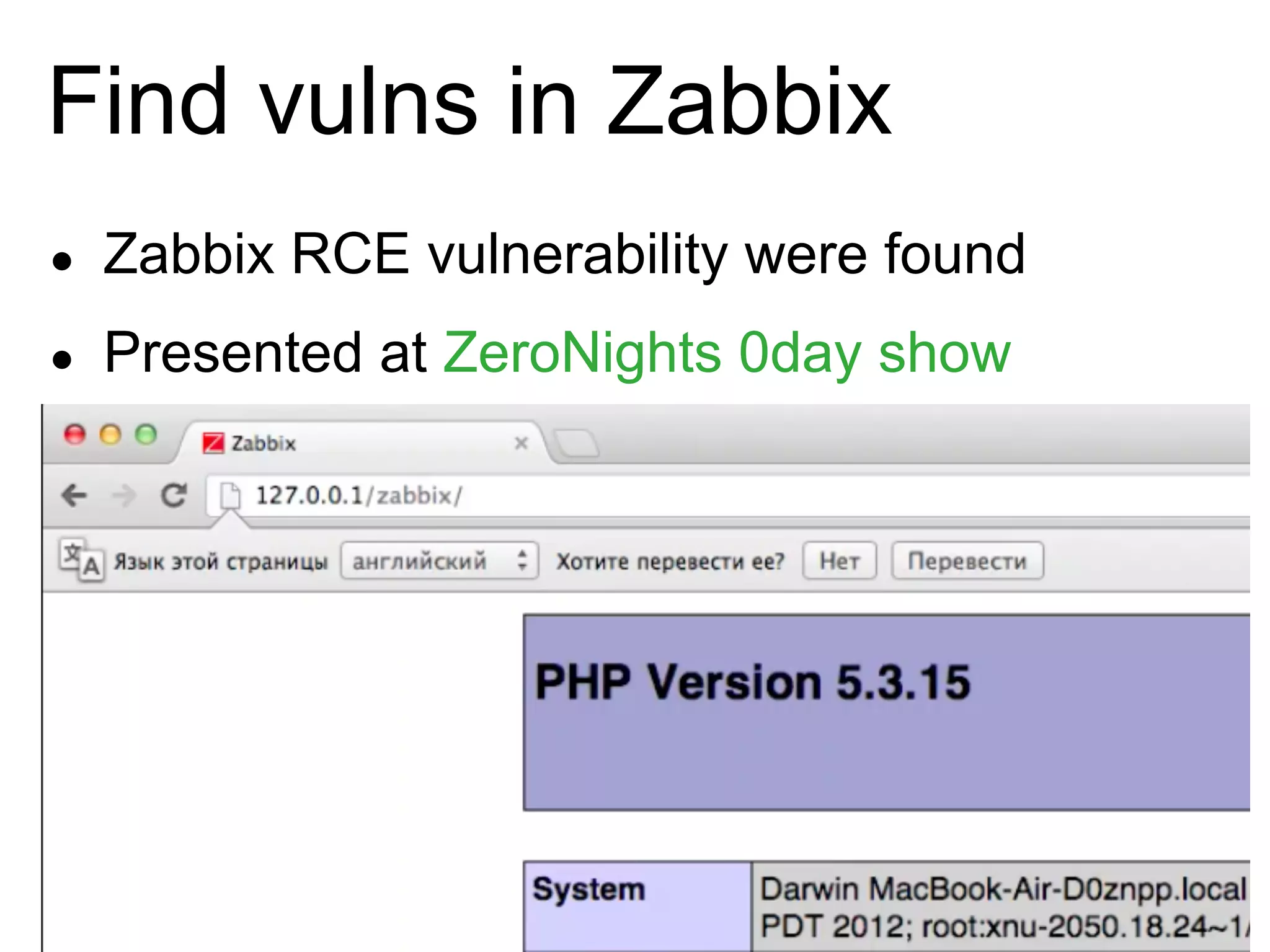
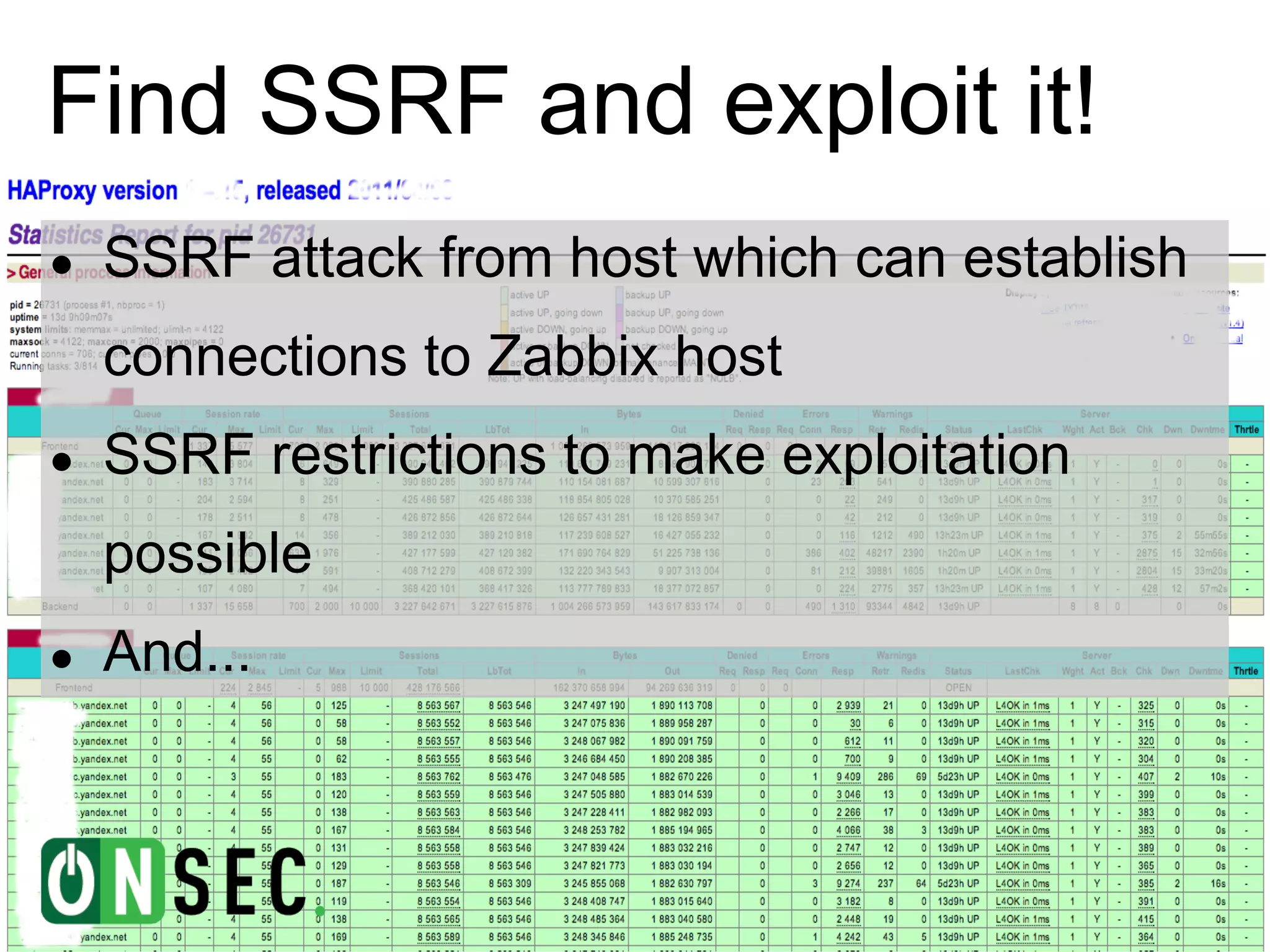
The document summarizes the history of Yandex's bug bounty program and ONsec Lab's experience finding vulnerabilities in Yandex systems between 2011-2013. It describes several vulnerabilities ONsec Lab reported to Yandex, including an XXE issue, an authentication bypass, and a CSRF/XSS collection vulnerability. It provides details on a current "Memcached injection through SSRF" bug and an attempted but failed remote code execution exploit of Yandex's internal Zabbix monitoring system via an SSRF vulnerability.










![???
@ONsec_Lab [http://lab.ONsec.ru]
@d0znpp
d0znpp@onsec.ru](https://image.slidesharecdn.com/yandexrewards-onsecexperience-130223165939-phpapp02/75/Yandex-rewards-ONsec-experience-18-2048.jpg)