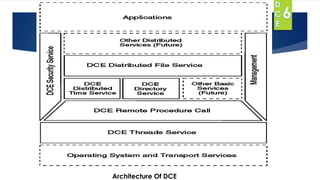
DCE is an architecture defined by OSF to provide a distributed computing platform. It includes services like RPC, directory service, security, time, and file service. DCE defines a framework for client-server communication and developing distributed applications across networked computers. It aims to address challenges of distributed computing like scalability, availability and security.