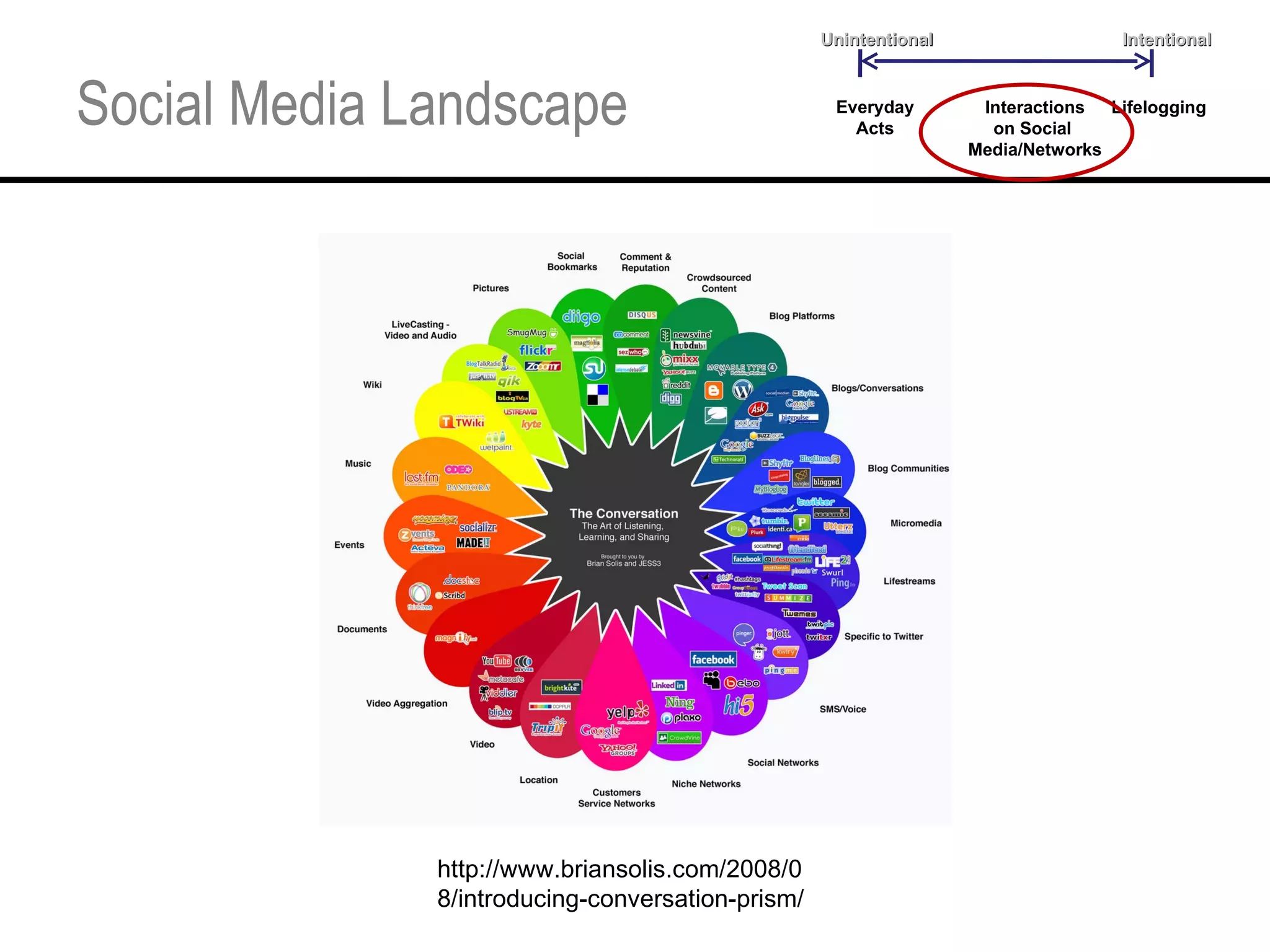
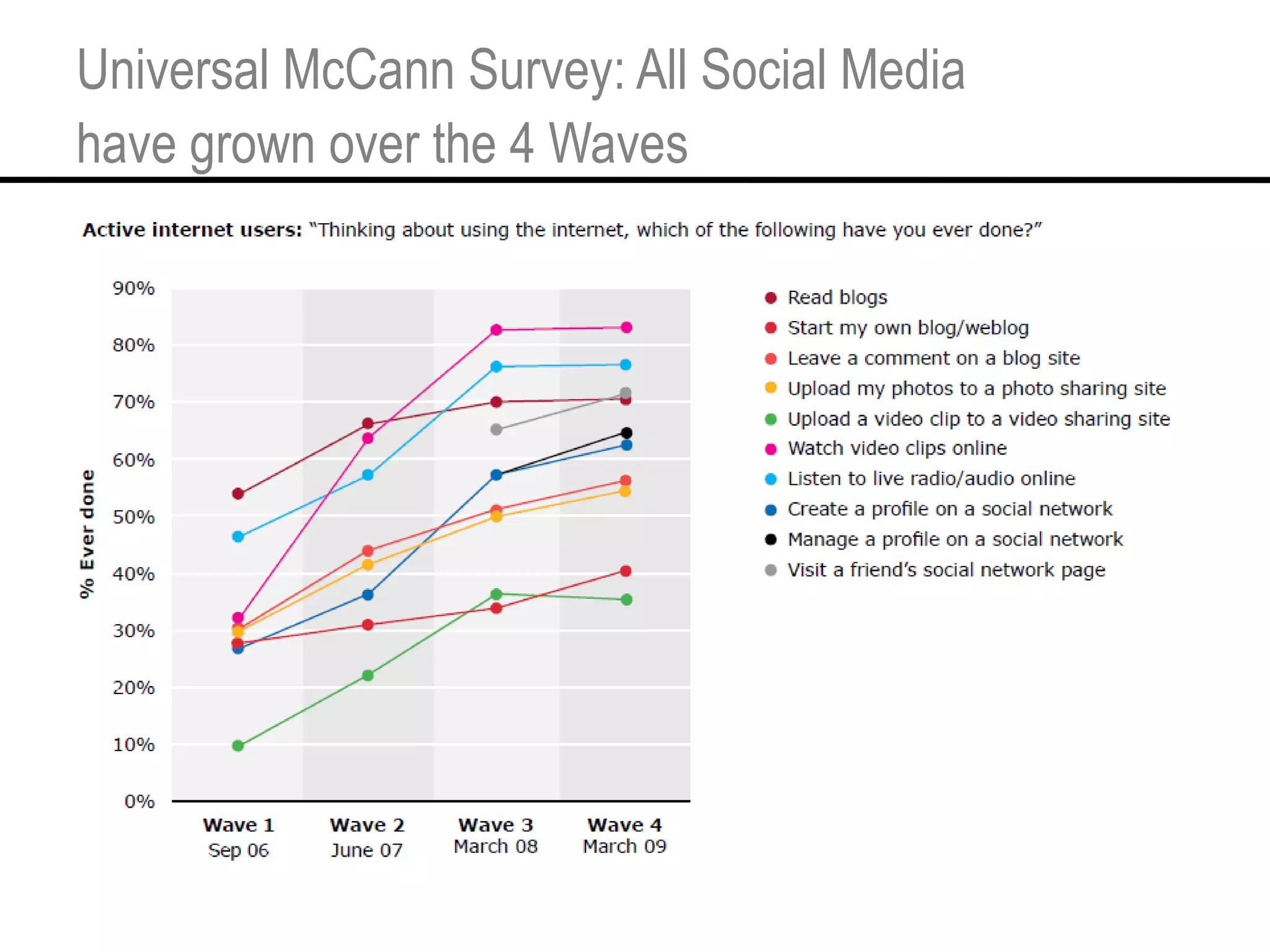
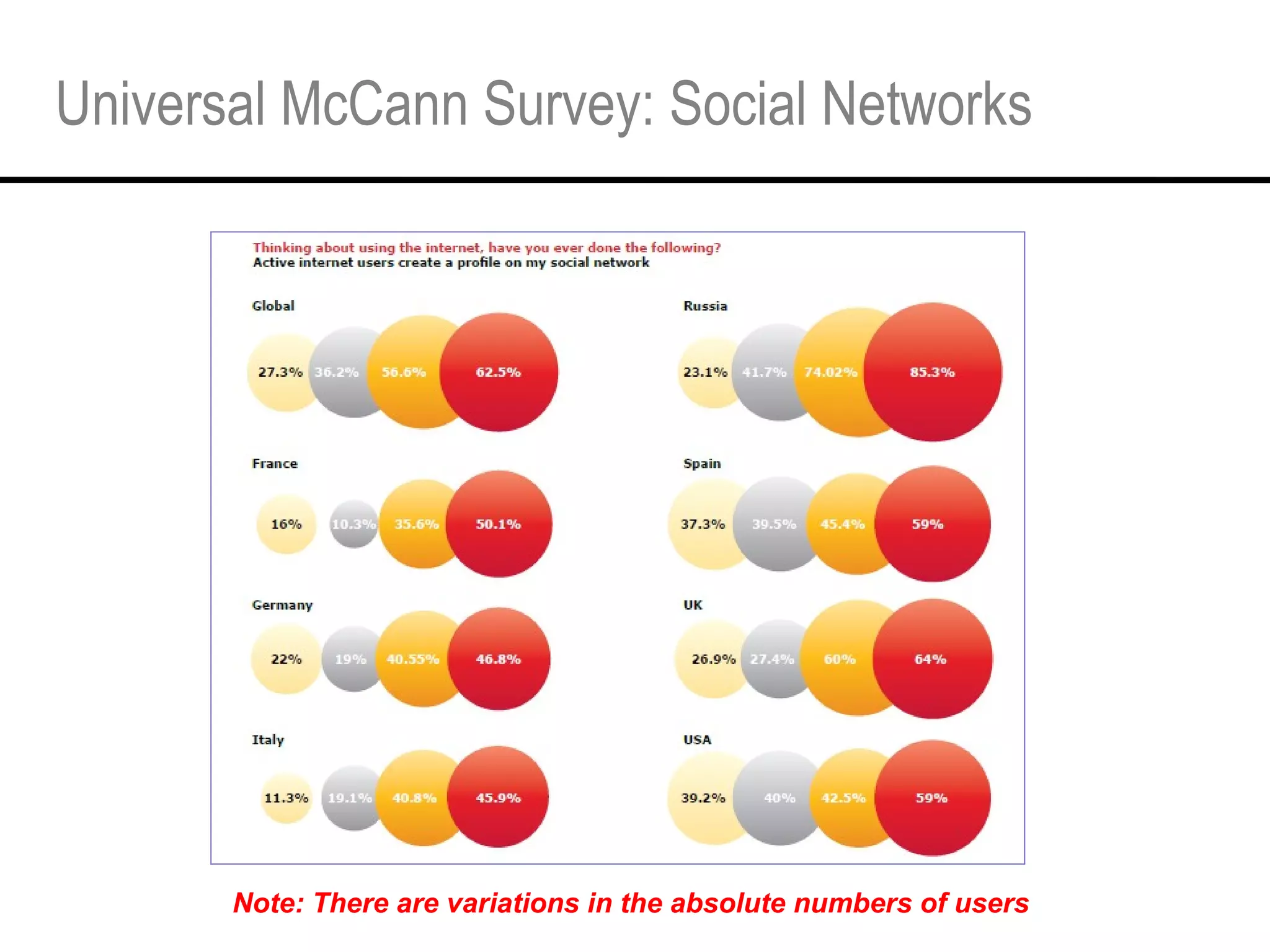
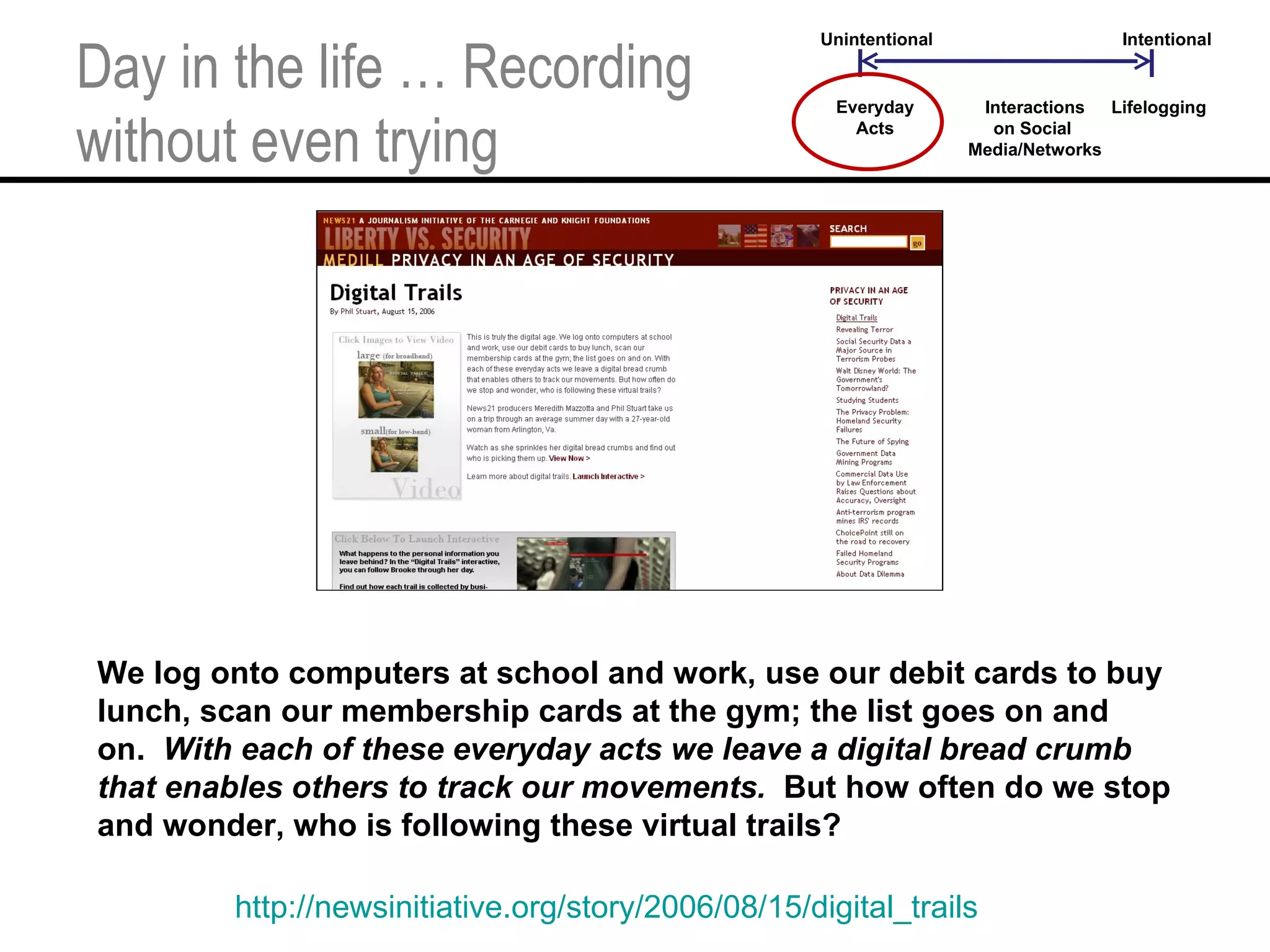
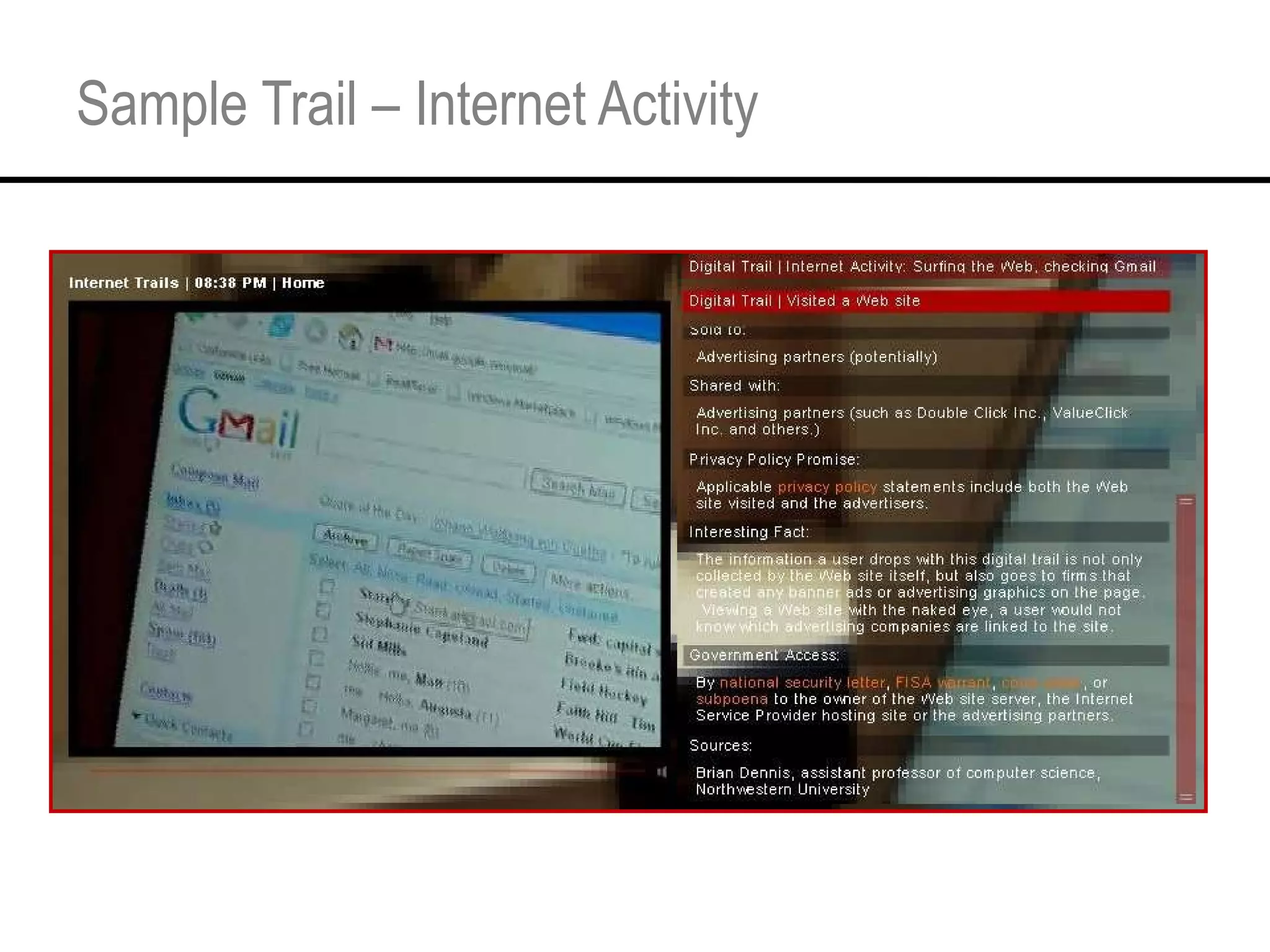
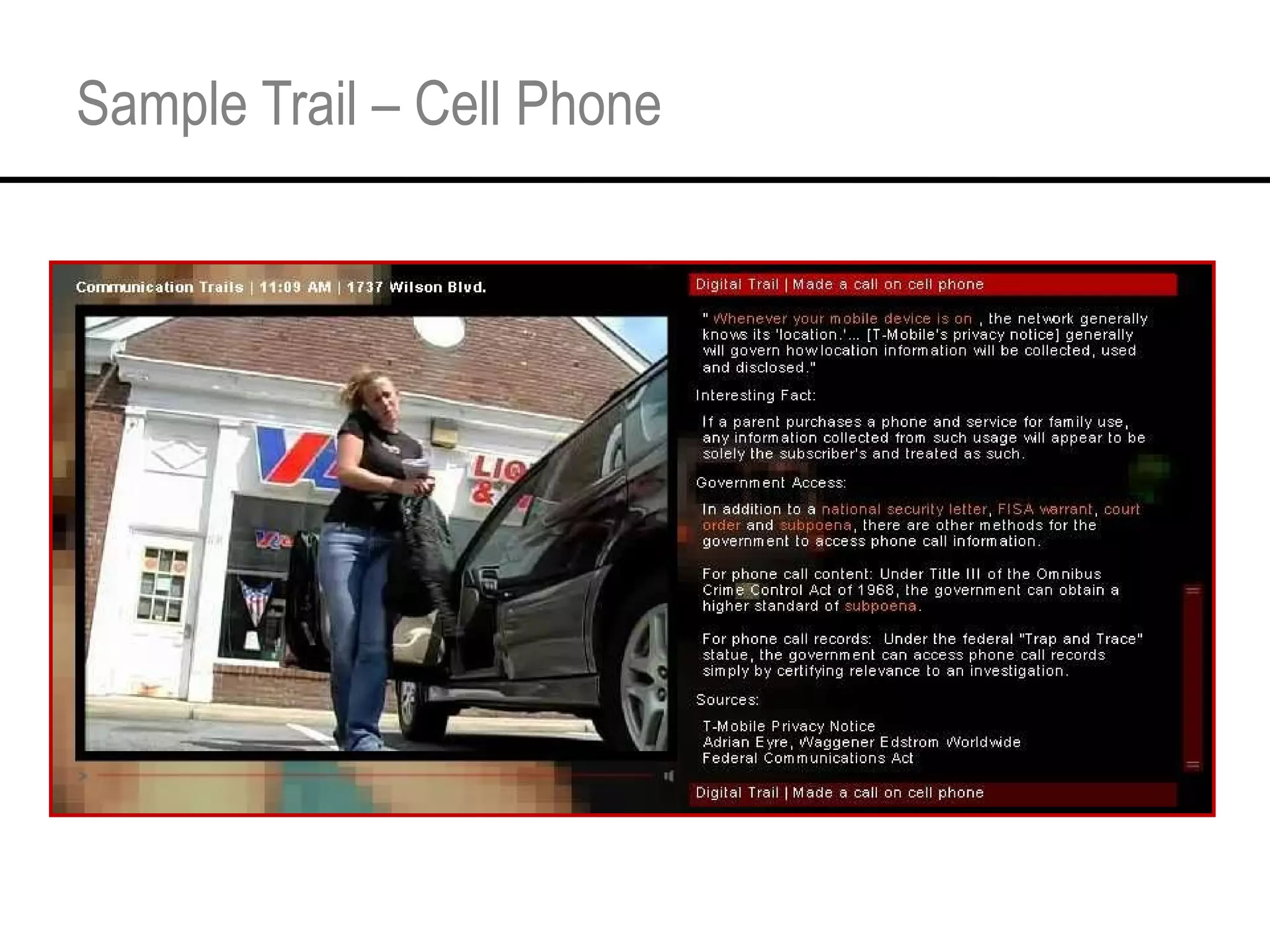
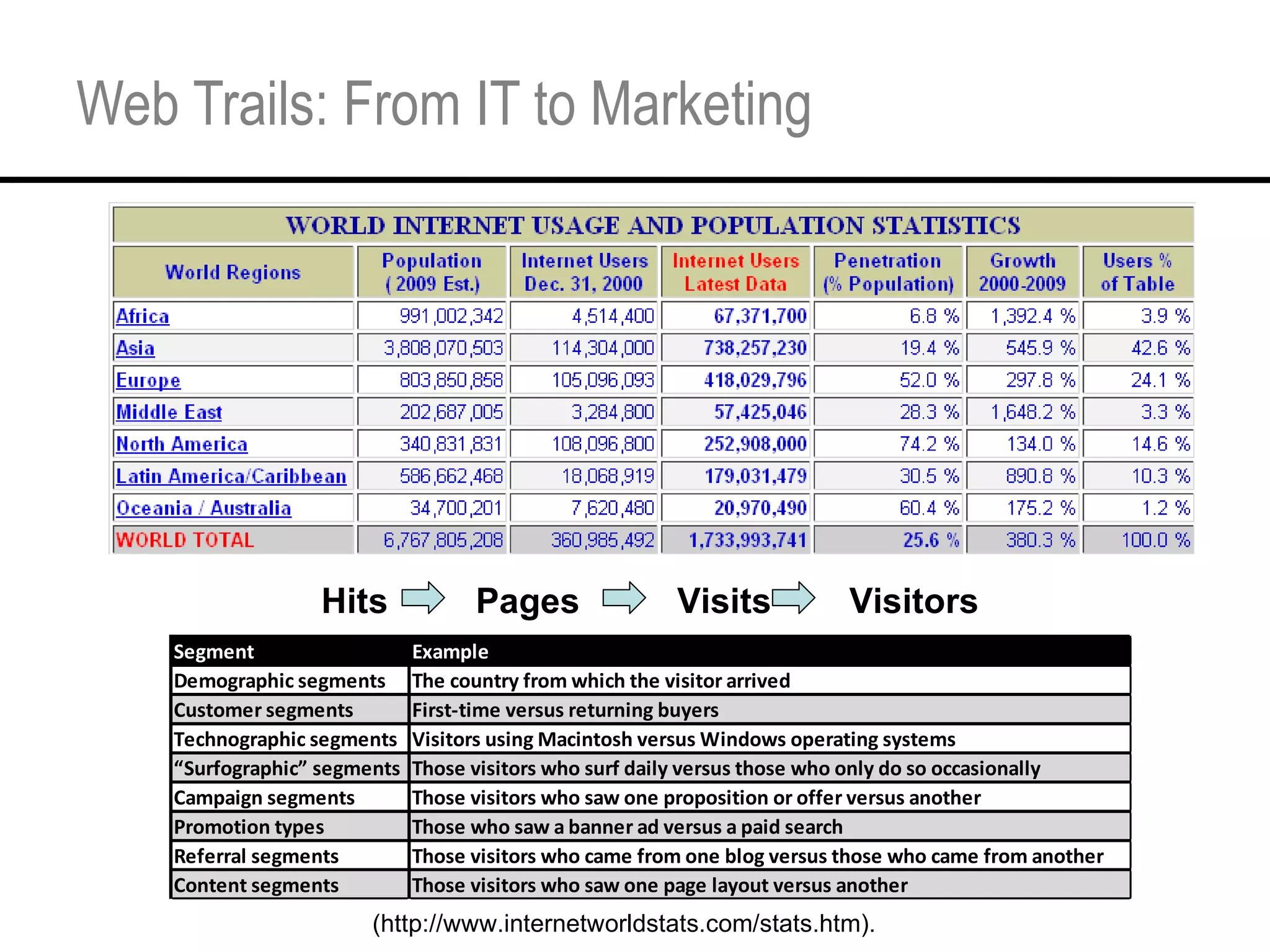
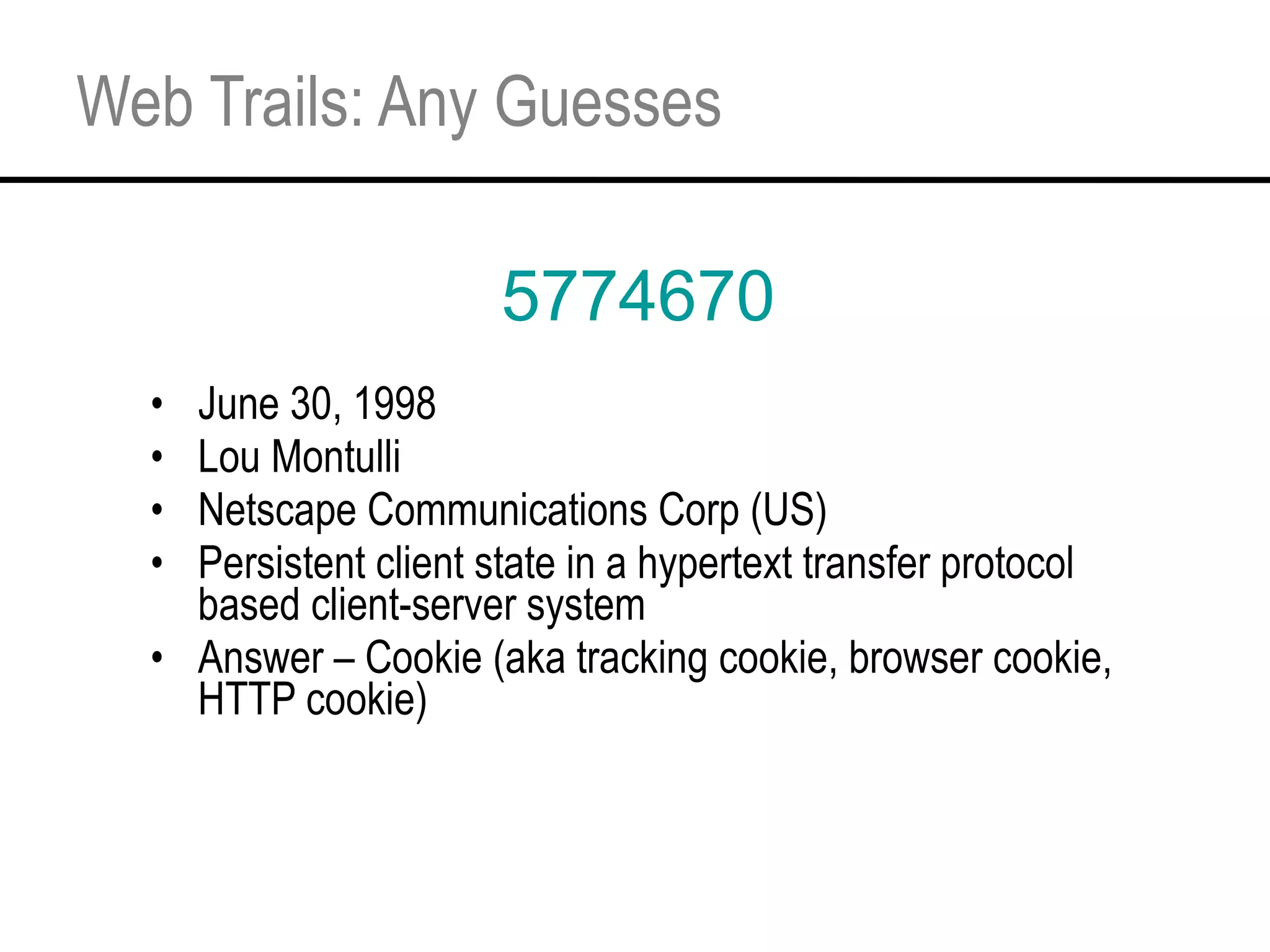
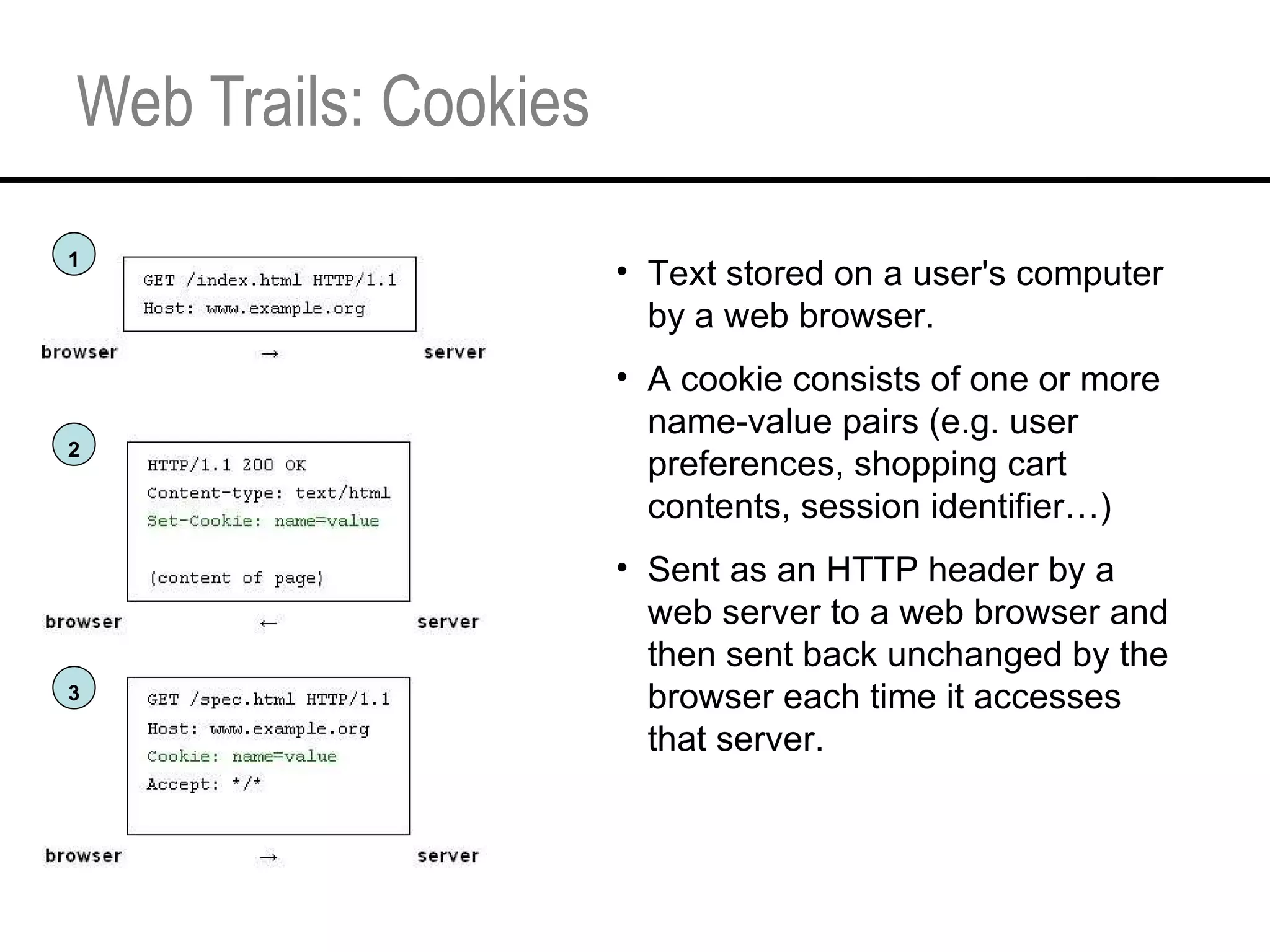
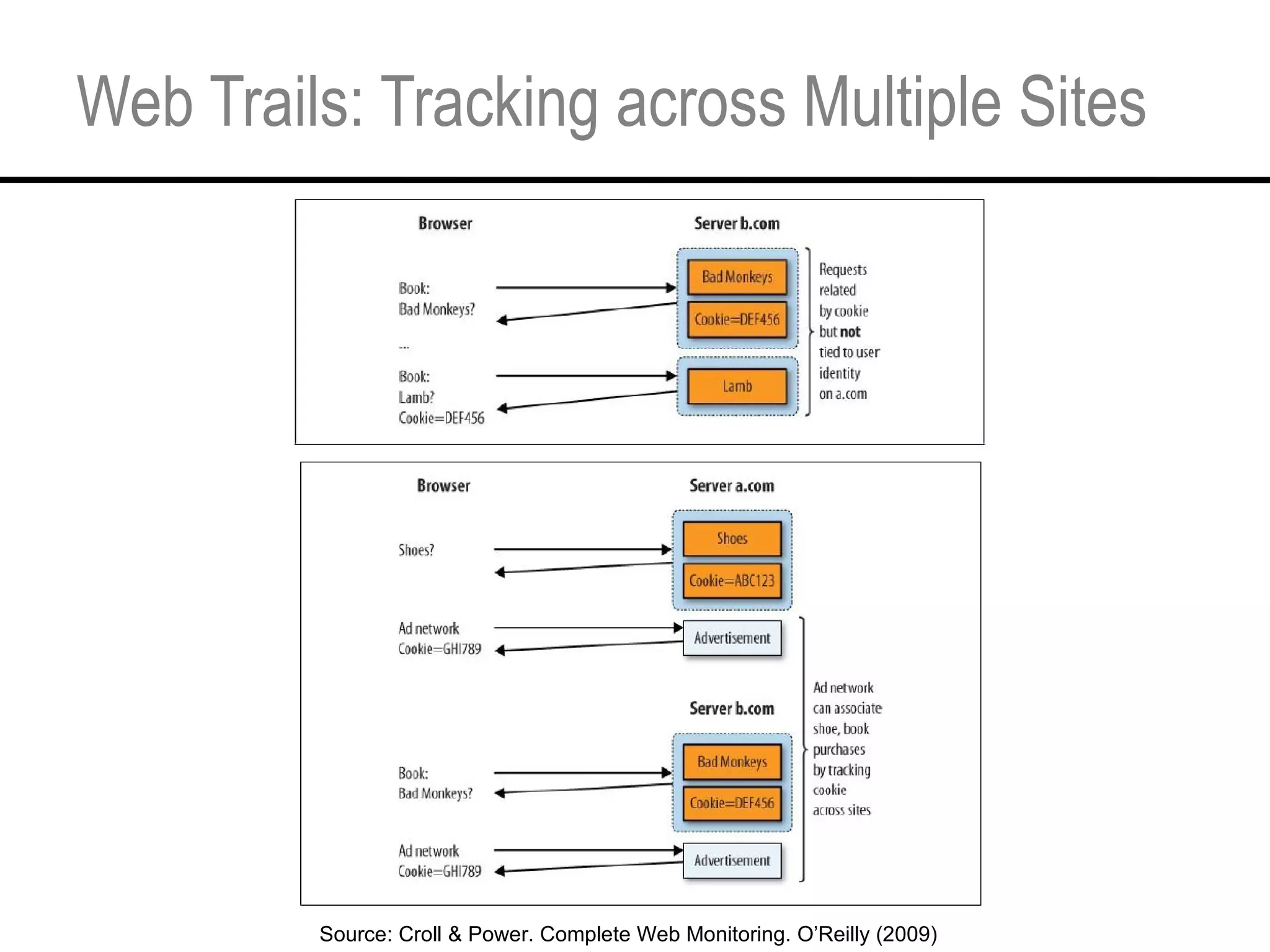
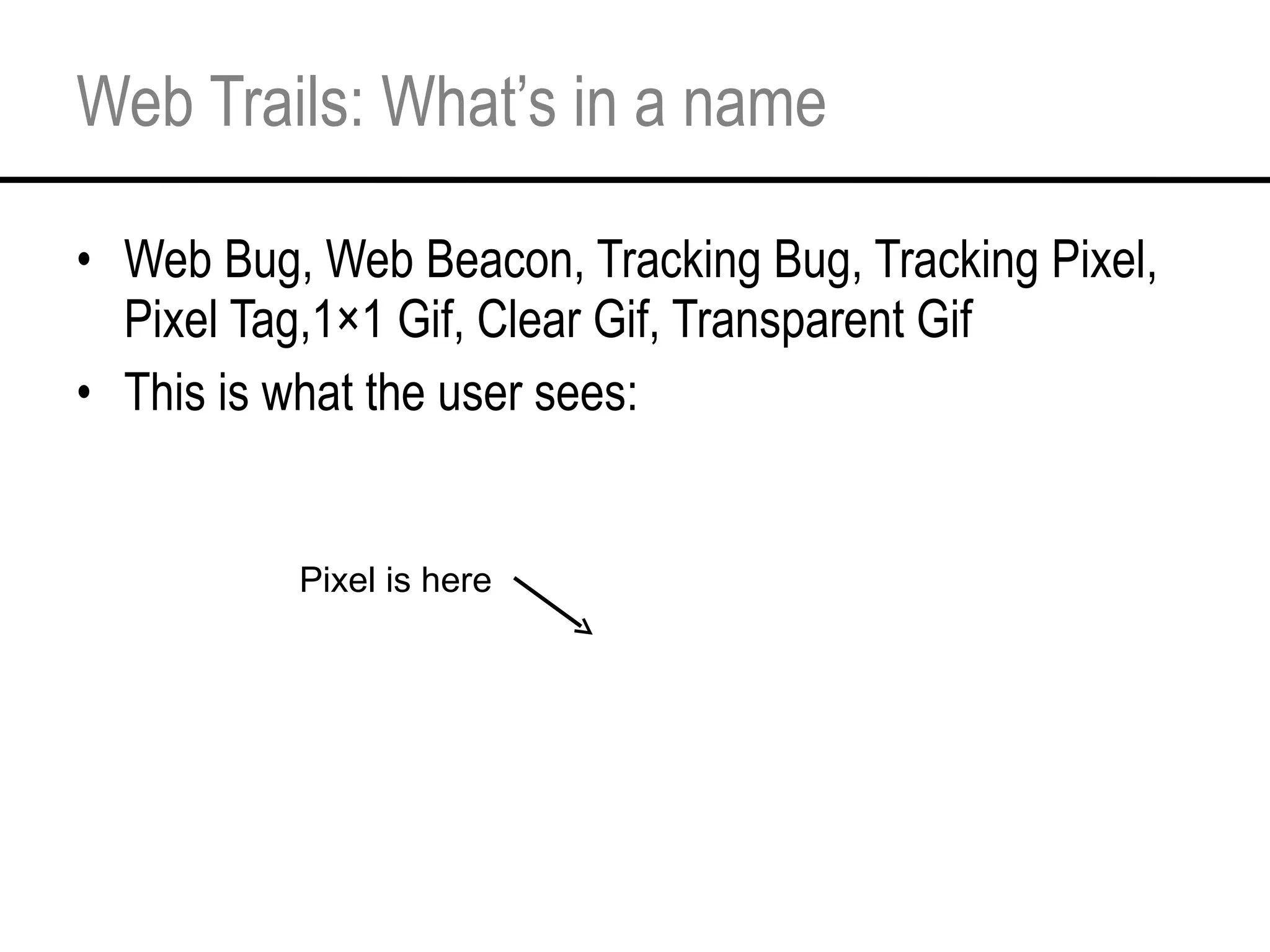
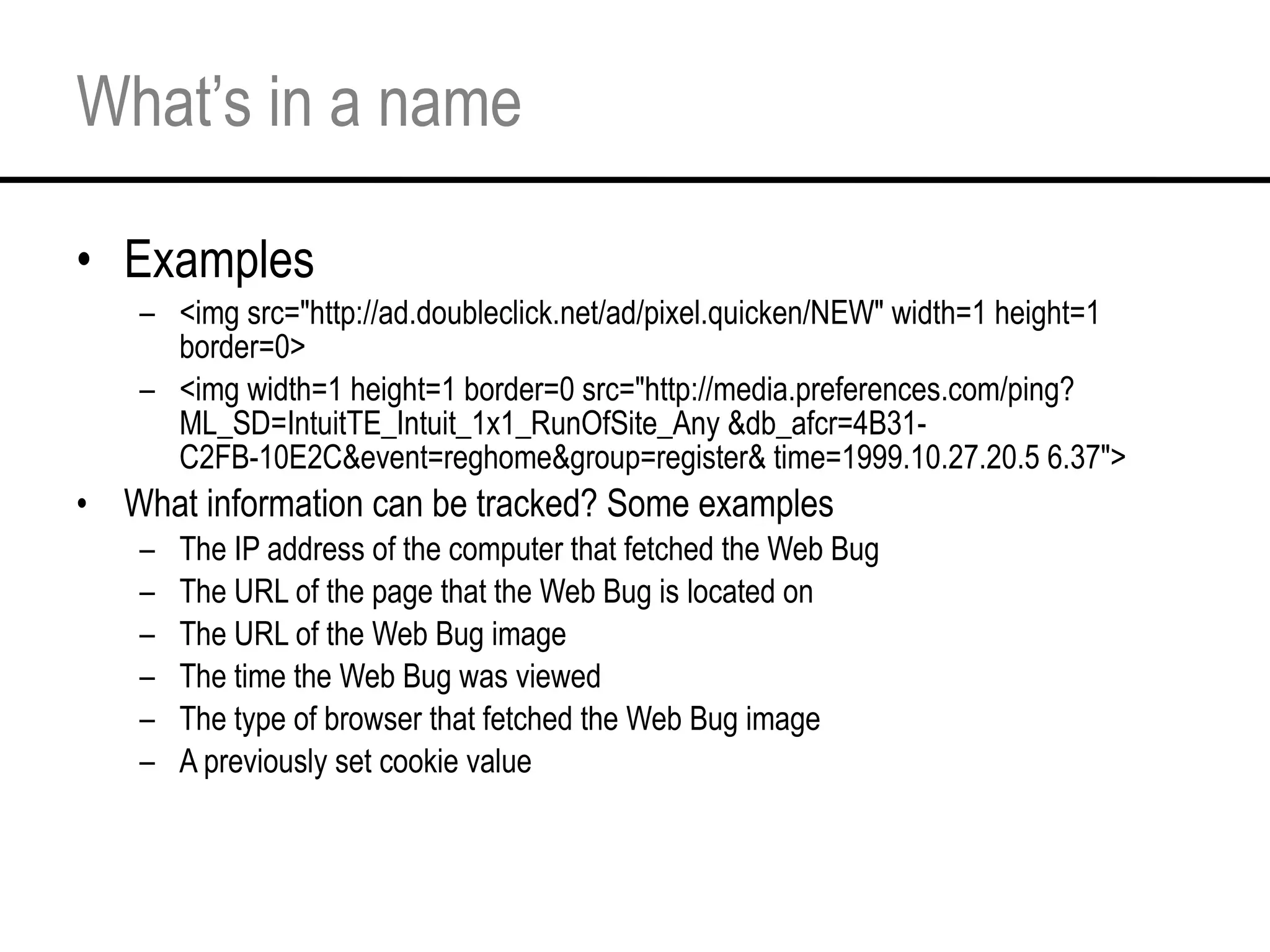
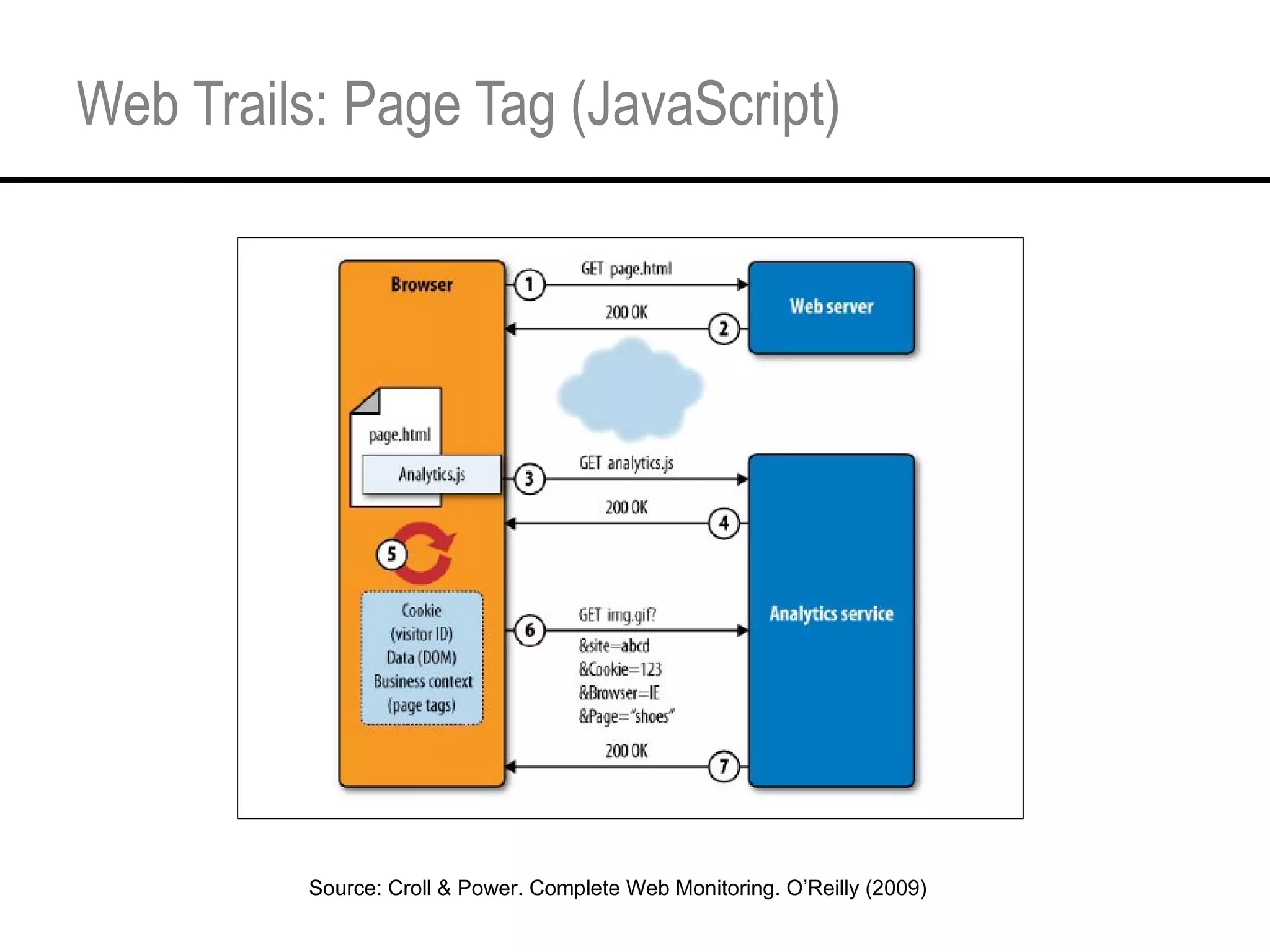
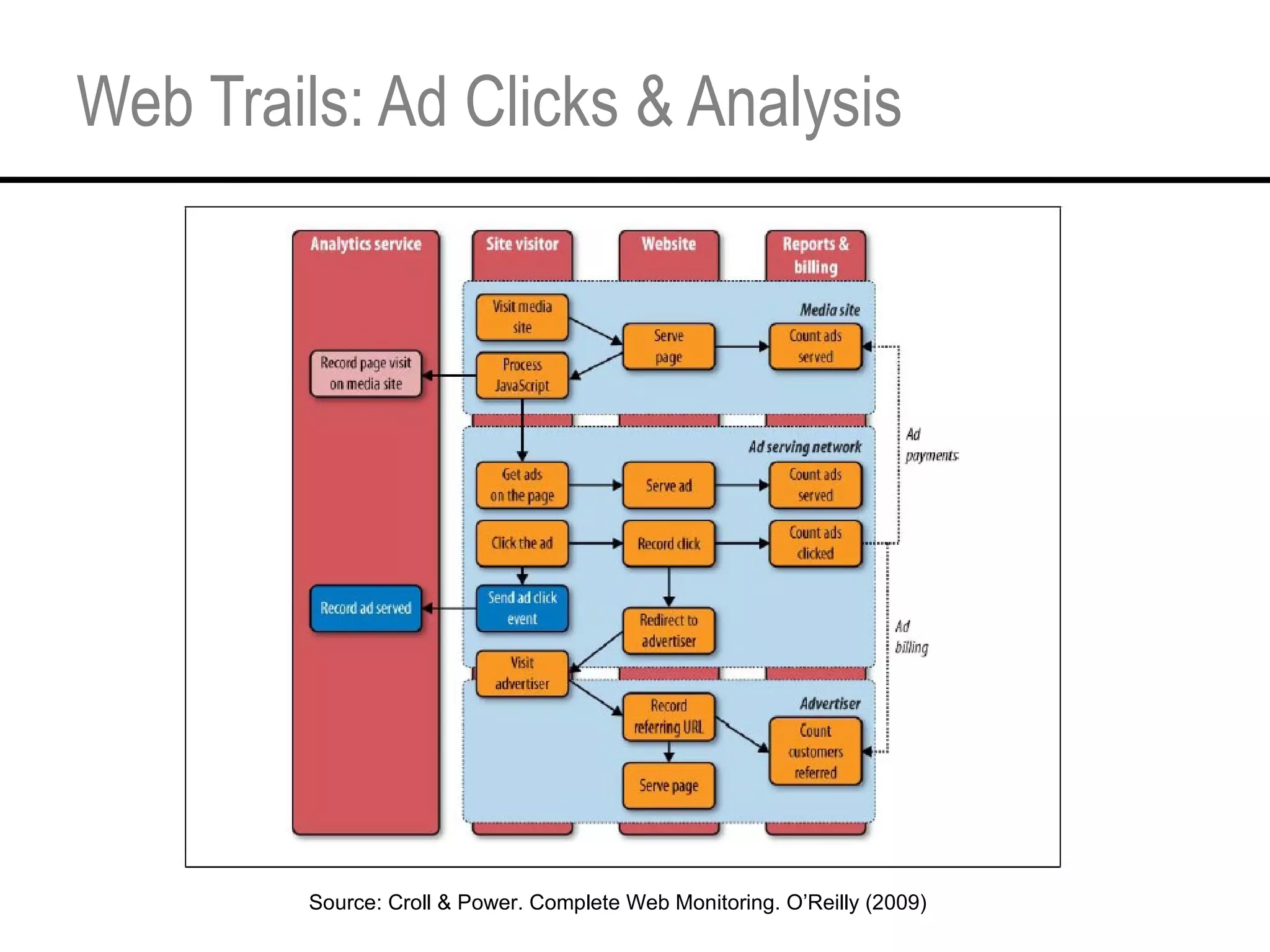
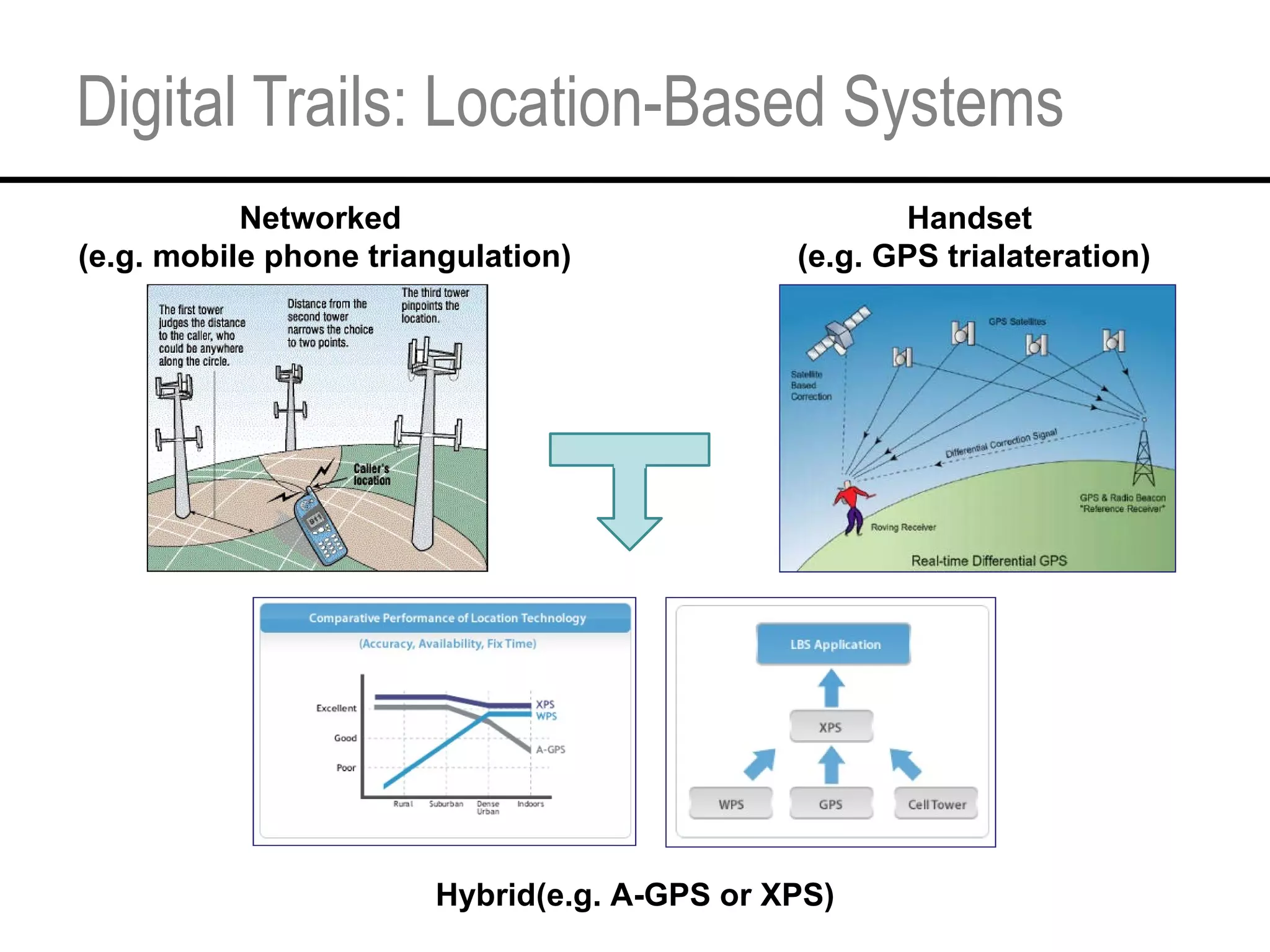
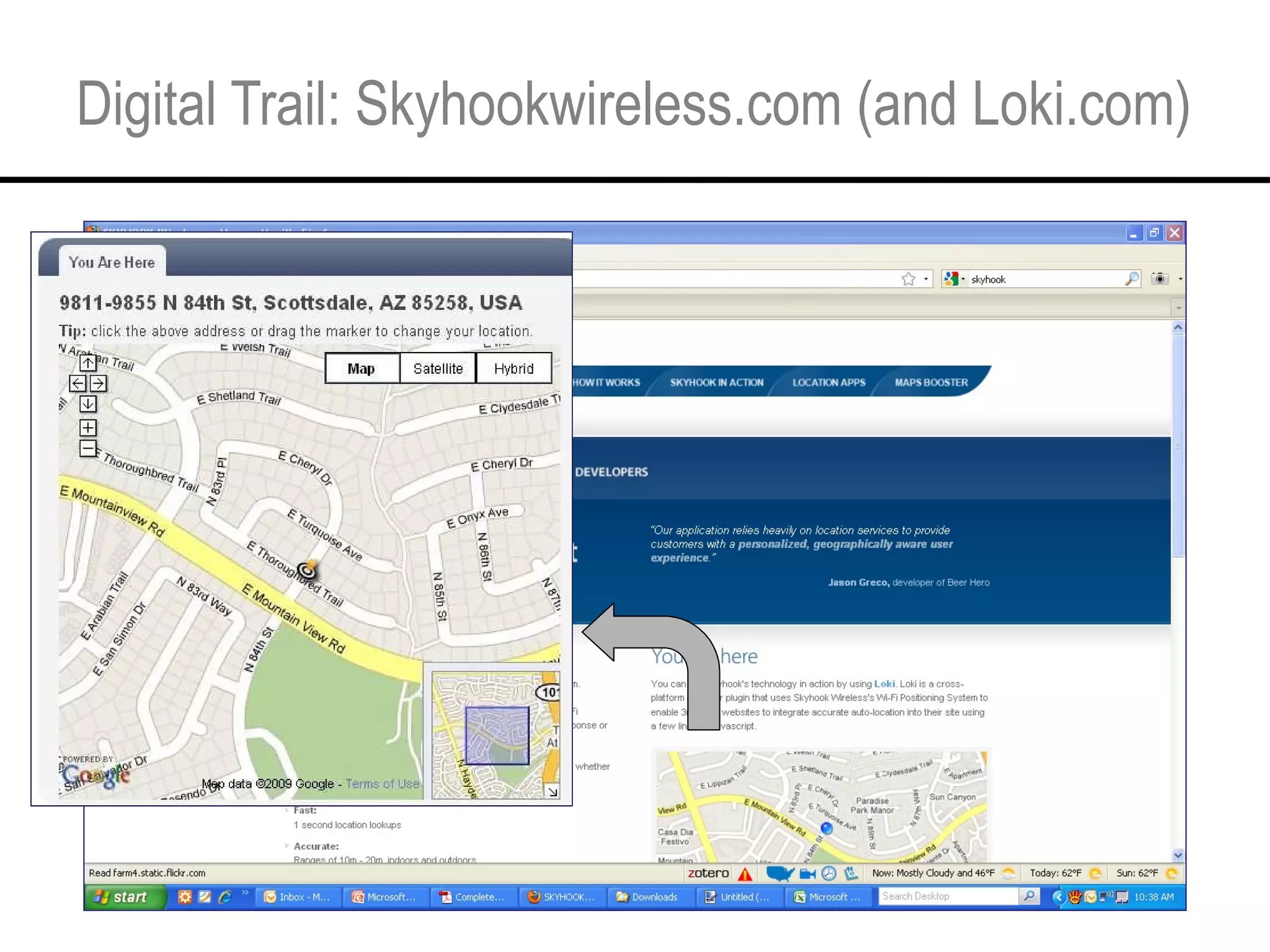
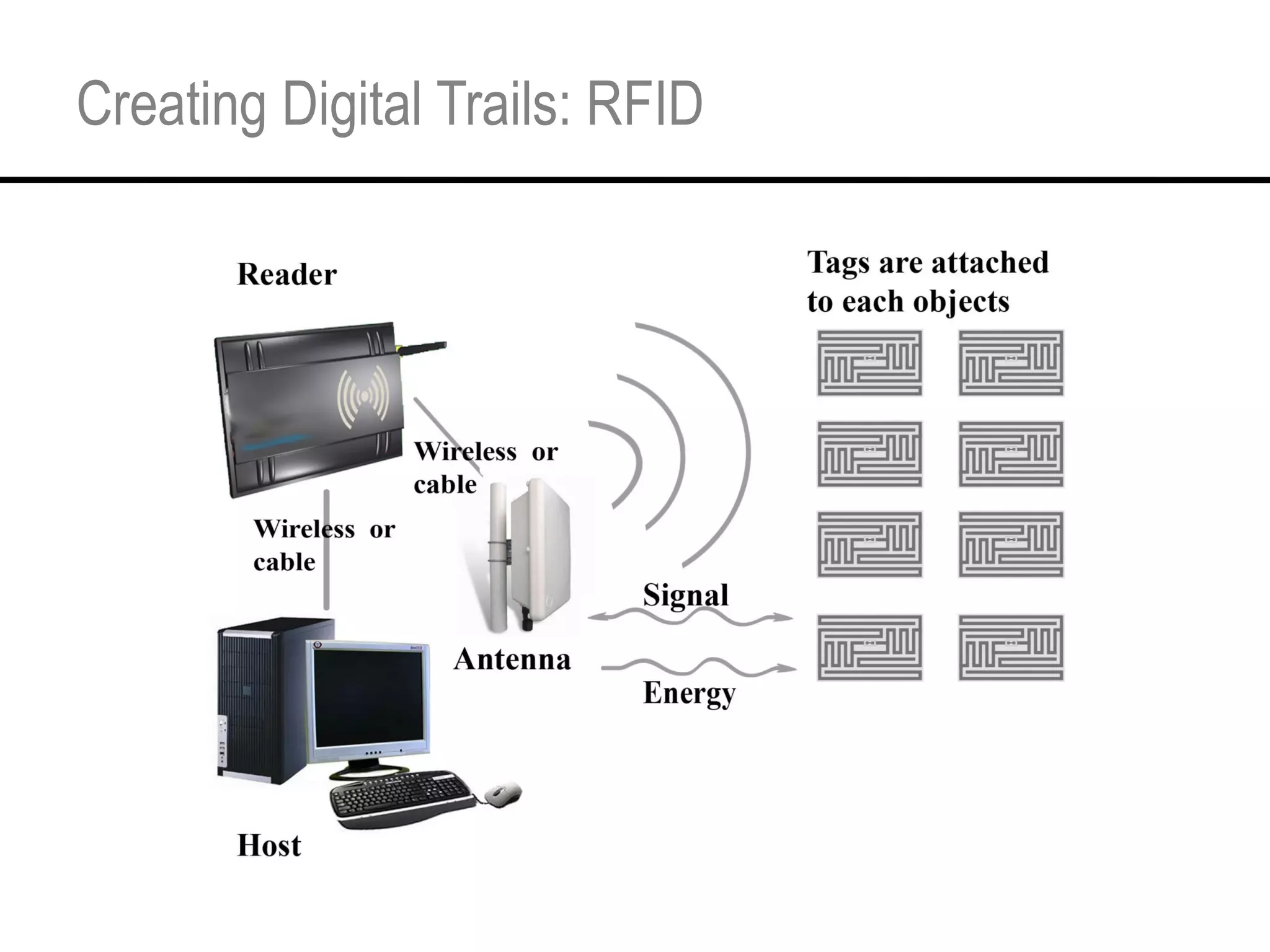
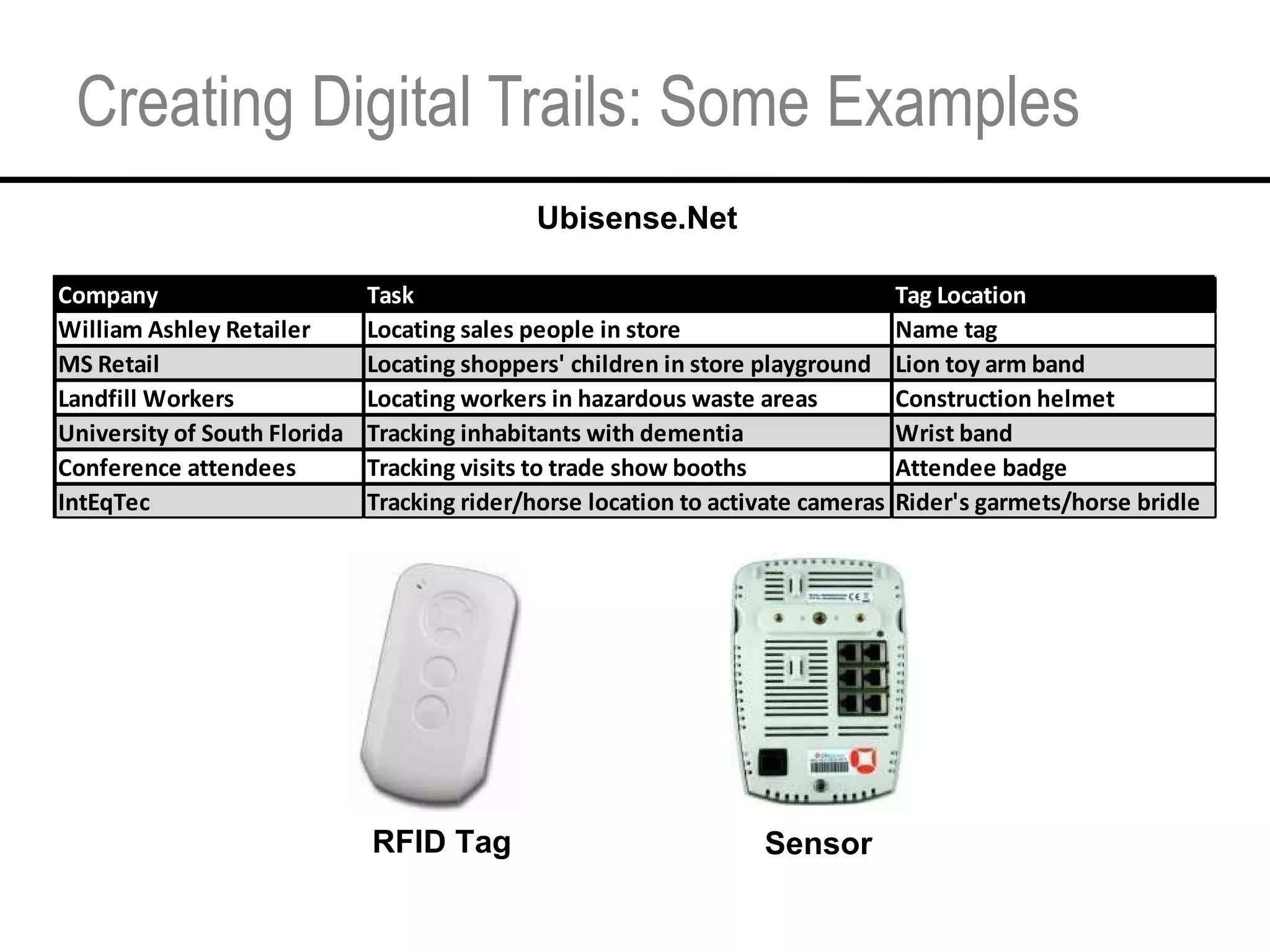
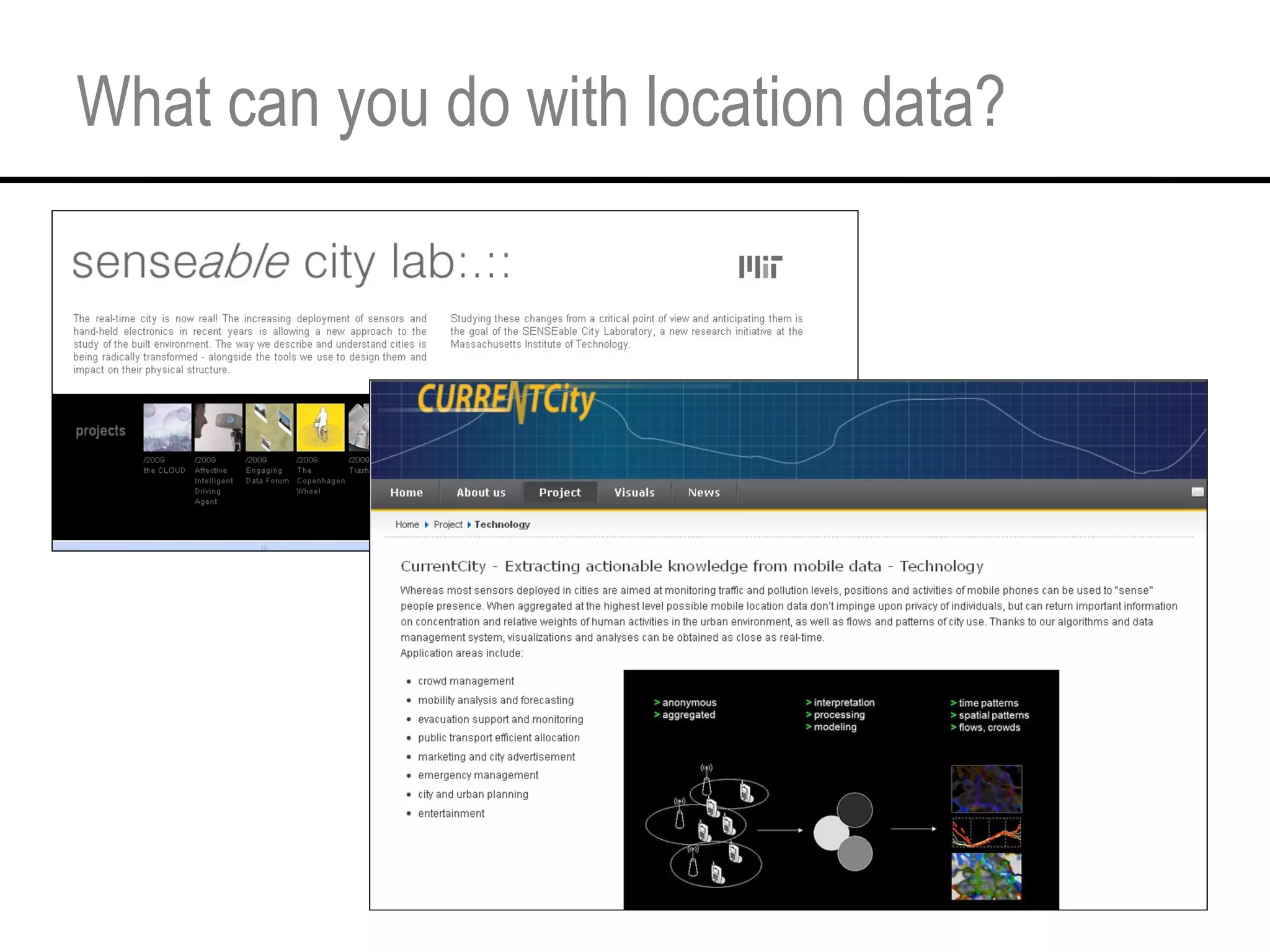
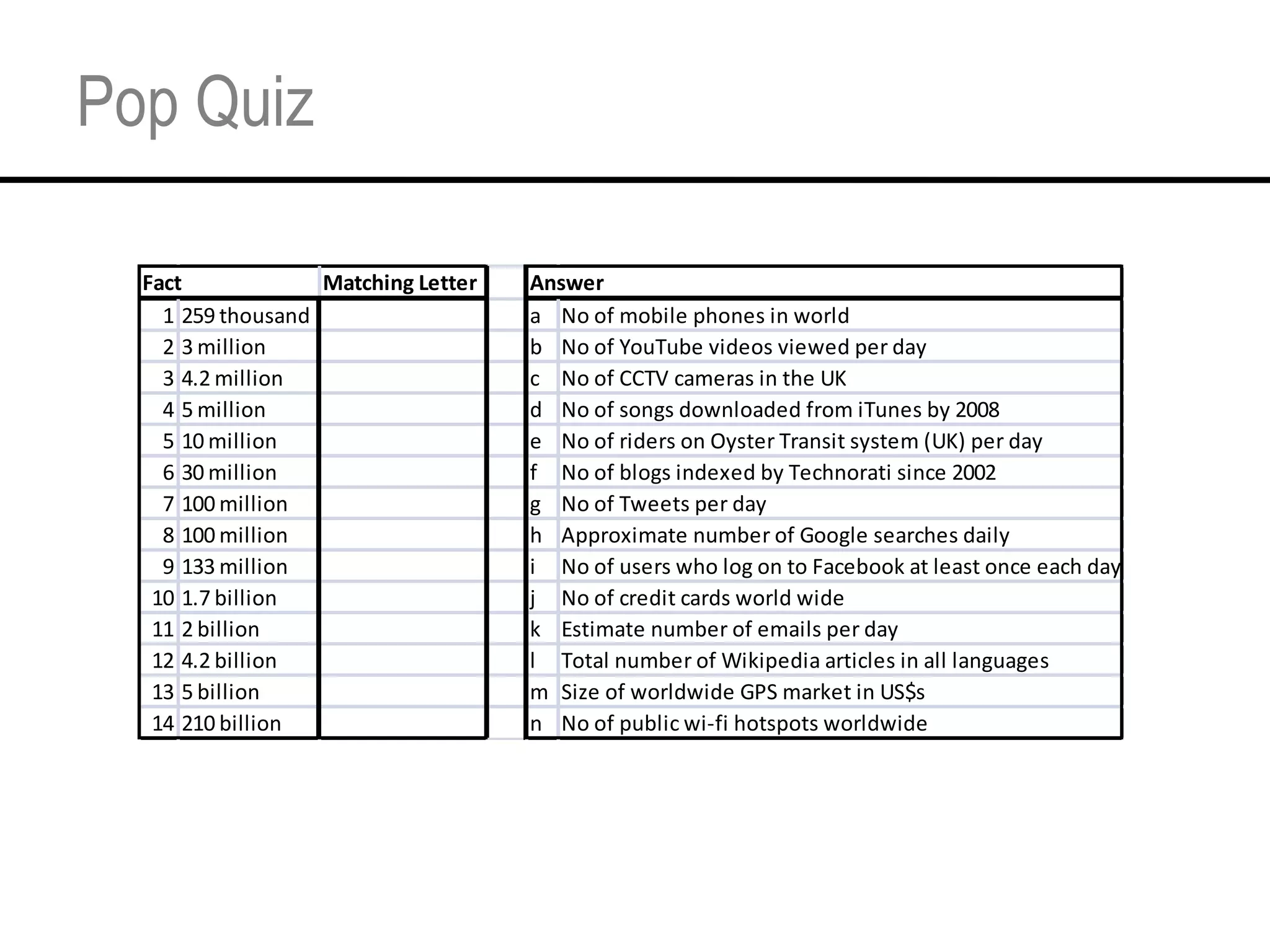
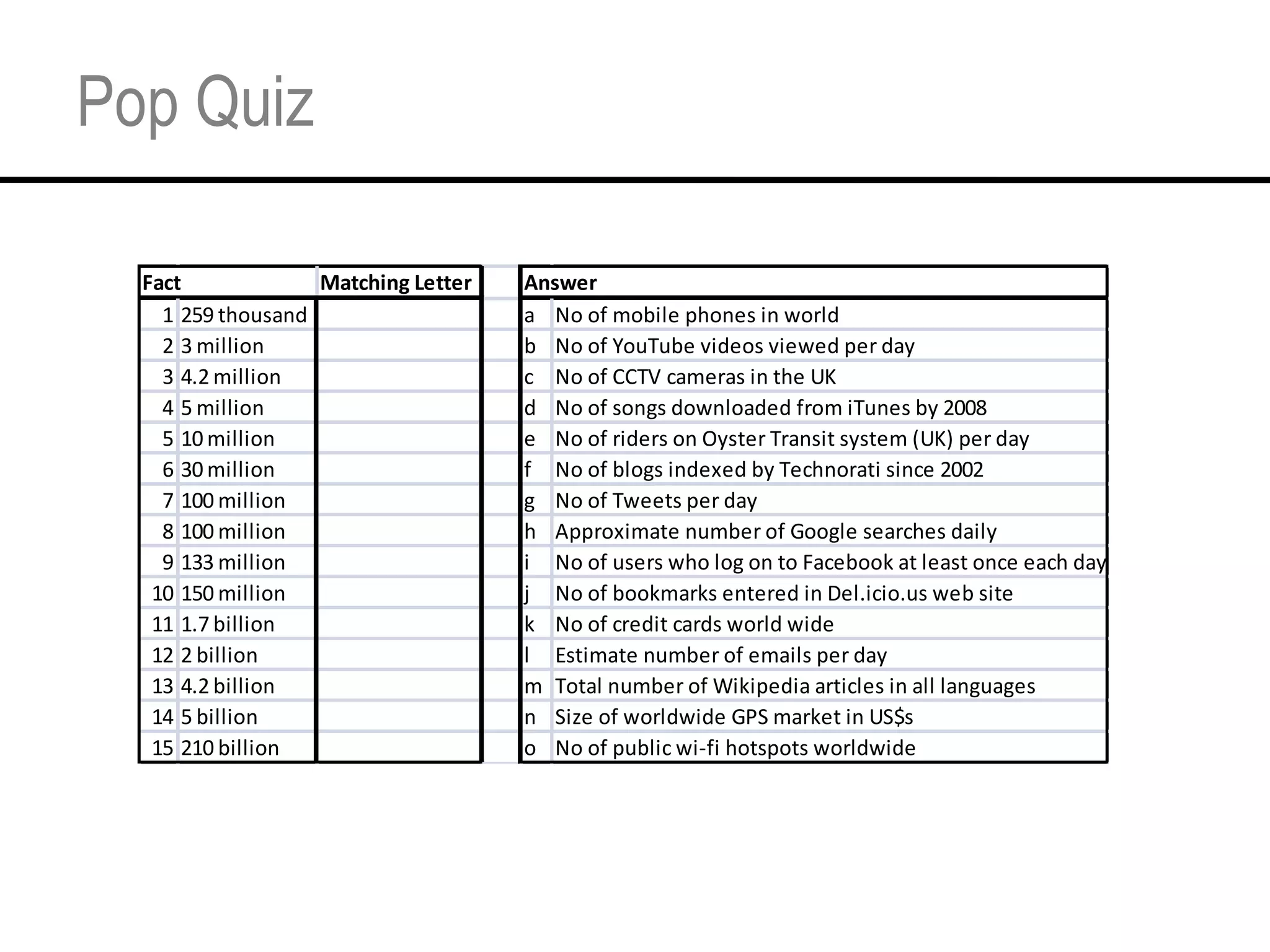
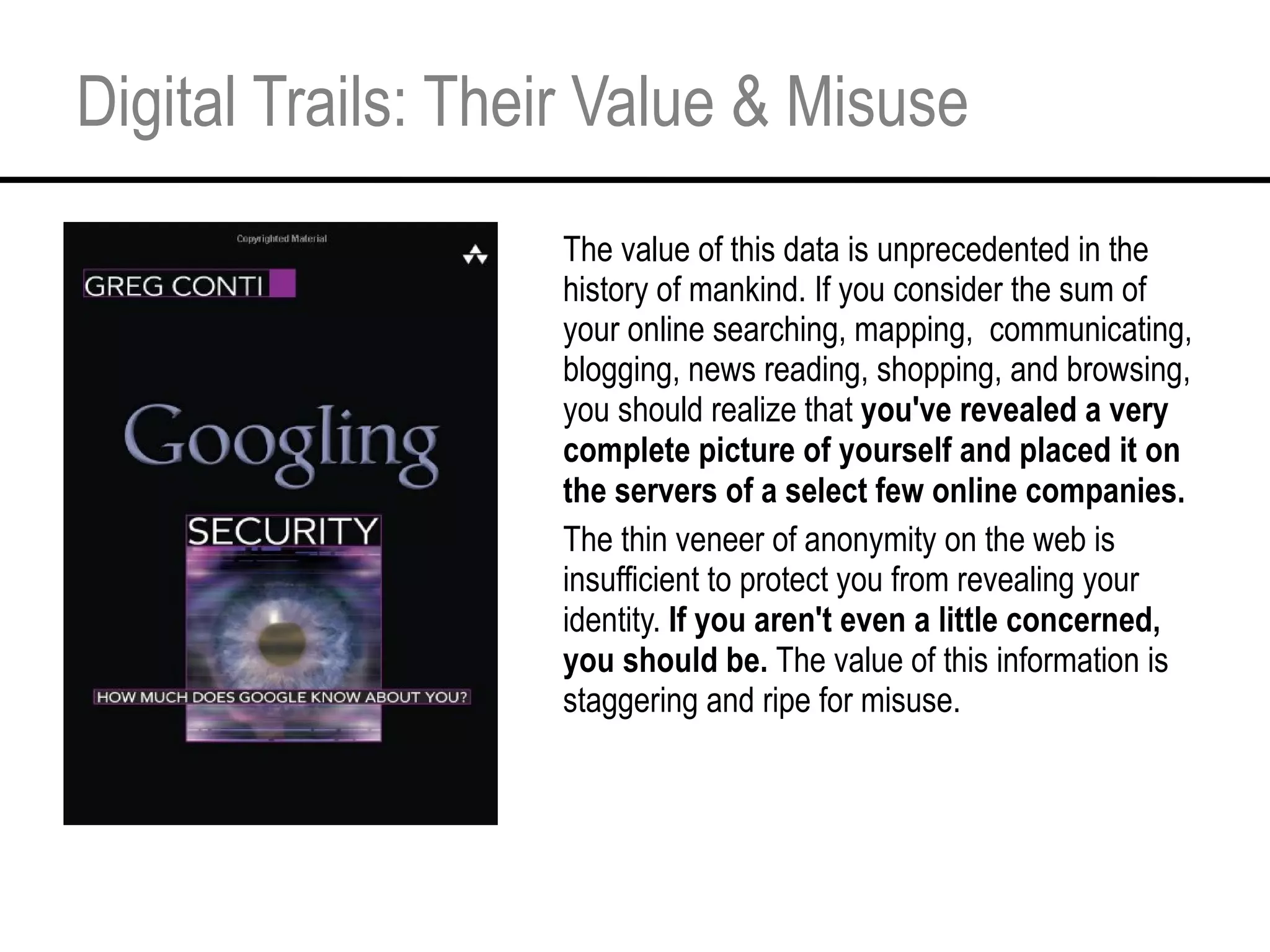
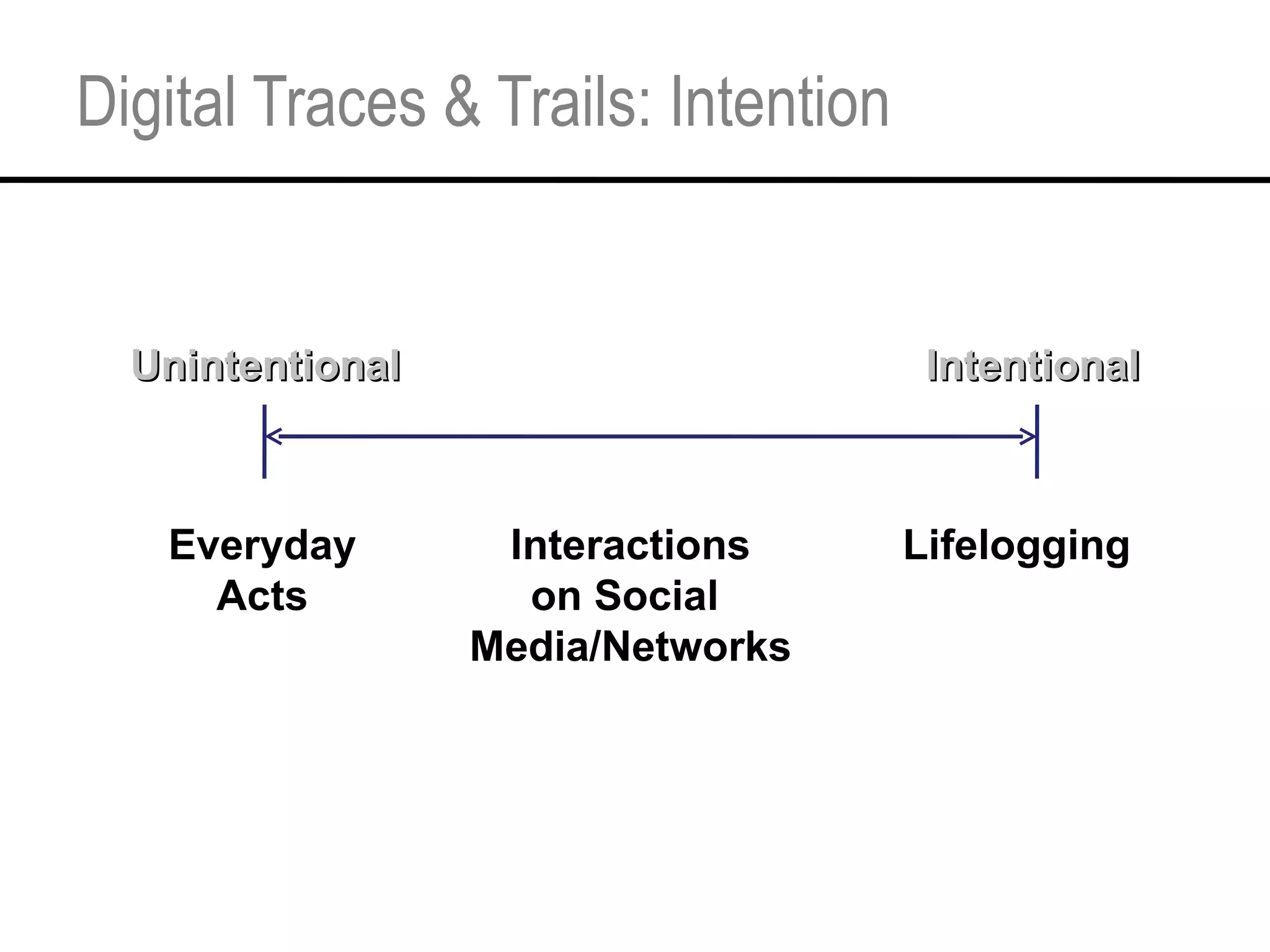
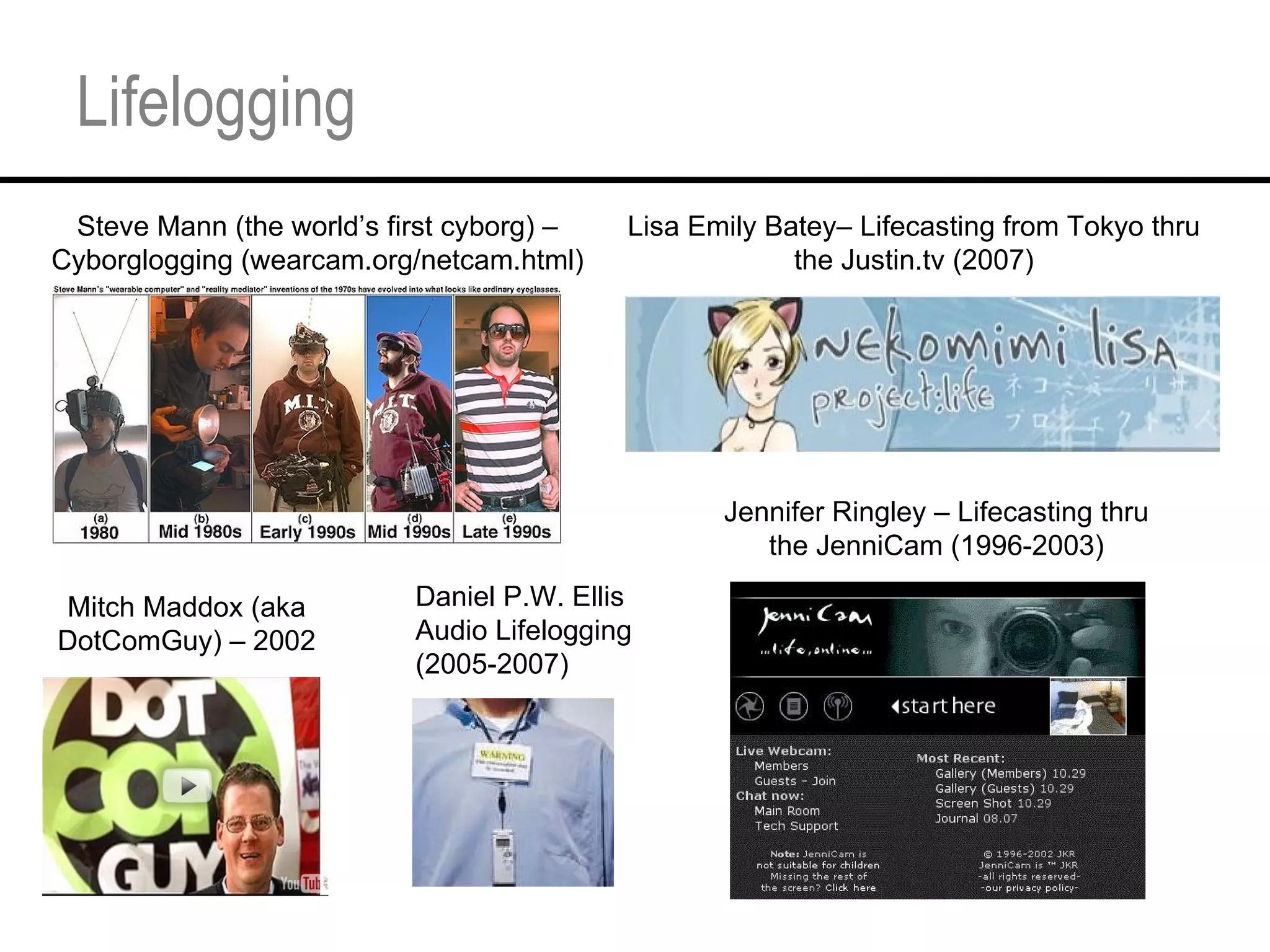
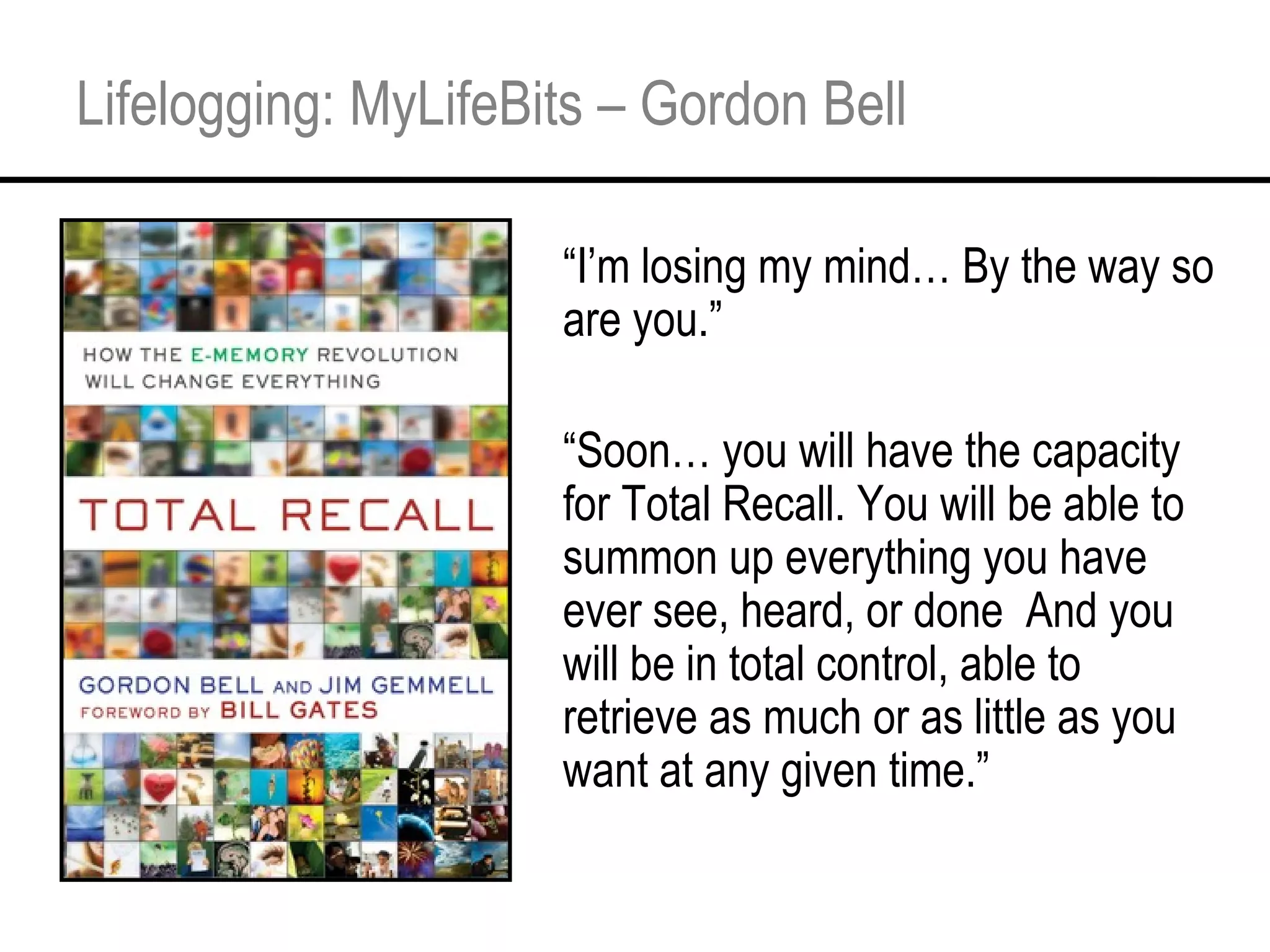
This document provides an overview and agenda for a tutorial on extracting intelligence from digital traces and trails left by web and mobile users. It discusses the proliferation of digital devices that create extensive data about people's online and mobile activities. Examples are given of different types of digital traces, including cookies, web bugs, location data, and social media interactions. Concerns about privacy are also mentioned as vast amounts of personal data are now collected and analyzed.









![Digital Traces: How much is a free smartphone worth? In the fall of 2008, 100 undergraduate students living in Random Hall at M.I.T. agreed for one year to swap their privacy for free smartphones in exchange for participating in a n MIT study aimed at understanding the impact of social interaction on social diffusion. When the participating students dialed other students, sent e-mails, or listened to songs the researchers knew…Every moment the students had their Windows Mobile smartphones with them, the researchers knew where they were and who was nearby. [ Translated into 350,000 hours of data – e.g. 65,000 phone calls, 25,000 SMS messages, 3.3 million scanned bluetooth devices and 2.5 million scanned 802.11 WLAN APs]](https://image.slidesharecdn.com/digitaltrails-daveking-1-5-10-part1-d3-100105055357-phpapp01/75/Digital-Trails-Dave-King-1-5-10-Part-1-D3-20-2048.jpg)