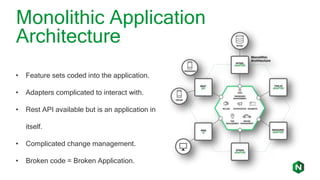
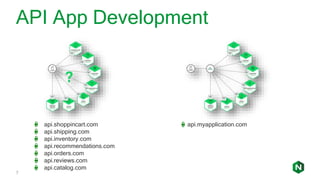
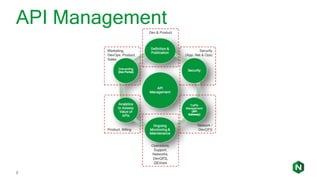
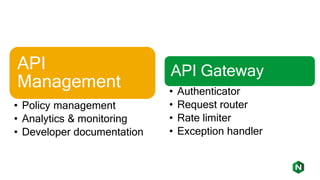
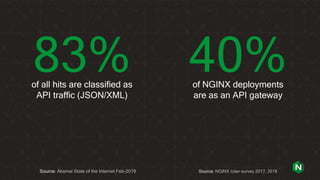
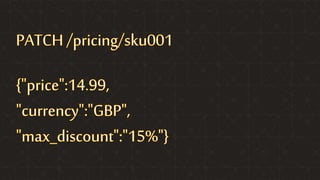
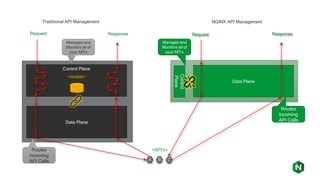
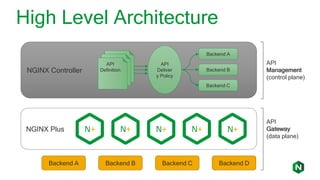
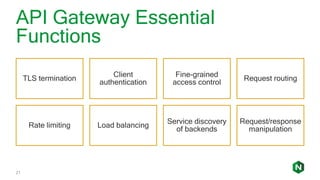
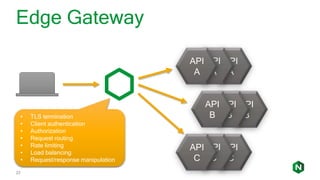
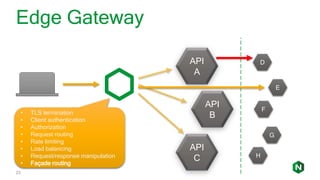
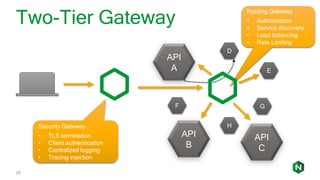
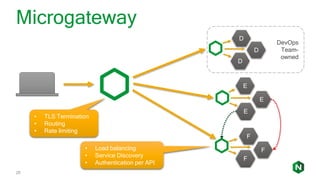
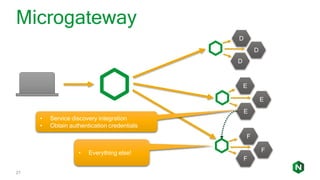
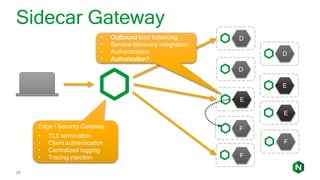
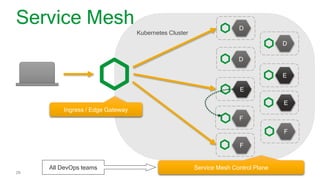
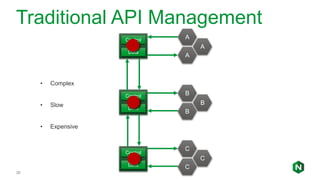
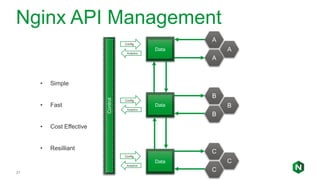
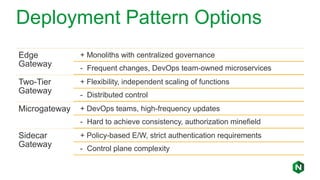
The document focuses on different API management and gateway deployment patterns, exploring the contrasts between traditional approaches and modern solutions like NGINX. It emphasizes the importance of scalability, flexibility, and efficient management within application architectures, particularly in the context of growing API traffic. Key functions and architectural considerations of API gateways, such as authentication, request routing, and load balancing, are also discussed with specific deployment scenarios.