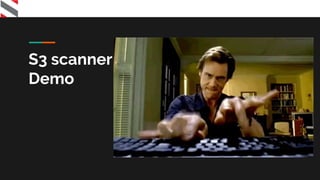
Deep-Dive into AWS Pentesting Cloud Security Workshop
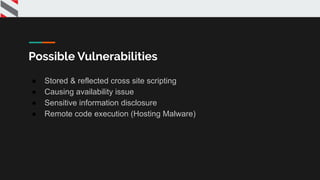
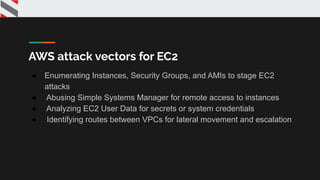
The presentation provides an overview of Amazon Web Services (AWS) and how to pentest AWS services. It covers various AWS services like EC2, S3, Lambda, RDS, IAM and tools that can be used for pentesting. It demonstrates how to find and exploit vulnerabilities in S3 buckets and discusses common attack vectors for services like EC2 and ways to escalate privileges in IAM. The presentation aims to help security professionals learn how to securely test cloud environments hosted on AWS.


























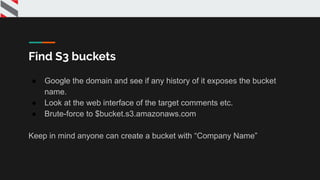
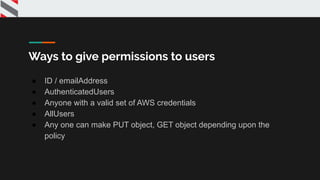
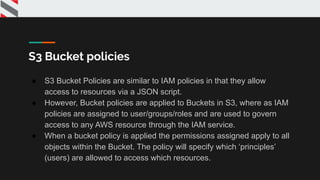
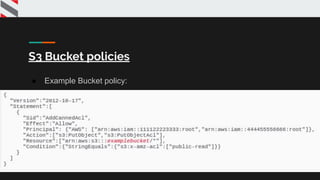
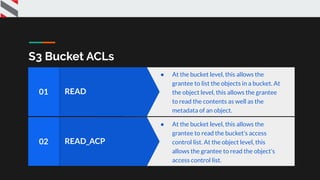
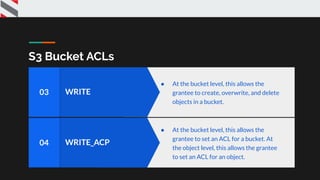
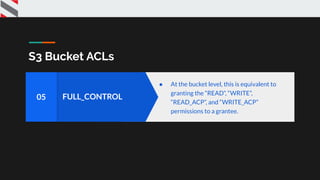
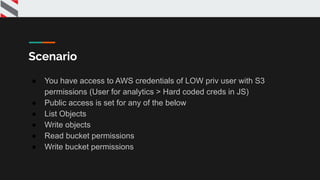

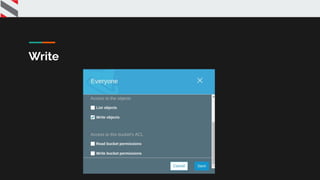
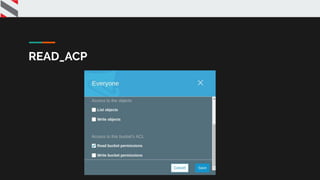
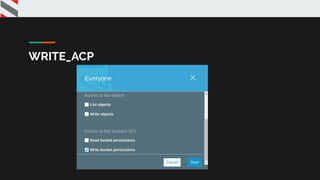


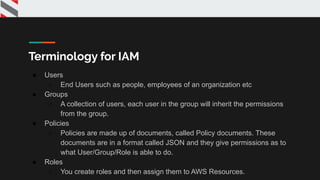
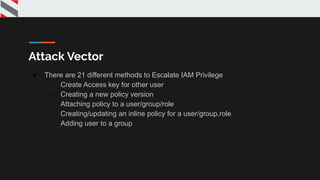

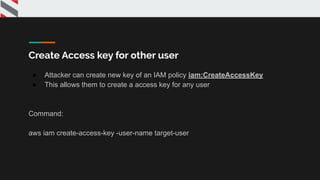
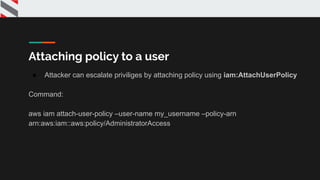
![{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:Get*",
"s3:List*"
],
"Resource": "*"
}
]
}
Normal user policy](https://image.slidesharecdn.com/deepdiveintocloudsecurity-200130055415/85/Deep-dive-into-cloud-security-Jaimin-Gohel-Virendra-Rathore-74-320.jpg)
![{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
Admin Policy](https://image.slidesharecdn.com/deepdiveintocloudsecurity-200130055415/85/Deep-dive-into-cloud-security-Jaimin-Gohel-Virendra-Rathore-75-320.jpg)