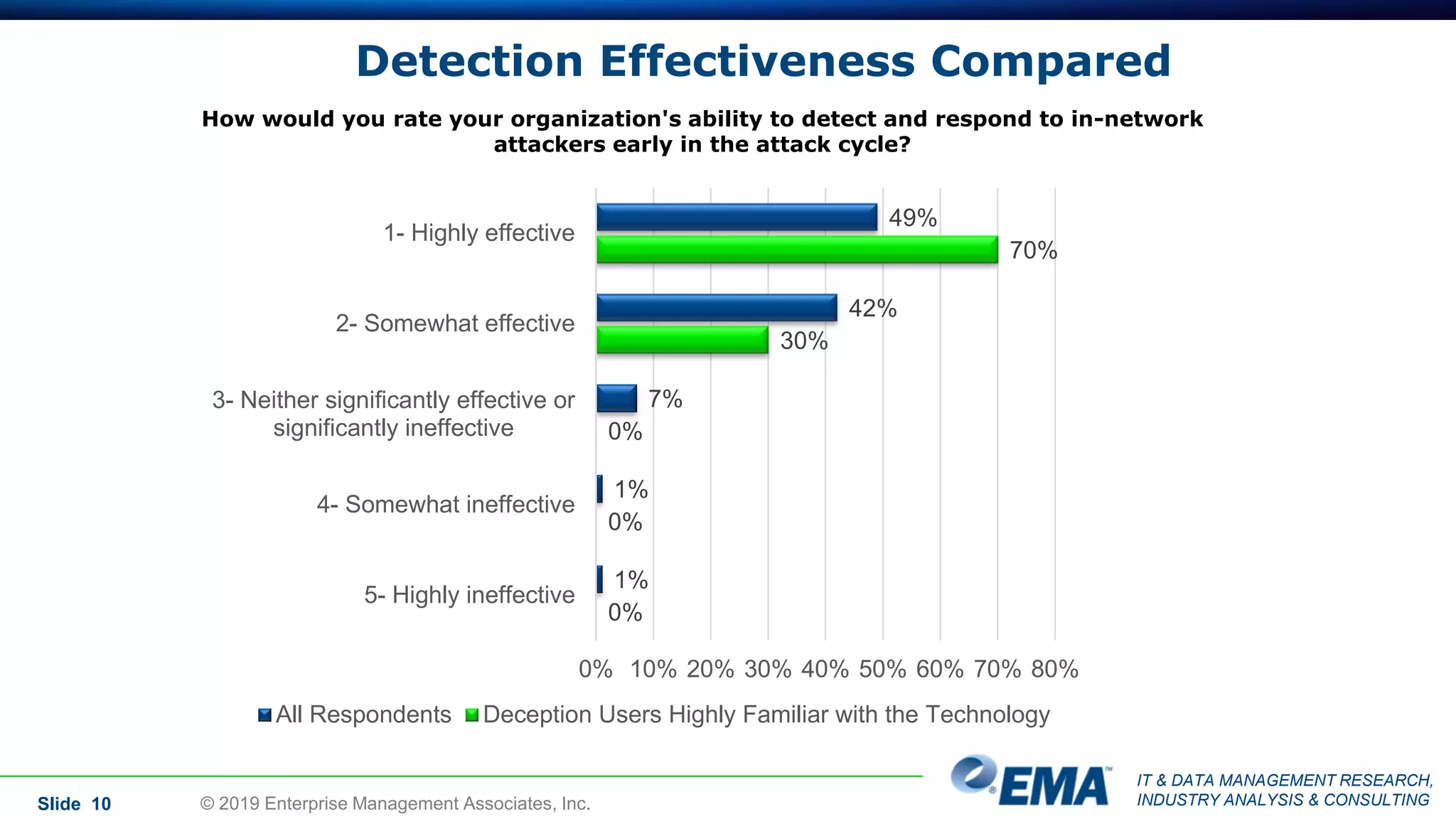
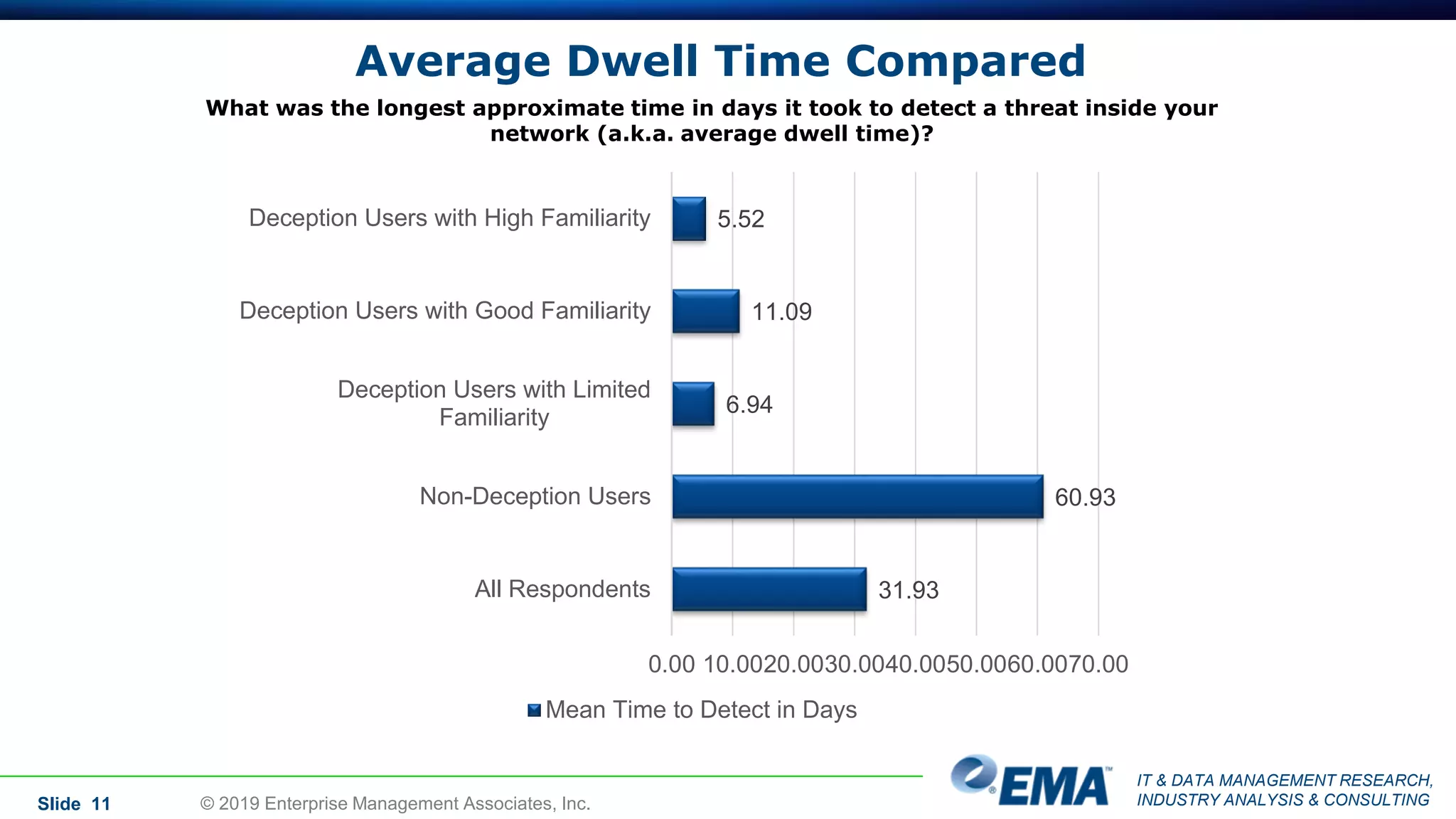
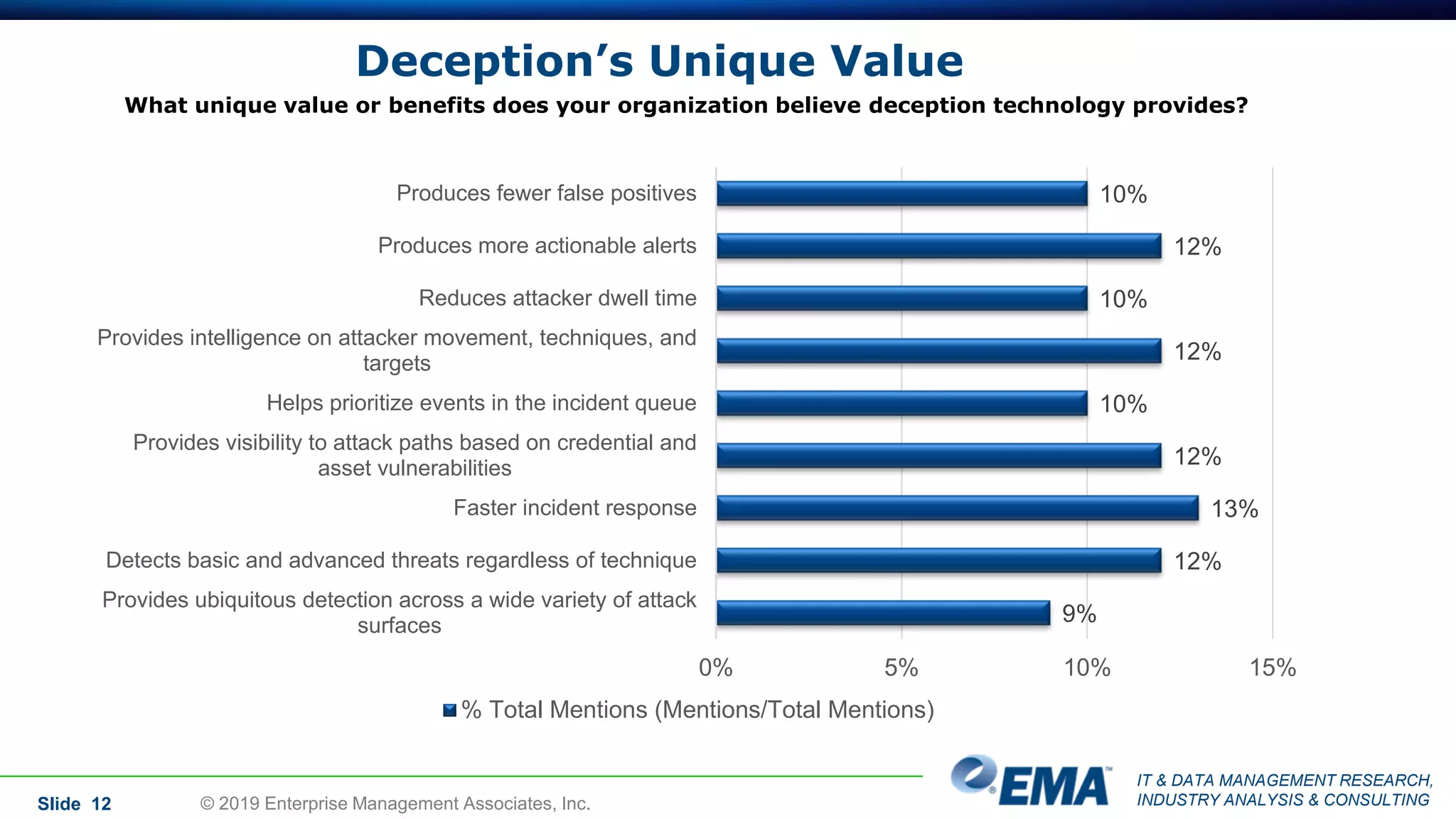
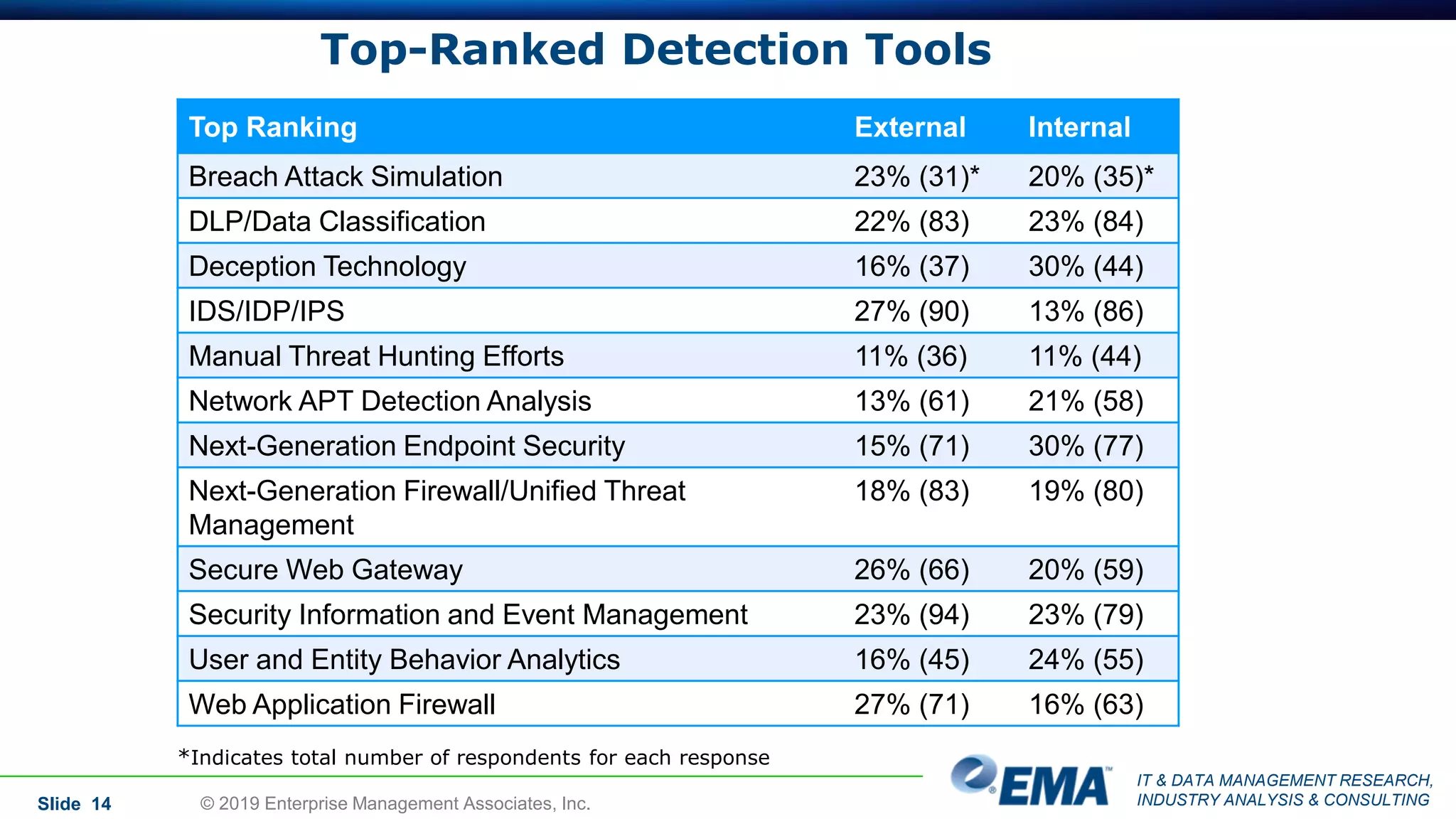
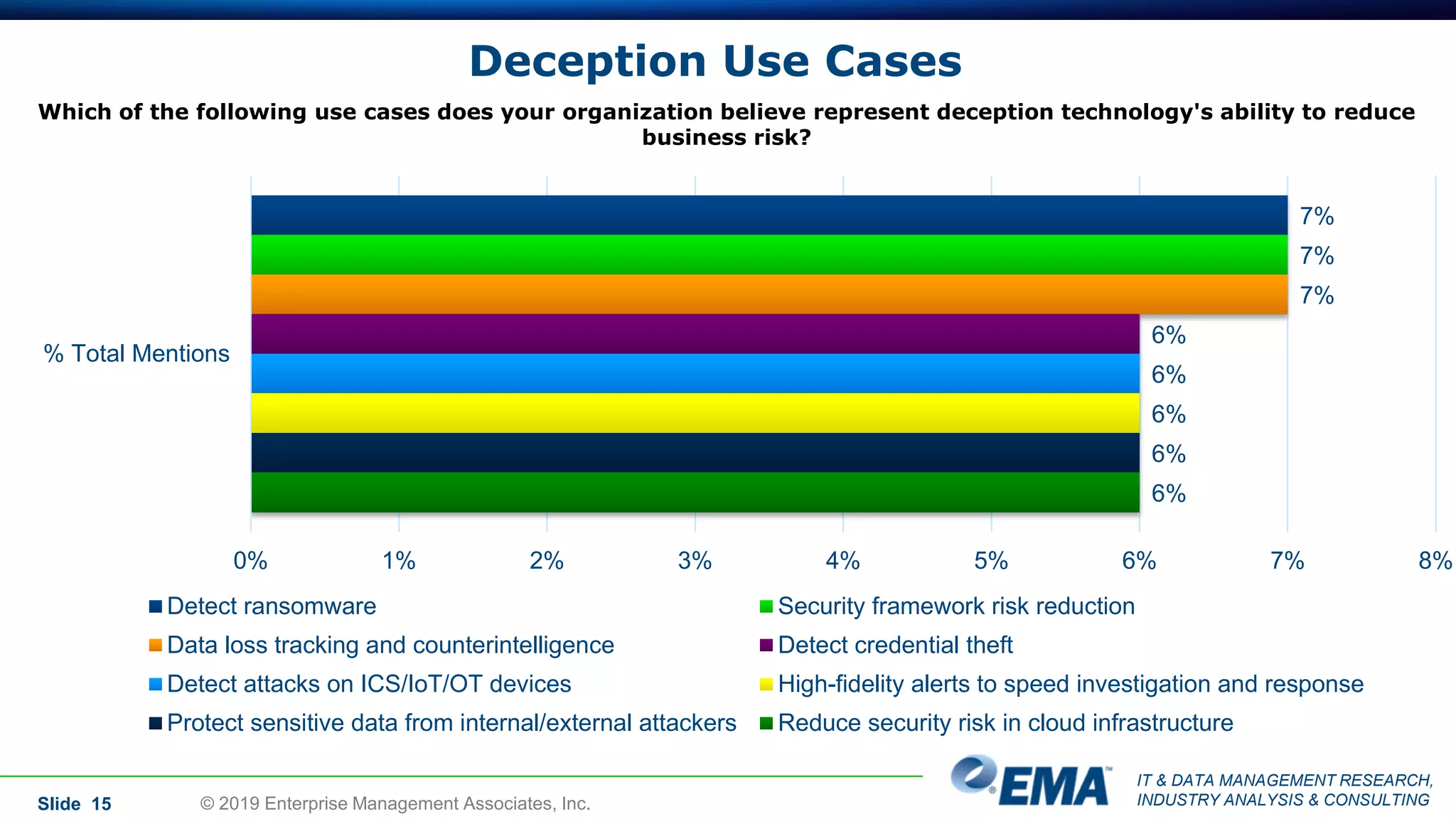
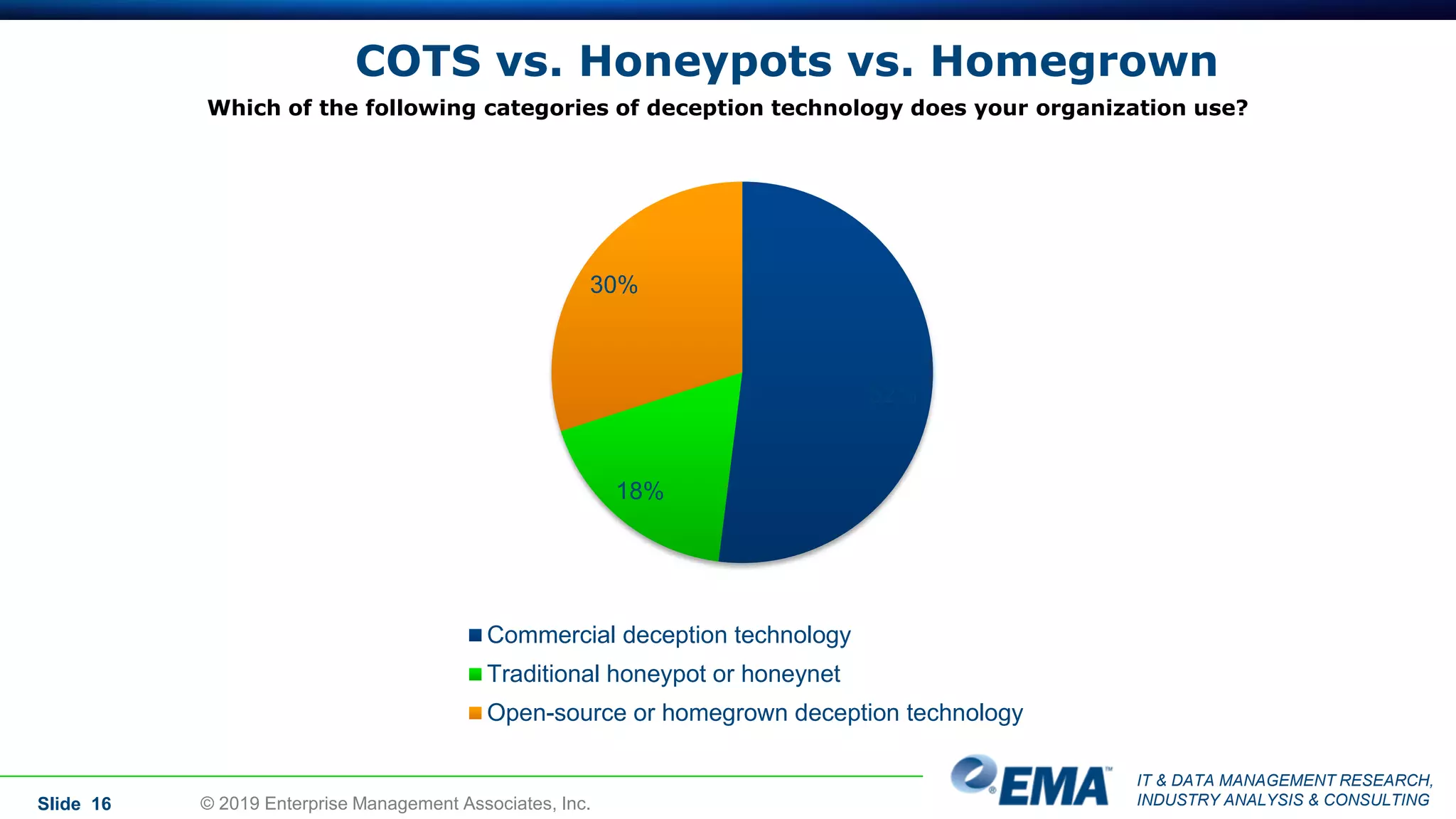
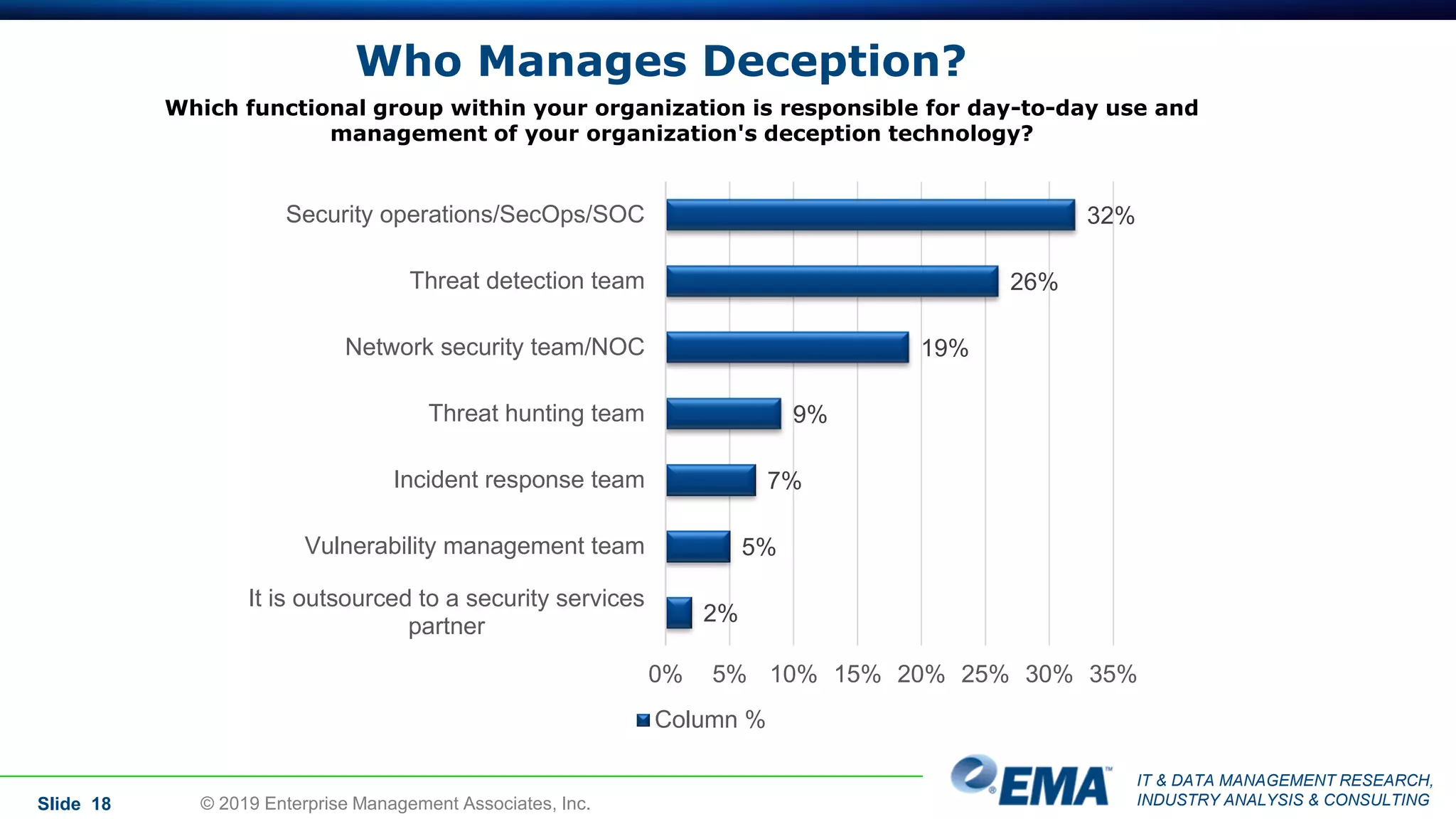
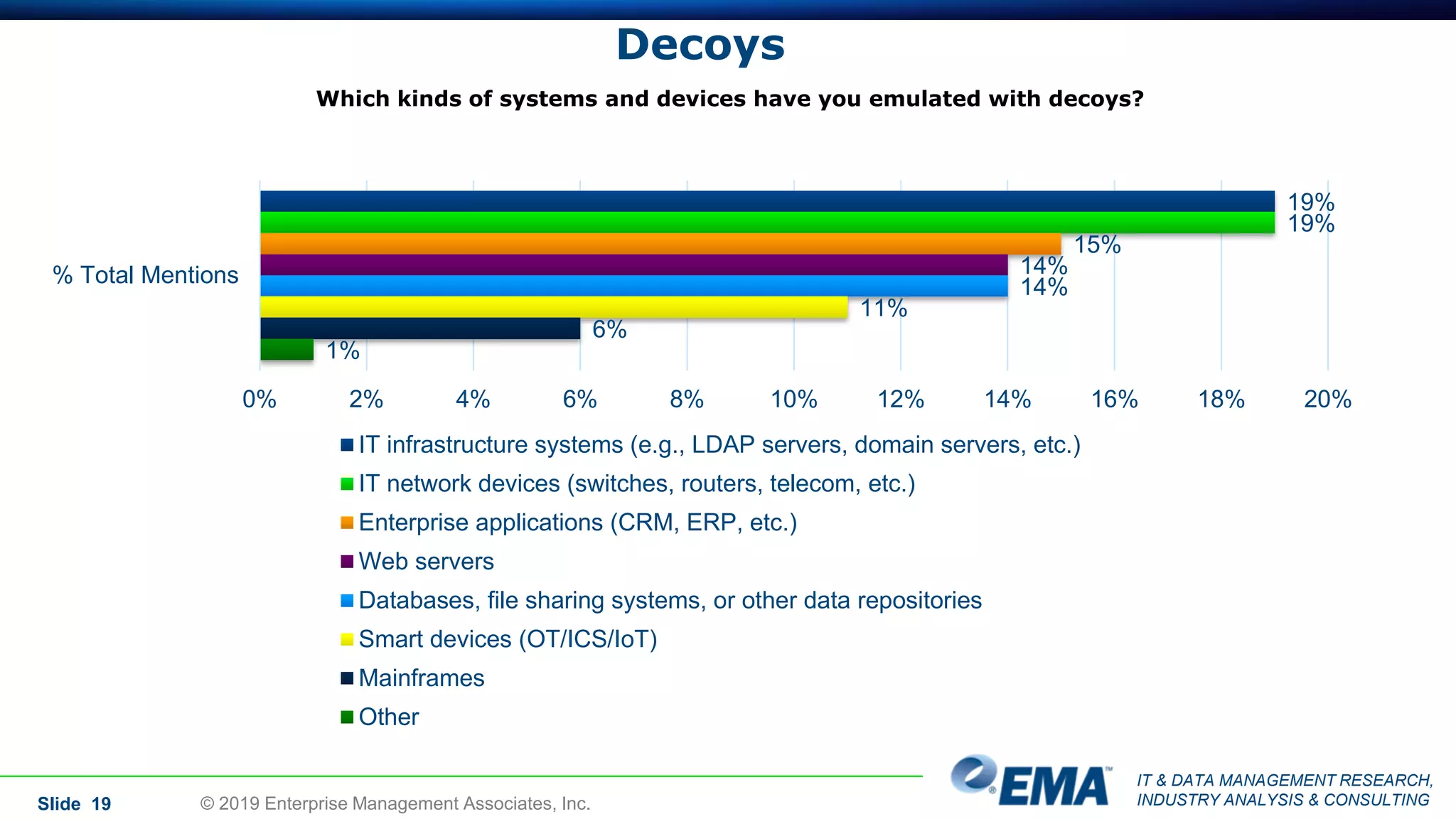
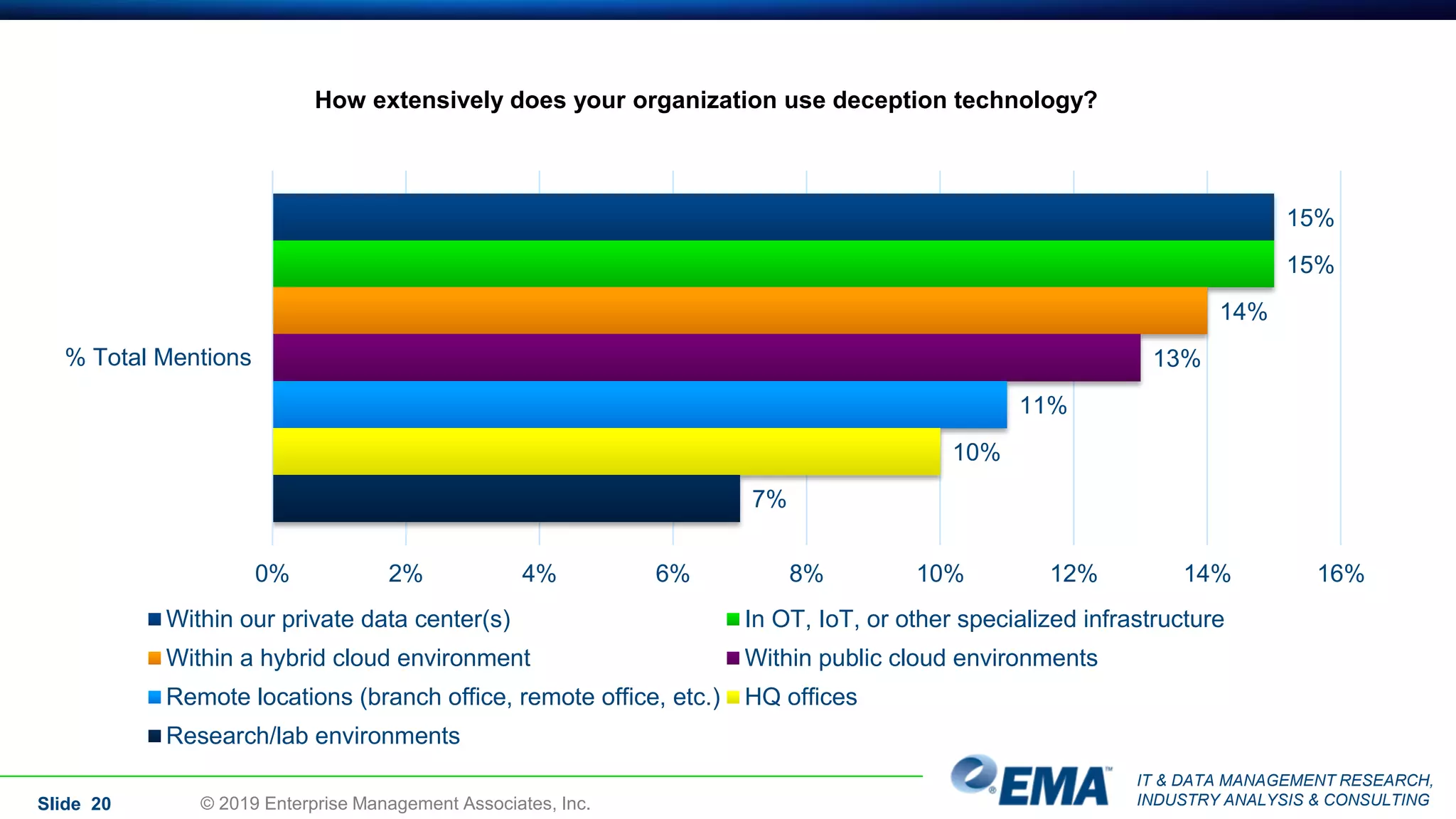
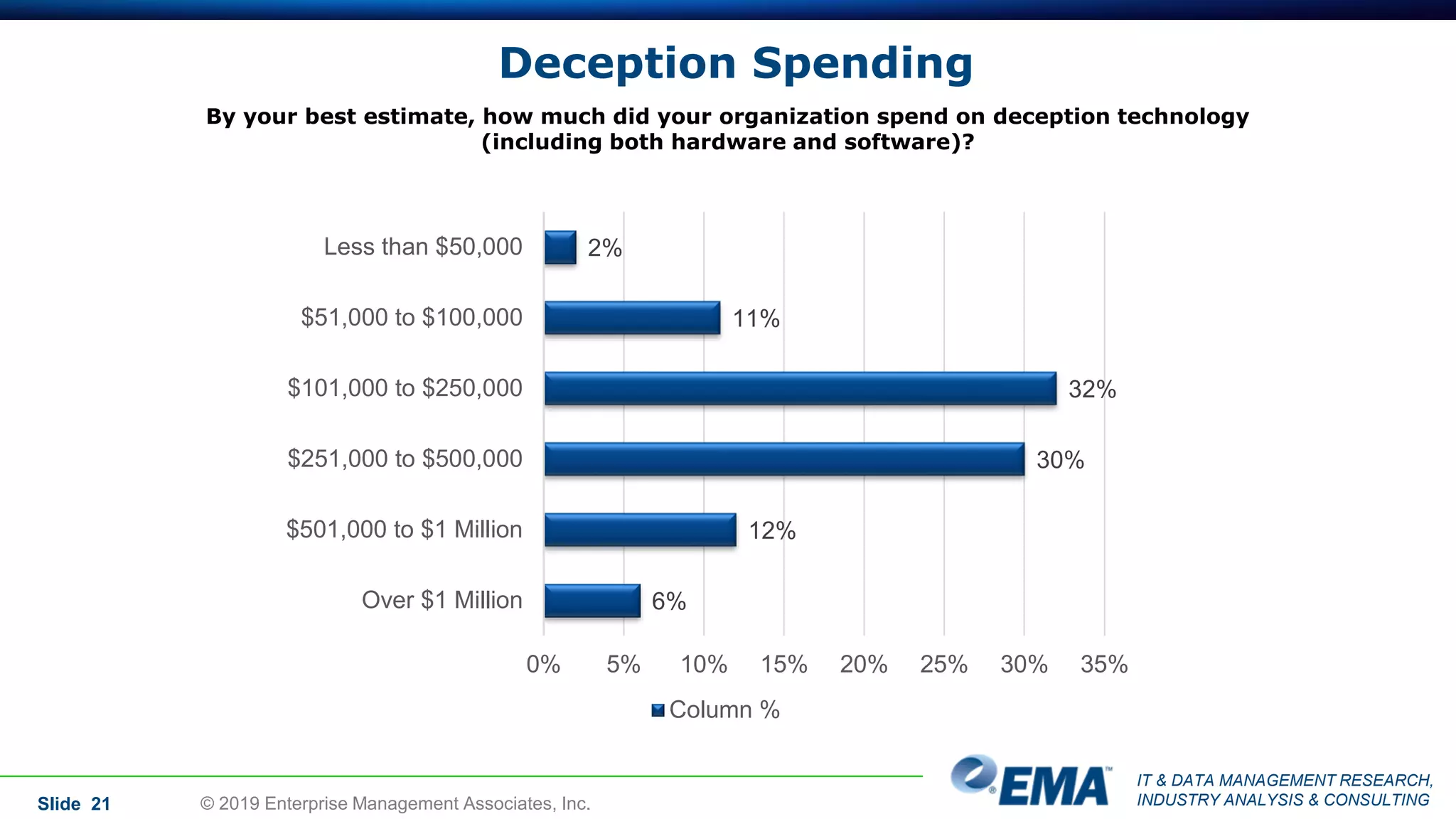
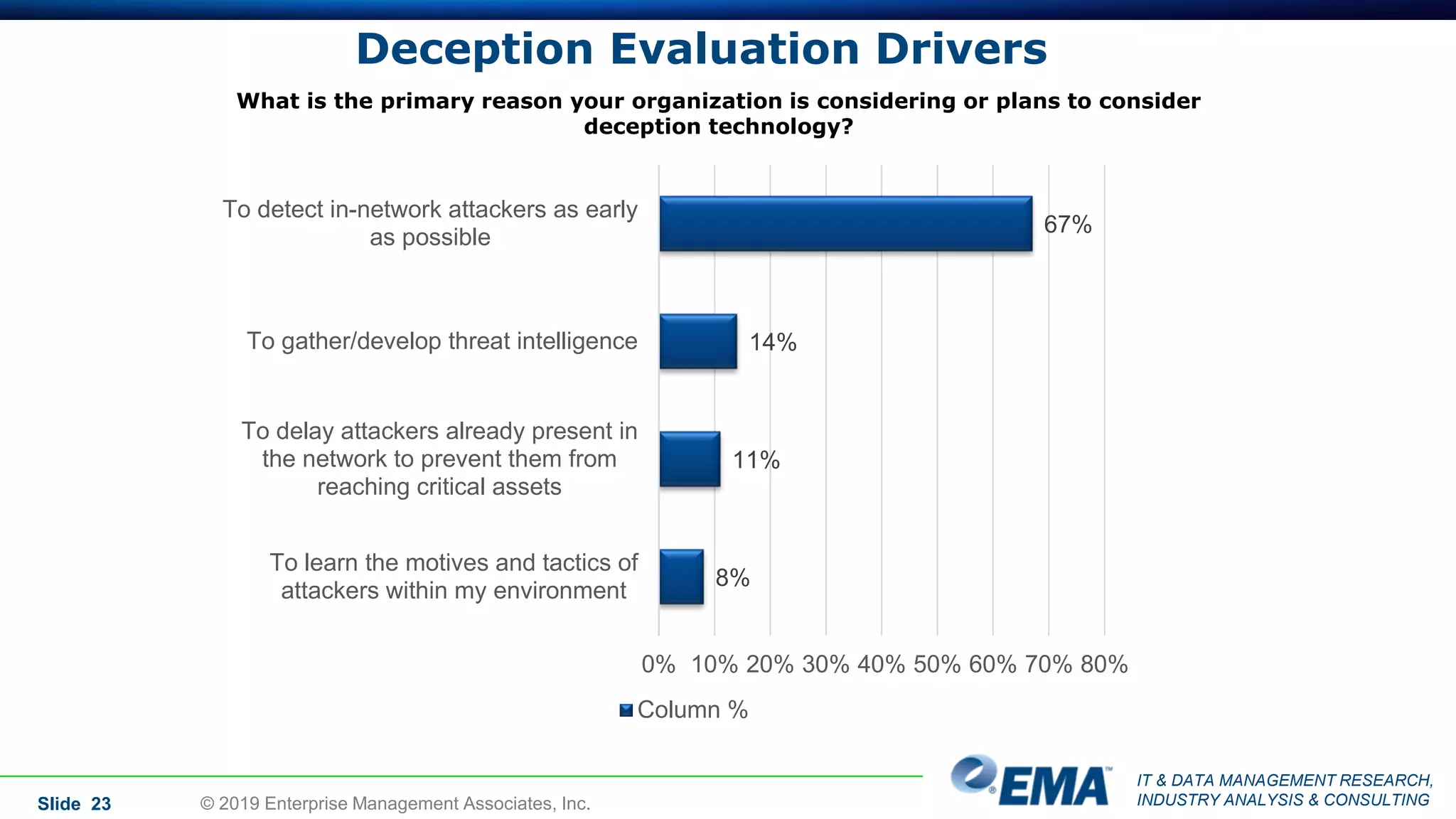
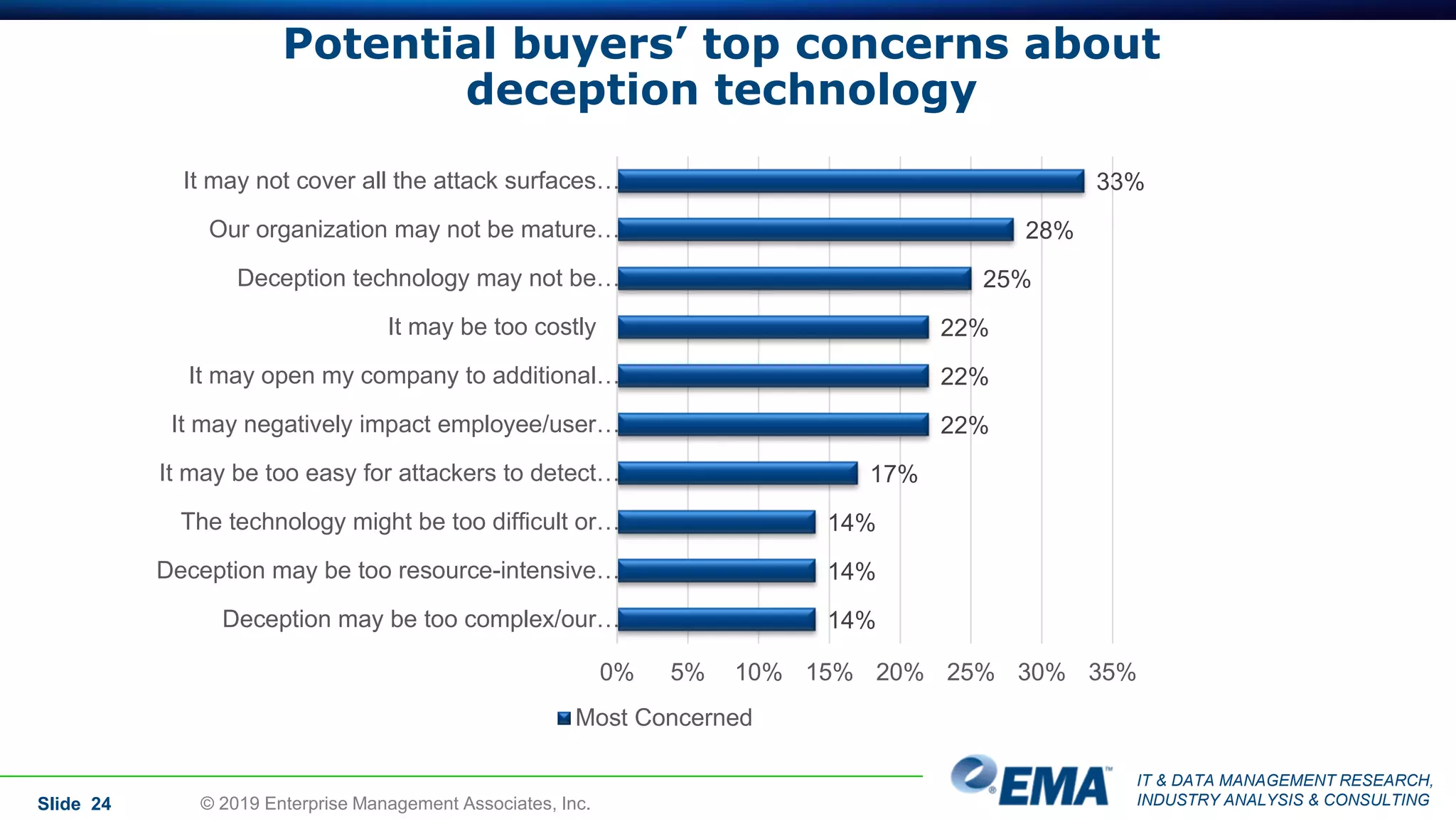
The document provides a comprehensive guide on deception technology in the field of IT and cybersecurity, detailing its advantages, application, and demographics of users. It highlights key findings from a survey of 208 respondents regarding usage practices, organizational management, and reported effectiveness of deception technology against cyber threats. The guide also addresses concerns potential buyers have about adopting this technology and features insights from experienced industry analysts.