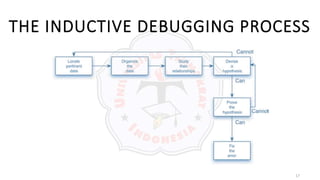
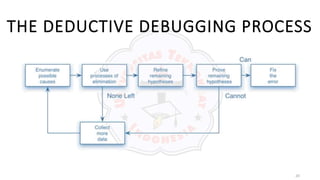
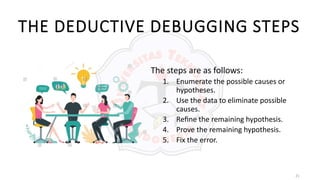
The document discusses various debugging techniques. It describes the brute force method, which involves taking memory dumps and adding print statements to locate bugs. This generates a large amount of data but requires little thought. The cause elimination method deduces or induces potential causes and tests hypotheses to eliminate them one by one. Other methods include trial and error, backtracking code to find failures, and forward tracking to see when results first became wrong. Principles for locating errors include thinking carefully and getting a fresh perspective. Principles for repairing errors are to fix the underlying cause, check for new errors, and re-evaluate the design when making changes.