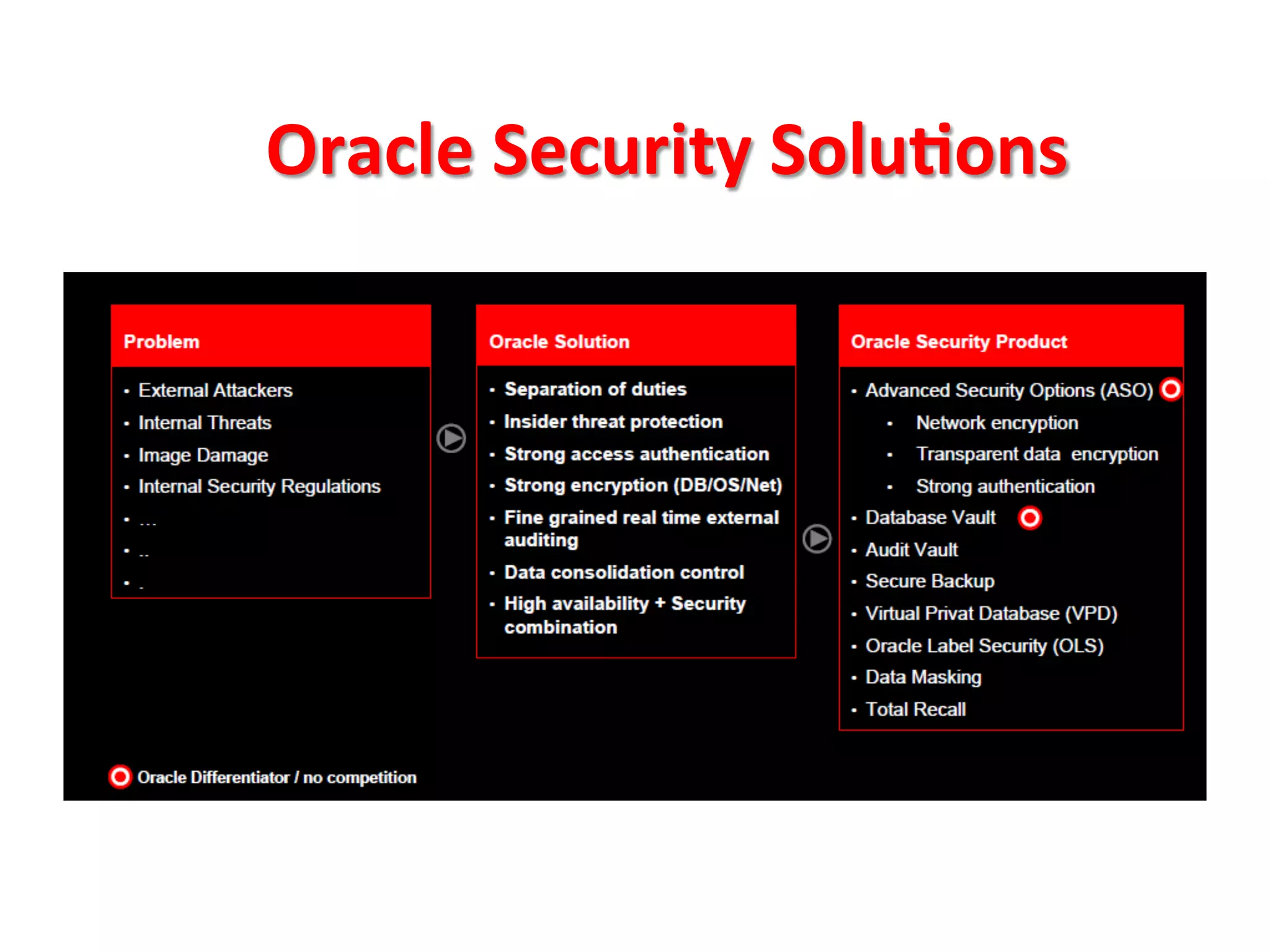
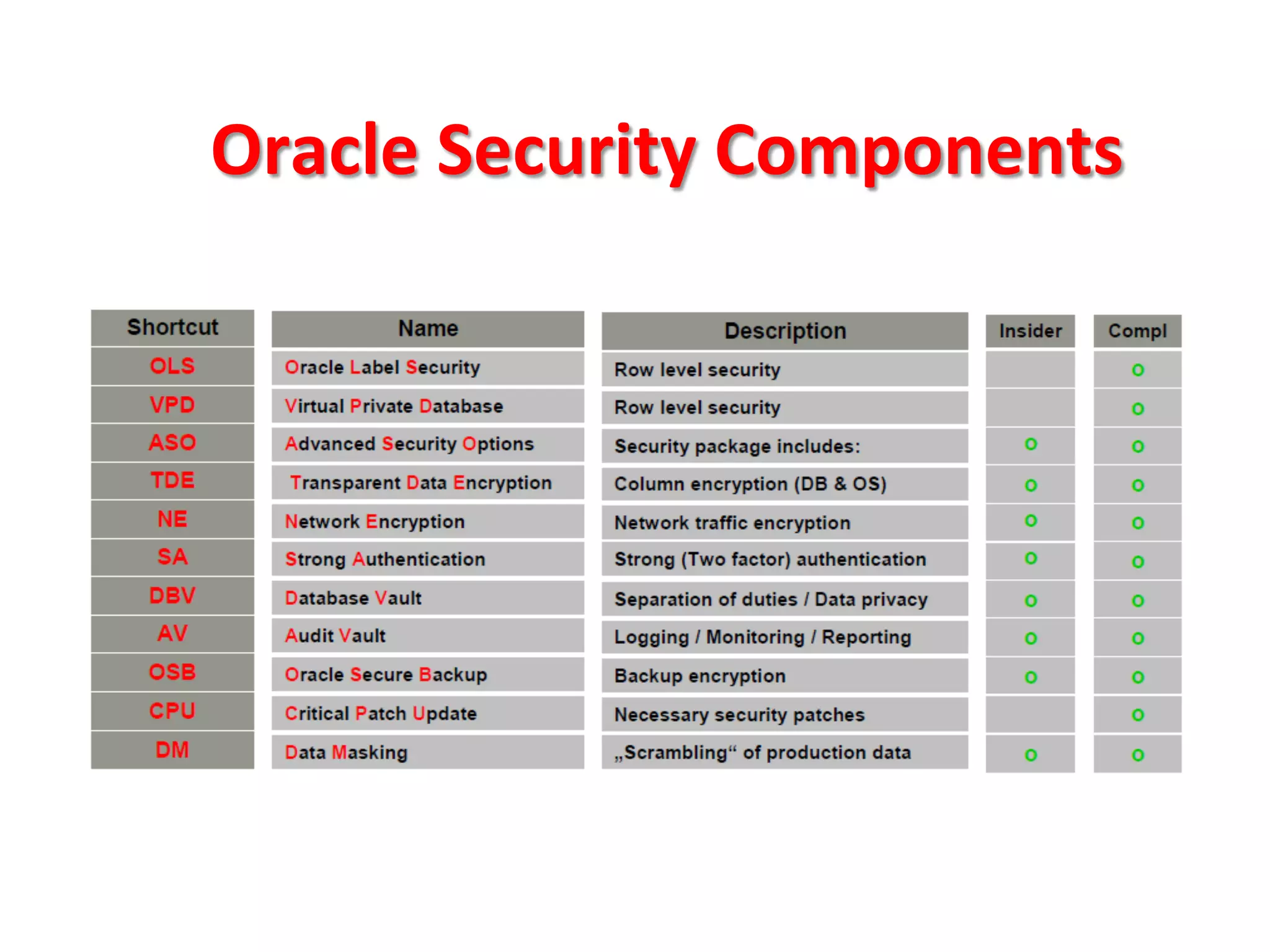
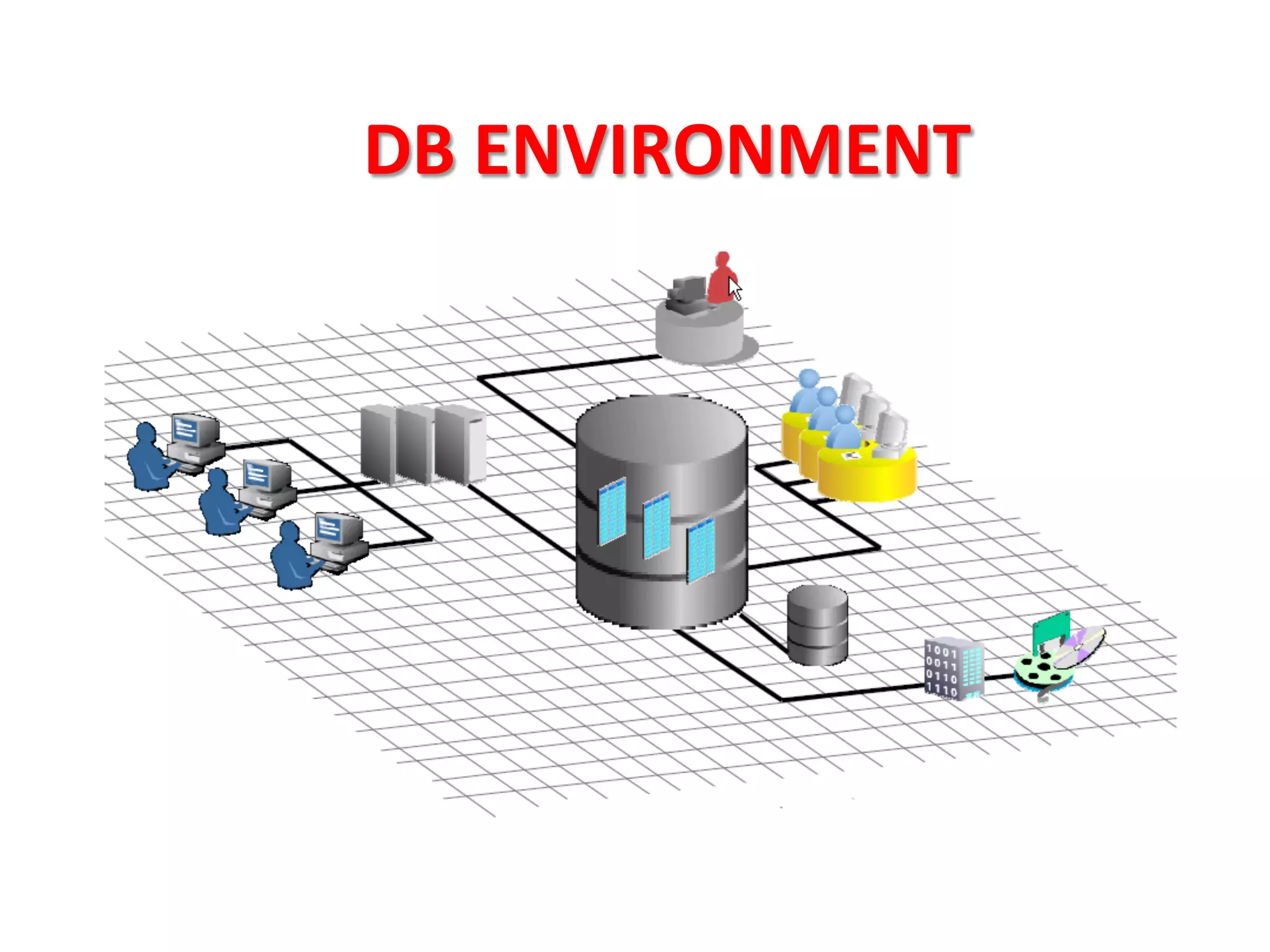
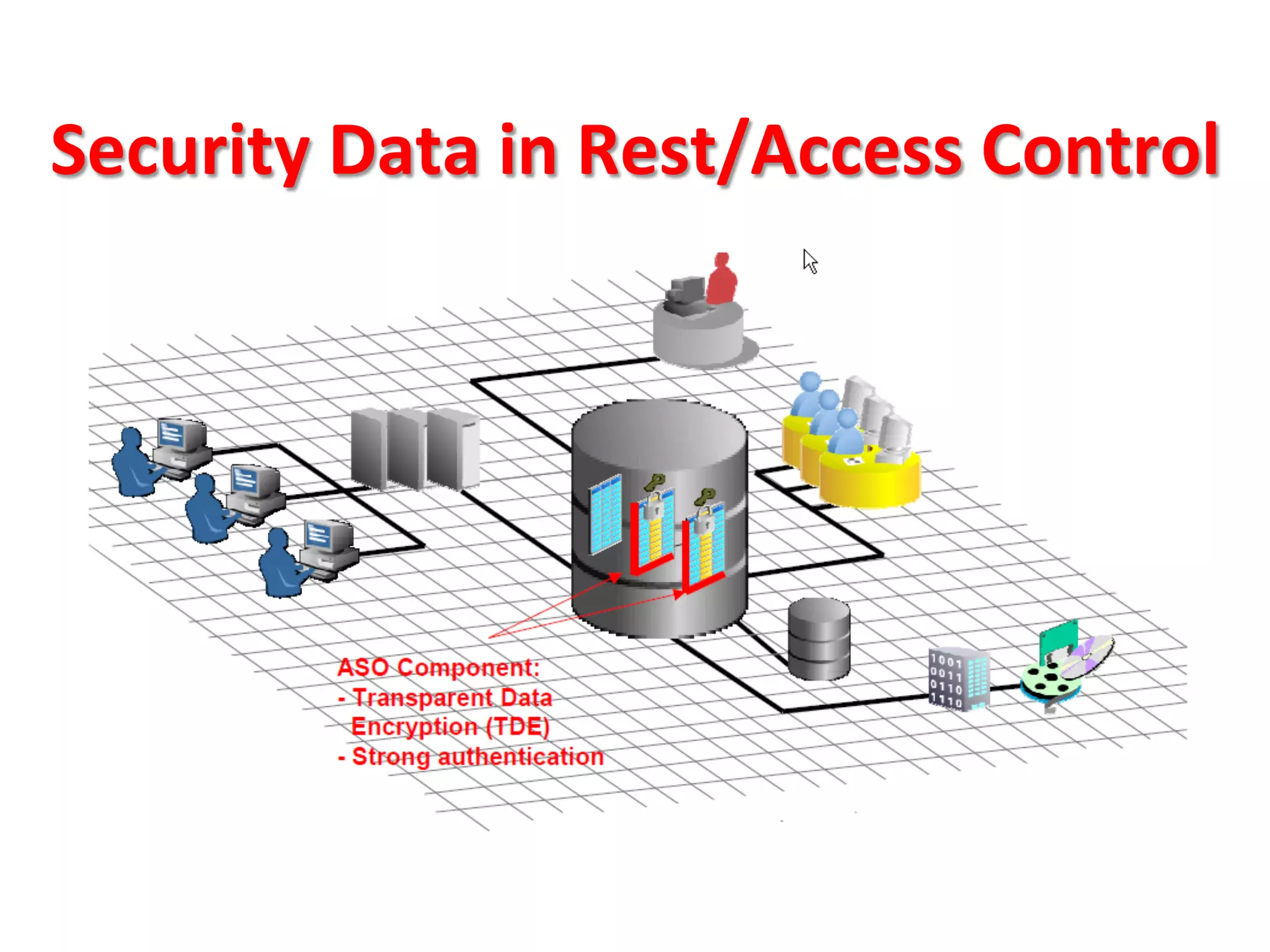
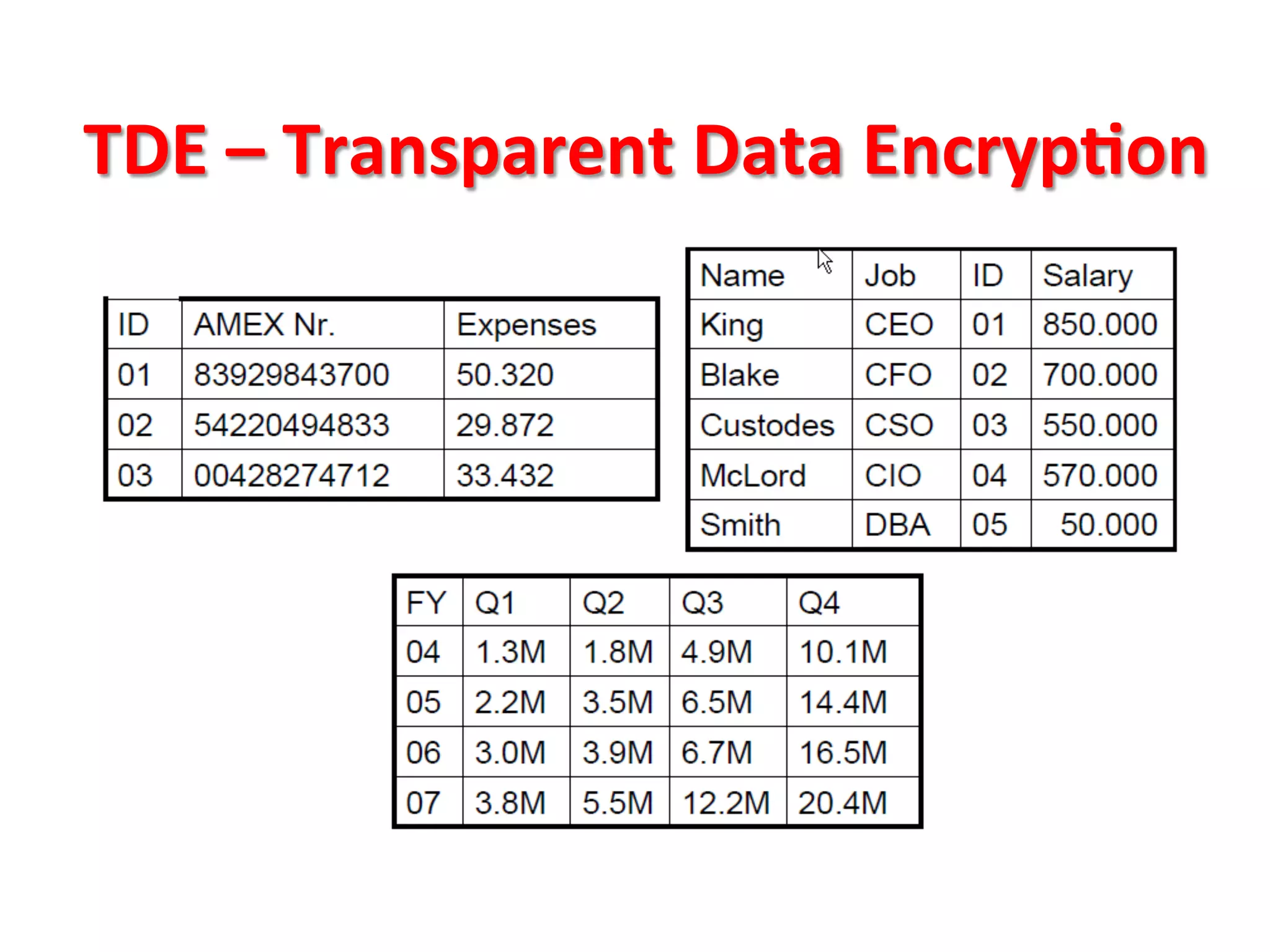
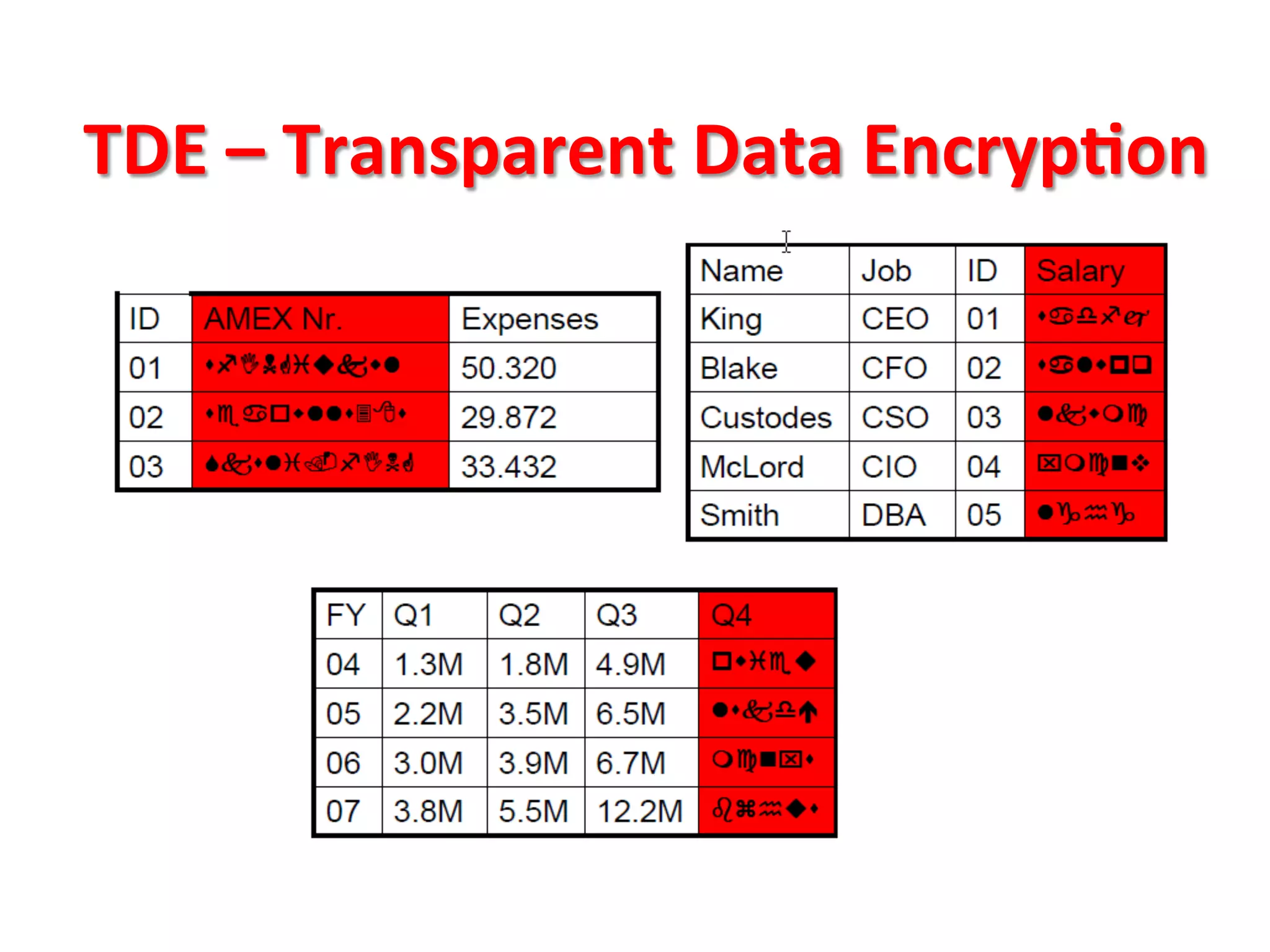
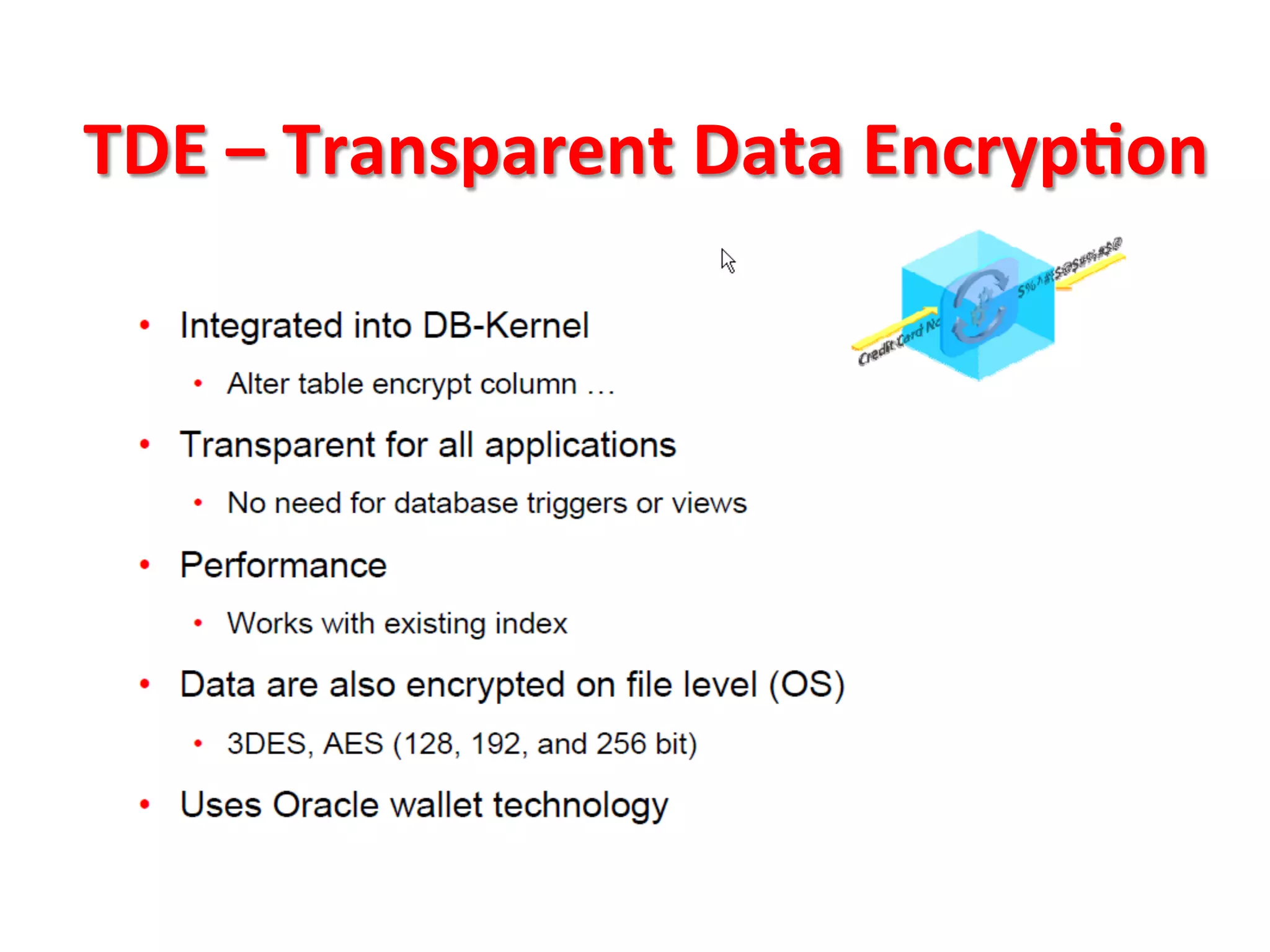
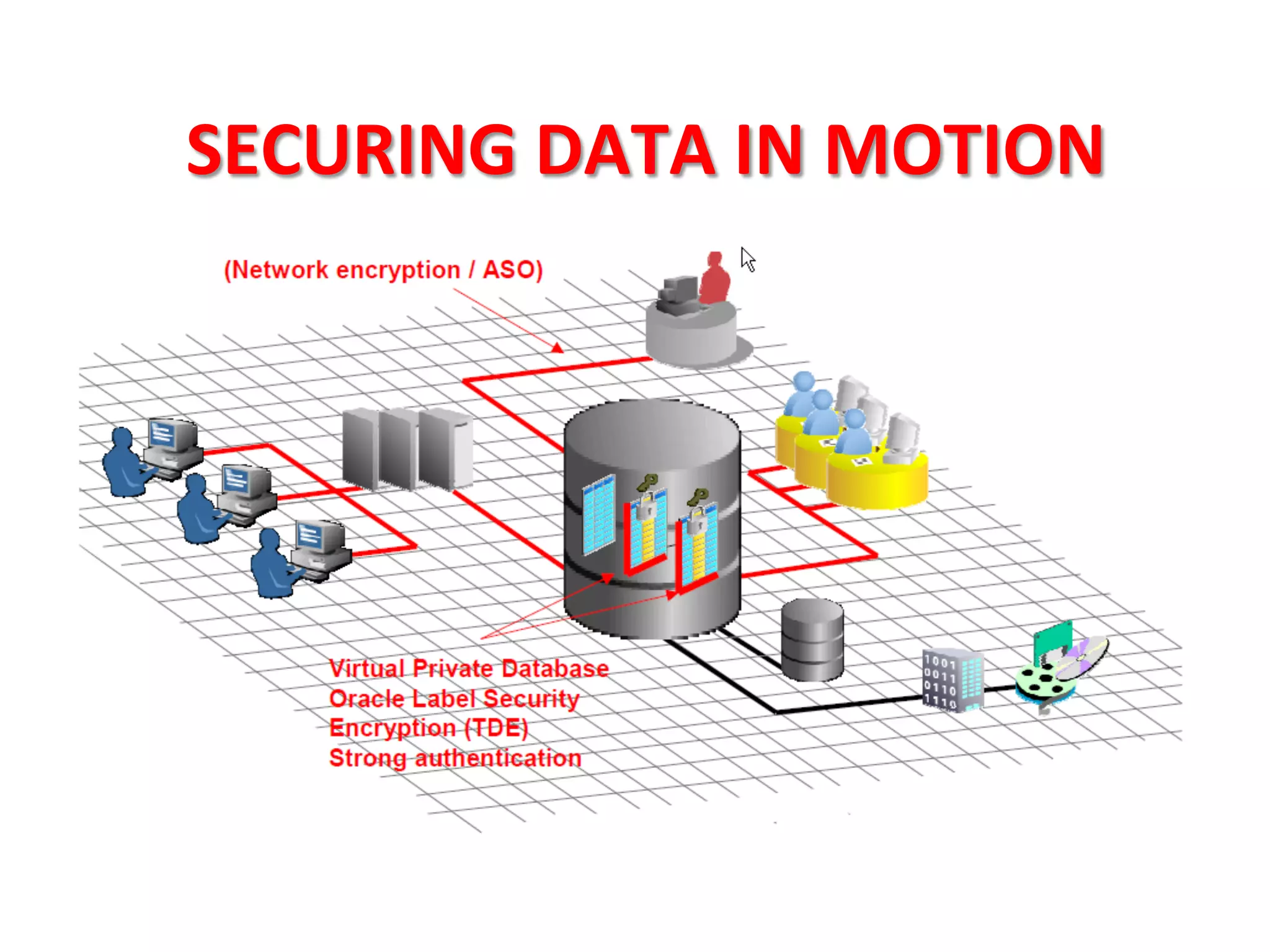
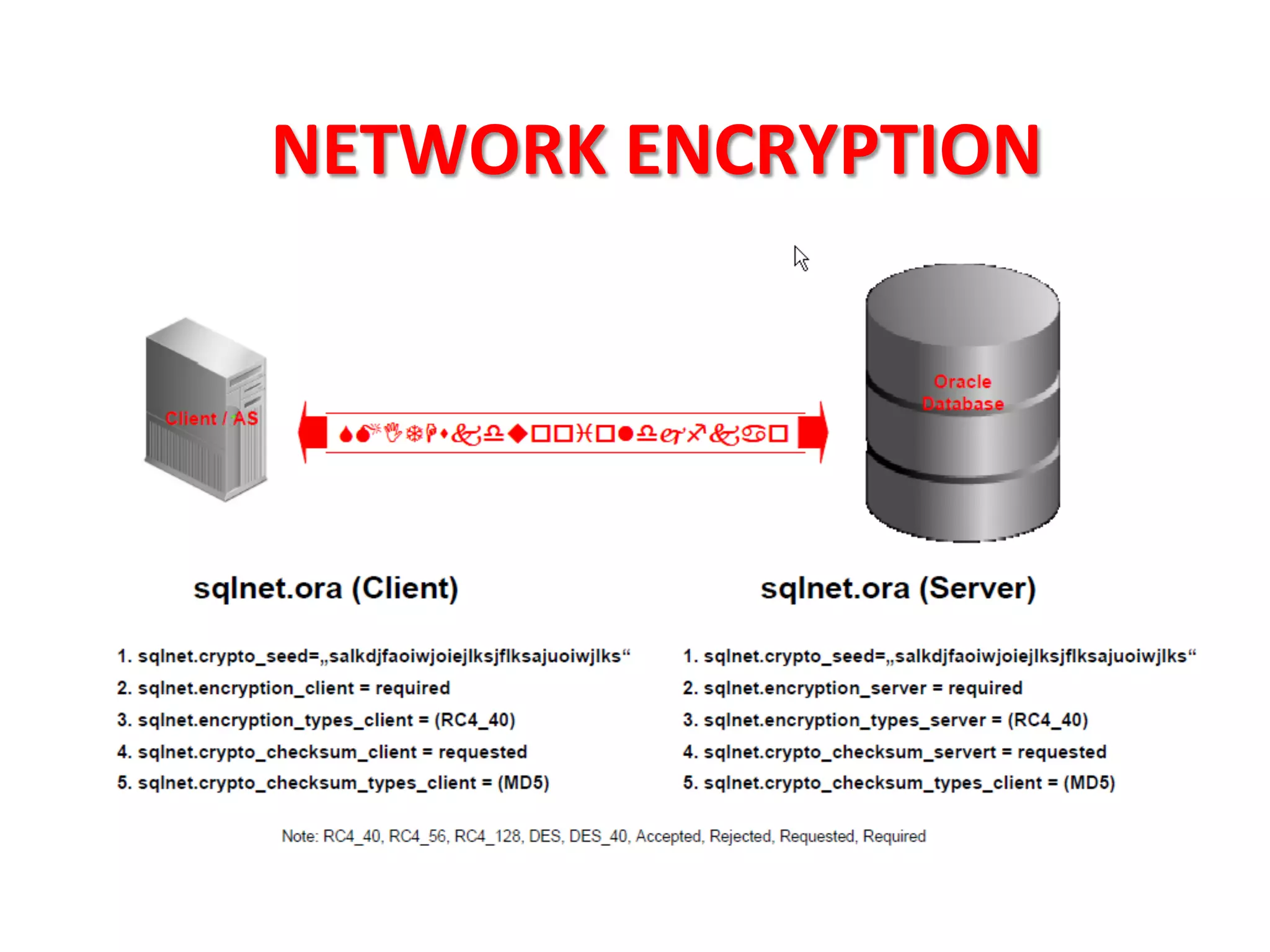
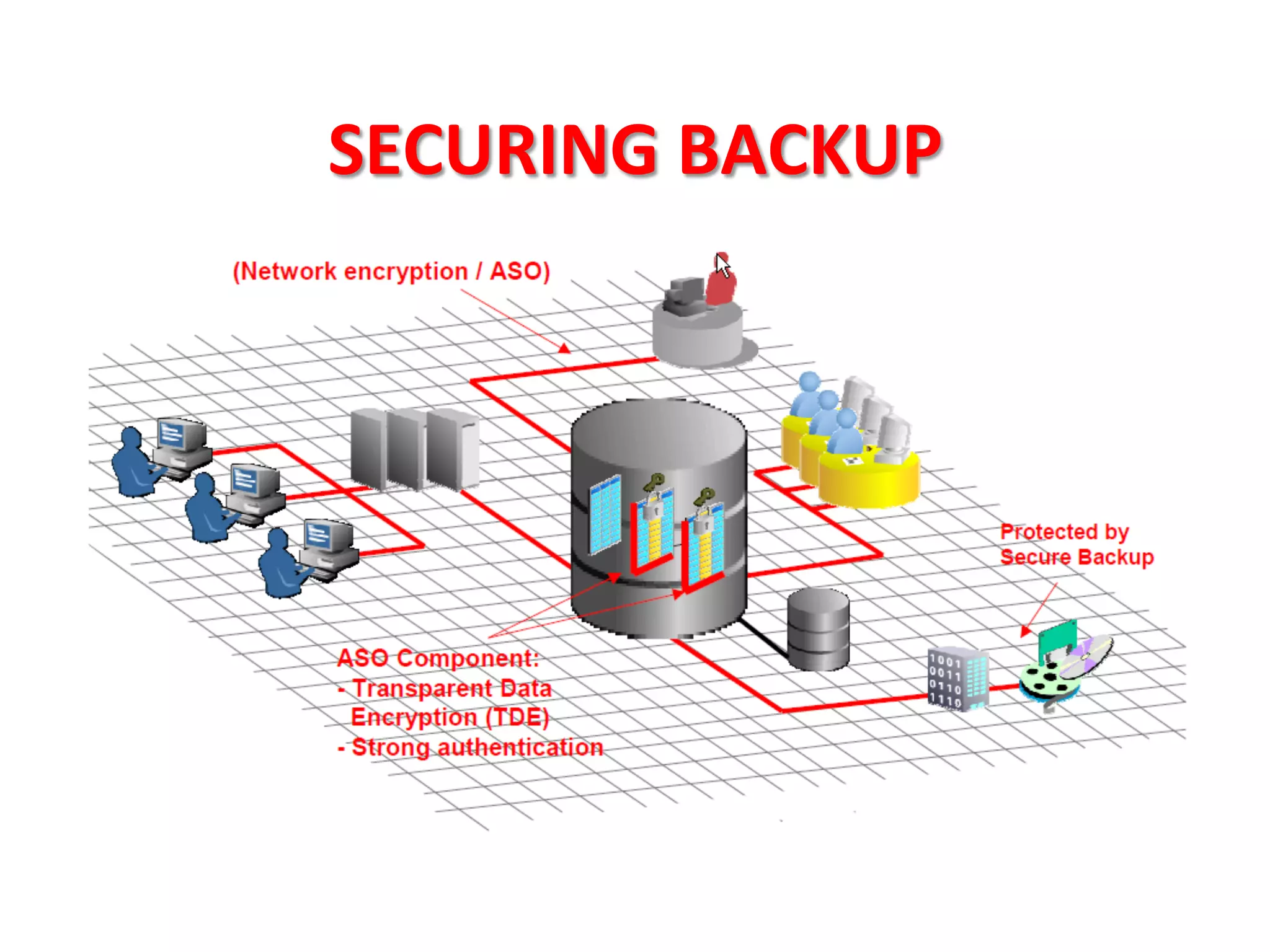
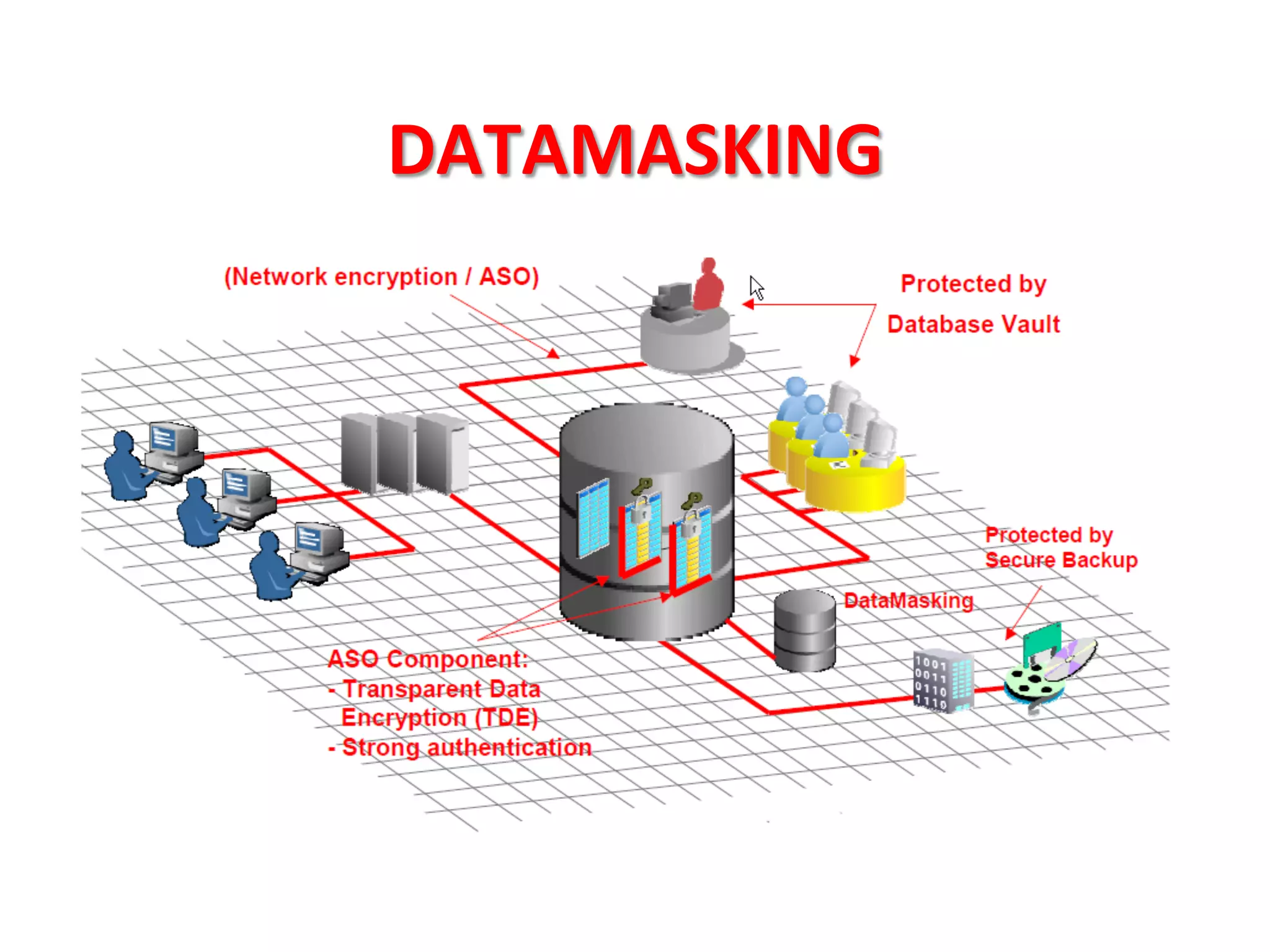
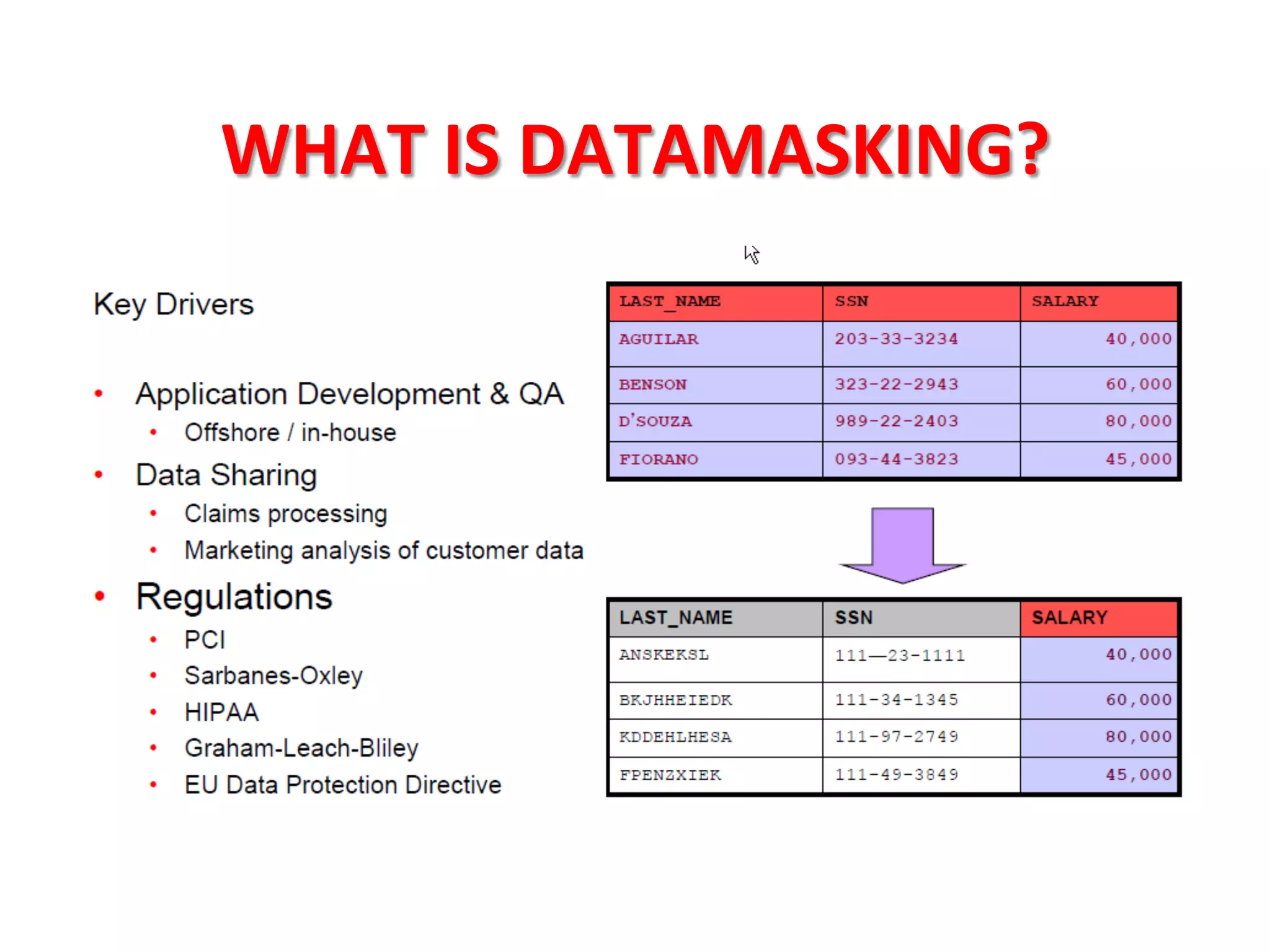
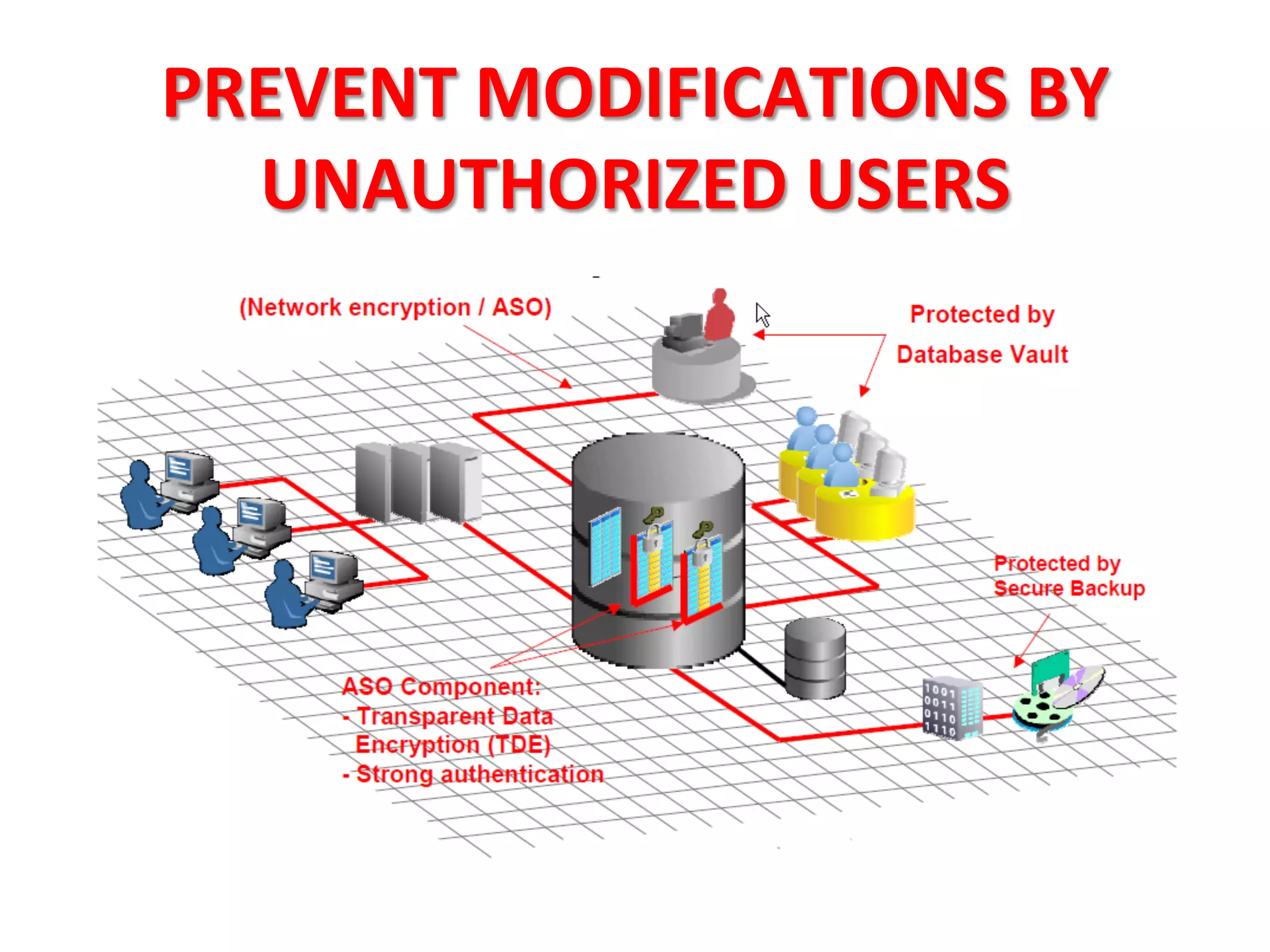
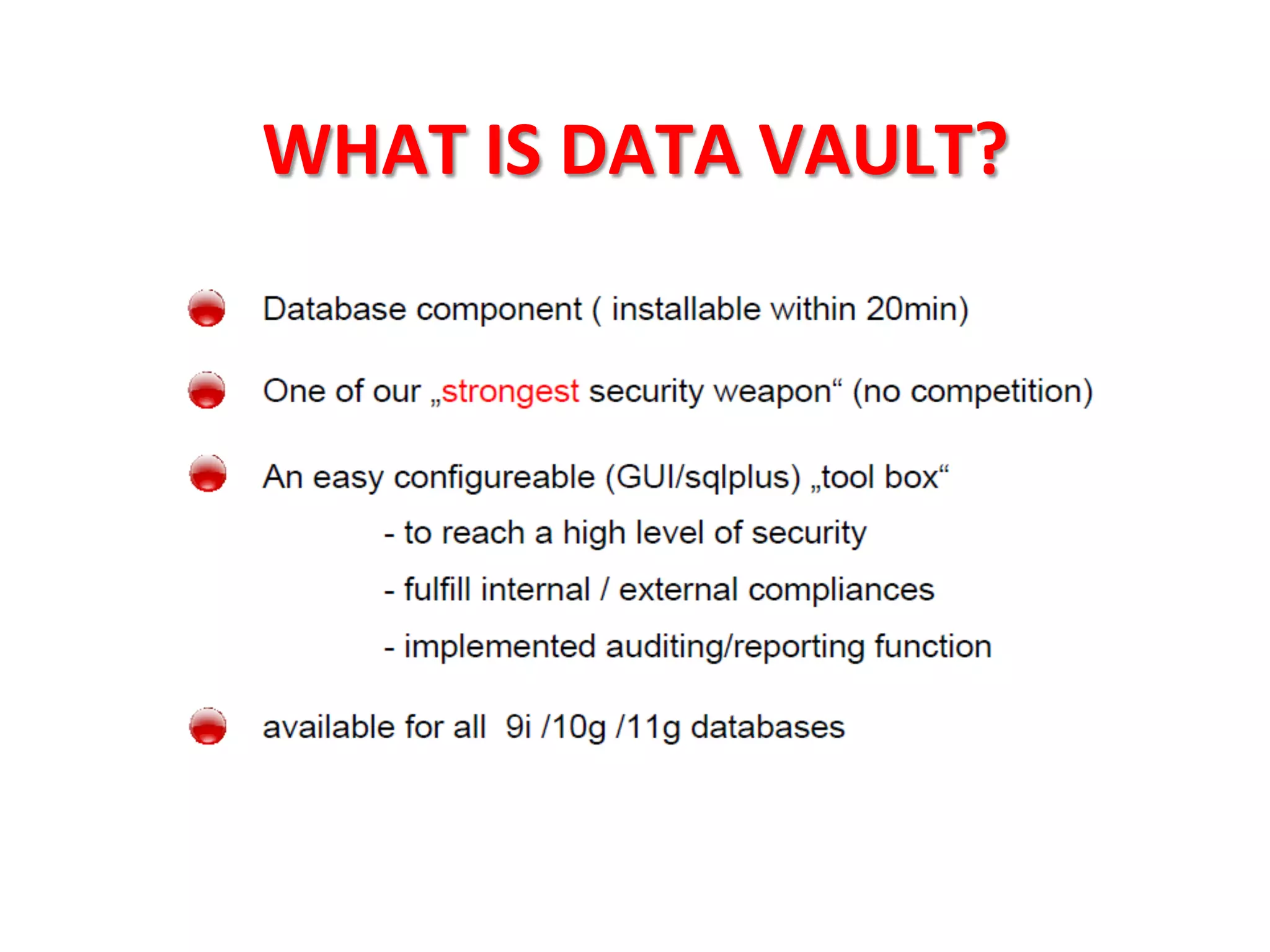
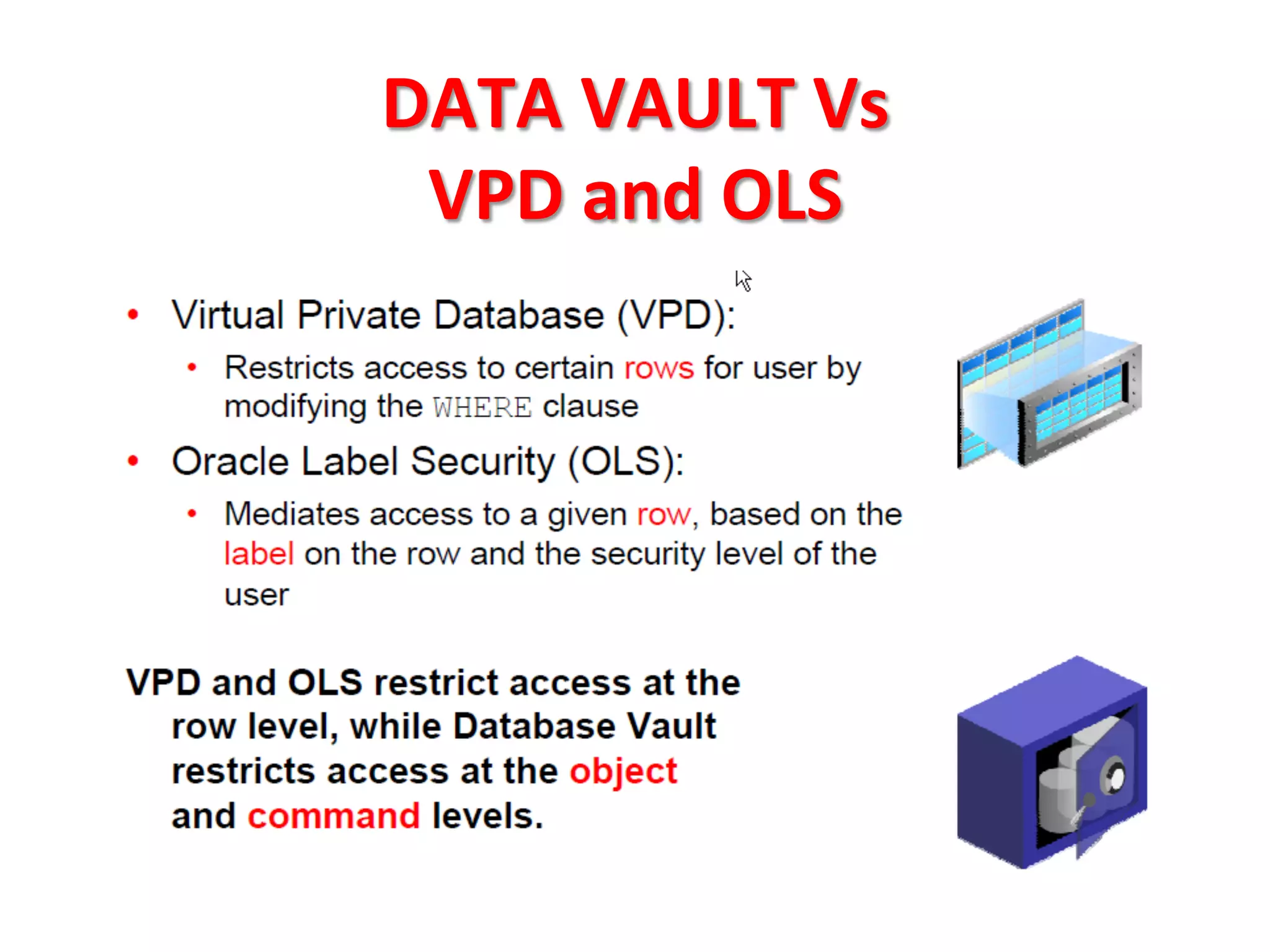
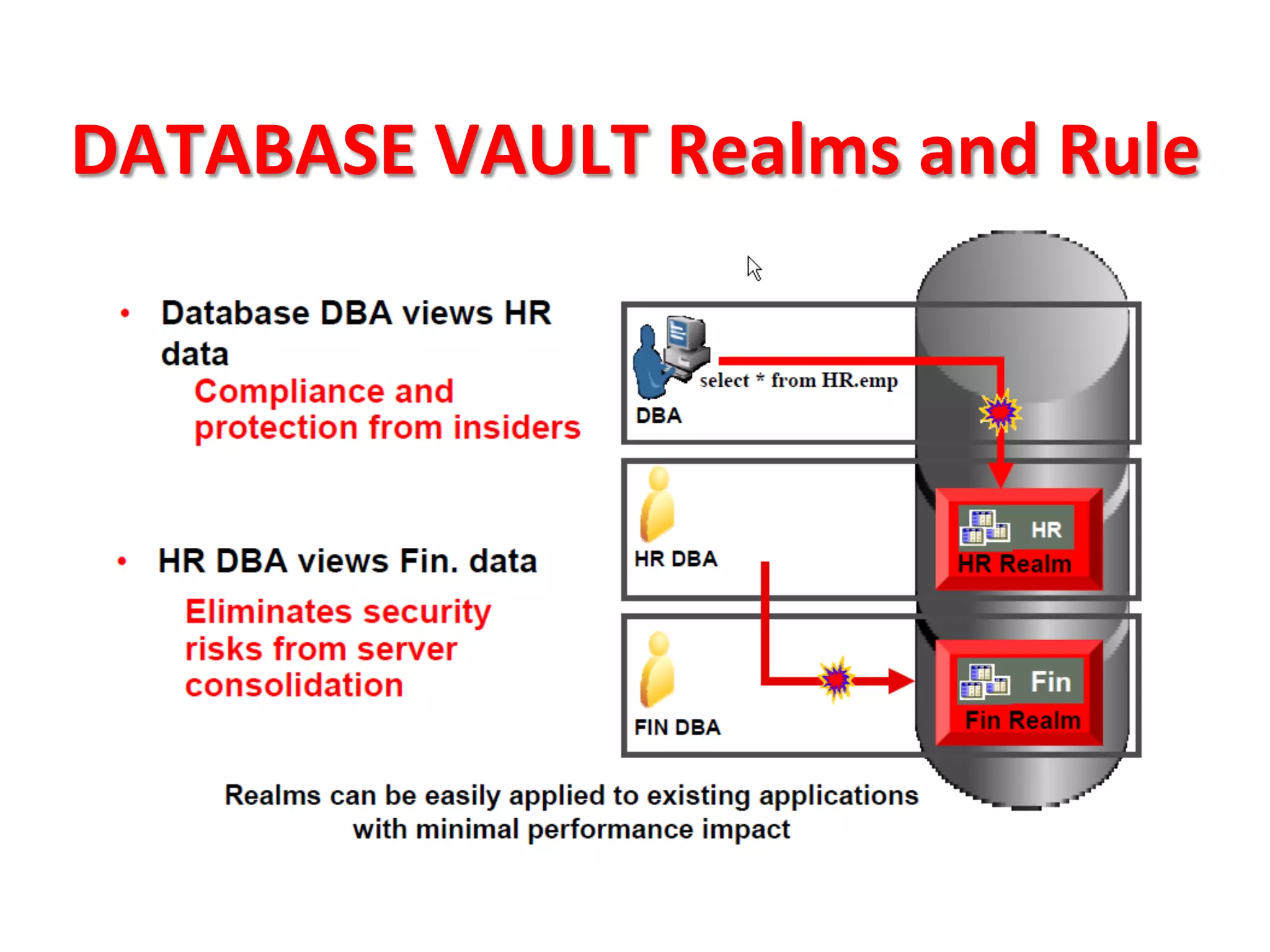
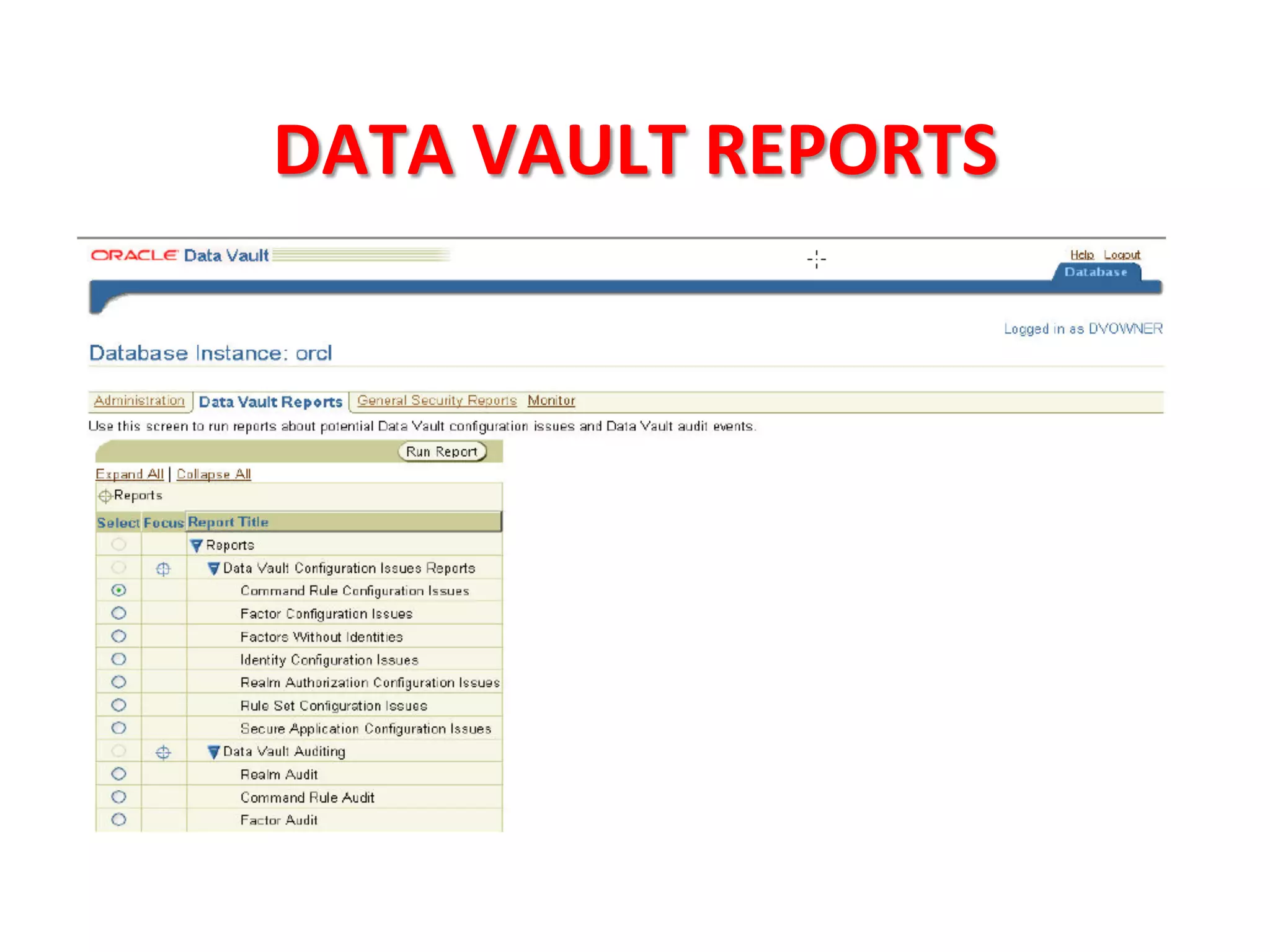
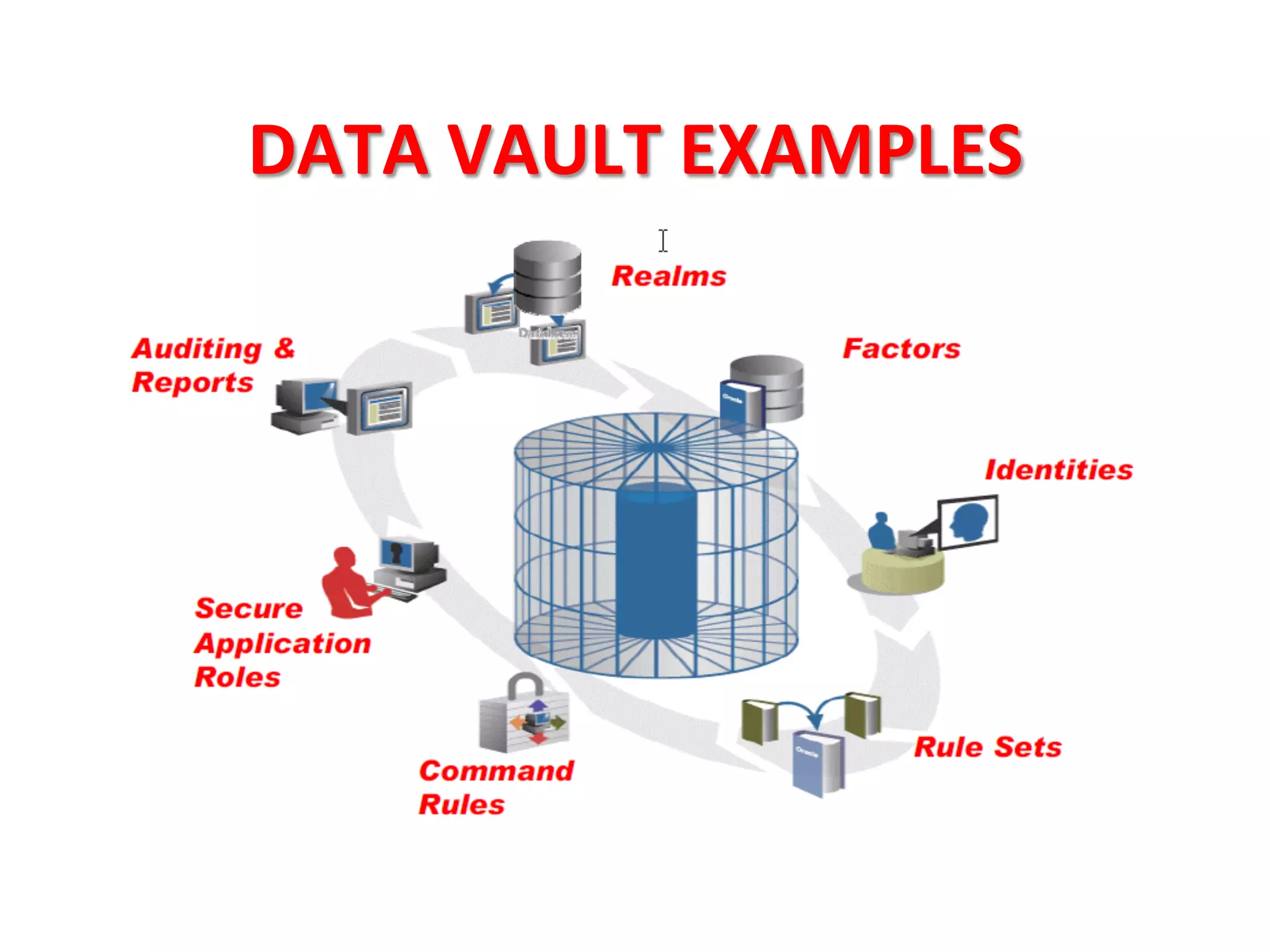
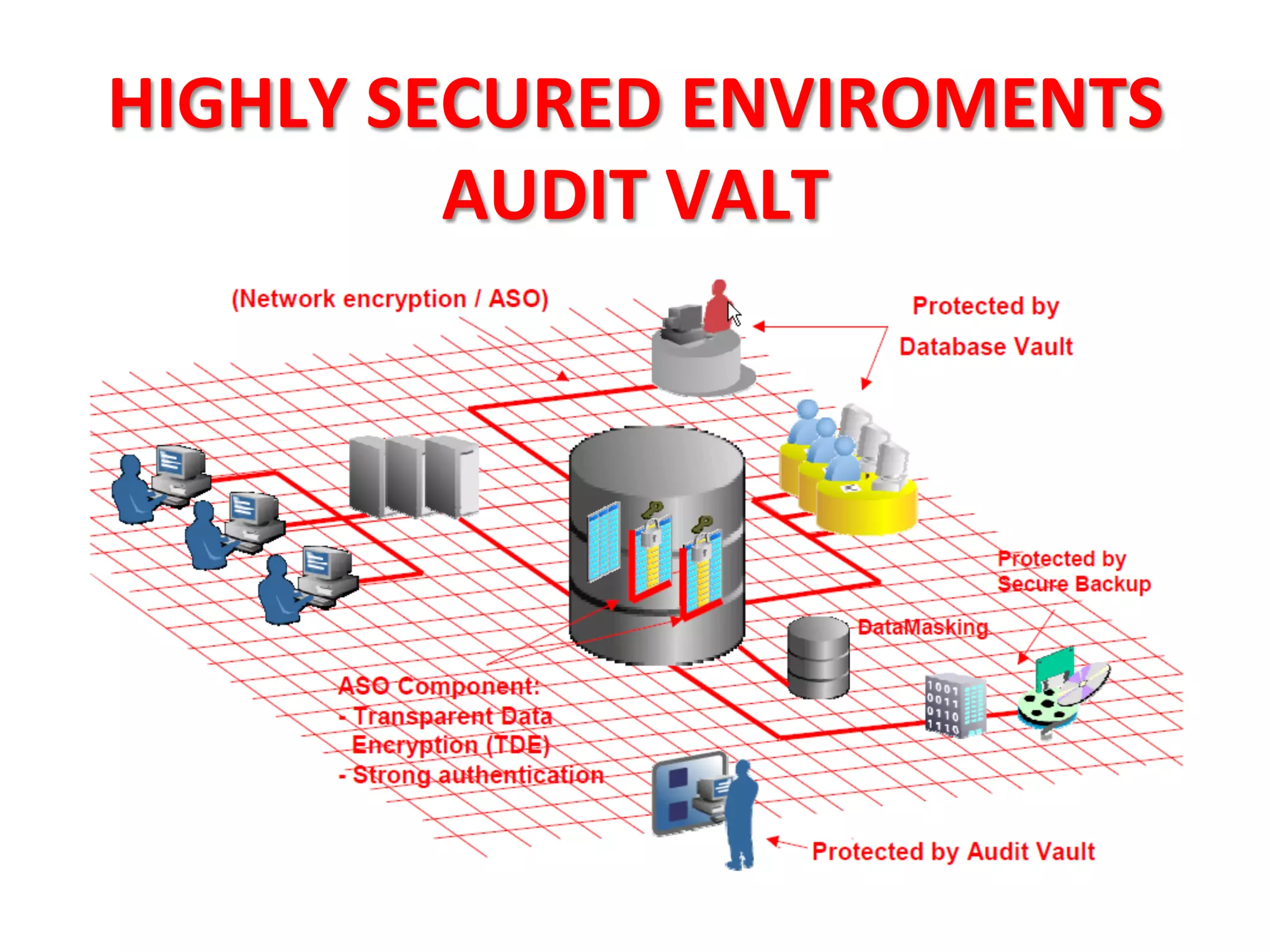
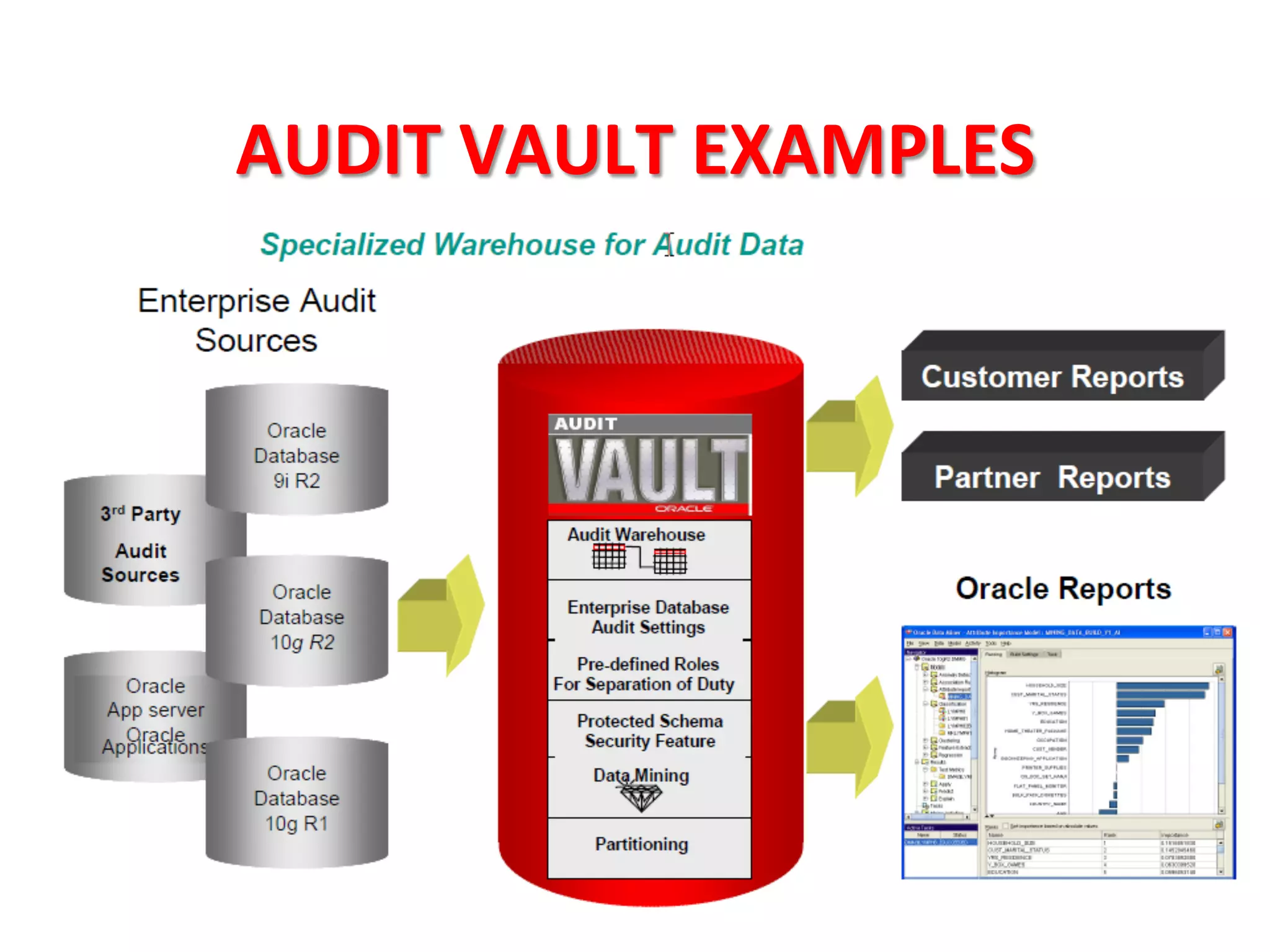
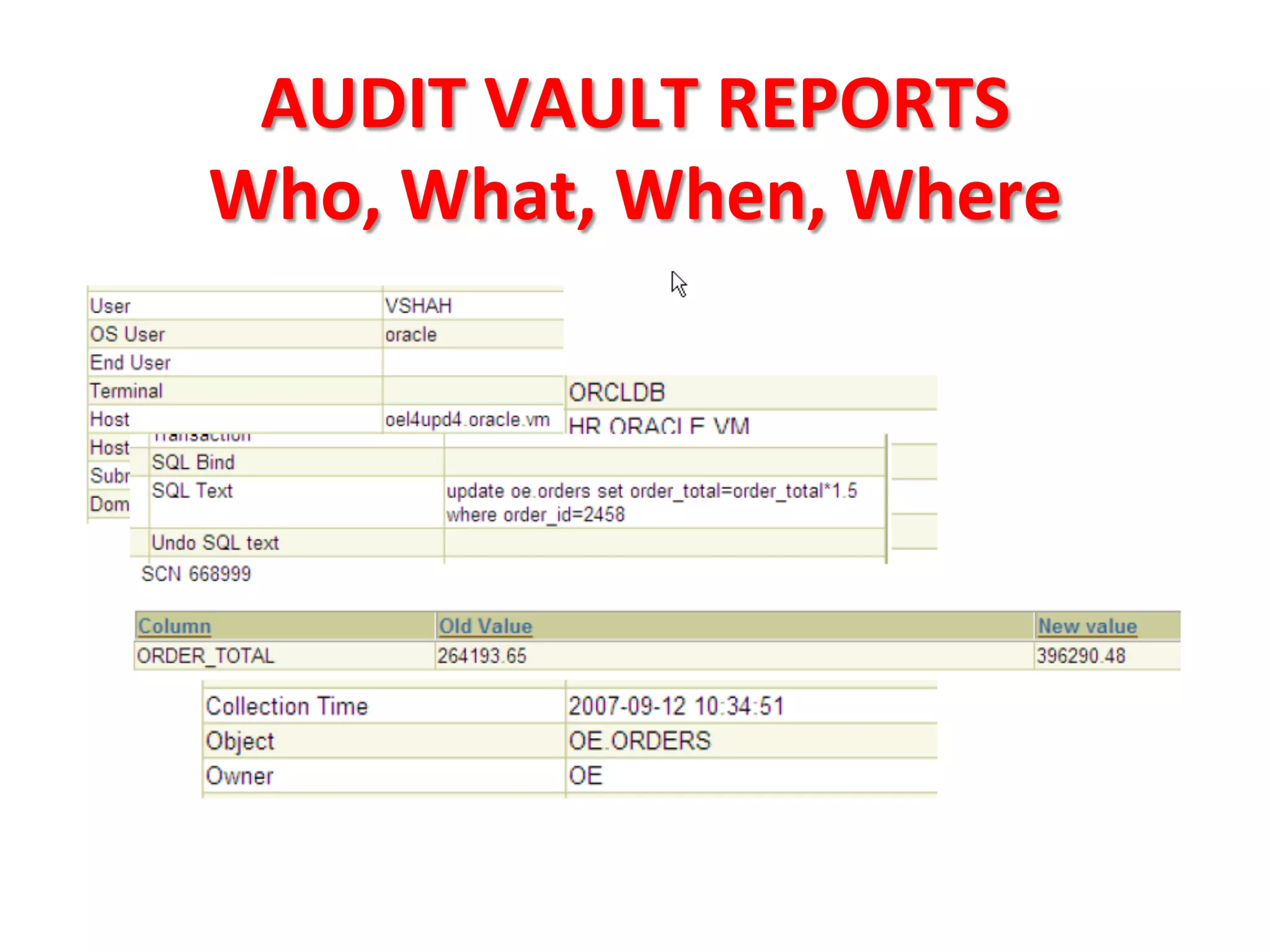
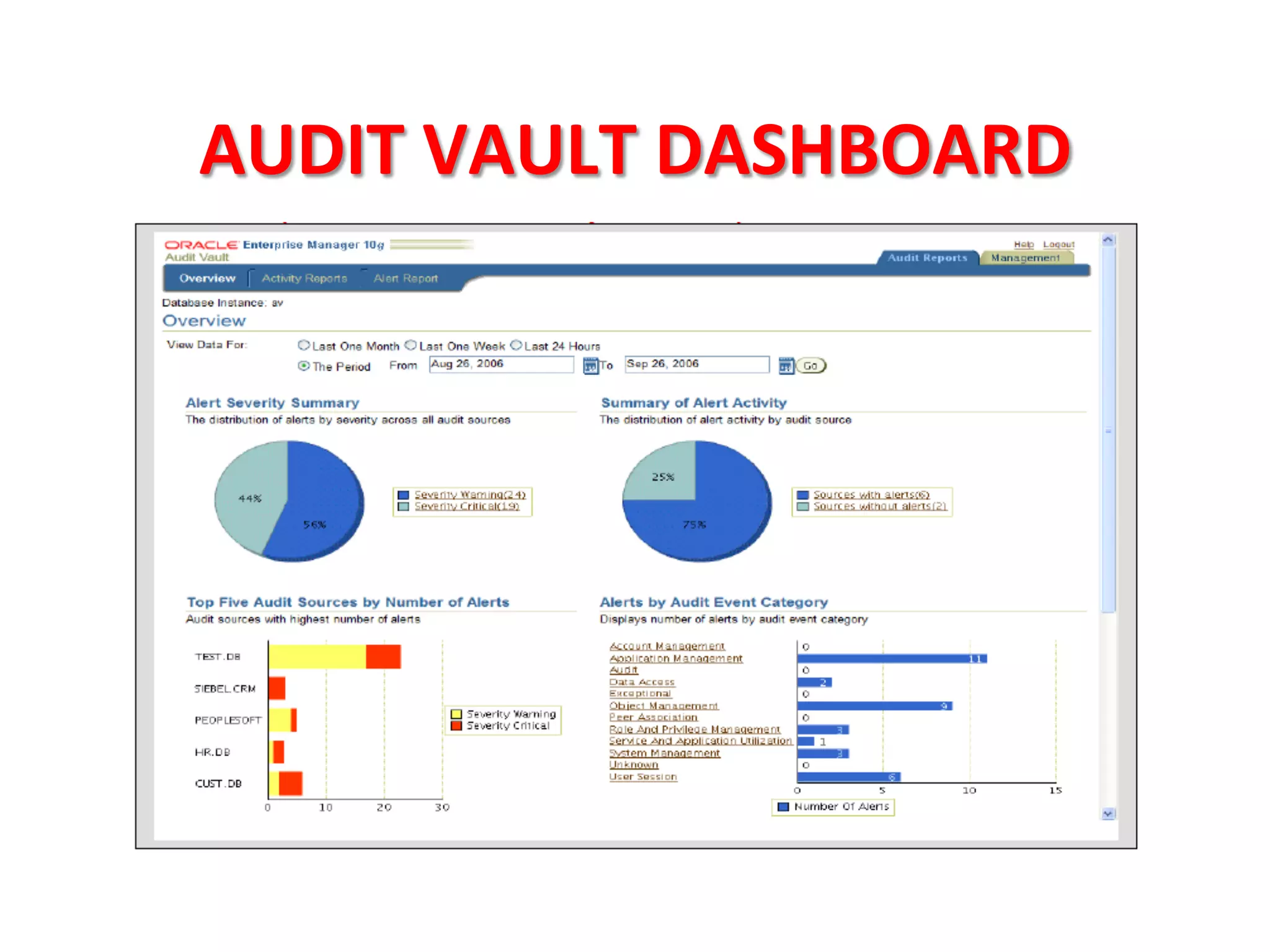
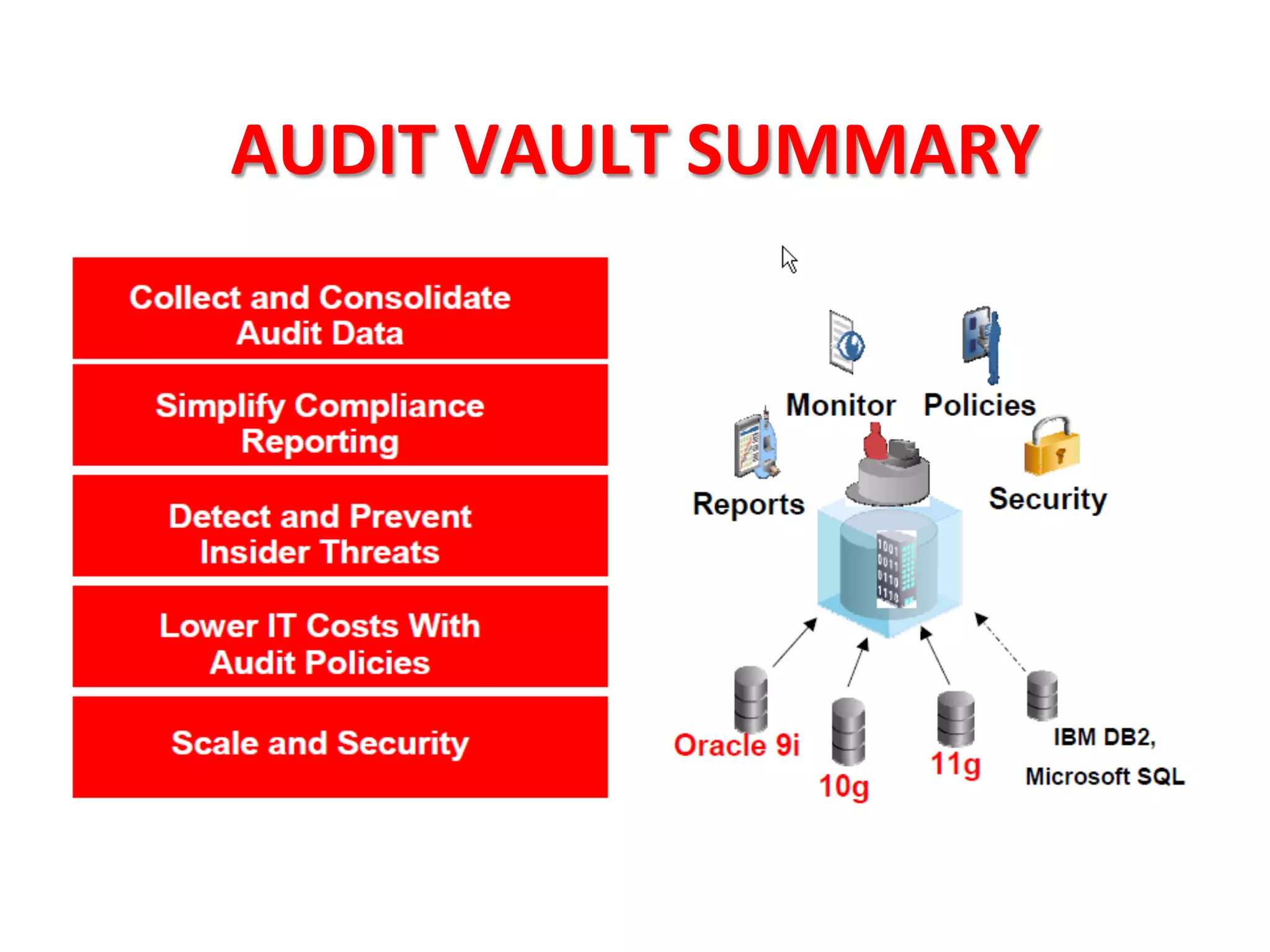
This document provides tips for improving Oracle database security. It recommends granting privileges only as needed, restricting administrative access, using roles to manage privileges, encrypting passwords, and limiting access to sensitive data and metadata. Proper user and privilege management can help enhance security. Regular backups and testing changes are also advised to ensure data integrity and recoverability in the event of issues.