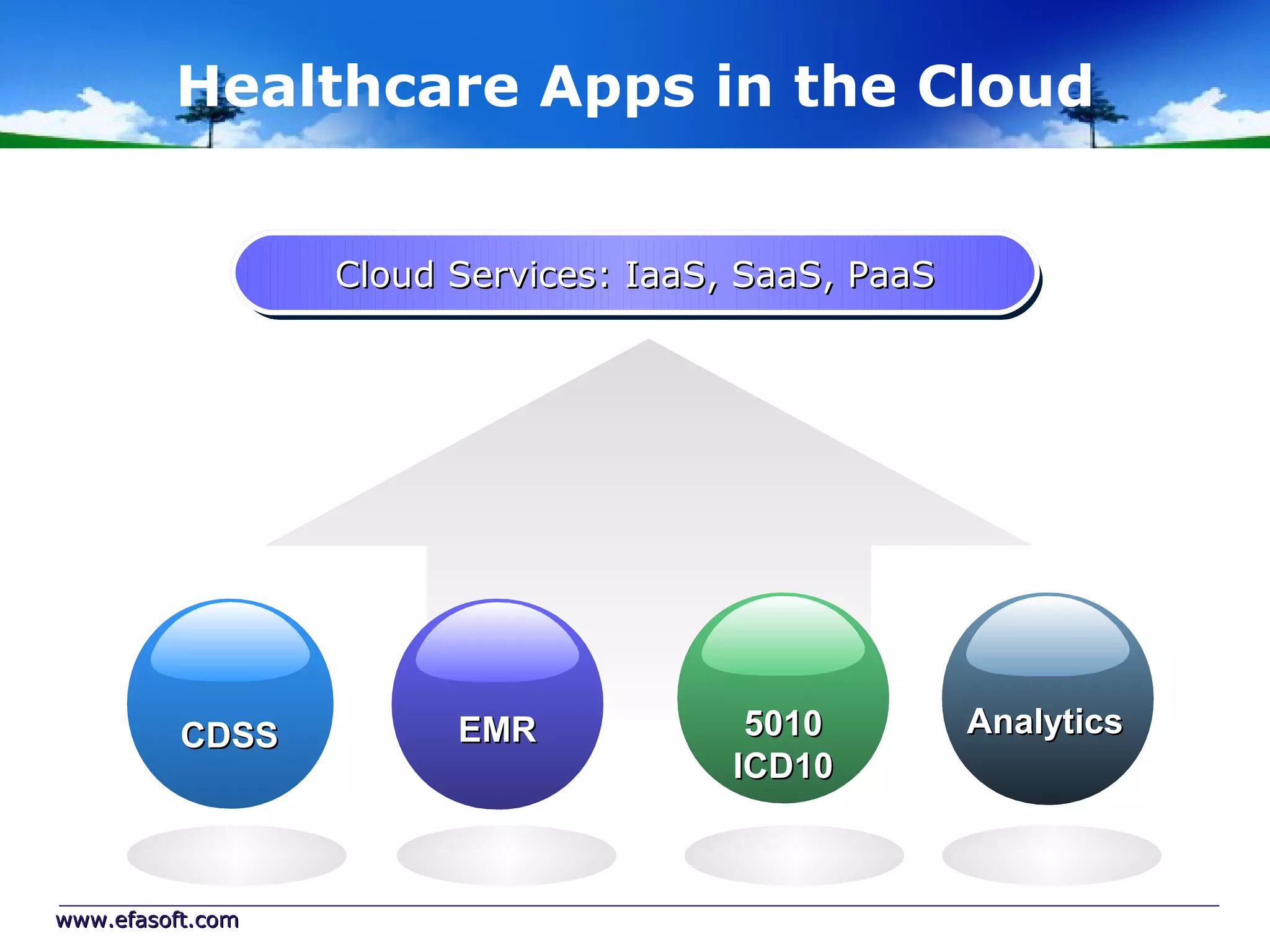
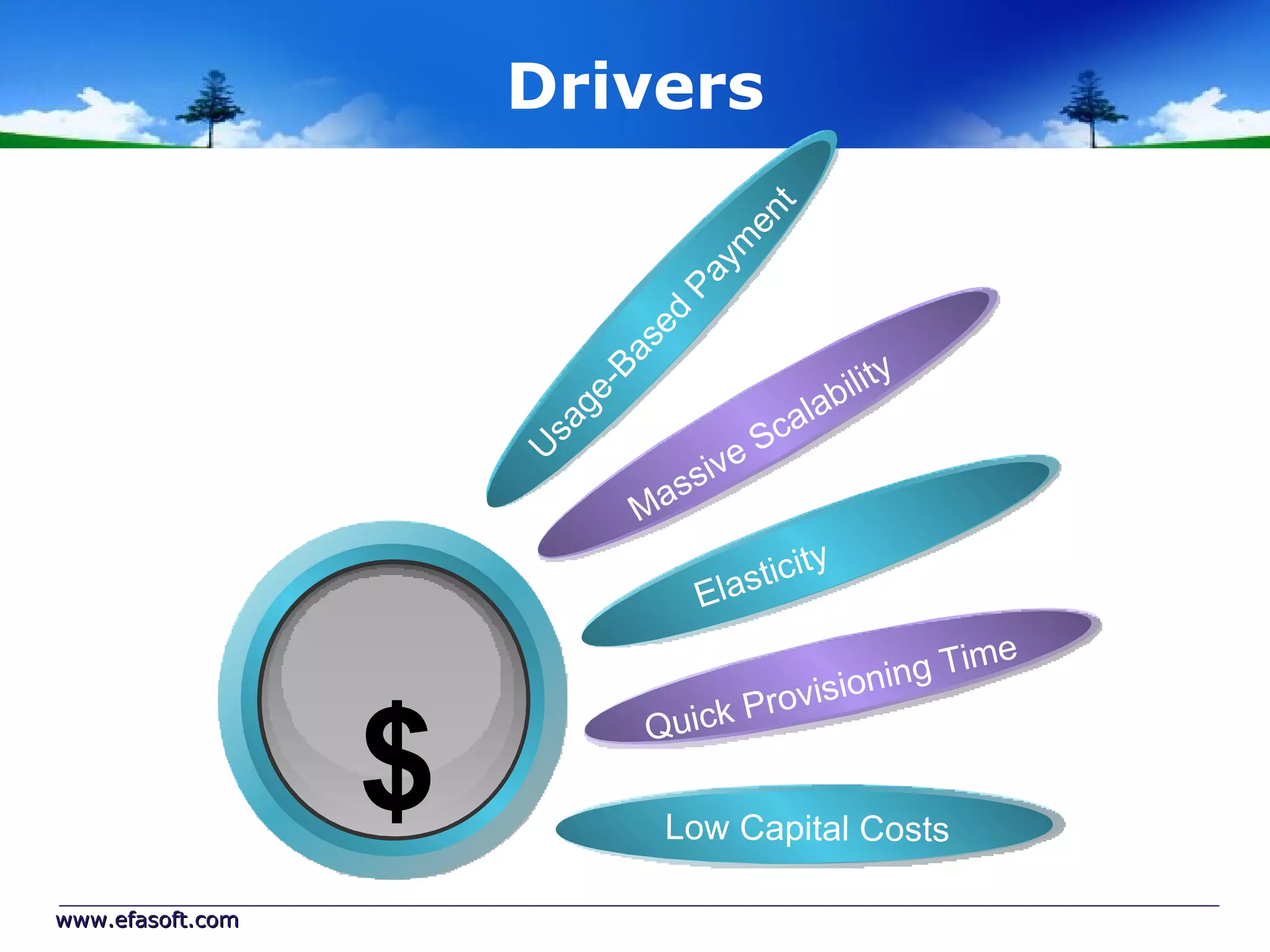
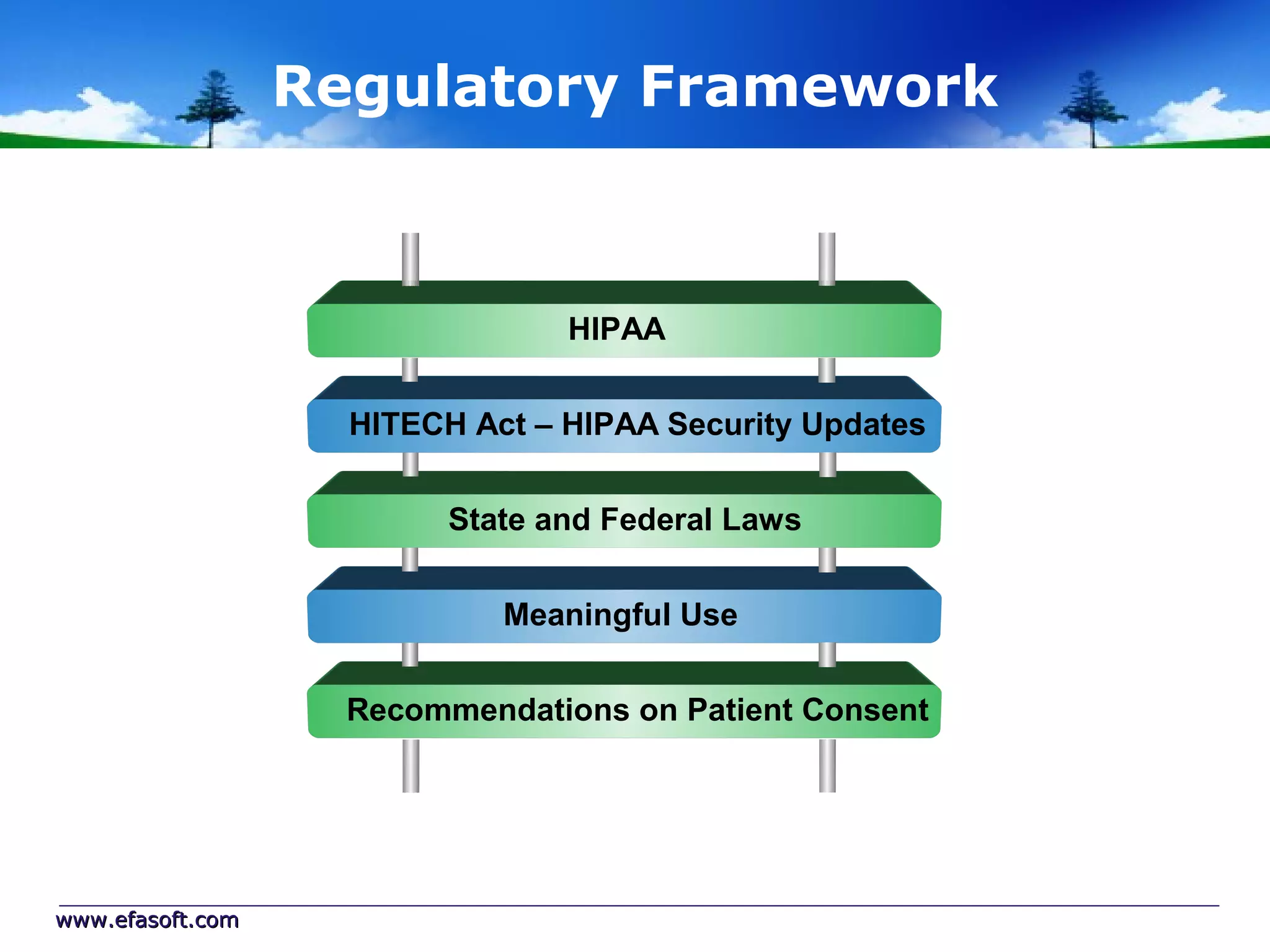
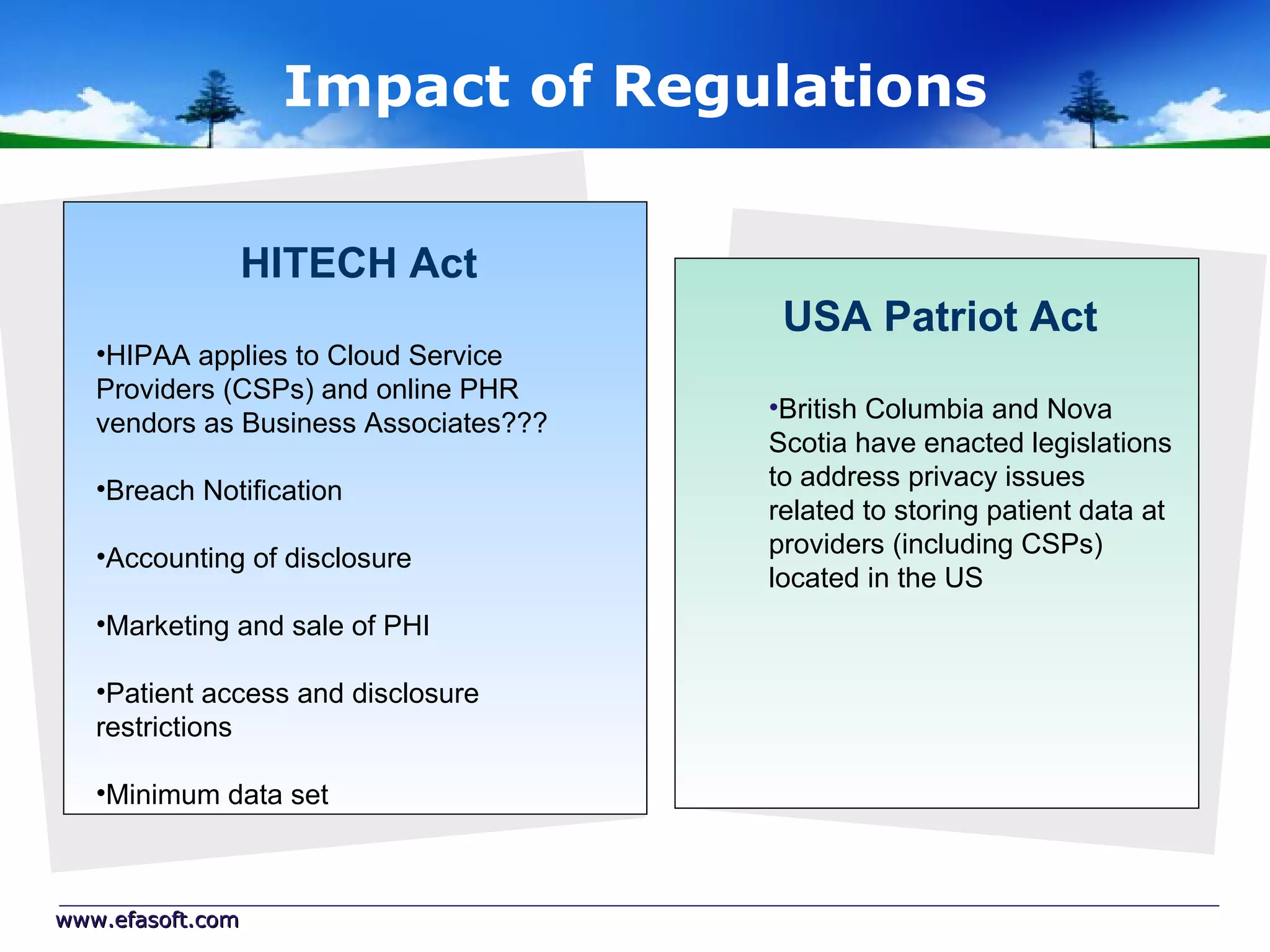
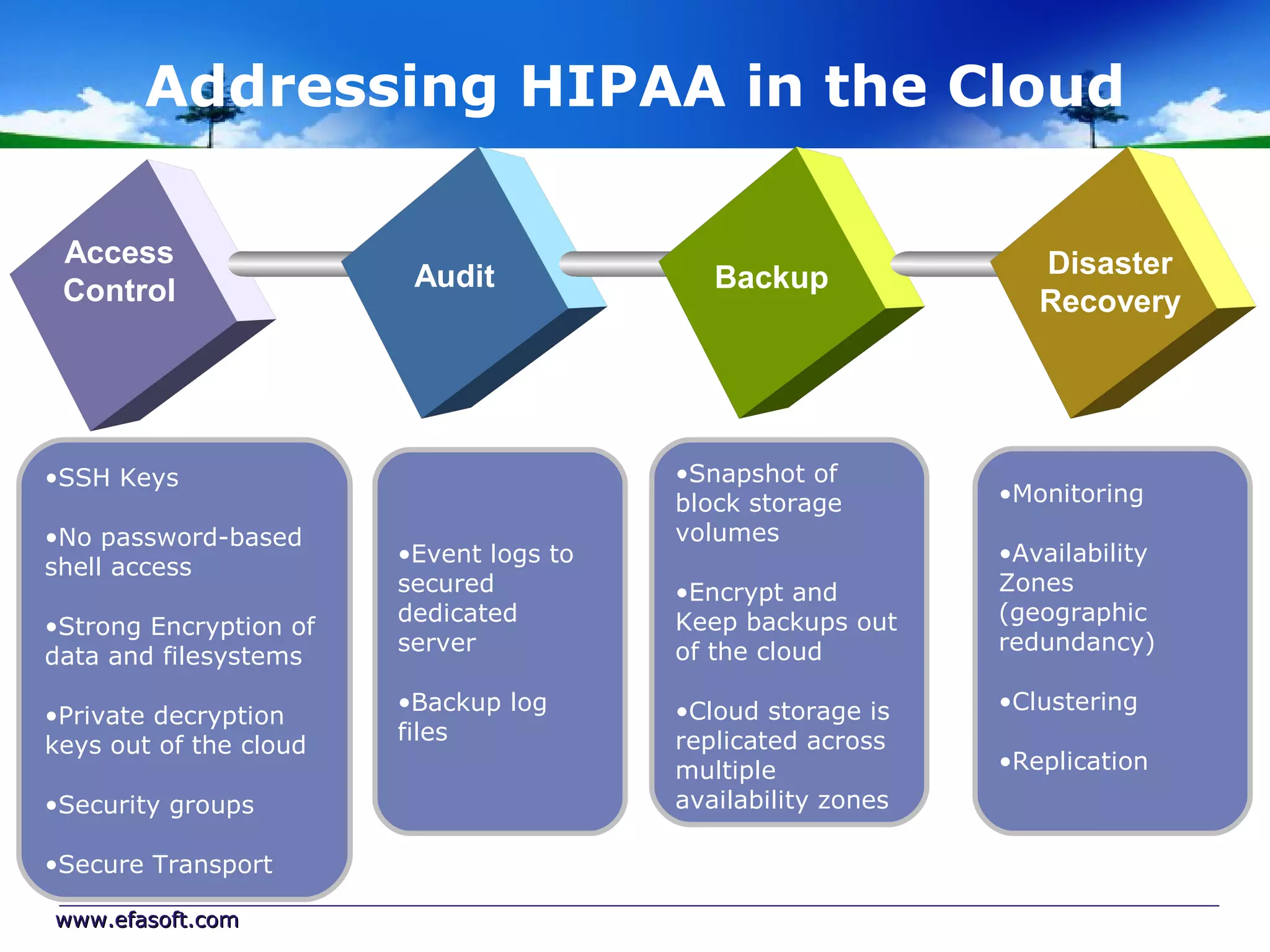
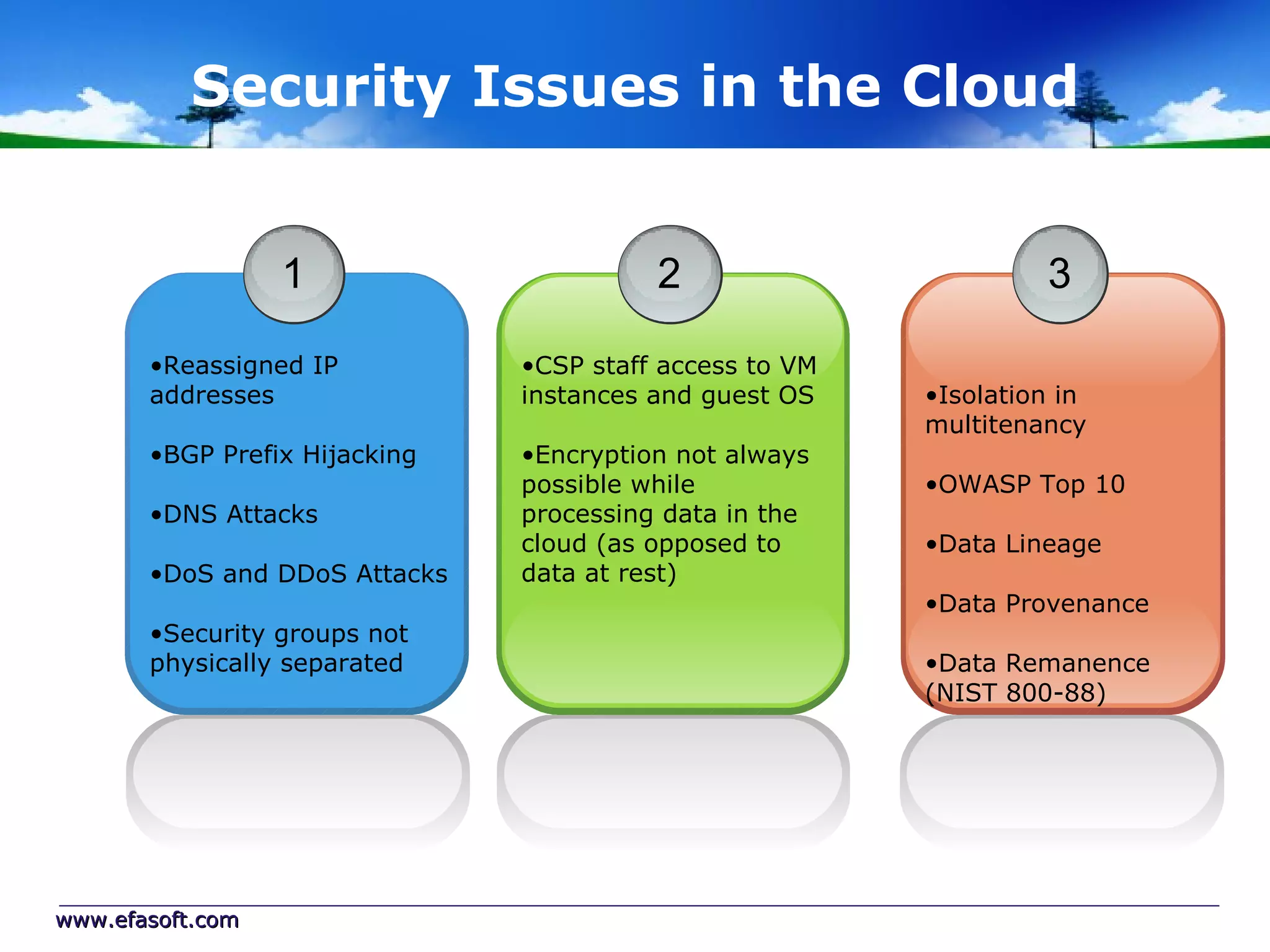
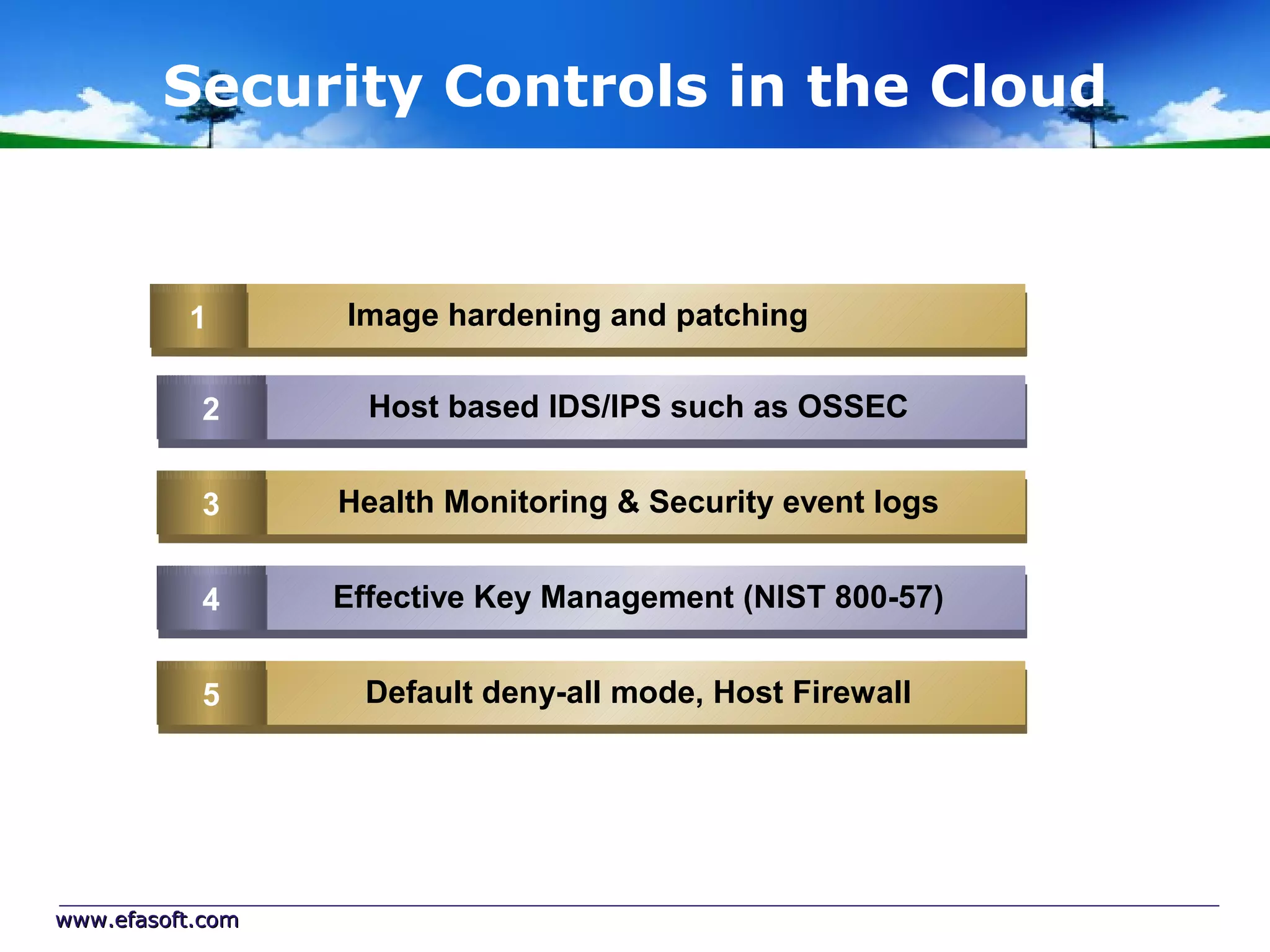
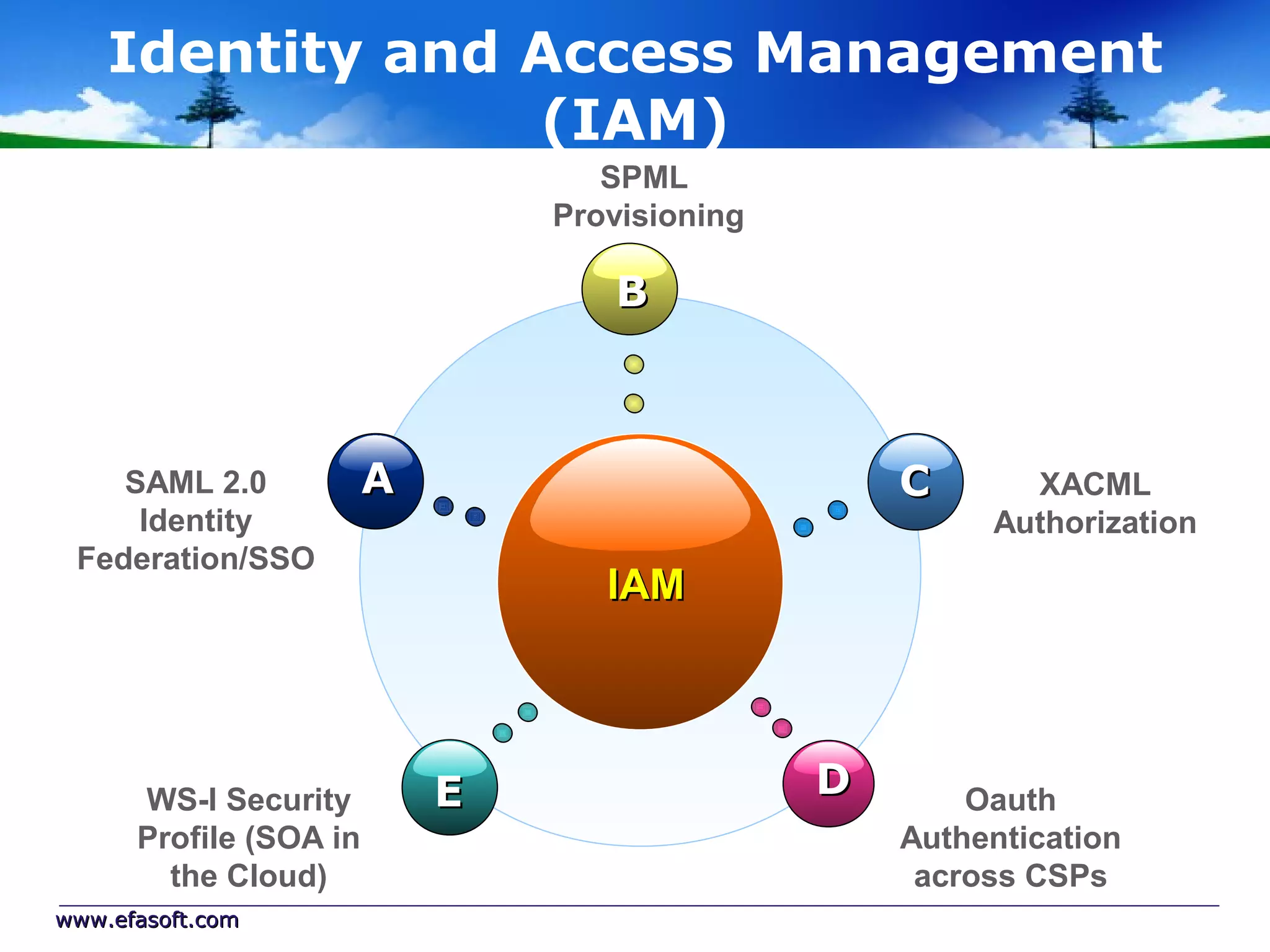
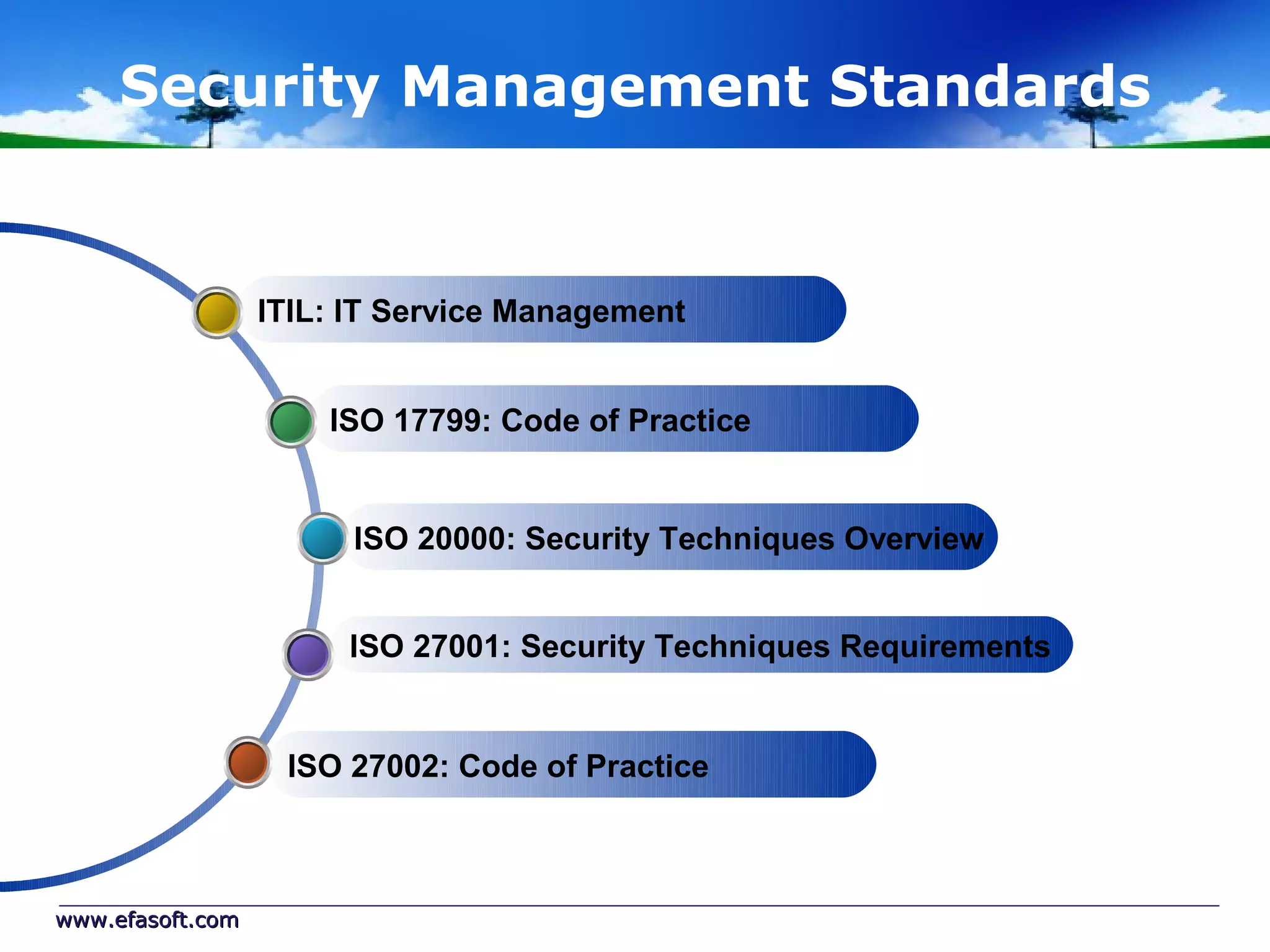
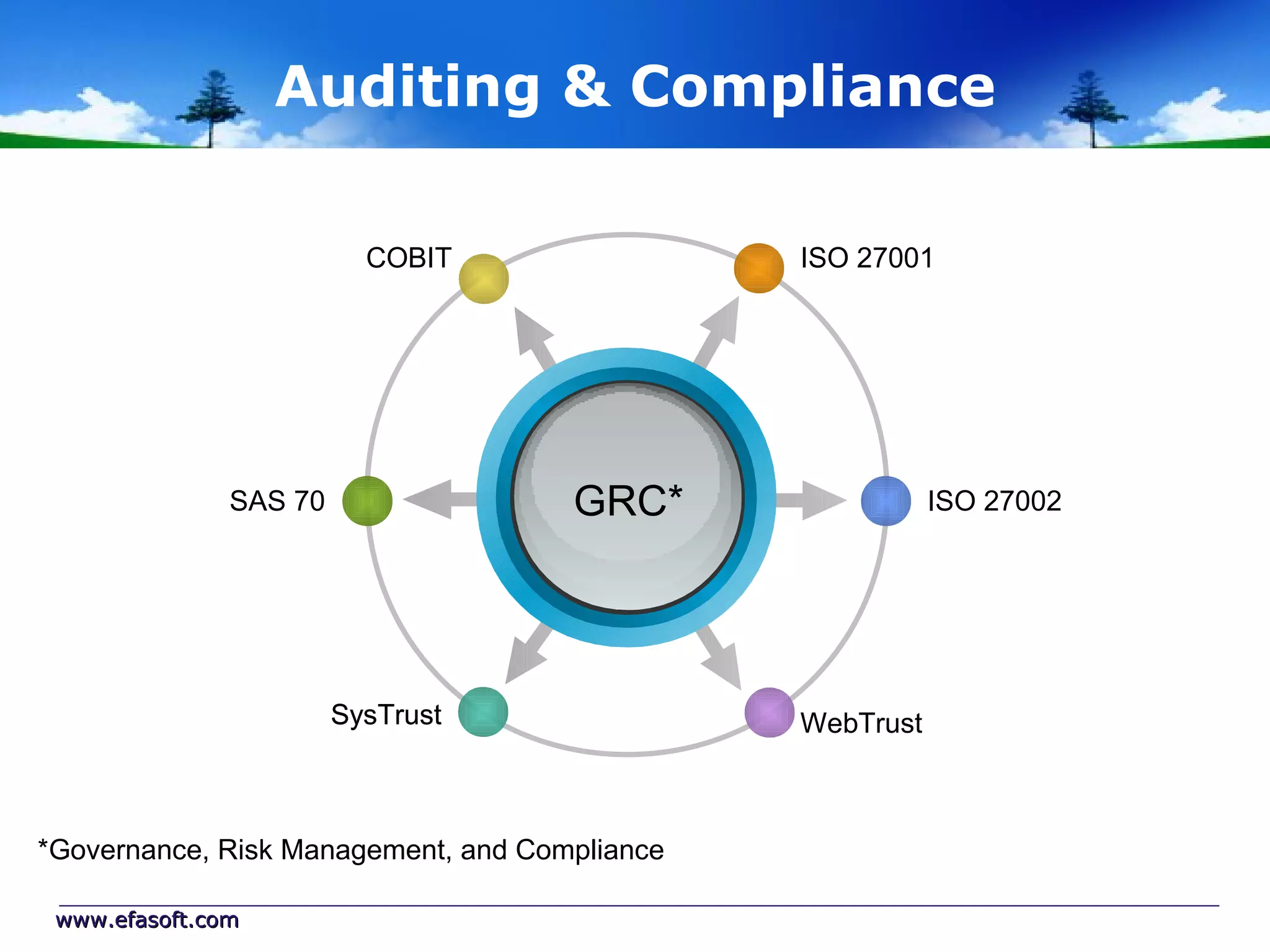
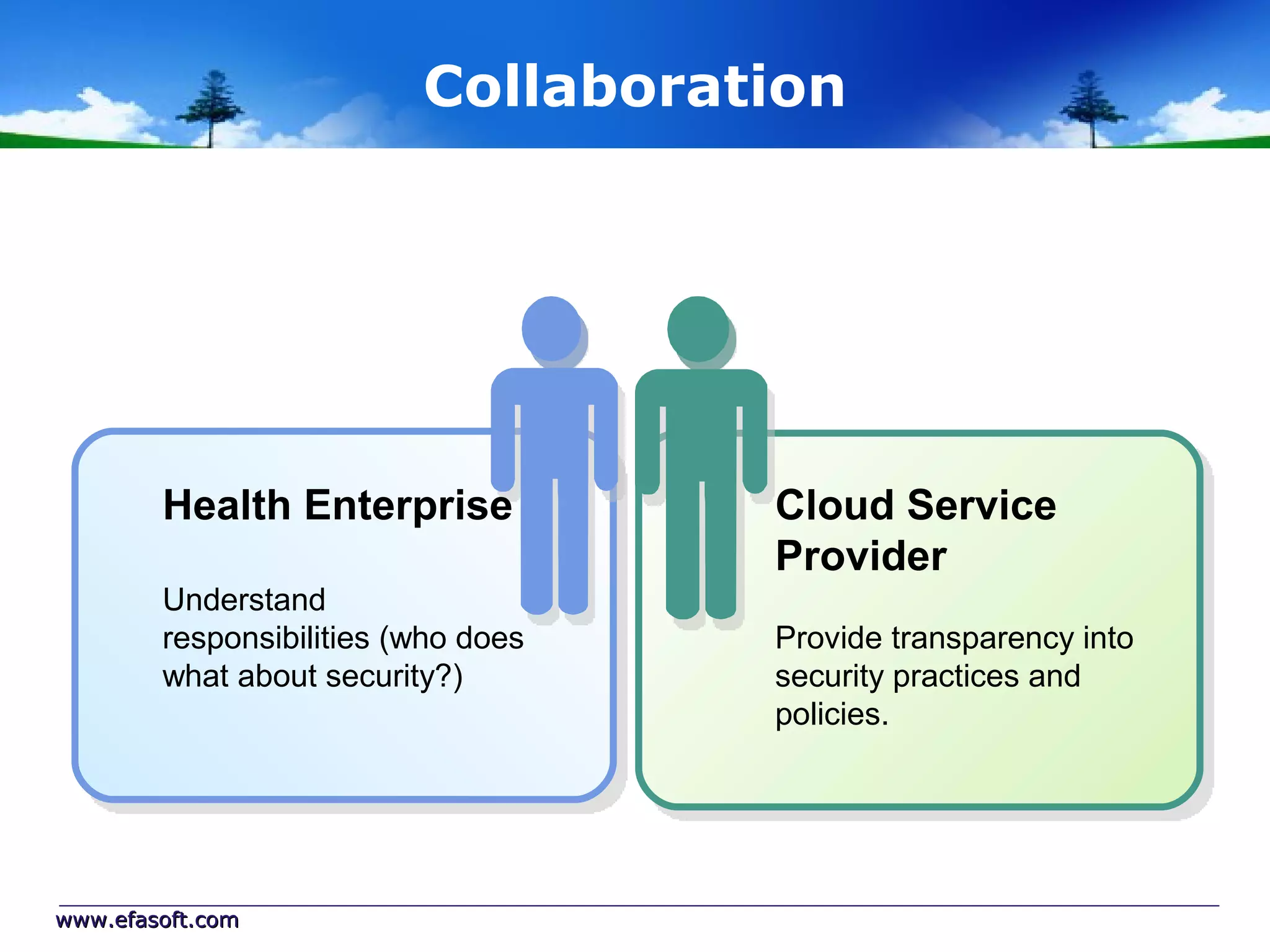
Secure Cloud Computing for the Health Enterprise discusses securing healthcare applications in the cloud. It addresses the regulatory framework including HIPAA, security practices like access control and encryption, and security management standards. Auditing and compliance are also covered to ensure cloud providers meet regulatory requirements for healthcare data. Overall it provides guidance to healthcare enterprises on collaborating with cloud providers to securely deploy applications while protecting sensitive patient information.