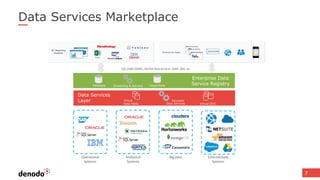
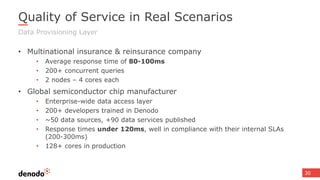
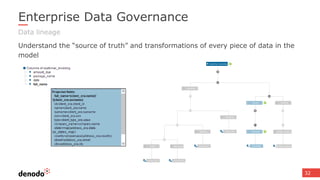
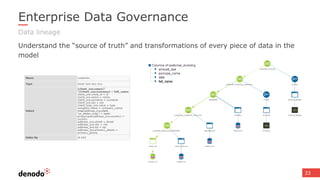
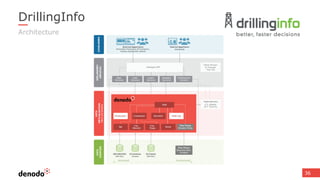
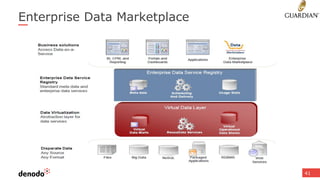
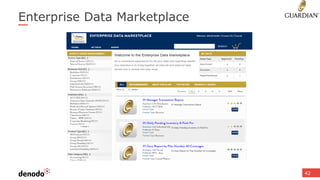
The document discusses the concept of data services marketplaces, highlighting their role in providing access to data for users and developers. It covers the challenges associated with data services, such as security, privacy, performance, and data governance, as well as outlining various technologies for implementing data services. Additionally, it provides customer success stories demonstrating the benefits of data services in real-world applications.