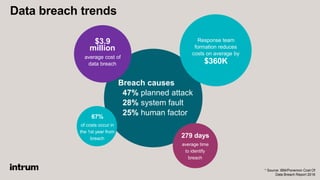
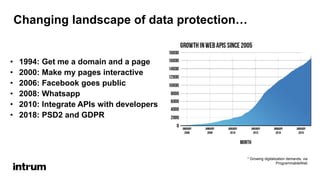
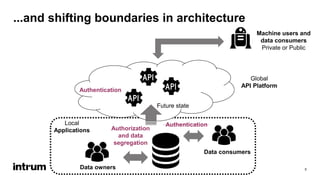
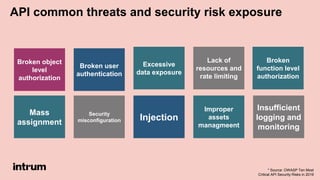
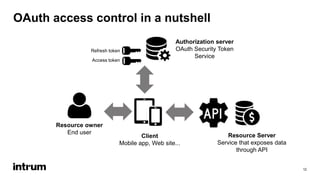
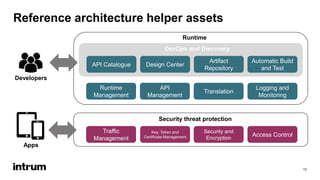
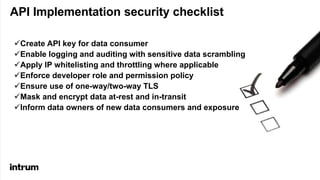
An API security expert presented on common API security risks and best practices. The document discussed an API bug at Google that may have exposed over 500,000 user profiles since 2015. It then covered common causes of data breaches and costs associated with them. The rest of the document outlined strategies for securing APIs, including using standards like OAuth for authentication and authorization, and implementing controls like access logging and monitoring, and input validation. It stressed the importance of limiting data exposure and enforcing access policies and permissions.