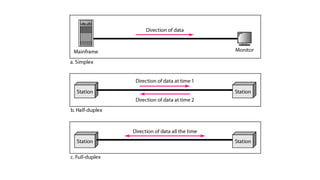
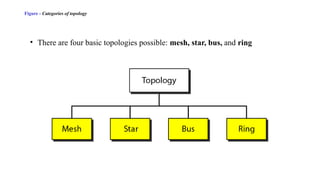
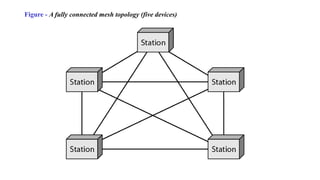
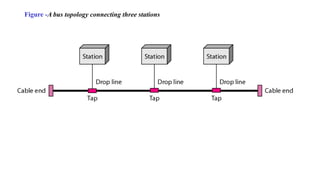
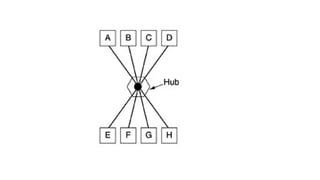
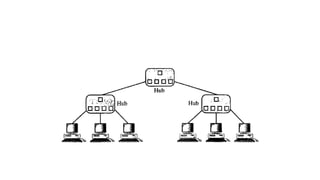
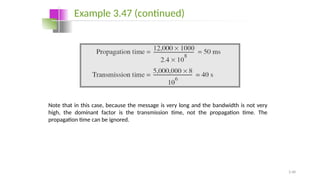
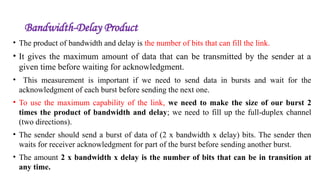
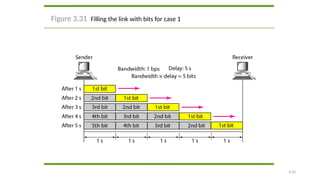
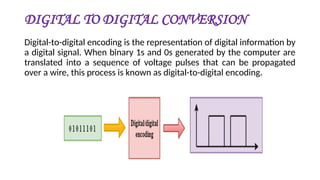
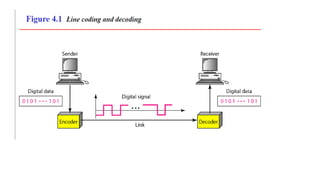
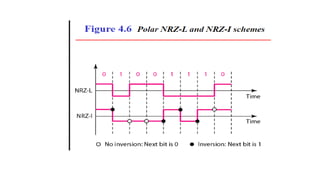
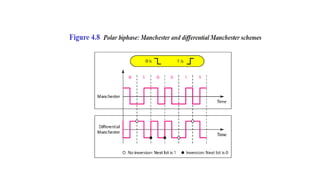
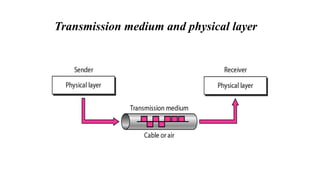
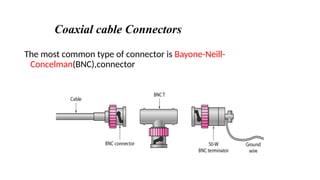
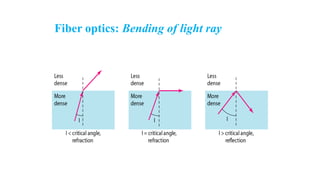
The document discusses physical layer data flow and various modes of communication between devices, including simplex, half-duplex, and full-duplex. It describes different topologies (mesh, star, bus, ring) and their advantages and disadvantages, as well as concepts like repeaters, hubs, bandwidth, throughput, latency, and the importance of the bandwidth-delay product in networking. Key aspects of performance, including the limits of transmission quality and the significance of network design in data communications, are also highlighted.