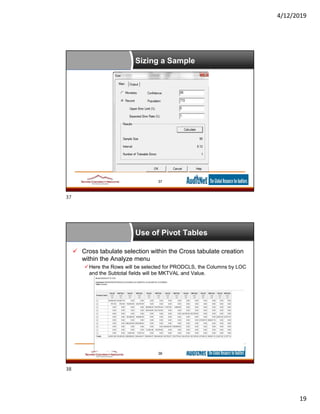
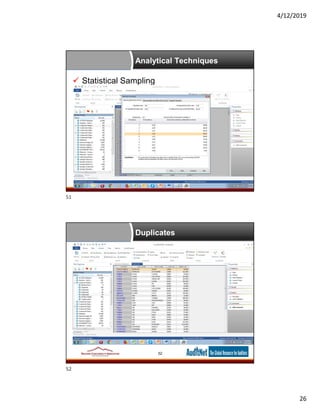
This document provides an overview of data analytics tools for internal auditors, highlighting various software like Excel, ACL, IDEA, and SAS. It details analytical techniques, data acquisition methods, and the significance of statistical analyses in auditing. Additionally, it introduces auditnet® as a resource for auditors, providing templates, training, and community networks.