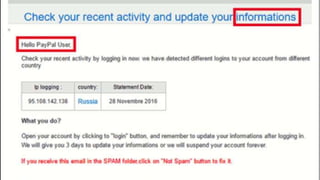
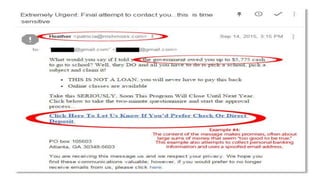
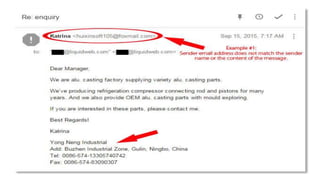
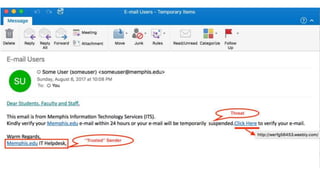
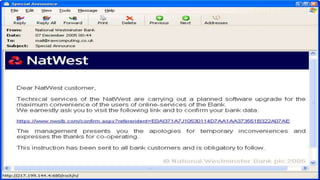
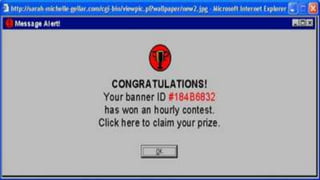
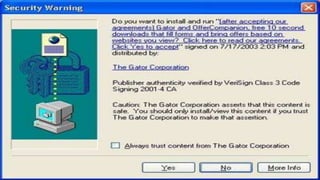
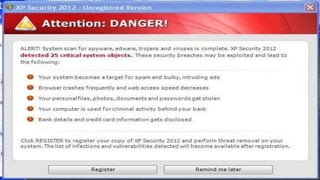
This document discusses various internet security threats such as email spam, email spoofing, phishing, pharming, spyware, computer worms, Trojan horses, computer viruses, and hackers. It provides definitions and descriptions of each threat, explaining how they endanger internet users by stealing personal and financial information or taking control of computers without authorization. The document aims to educate people about these dangers in the internet in order to empower them with knowledge on technology security issues.