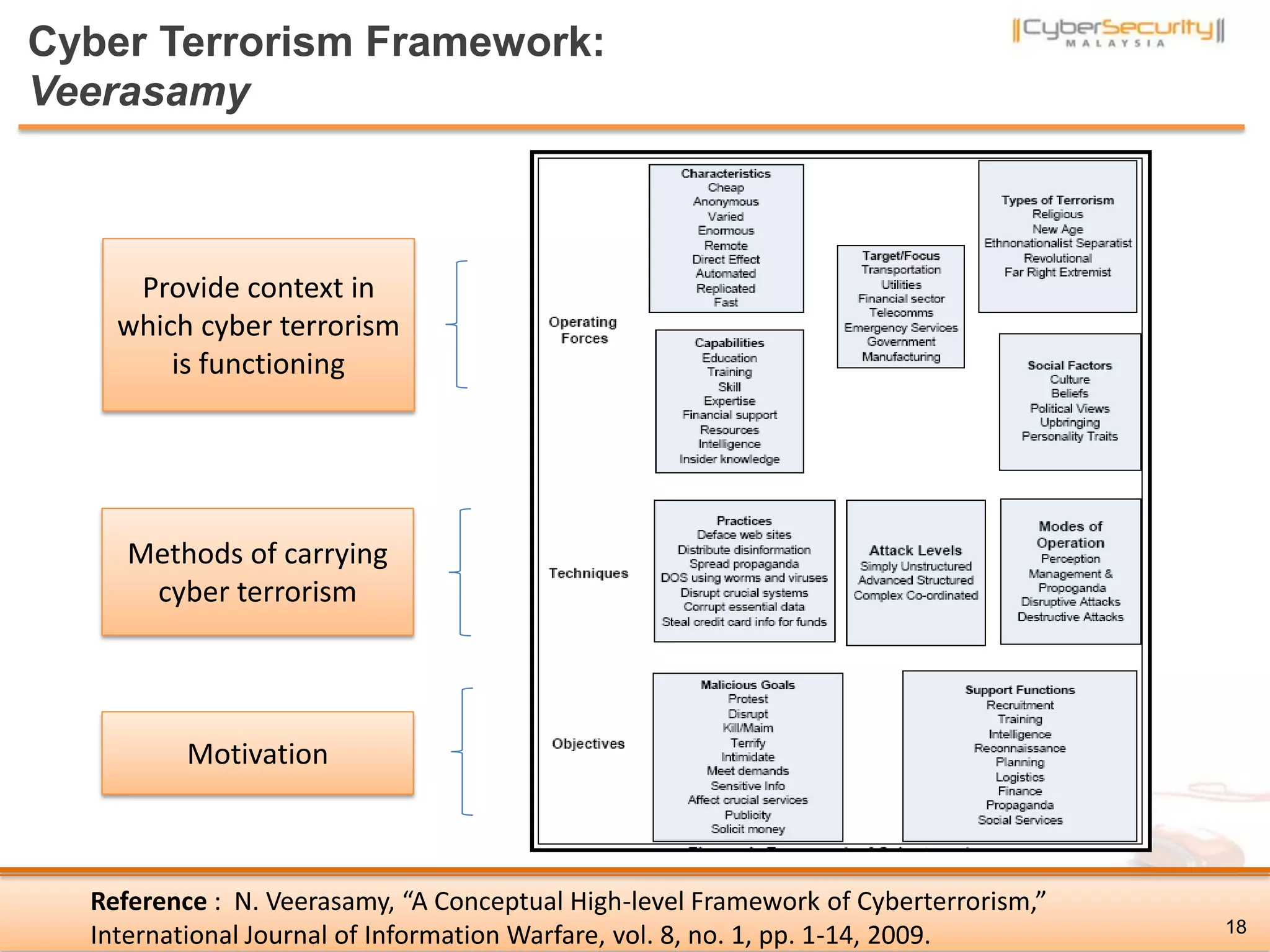
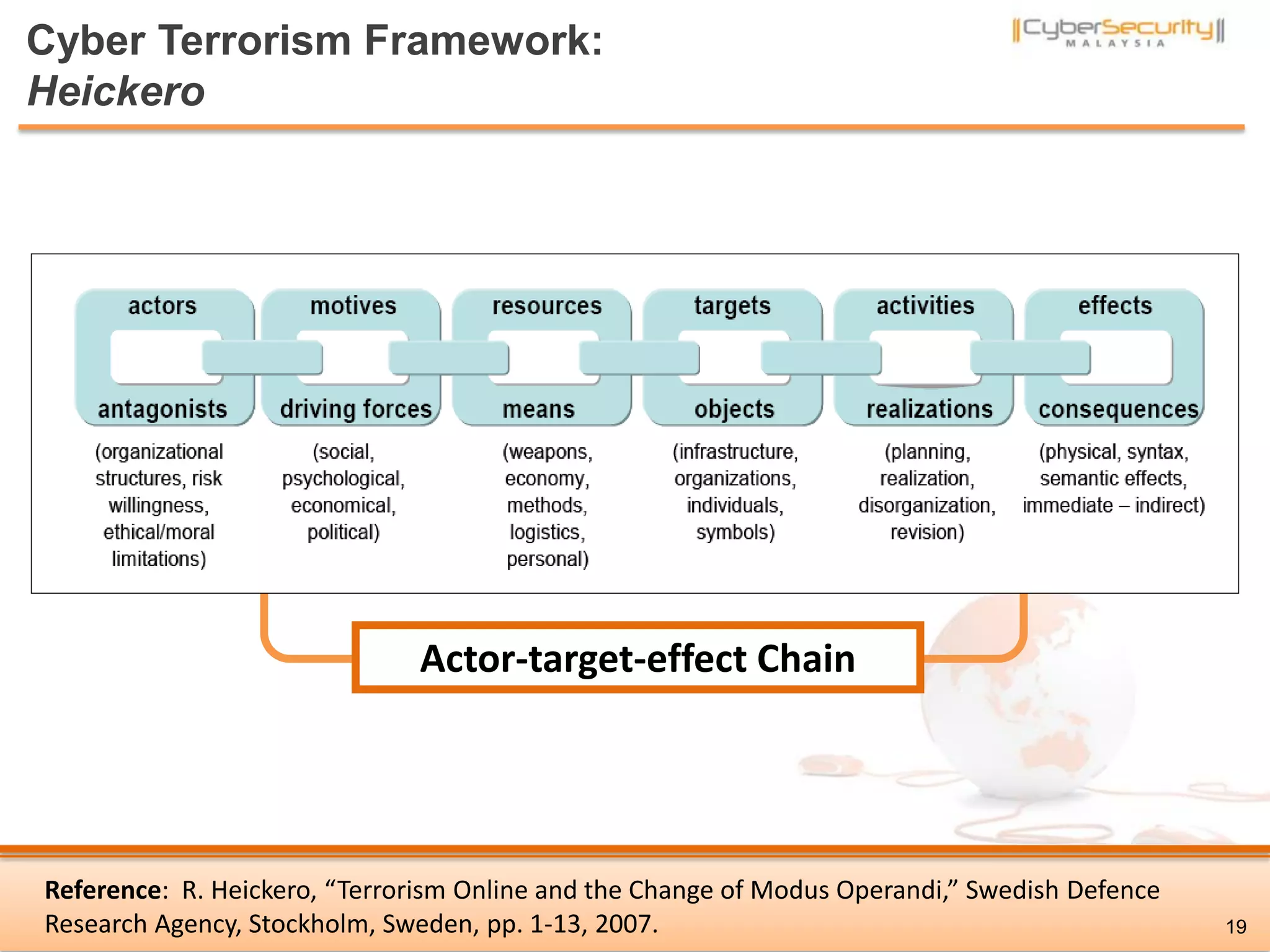
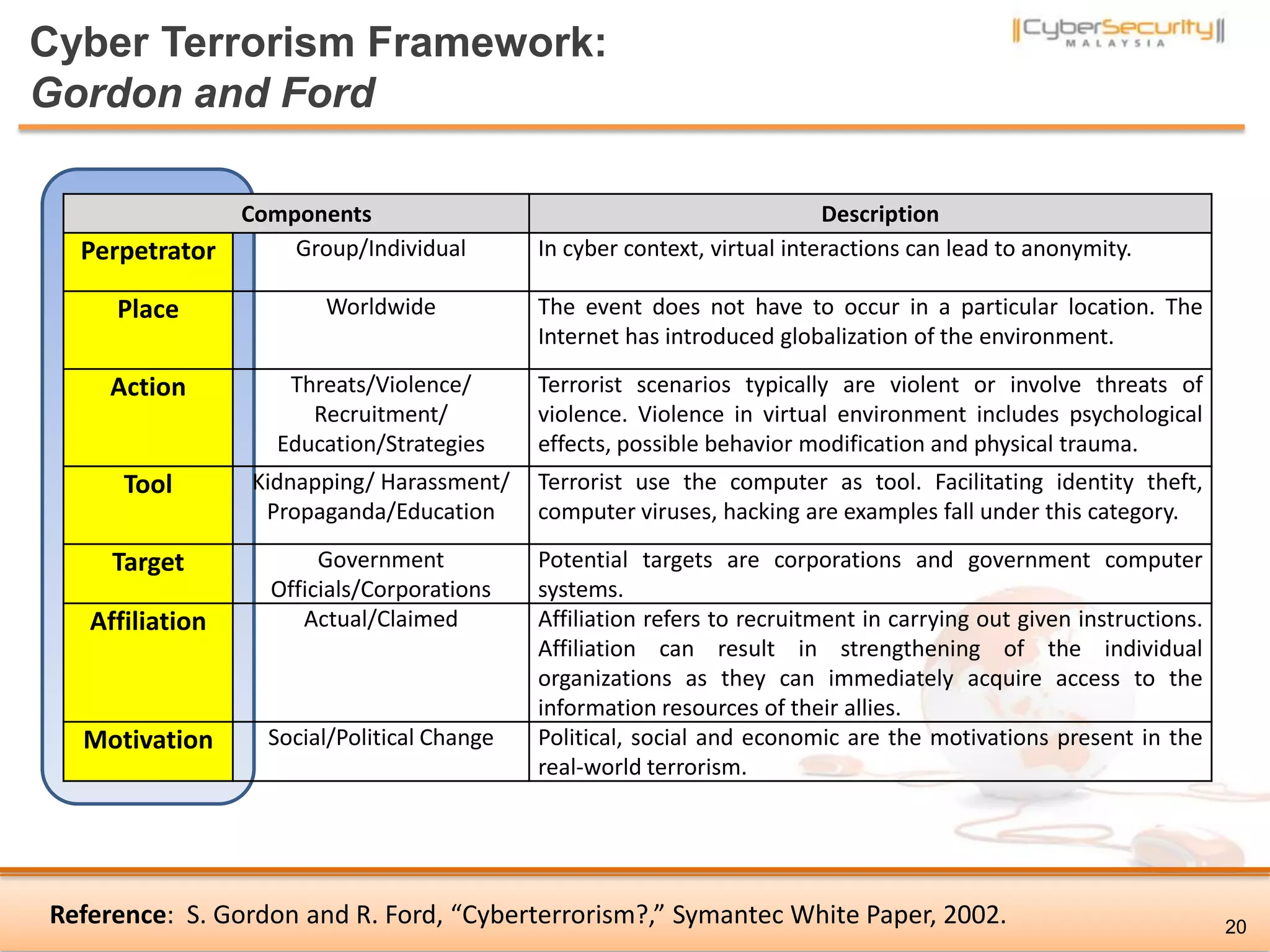
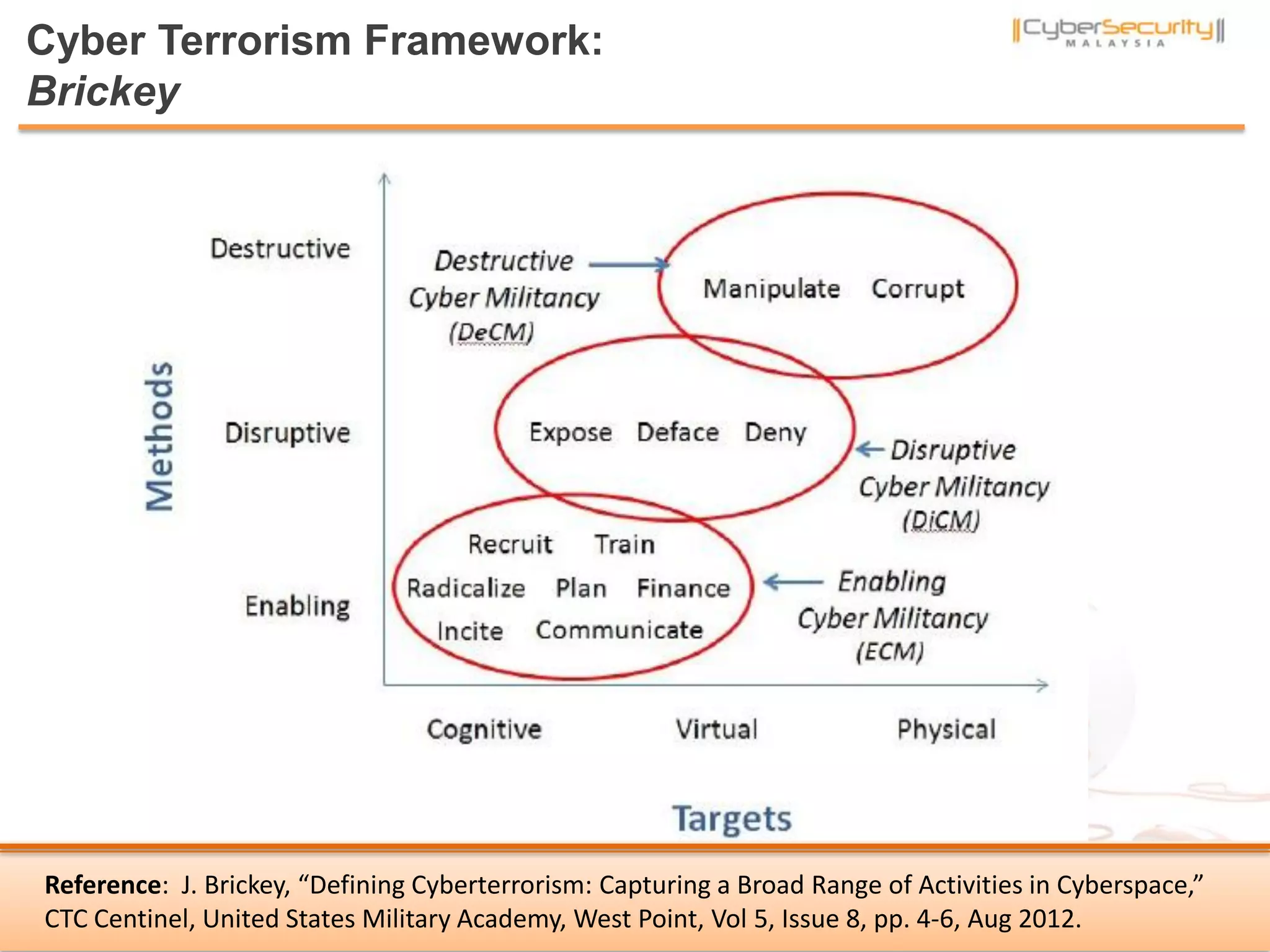
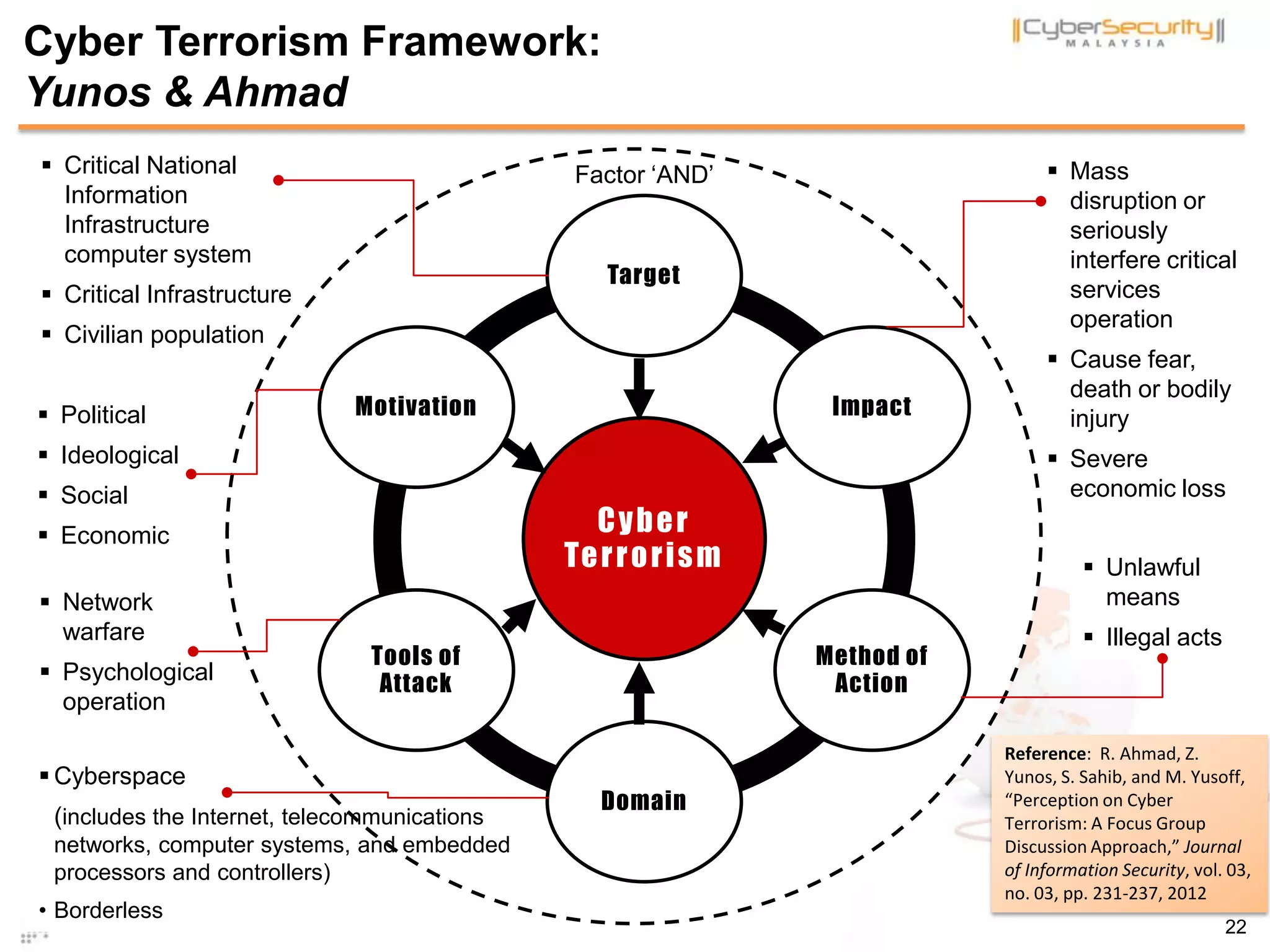
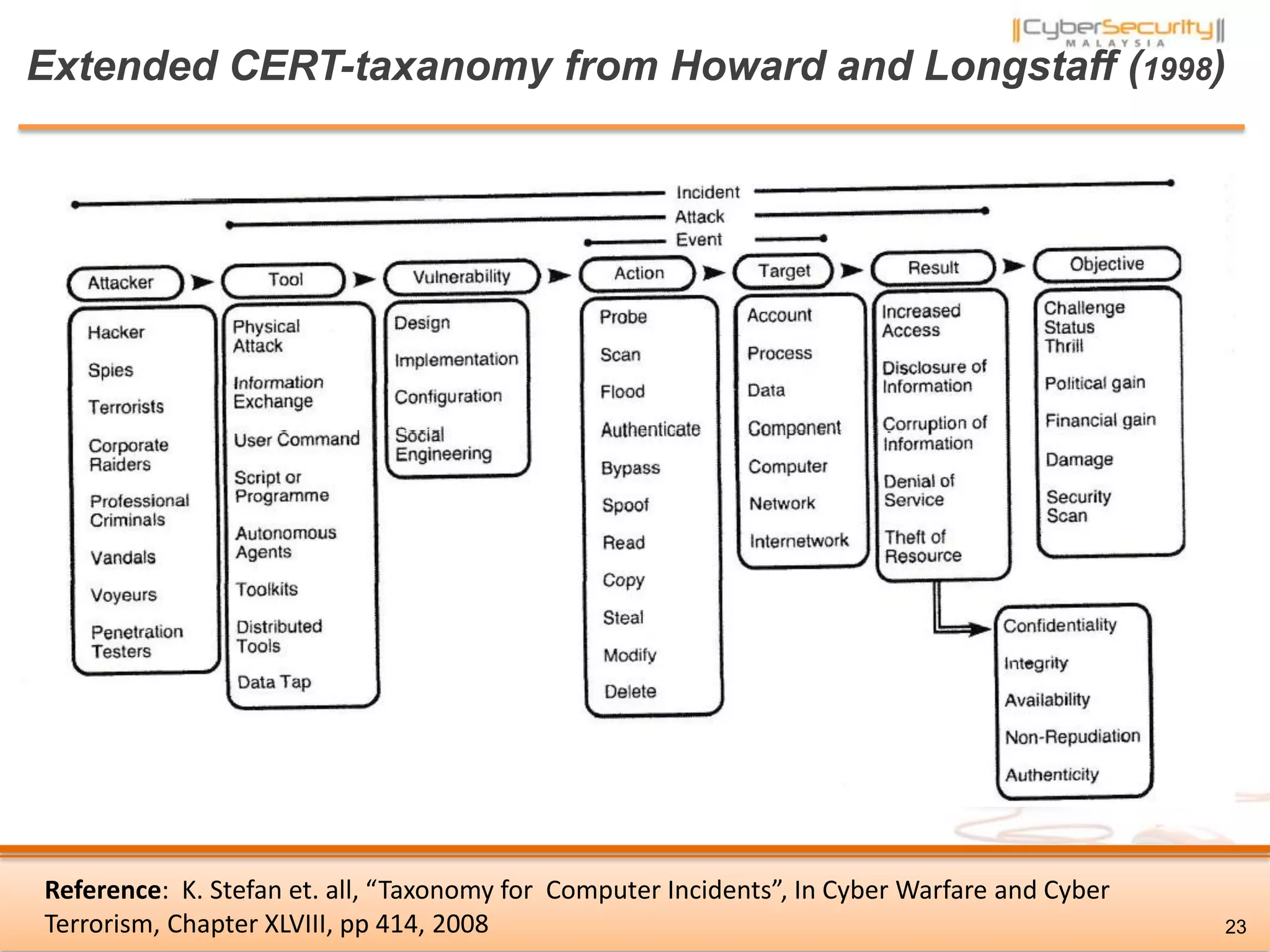
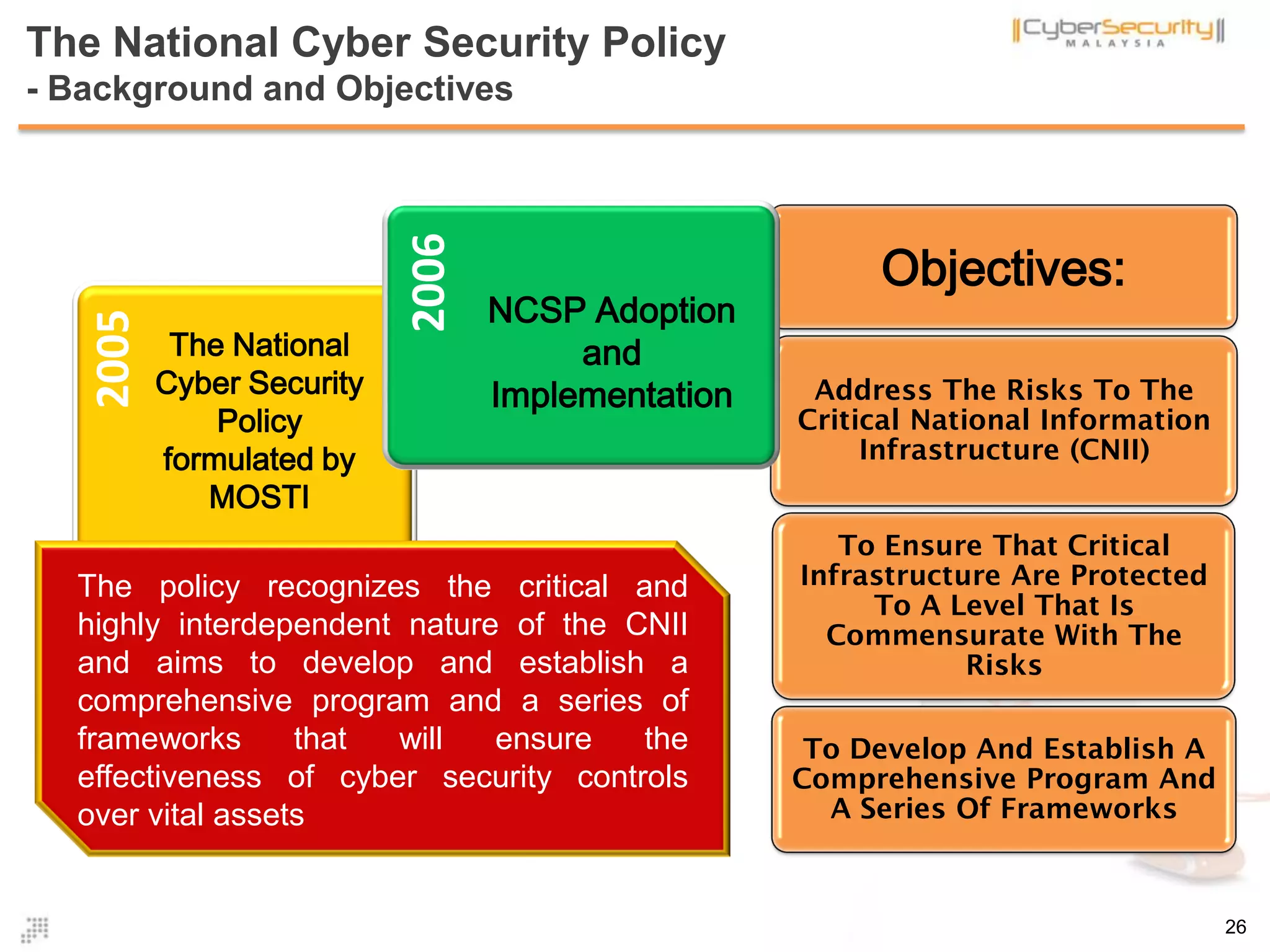
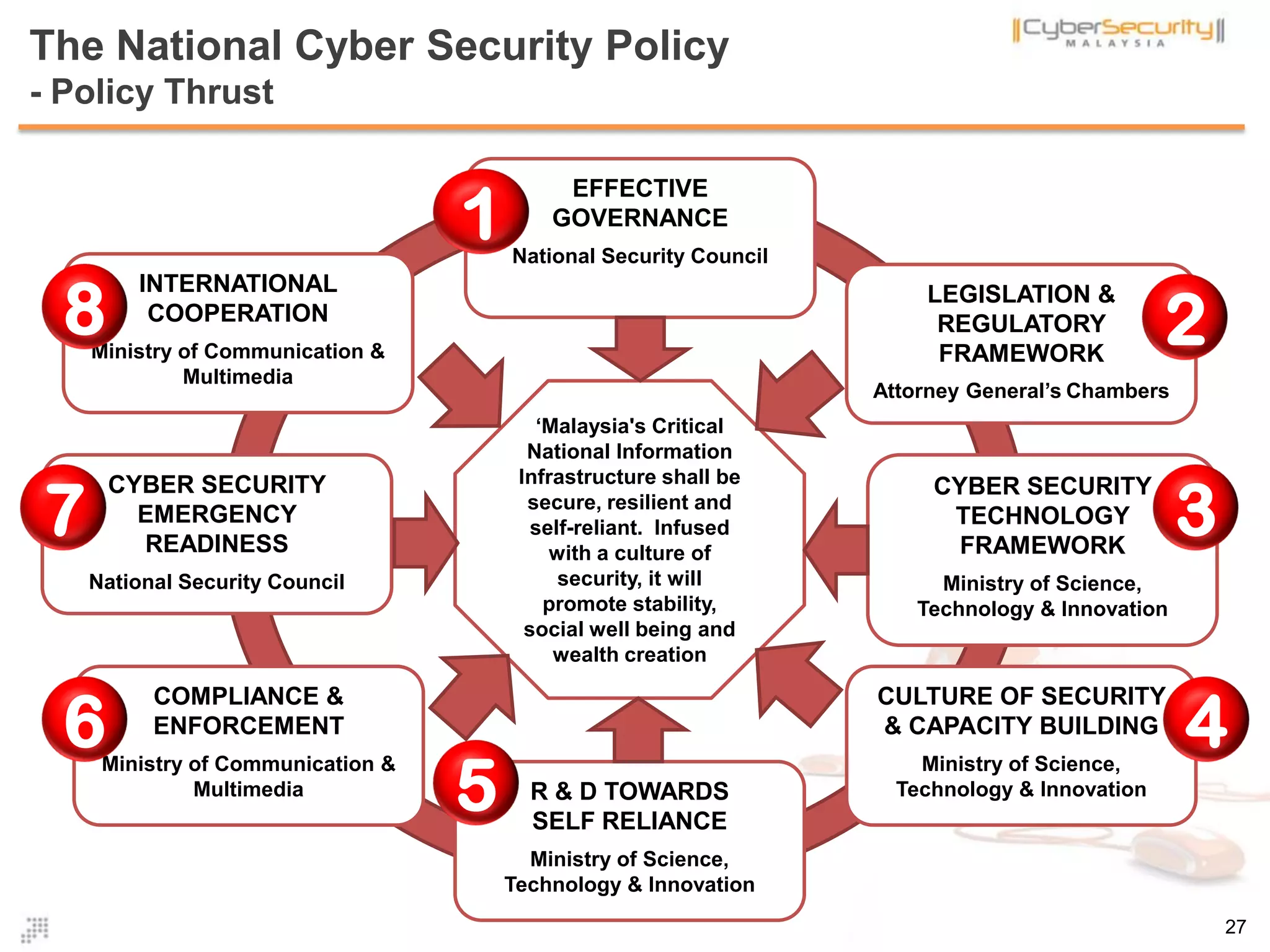
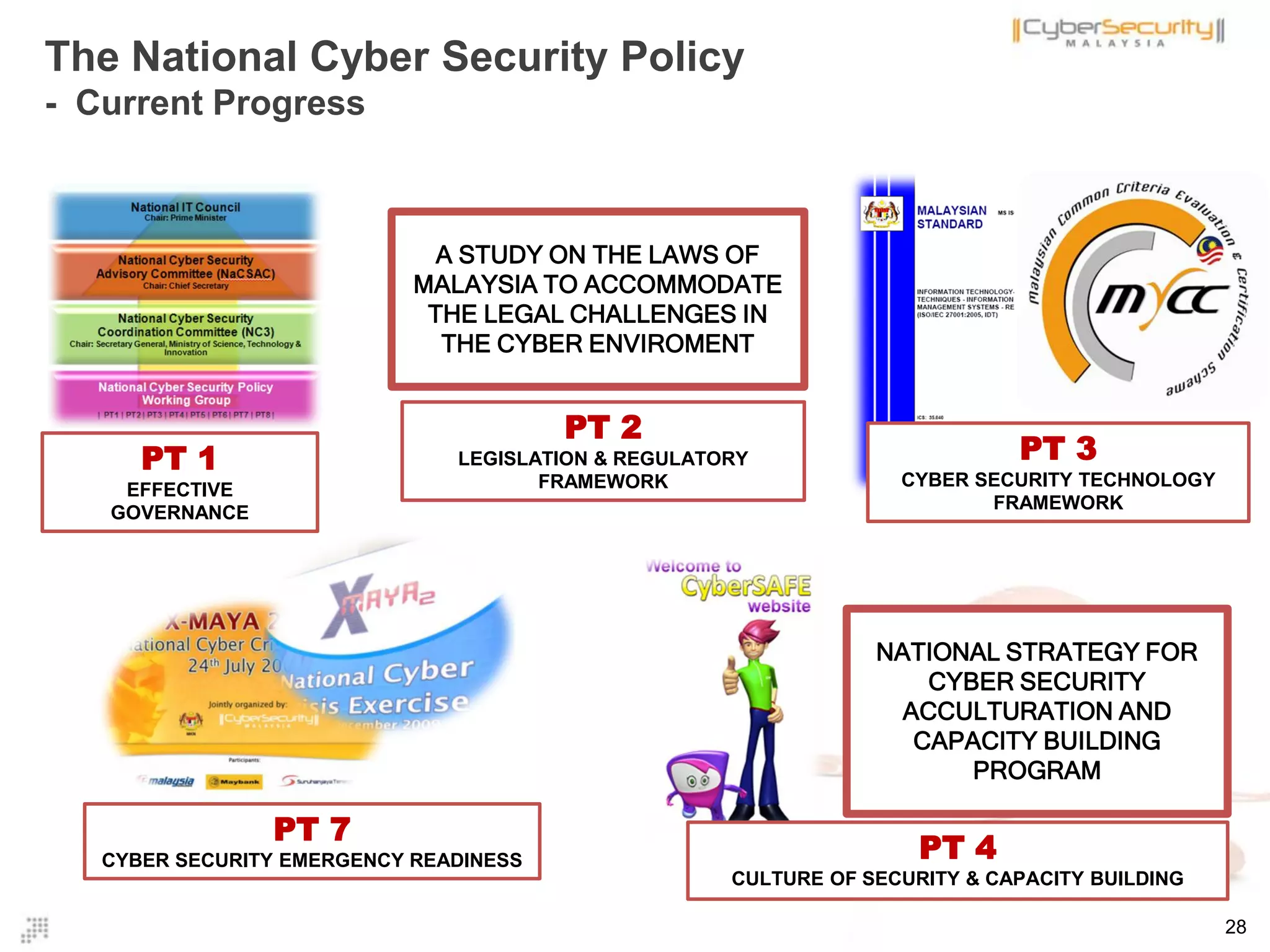
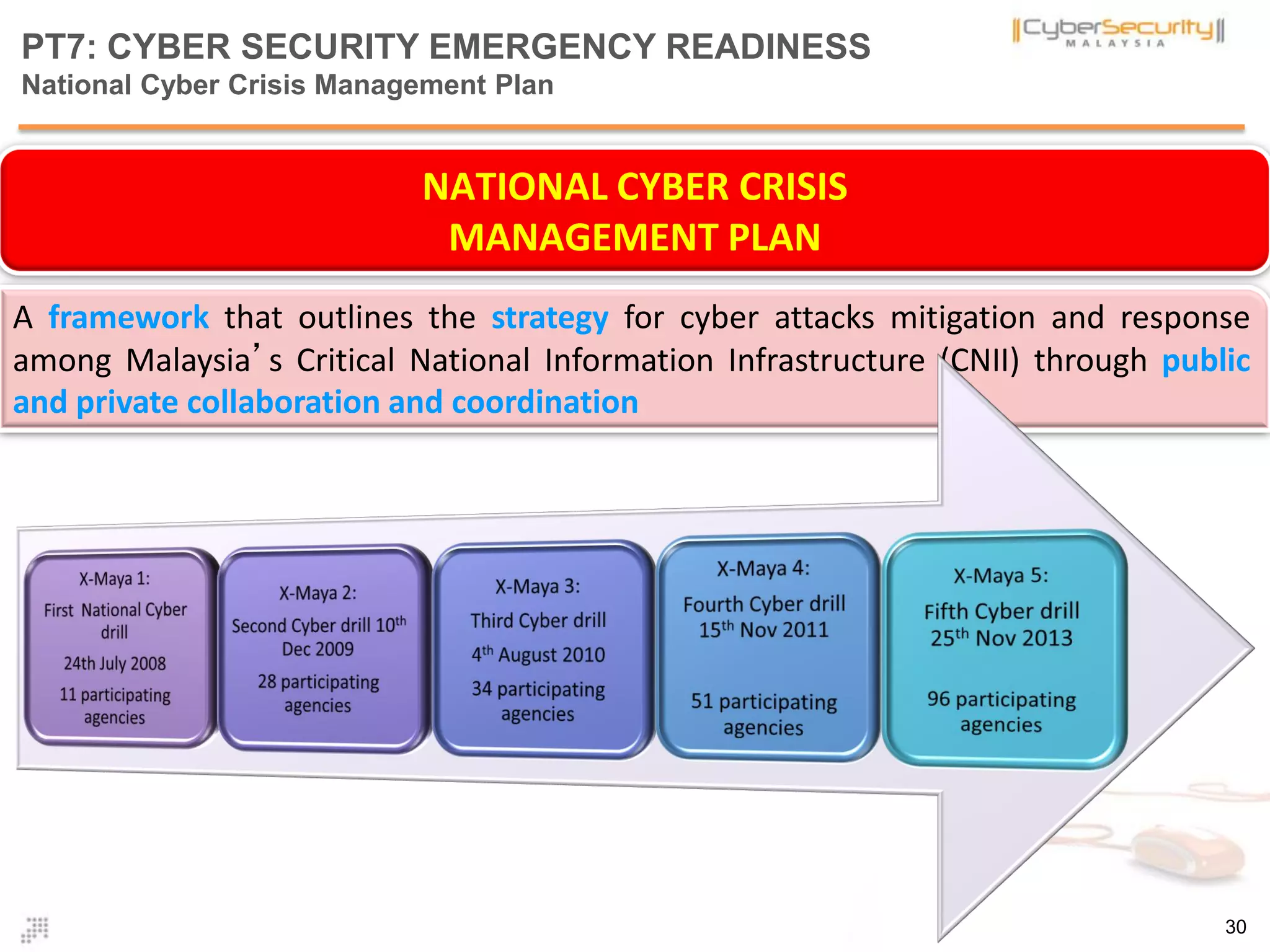
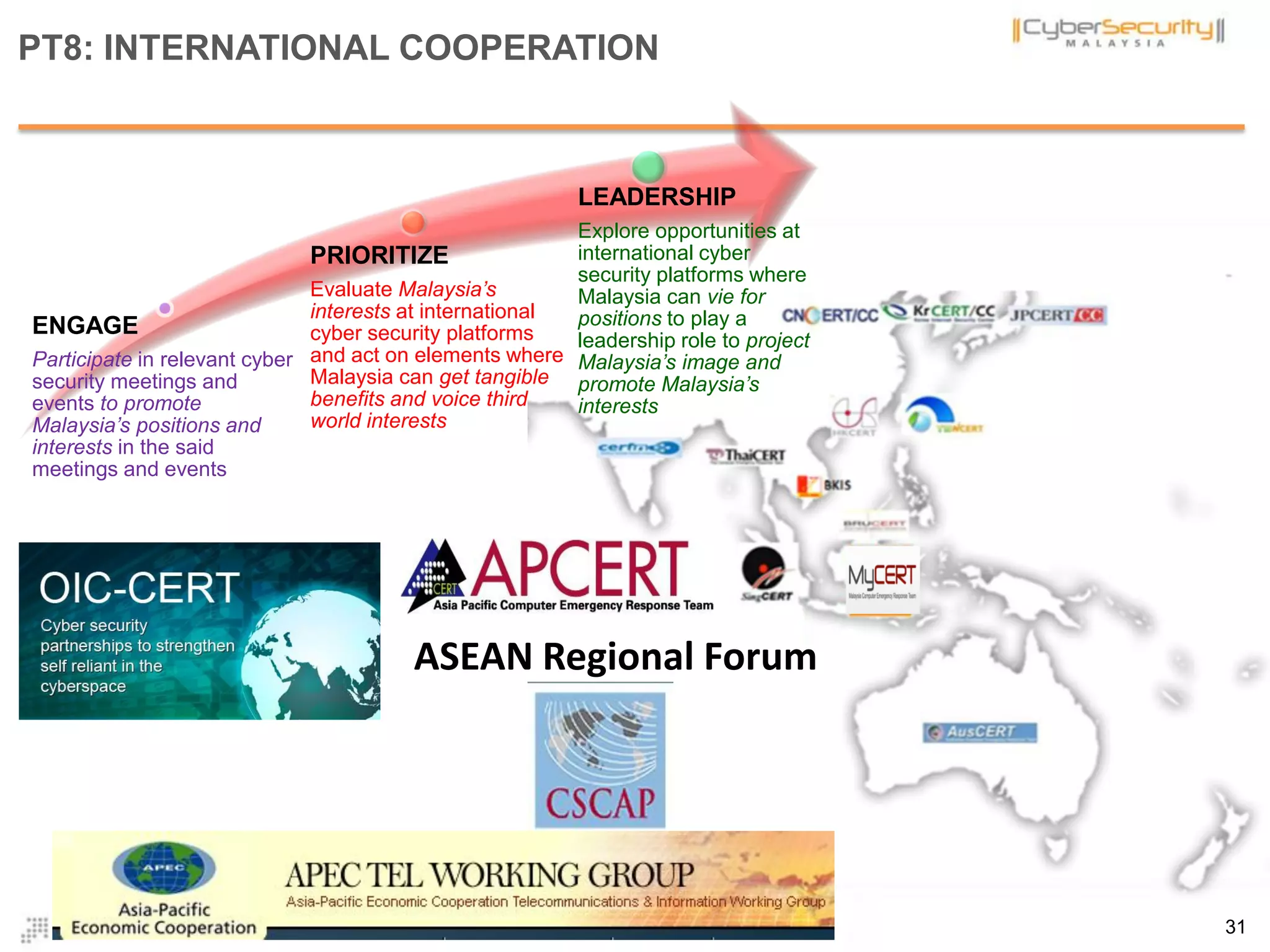
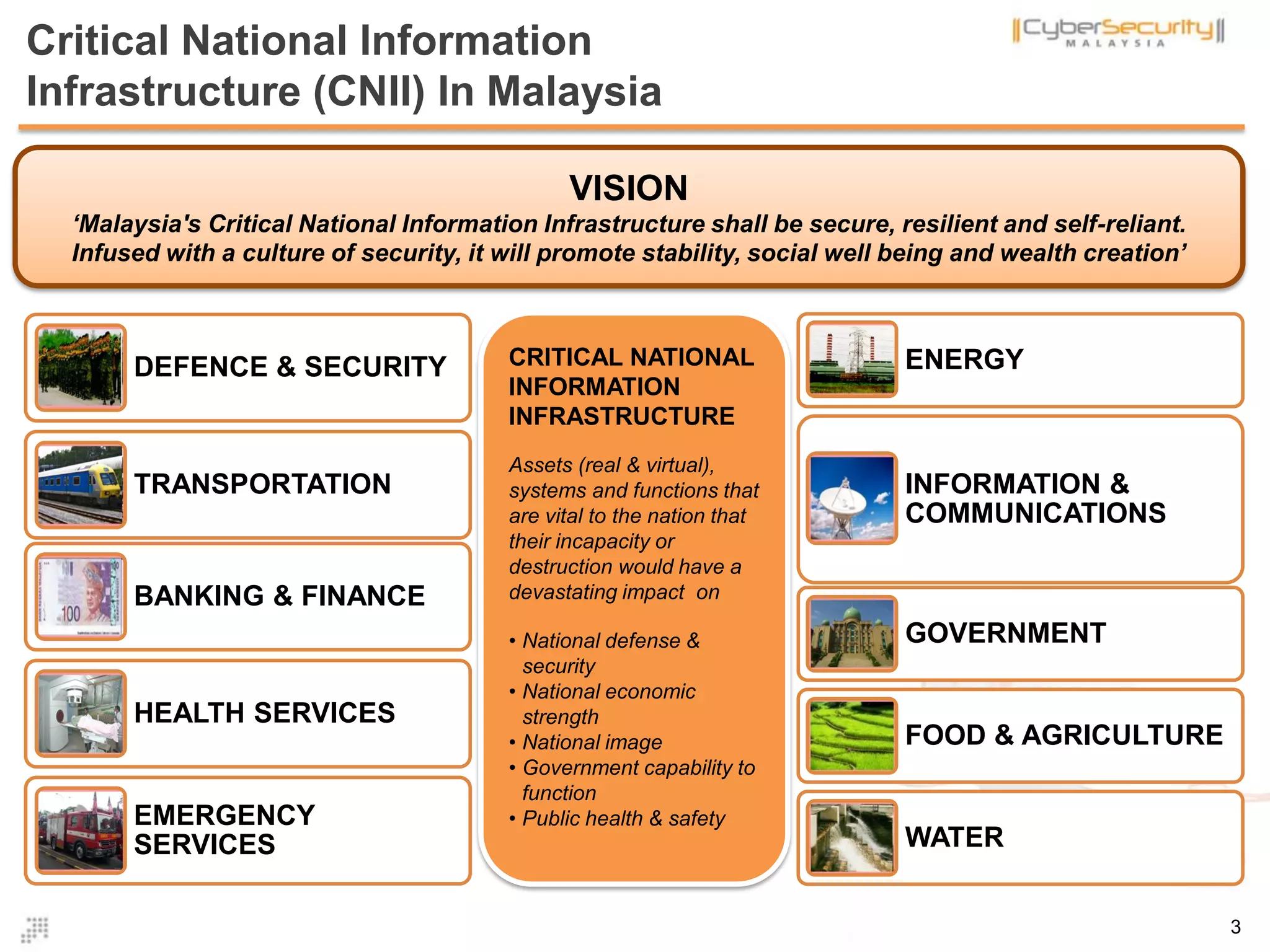
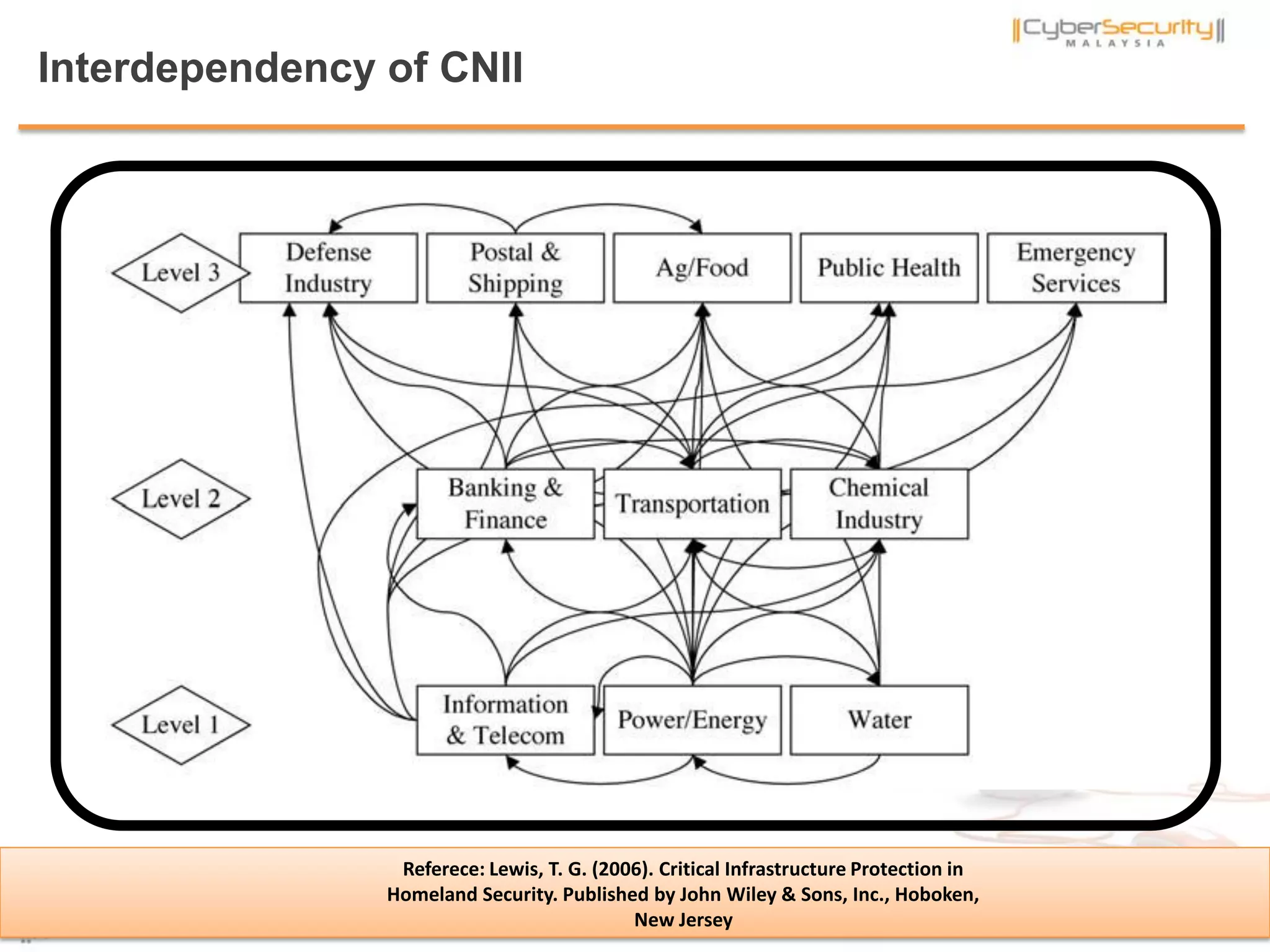
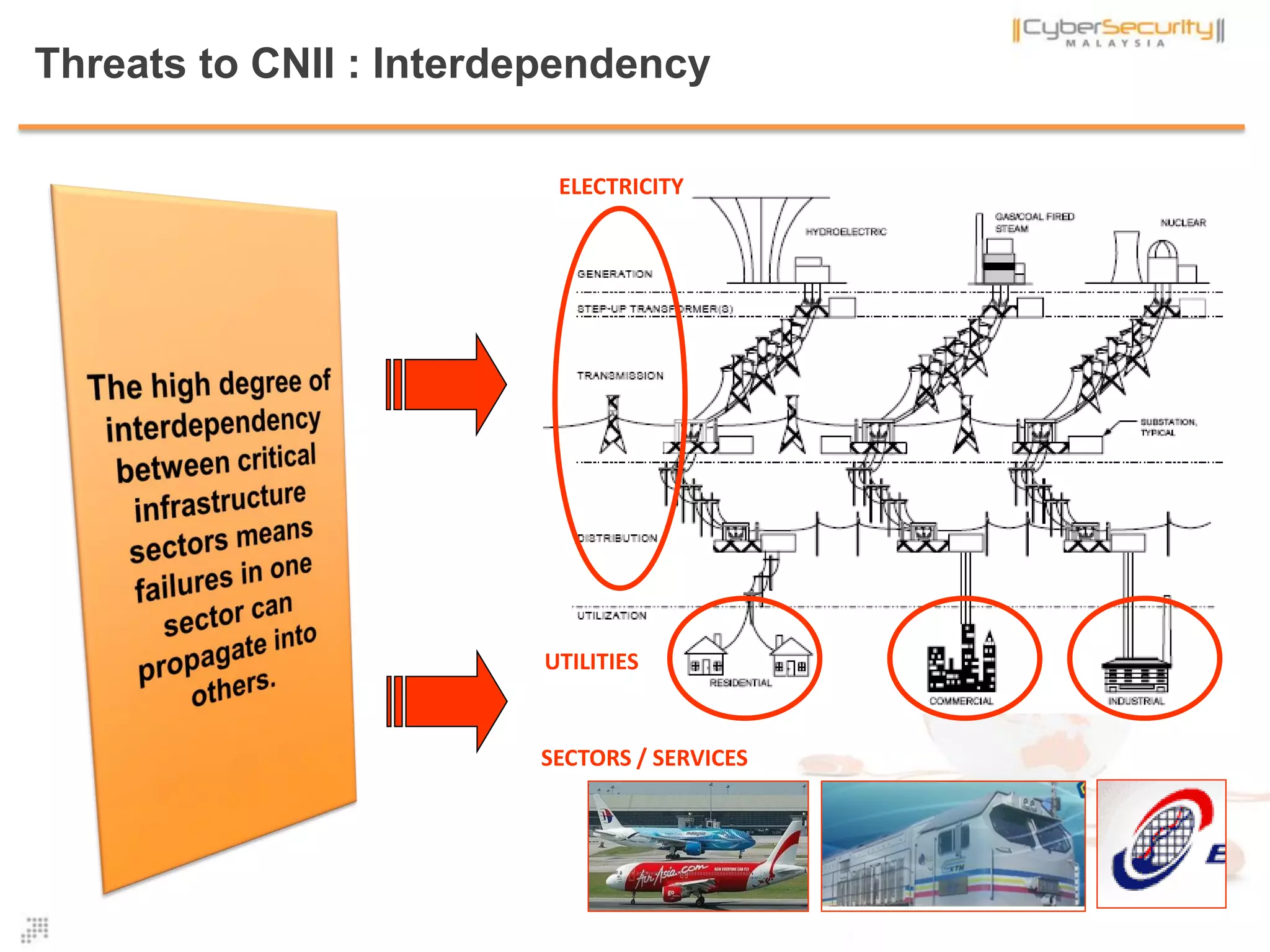
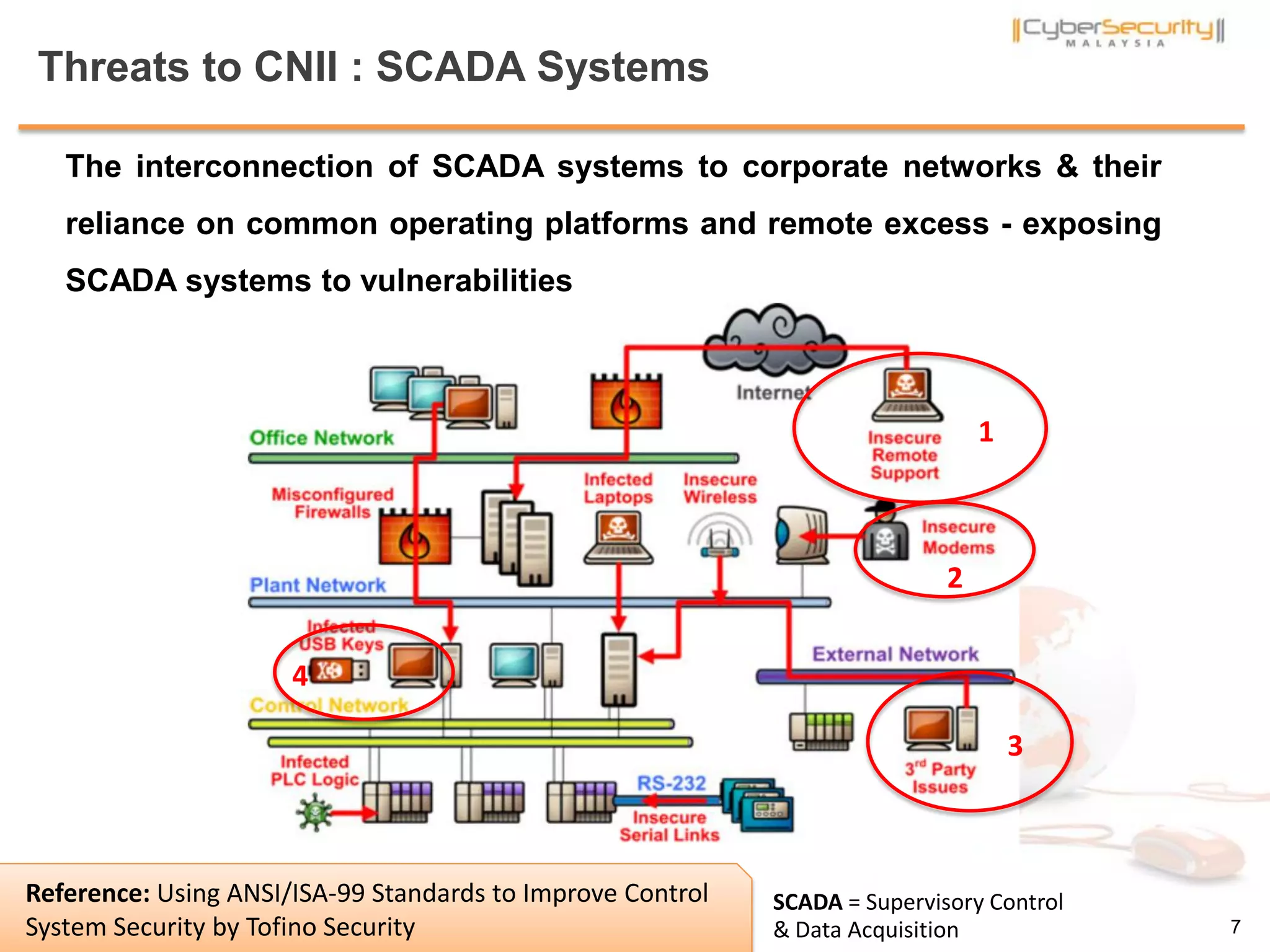
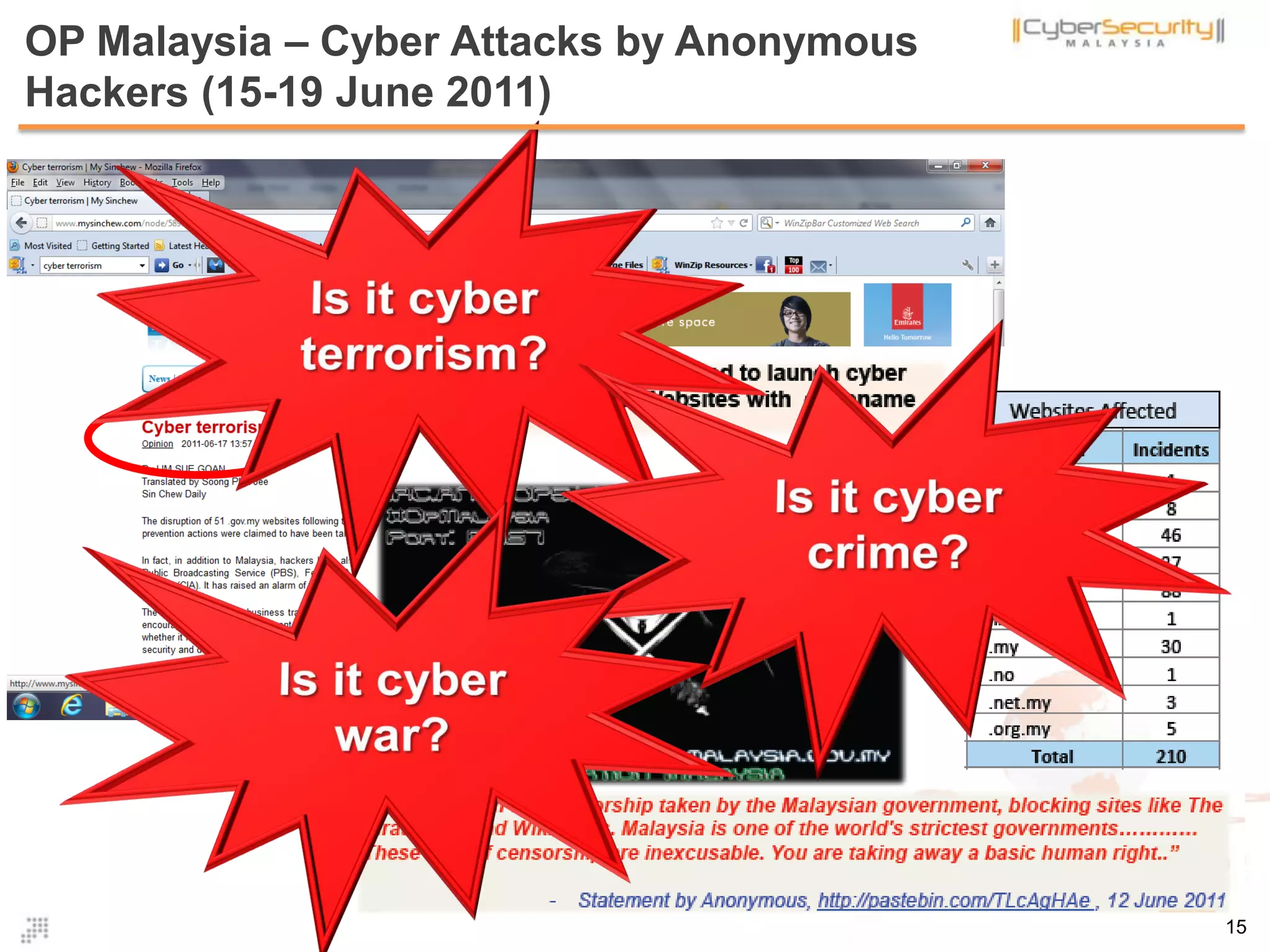
The document discusses cyber terrorism and threats to critical national infrastructure in Malaysia. It provides definitions of critical national infrastructure and cyber terrorism. It outlines Malaysia's National Cyber Security Policy and its objectives to protect critical infrastructure from cyber threats. The policy has several thrusts including effective governance, legislation, cyber security frameworks, emergency readiness, international cooperation, and developing a culture of security. It also discusses initiatives to safeguard critical infrastructure from cyber terrorism through public-private partnerships and a national cyber crisis management plan.



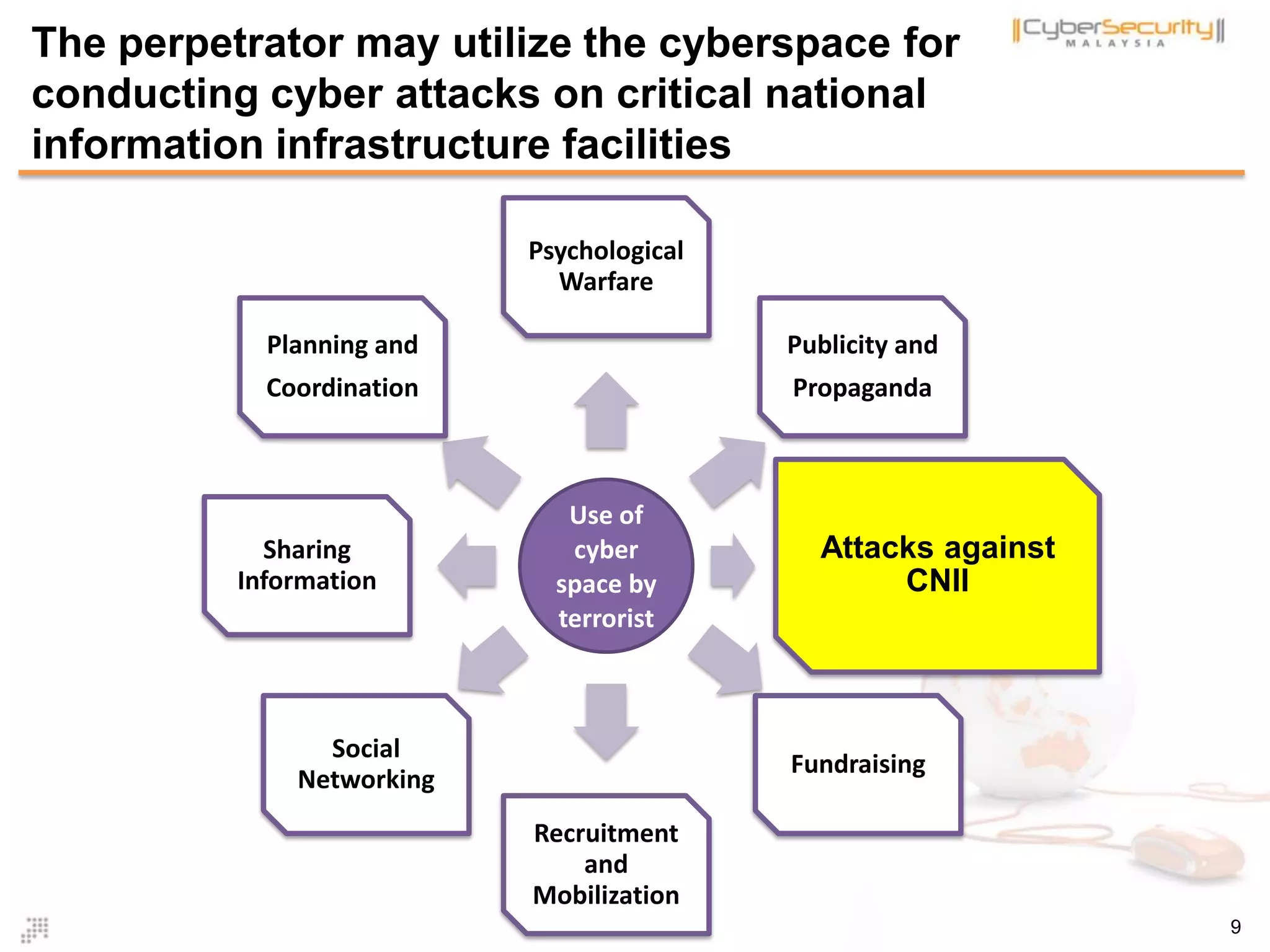
![Threats to CNII : The Use of ICT and
Cyberspace by Terrorist
Use of
Internet
By
Terrorist
Psychological
Warfare
Publicity and
Propaganda
Data Mining
Fundraising
Recruitment
and
Mobilization
Social
Networking
Sharing
Information
Planning and
Coordination
Reference:
[1] Mantel, B.: (2009). Terrorism and the Internet.
Should Web Sites That Promote Terrorism Be
Shut Down?. From CQ Researchers, pp. 129-153
[2] Zhang, Y., Zeng, S., Huang, C.N., Fan, L., Yu, X.,
Dang, Y., Larson, C., Denning, D., Roberts, N., and
Chen, H.: (2010). Developing a Dark Web
Collection and Infrastructure for Computational
and Social Sciences. IEEE International
Conference on Intelligence and Security
Informatics, pp. 59-64
[3] Li, X., Mao, W., Zeng, D., and Wang, F.: (2010).
Automatic Construction of Domain Theory for
Attack Planning. IEEE International Conference on
Intelligence and Security Informatics, pp 65-70
[4] Fu, T., Abbasi, A., and Chen, H. A Focused
Crawler for Dark Web Forums. Journal of the
American Society for Information Science and
Technology
[5] Yunos, Z., Ahmad, R., Mat Ali, S., and
Shamsuddin, S. Illicit Activities and Terrorism in
Cyberspace: An Exploratory Study in the
Southeast Asian Region. in:M. Chau et al. (Eds.):
Pacific Asia Workshop on Intelligence and
Security Informatics (PAISI 2012), 29 May 2012,
LNCS 7299 Springer, Heidelberg, pp. 27-35, 2012
8](https://image.slidesharecdn.com/session3-140319092443-phpapp02/75/Session-3-2-Zahri-Hj-Yunos-8-2048.jpg)


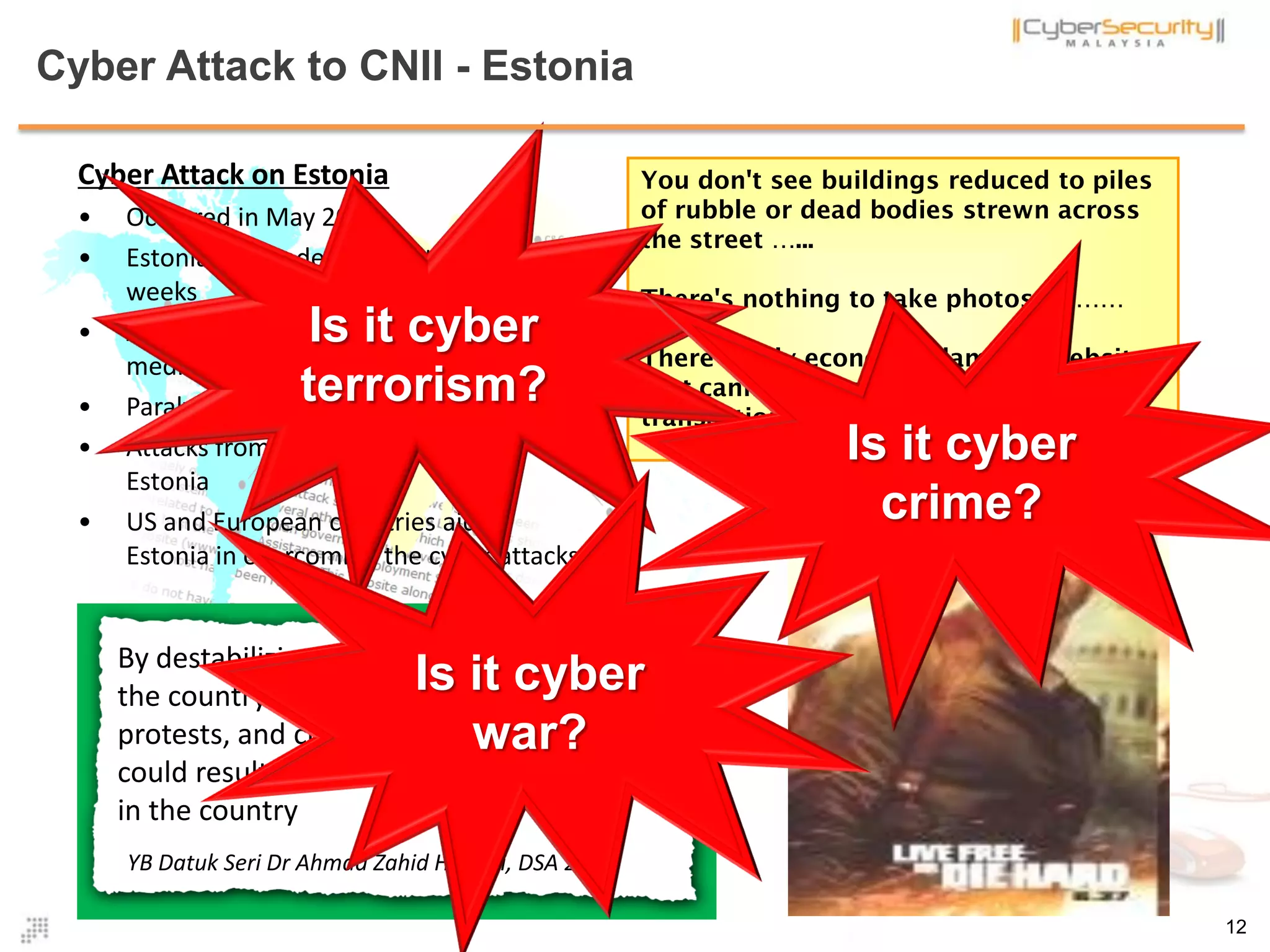
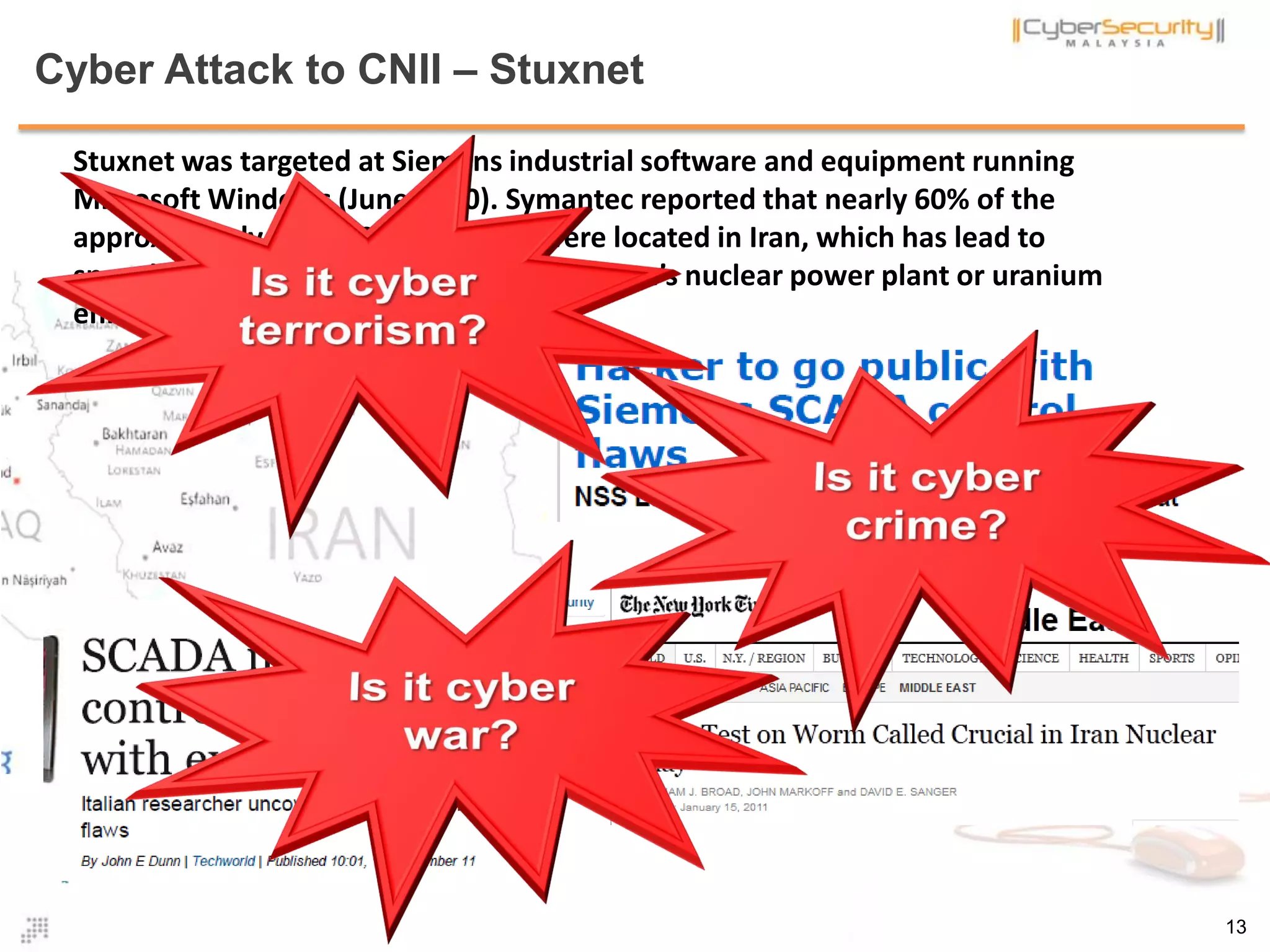
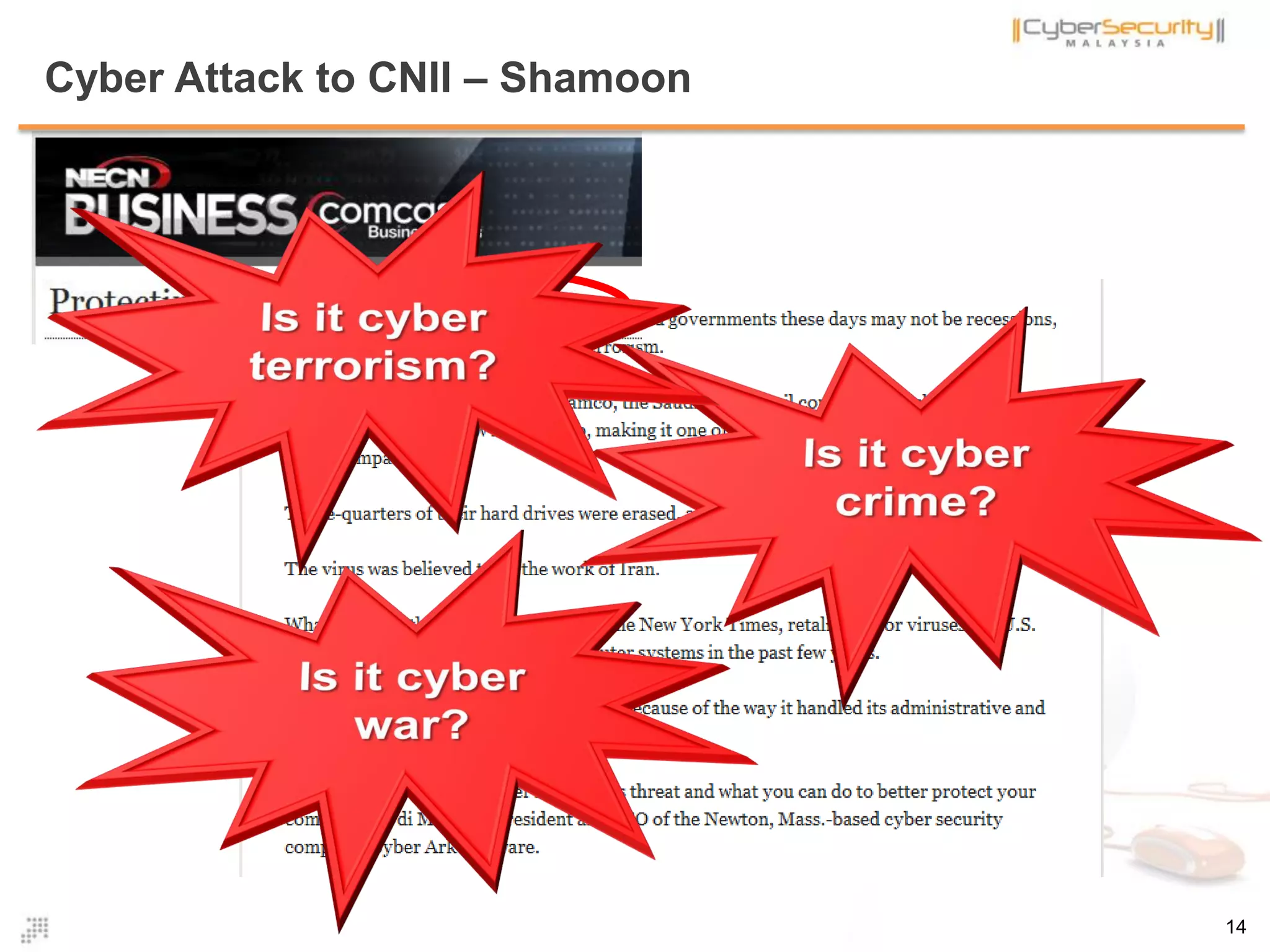

![Definition : Cyber Terrorism .. many more
• There are many definitions on cyber terrorism provided by researchers,
policy makers and individuals
• Interestingly, most governments in the world do not agree on one single
definition of cyber terrorism. There is no common definition of cyber
terrorism
• The ambiguity in the definition brings indistinctness in action; as the old
maxim goes “one man’s terrorist is another man’s freedom fighter” [1].
• According to Schmid, "there is no agreement among experts and there is
not likely to be an agreement as long they cannot even agree on a common
definition on terrorism (and cyber terrorism).“ [2]
Reference:
[1] L. E. Prichard, J. J., and MacDonald, “Cyber Terrorism: A Study of the Extent of Coverage in Computer Security
Textbooks,” Journal of Information Technology Education, vol. 3, 2004.
[2] A. P. Schmid, “Root Causes of Terrorism: Methodological and Theoretical Notes, Empirical Findings and Four
Inventories of Assumed Causal Factors,” 2005. 17](https://image.slidesharecdn.com/session3-140319092443-phpapp02/75/Session-3-2-Zahri-Hj-Yunos-17-2048.jpg)