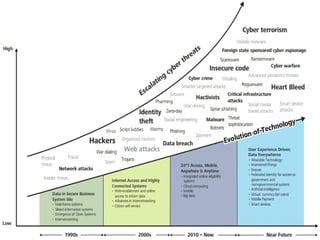
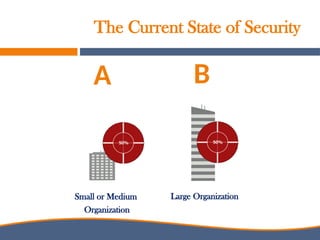
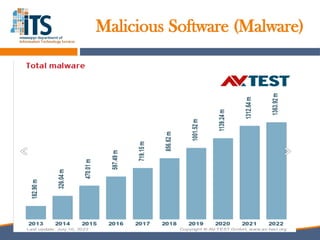
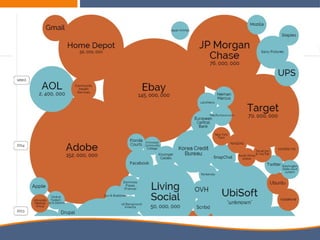
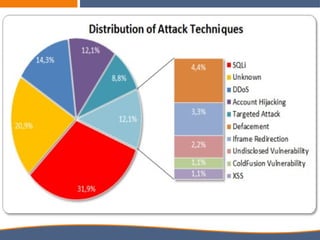
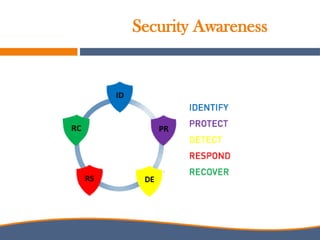
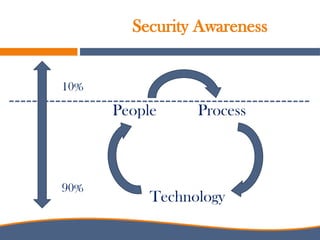
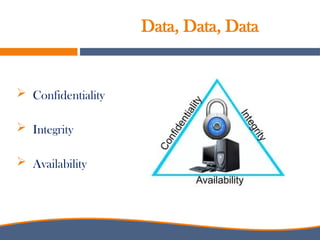
The document discusses the increasing importance of cybersecurity driven by the widespread use of the internet and connected devices, highlighting that nearly 310 million people in North America and 6 billion globally use the internet. It underscores the vulnerability of small businesses, with 60% of them going out of business within six months of a cyberattack, and reveals alarming statistics about the rise in cybercrime costs, breaches, and the inadequate cybersecurity preparedness among organizations. Furthermore, it emphasizes the human element in breaches and the need for comprehensive security awareness and measures to protect against various cyber threats.