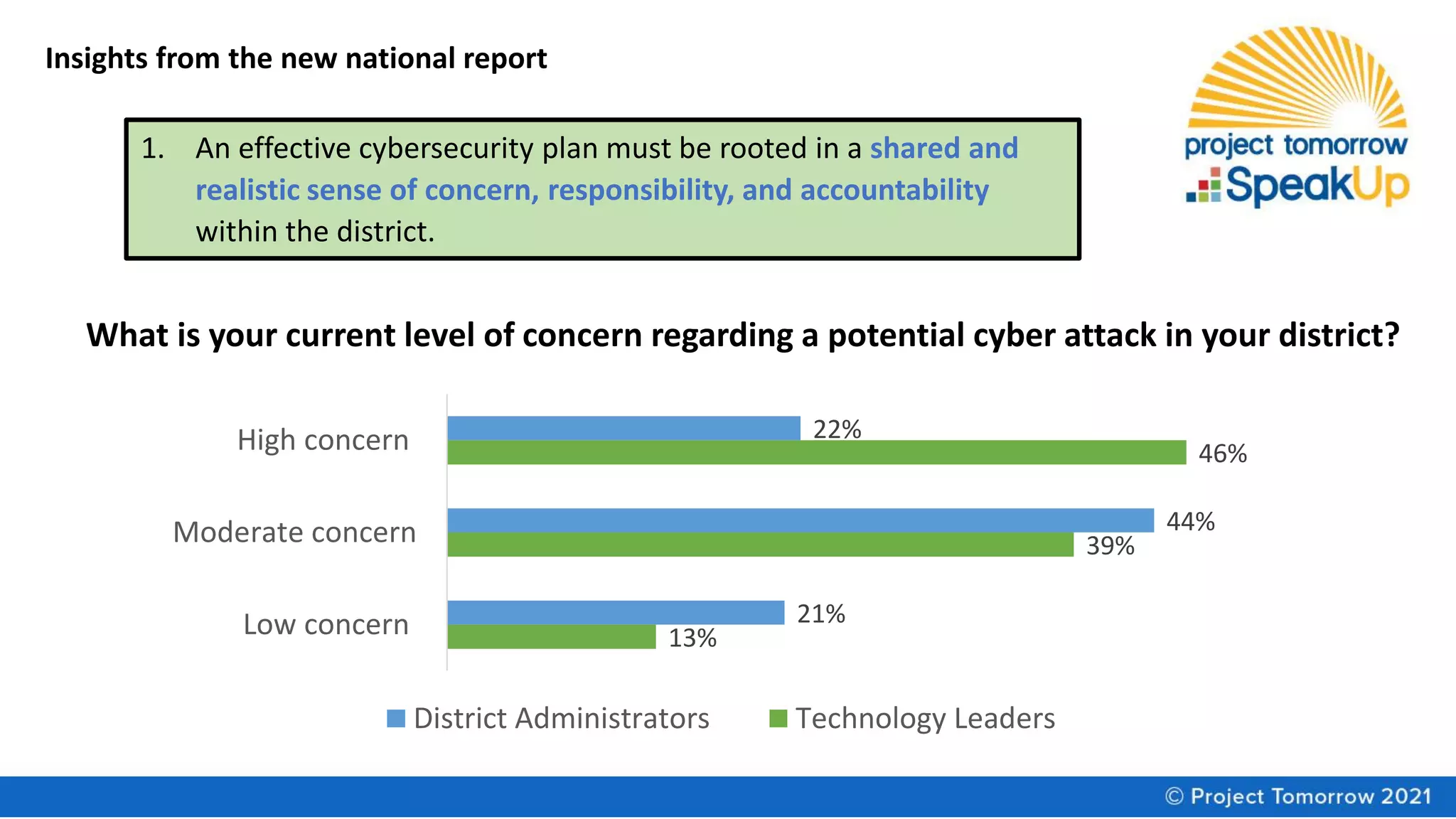
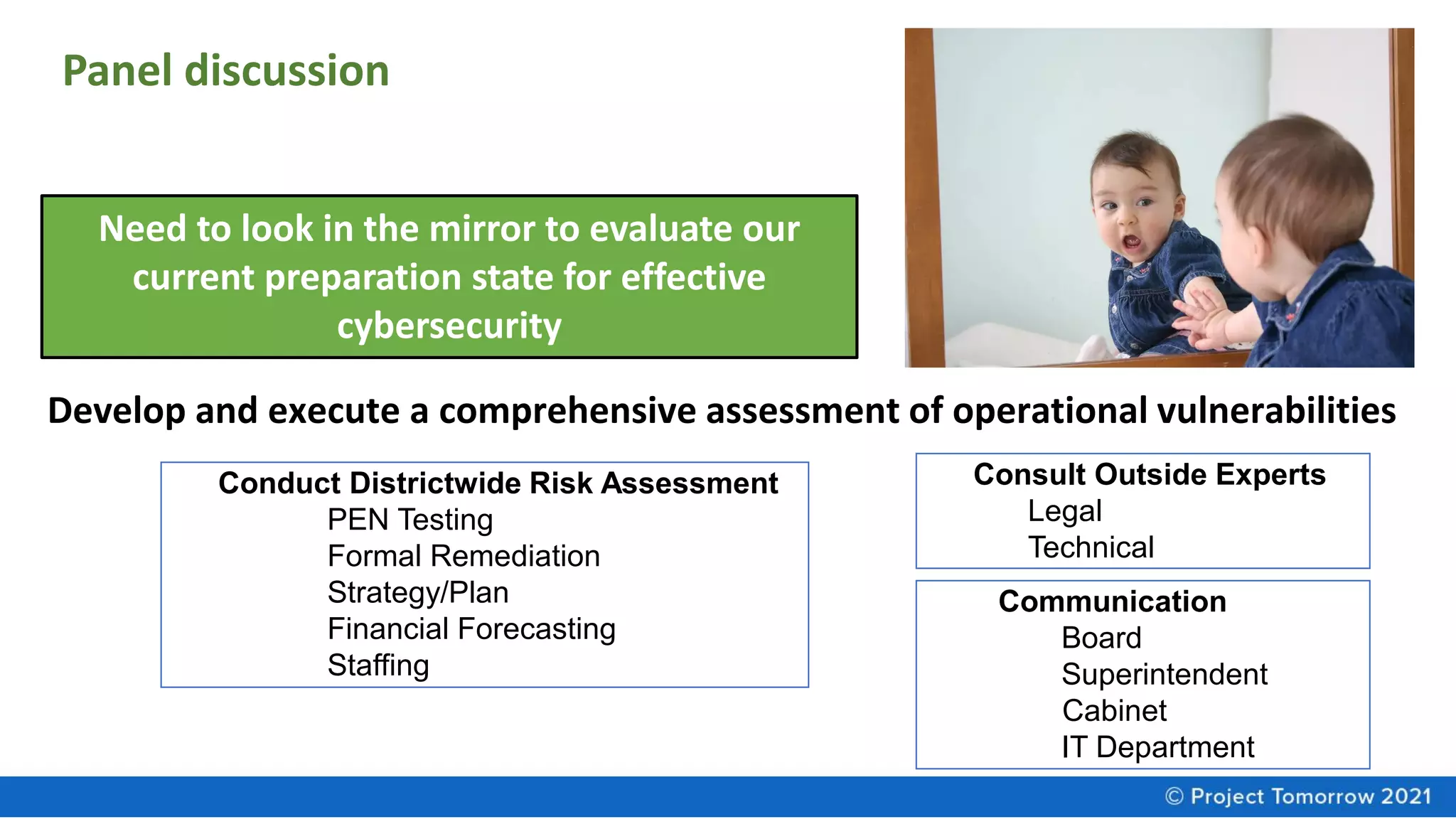
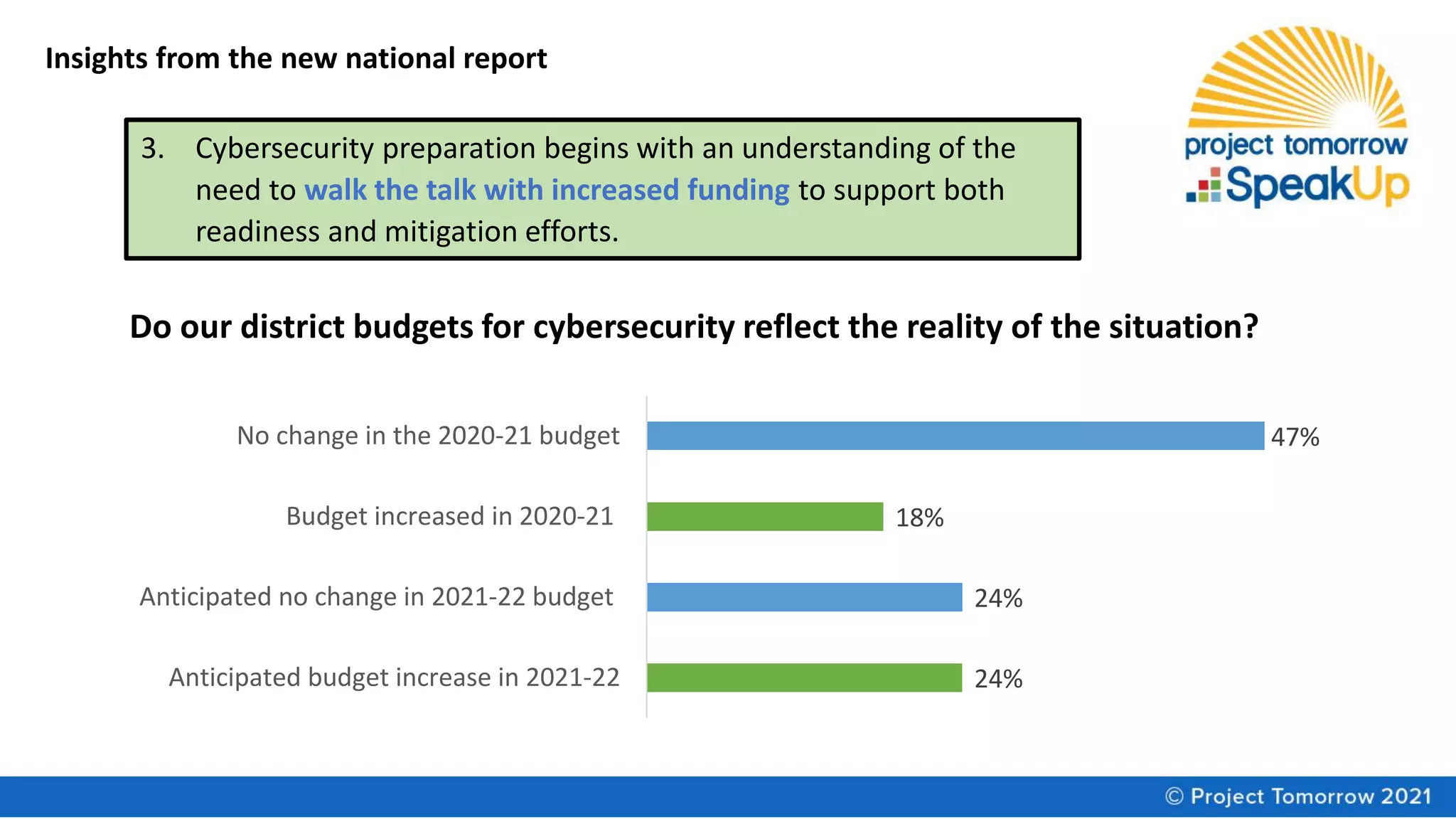
The document summarizes a panel discussion on cybersecurity strategies, policies, and practices for K-12 schools. The panel discusses the disconnect in leadership awareness of cybersecurity issues, findings from a new report on the topic, and resources for improving cybersecurity culture and preparedness. Key insights from the report include the need for shared accountability, reassessing management of technology assets, and ensuring adequate funding to support readiness and mitigation efforts.