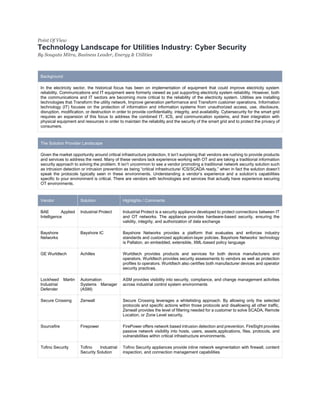
Utilities are increasingly relying on digital technologies to improve operations, but this exposes them to cybersecurity risks. While many vendors offer cybersecurity products, many lack experience securing operational technology (OT) environments used in utilities. It is important for utilities to understand vendor experience in OT security and whether solutions are compatible with protocols in these environments. A few vendors highlighted have technologies and services with experience securing OT networks for utilities.