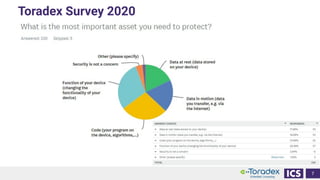
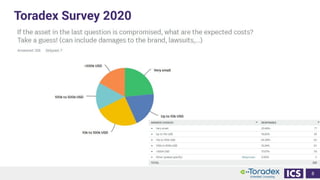
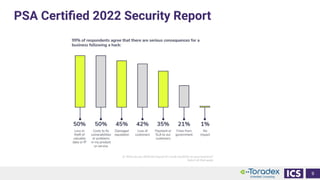
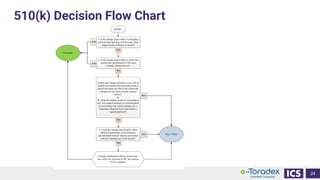
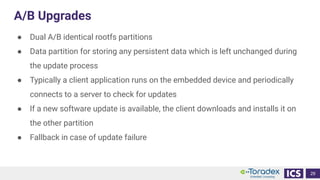
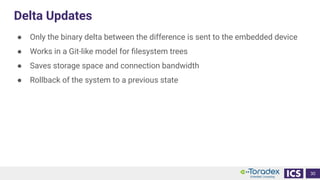
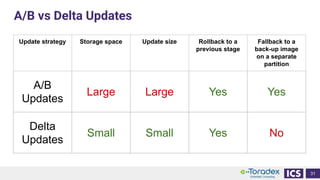
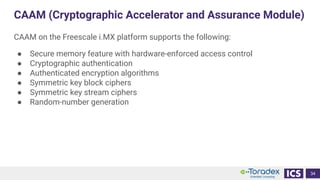
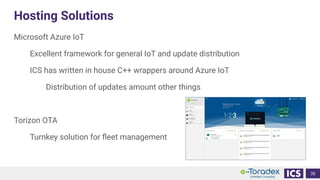
This document discusses cybersecurity and software updates in medical devices. It provides an overview of Integrated Computer Solutions (ICS) and the services it offers for medical device development. These include human factors engineering, software development, medical device cybersecurity, and software verification testing. The document also discusses Toradex and the Torizon platform it provides for over-the-air software updates in embedded systems. It notes regulations and standards driving new requirements for medical device cybersecurity and software updates. Finally, it discusses strategies for implementing secure software updates, including A/B updates, delta updates, container-based updates, and leveraging hardware encryption.