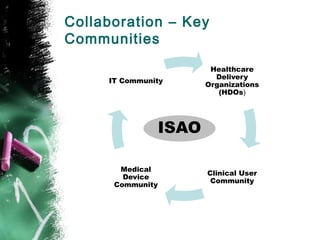
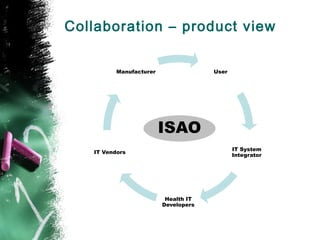
The document discusses the challenges of cybersecurity in networked medical devices, highlighting the potential risks to patient safety and public health due to vulnerabilities. It emphasizes the FDA's expectations for a holistic, proactive approach to post-market management, involving collaboration among various stakeholders in the healthcare sector. Key themes include continuous monitoring, risk assessment, and shared responsibility to ensure device safety and effectiveness.