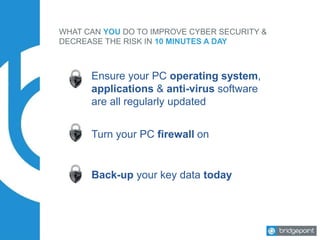
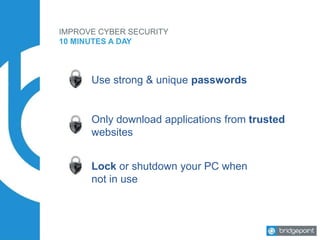
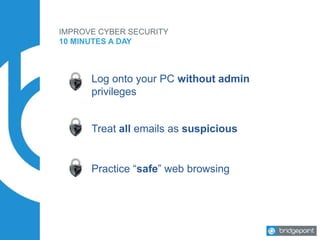
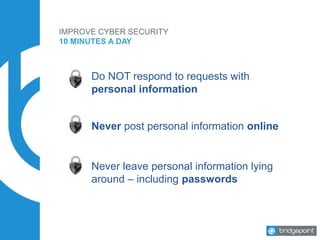
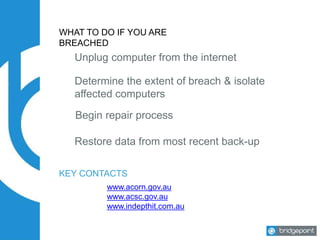
This document discusses the risks and challenges of cyber security for small and medium businesses. It notes that if a business uses email or has a bank account, it is a target for cyber attacks. Some key points made include that every minute a computer accesses a malicious website, every 3 minutes an infected computer communicates with an attacker, and every 10 minutes a malware is downloaded. It provides tips for improving cyber security in 10 minutes a day, such as ensuring systems and backups are updated, using strong unique passwords, and practicing safe web browsing. The document stresses that employee education is key to preventing most breaches.