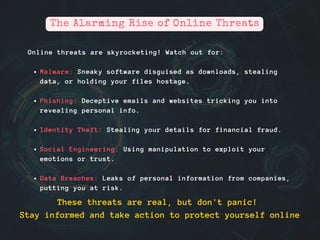
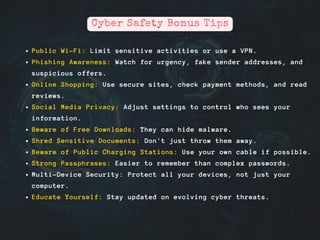
The document emphasizes the importance of cybersecurity in the digital age, highlighting various online threats such as malware, phishing, and identity theft. It offers practical tips for individuals to protect themselves, including using strong passwords, enabling two-factor authentication, and being cautious with public Wi-Fi and online shopping. The document encourages continued education on evolving cyber threats to ensure a secure online experience.