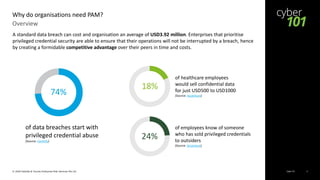
Privileged access management (PAM) is the combination of tools and technology used to secure, control, and monitor access to an organization's critical information and resources. PAM solutions typically include an access manager to control employee access, a session manager to monitor privileged user actions, and a password manager to protect and enforce password policies. PAM is important because the majority of data breaches start with privileged credential abuse, and it can help organizations comply with regulations, recover from attacks faster, and save both time and money.