Embed presentation
Download to read offline
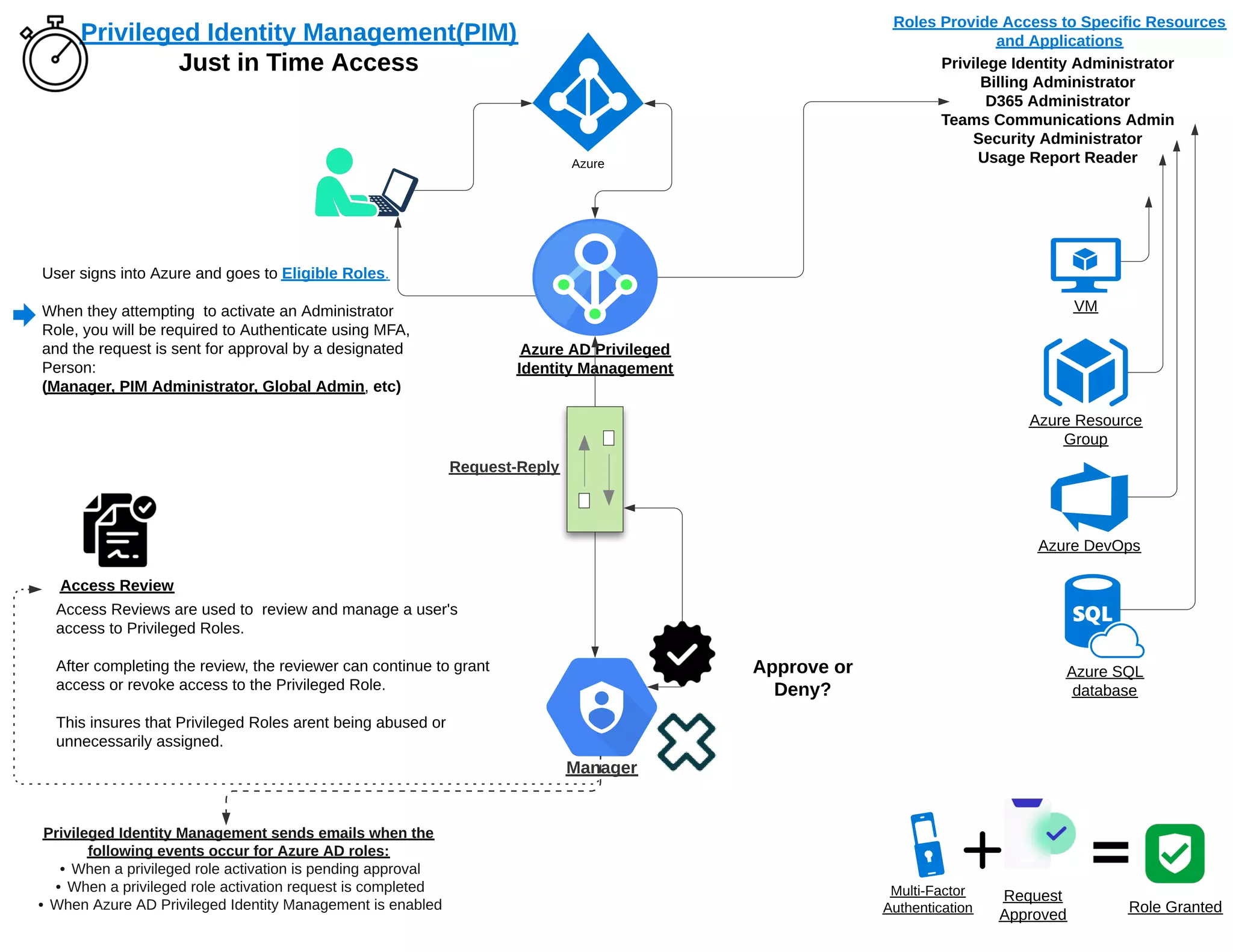

The document outlines the process for activating administrator roles in Azure, which includes mandatory multi-factor authentication (MFA) and approval from a designated individual. It describes how access reviews are used to manage and evaluate user access to privileged roles to prevent misuse. Notifications are sent out for various actions related to role activation and management within Azure Active Directory's Privileged Identity Management.
