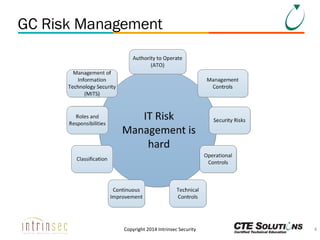
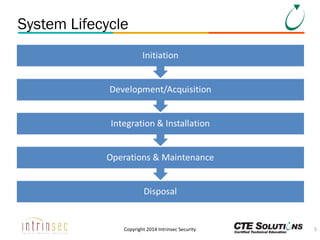
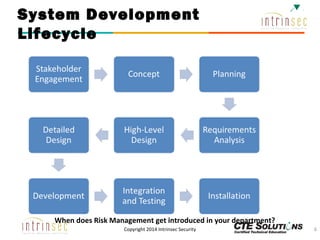
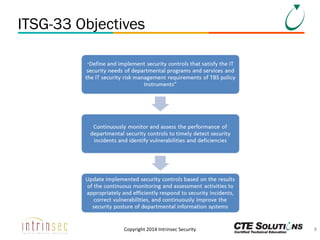
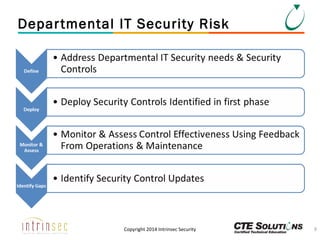
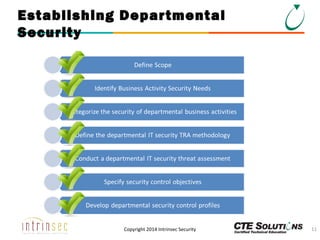
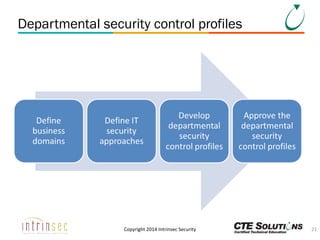
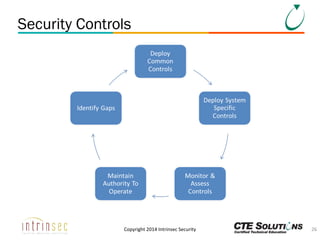
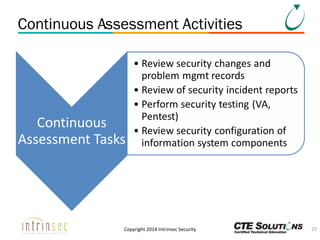
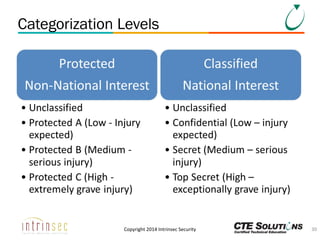
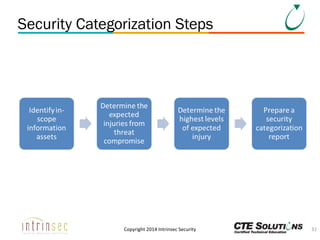
The document outlines the ITSG-33 security standards for risk management, detailing various aspects such as system development lifecycle, threat assessments, and security control objectives. It emphasizes the importance of continuous security assessment activities and categorization processes to ensure departmental security. For further information and training, the document references the resources provided by CTE Solutions and offers contact details for their offices.